Hello everyone, it’s nice to see you again. I am your friend, FullStackJun, here to talk about LC5 activation.
lc5 Download:
Link: https://pan.baidu.com/s/1Ljg3aJiaarf2vYHEJ91fiQ Extraction Code: xxmt
Contents
Experiment Purpose:
1. Master the method of setting up an FTP server 2. Understand the use of FTP. 3. Learn the configuration and use of the LC5 activation success tutorial password tool.
Experiment Tasks:
1. Set up a simple FTP server, assign users, and set passwords according to the experimental content. 2. LC5 activation success tutorial tool.
Experiment Principles:
Generally, intruders commonly use the following methods to obtain users’ passwords, including weak password scanning, Sniffer password sniffing, brute force activation success tutorial, probing, extracting, or synthesizing passwords, etc. For the activation success tutorial of system user account passwords, the main method is based on string matching activation success tutorial. The most basic methods include brute force and dictionary attacks. The brute force method is the least efficient, generating password strings according to the exhaustive rules of characters or numbers and attempting them one by one. In cases where the password combination is slightly complex, the brute force activation success tutorial speed is very low. The dictionary attack is relatively more efficient; it uses pre-defined common characters in a password dictionary to attempt to match passwords. A password dictionary is a large text file that can be self-edited or generated by dictionary tools, containing combinations of words or numbers. If your password is just a word or a simple number combination, the activation success tutorial could easily activate the password. Client operating system: Windows 2000 / Windows XP with IP address 192.168.2.1, server operating system: Windows 2000 Advance Server / Windows XP with IP address 192.168.2.2. During the experiment, if there are no two machines, a virtual machine can be used to install the server Windows 2000 Advance Server / Windows XP in the virtual machine. The client and server can also be installed in the virtual machine simultaneously.
Experiment Environment:
Client operating system: Windows 2000 / Windows XP with IP address 192.168.2.1 Server operating system: Windows 2000 Advance Server / Windows XP with IP address 192.168.2.2 During the experiment, if there are no two machines, a virtual machine can be used to install the server Windows 2000 Advance Server / Windows XP in the virtual machine. The client and server can also be installed in the virtual machine simultaneously.
Experiment Steps:
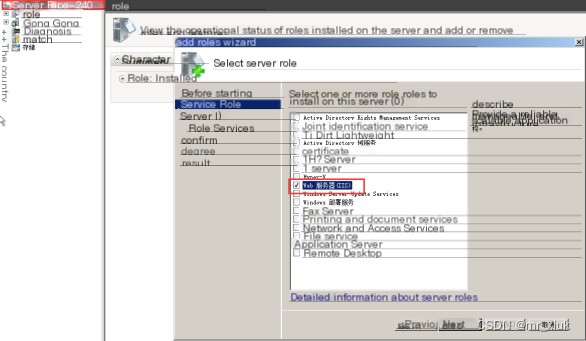
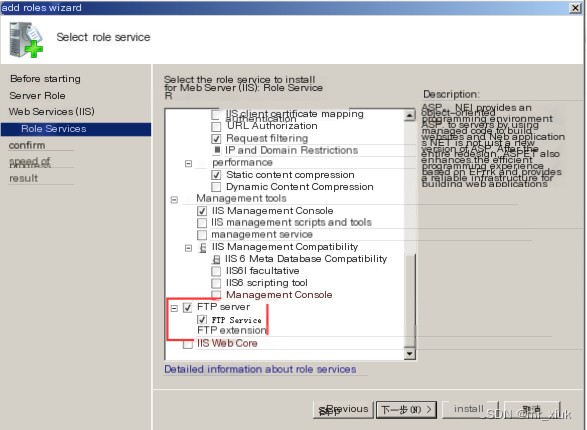
1. First, set up the IIS server, selecting the role service as an FTP server, and click next to install.
 />
/> />
/>
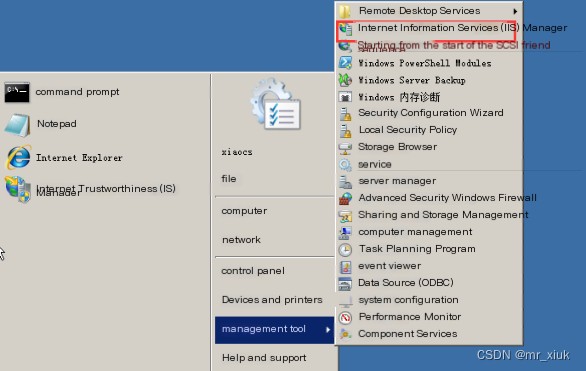
2. Then set up the FTP service on the server, select Add FTP site, and right-click to choose Properties.
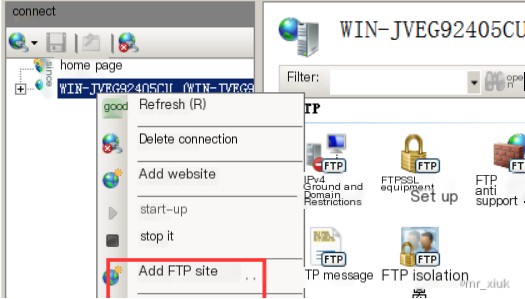
Set the IP address (bind the server’s IP address 192.168.192.175)
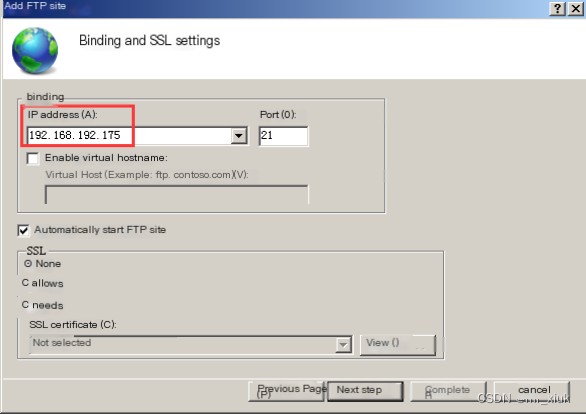
3. Then create a user xiaoxiukun (for following FTP remote login experiment)

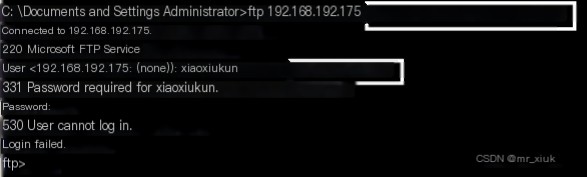
4. Connect to the server’s FTP service on the client: Start Wireshark on the client (as no available Sniffer sniffer was downloaded, Wireshark is used here for packet capture monitoring), and then use the FTP command under DOS to connect to the server’s FTP server. (When the password is unknown)
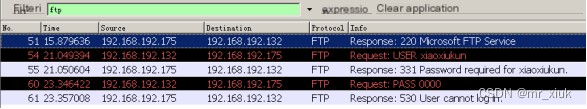
Use the packet capture tool Wireshark to view the captured FTP process (Sniffer is recommended):
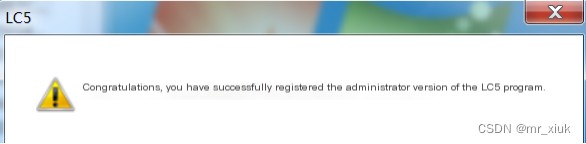
5. Activate the FTP server password, a username and password pair have been set in advance (where the username is known but the password is unknown, but known to be a pure numeric password no longer than six digits, or a complex password containing numeric characters), and the program’s function is to perform a brute force activation success tutorial on this user’s password on the FTP server, and record the time used for the activation success tutorial. First, use the registry file in the downloaded software package to register LC5 Admin Edition.
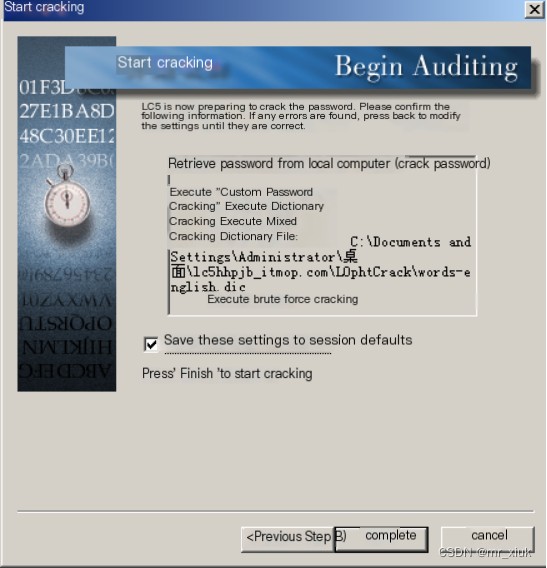
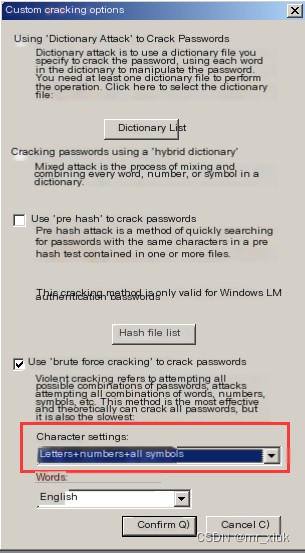
Start the activation success tutorial (Note: Select the appropriate method of activation success tutorial depending on requirements)
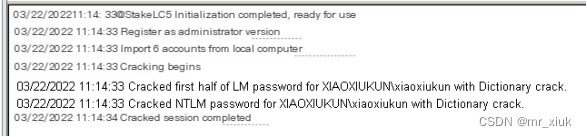
Verify if it is correct:
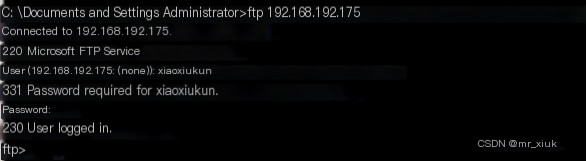
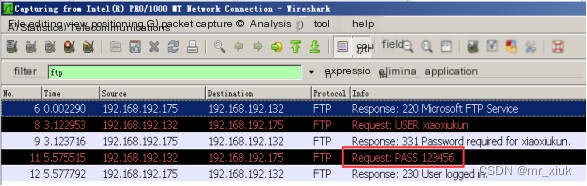
Successful login


