- ARP Protocol: Address Resolution Protocol, it is a TCP/IP protocol used to get a MAC address based on an IP address.
- ARP Attack: Mainly divided into flooding attacks and spoofing attacks.
- The first type primarily sends a large number of ARP messages, causing the target machine to disrupt communication.
- (With one command you can arpspoof -i eth0 -t target IP gateway IP);
- The second type mainly involves deceiving the target machine that it is the gateway, etc., and performing data tampering and sniffing, categorized as a man-in-the-middle attack. ARP attack premise: Must be on the same local area network as the target machine.
- Driftnet: A software that captures images from network traffic and displays them in a small window.
Code Language: JavaScriptCopy
Major parameters:-b Sound alert when a new image is captured-i Select the listening interface-f Read images from a specified pcap data packet-a Background mode:-m Specify the number of images to be saved-d Specify the path to save images-x Specify the prefix name for saving images123456789Implementation:
Let’s sort out, mainly three points: deceive, intercept, get away!Target, the lady’s phone ip192.168.0.102 (don’t ask how I know, just nmap -sP scan the entire network segment of the local network)Attacker 192.168.0.104Gateway 192.168.0.1First, open ettercap, then select sniff->unified sniffing, and then choose the network card you want to capture packets from, as shown below:
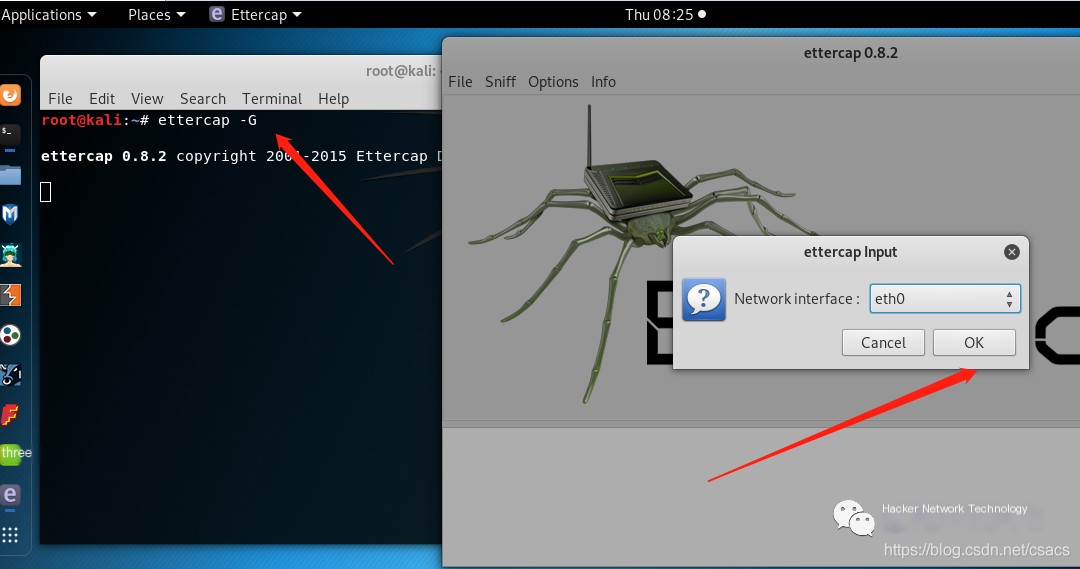 >
>
Then click Hosts->Scan for host. After the scan is completed, click Host list, and you can see the list of scanned hosts, as shown below:
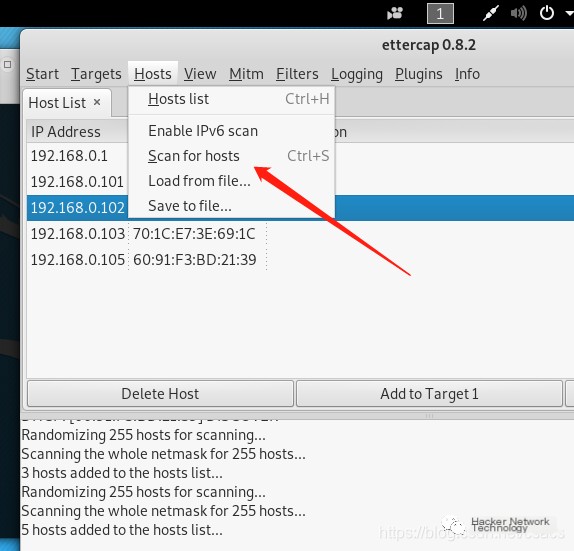 >
>
Then you can select the target 192.168.0.102, click Add to Target 1, then select the IP address of the gateway 192.168.0.1, click Add to Target 2.
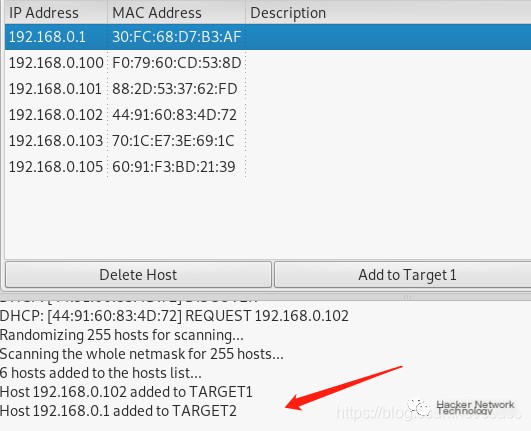
The main principle is to deceive the host 192.168.0.102 that I (192.168.0.104) am the gateway (192.168.1.1), so that the host directs all data traffic through me. This means I can now delete, manipulate, simulate, and view all communications. This is not good.Implementation steps are mitm->arp poisoning->Sniff remote connections, and finally start.
Then you can use Wireshark to capture all traffic packets, but this time our focus is on visual impact; text doesn’t really convey a feeling, so use driftnet to directly capture images.Now, it’s the moment to witness the miracle!!!
In fact, 192.168.0.104 is my own phone, screenshot as proof,
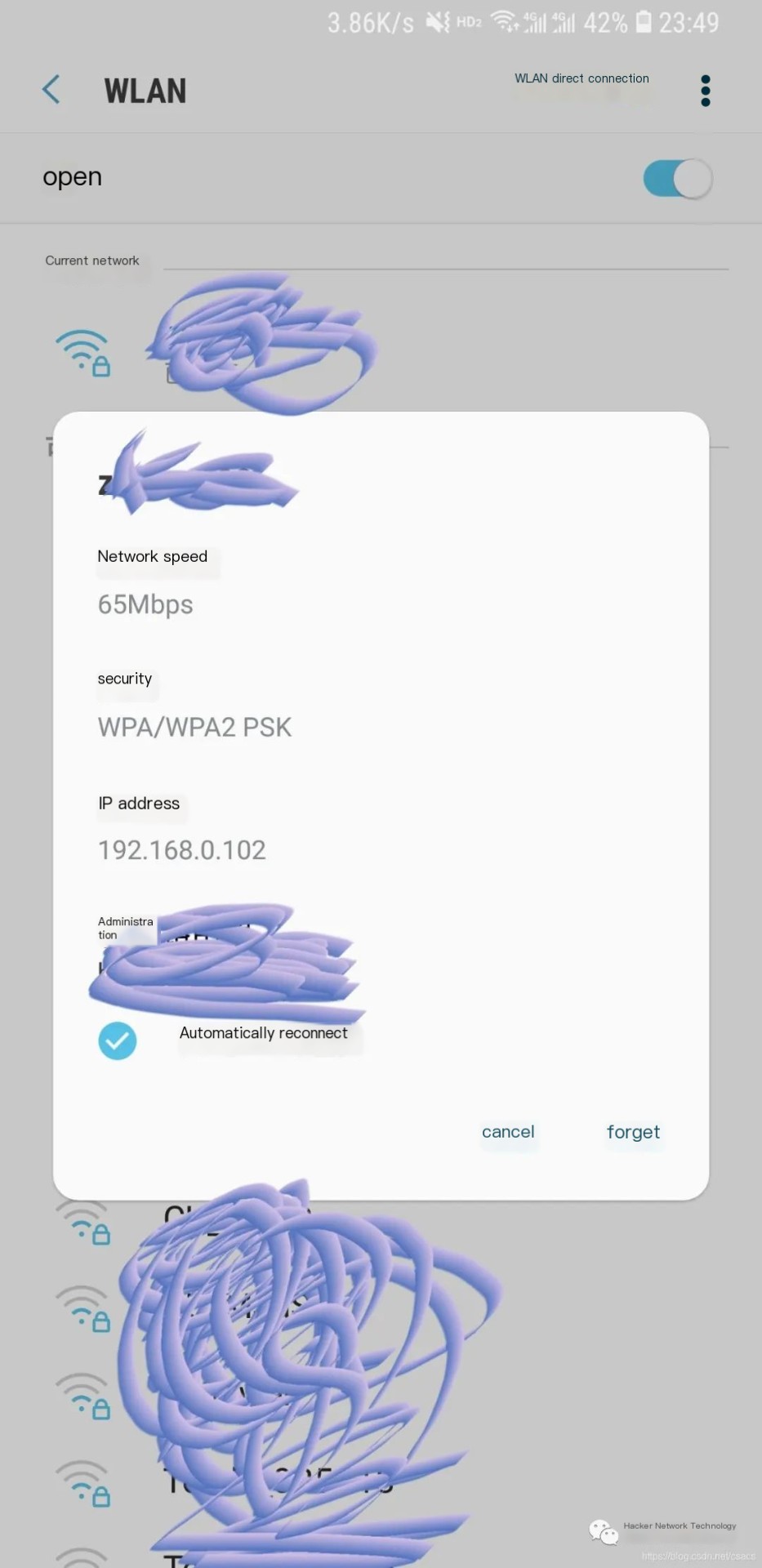
Actually, the biggest surprise is here, here:
Knock the blackboard: "Criminal Law" Article 285 [Crime of Illegal Invasion of Computer Information System; Crime of Illegally Acquiring Computer Information System Data, Crime of Illegally Controlling Computer Information System] Violating national regulations, invading state affairs, national defense construction, computer information systems in cutting-edge science and technology fields shall be sentenced to a fixed-term imprisonment of up to three years or to criminal detention. Violating national regulations, invading computer information systems other than those specified in the preceding paragraph or using other technical means to acquire data stored, processed, or transmitted in that computer information system, or illegally controlling that computer information system, and if the circumstances are serious, shall be sentenced to a fixed-term imprisonment of up to three years or to criminal detention, and a fine may be imposed in addition to or separately; if the circumstances are particularly serious, shall be sentenced to more than three years and up to seven years of fixed-term imprisonment, and a fine shall be imposed.
After playing around, let’s talk about serious matters, how to defend?:
- 1. The simplest way is to bind the correct IP and MAC mapping, such as the gateway IP and gateway MAC
arp -s ip mac - 2. If this is still troublesome, then just download an ARP firewall
- 3. For learning and communication only, do not engage in any illegal operation, consequences are at your own risk!


