Target Address: https://xj.edisec.net/challenges/52
Background: Xiao Zhang’s company recently suffered a phishing email attack. Multiple employee workstations were compromised and used as jump servers to attack the internal network system. Please analyze the data samples backed up by Xiao Zhang to perform a source analysis of the phishing email and the compromised internal systems.
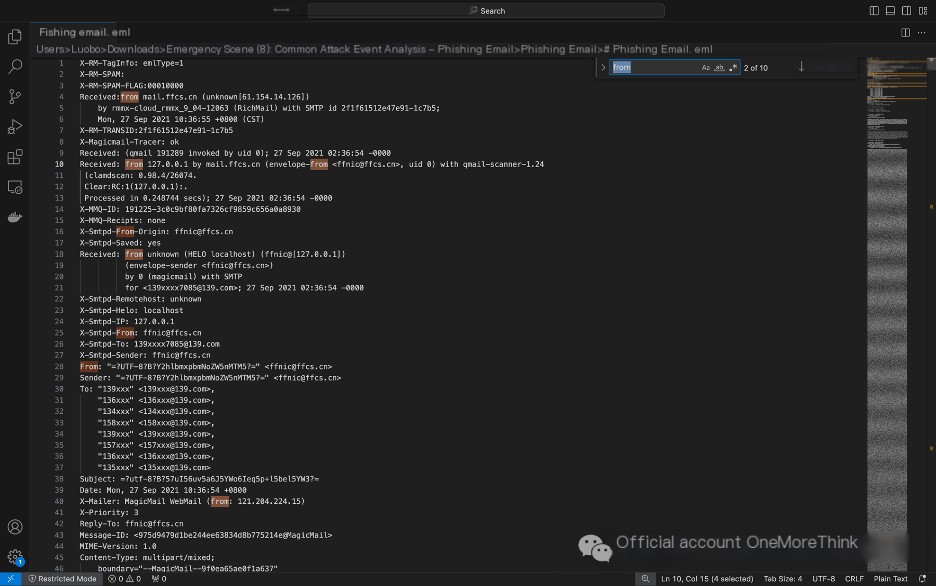
Analyzing Phishing Emails to Identify the Hacker’s IP Address
Search for from in the eml file of the phishing email; the last from is the IP address used by the hacker to send the phishing email: 121.204.224.15.
 />
/>
flag{121.204.224.15}
II. Analyze to obtain the control-end IP address of the Trojan program used in the hacker’s phishing email
Content-Transfer-Encoding: base64 indicates that the email body uses base64 encoding.
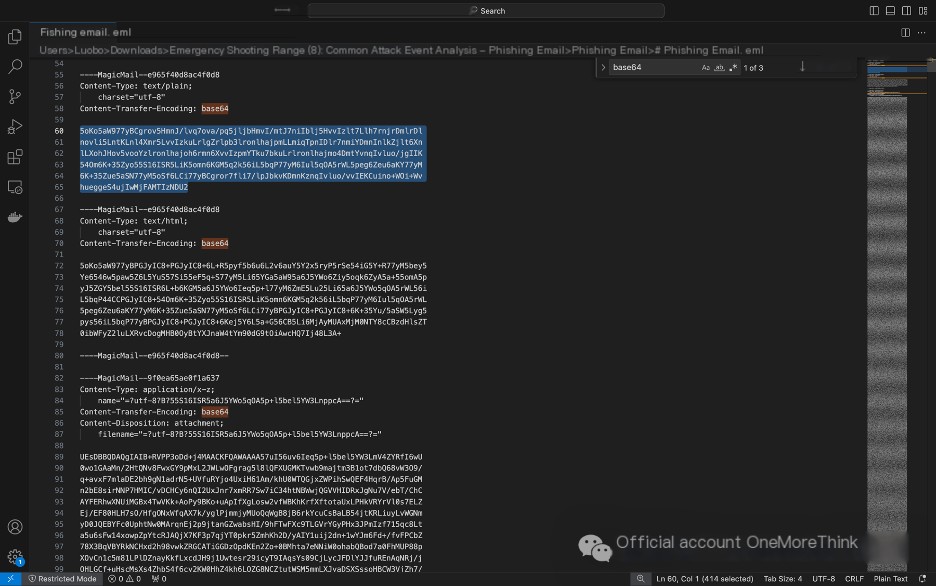 />
/>
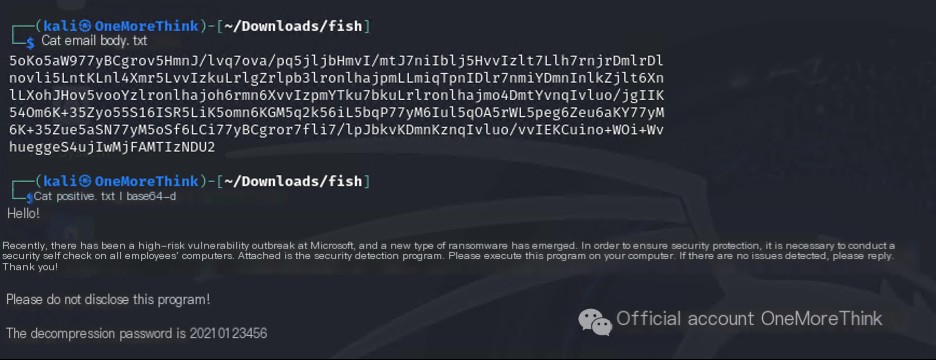
Save the email body to a txt file and use the command cat email_body.txt | base64 -d to decode it. Obtain the email body content, and find that the extraction password for the compressed file is: 2021@123456.
Save the email attachment to a txt file and use the command cat phishing_attachment.txt | base64 -d | less to decode and view it. From the PK at the beginning of the file, we know that the email attachment is a zip compressed file, because PK is the abbreviation of the name of the author who invented the zip compression format.
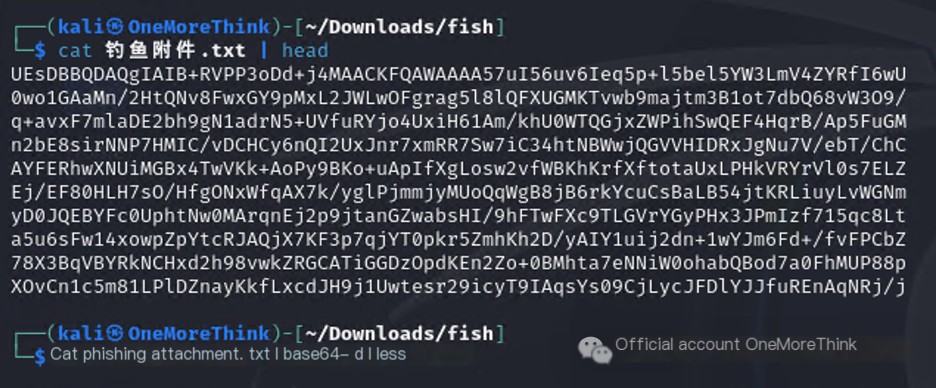
Use the command cat phishing_attachment.txt | base64 -d > phishing_attachment.zip to decode and save it to a zip file, and then decompress it with the password to finally obtain the program: Terminal Self-Check Tool.exe.
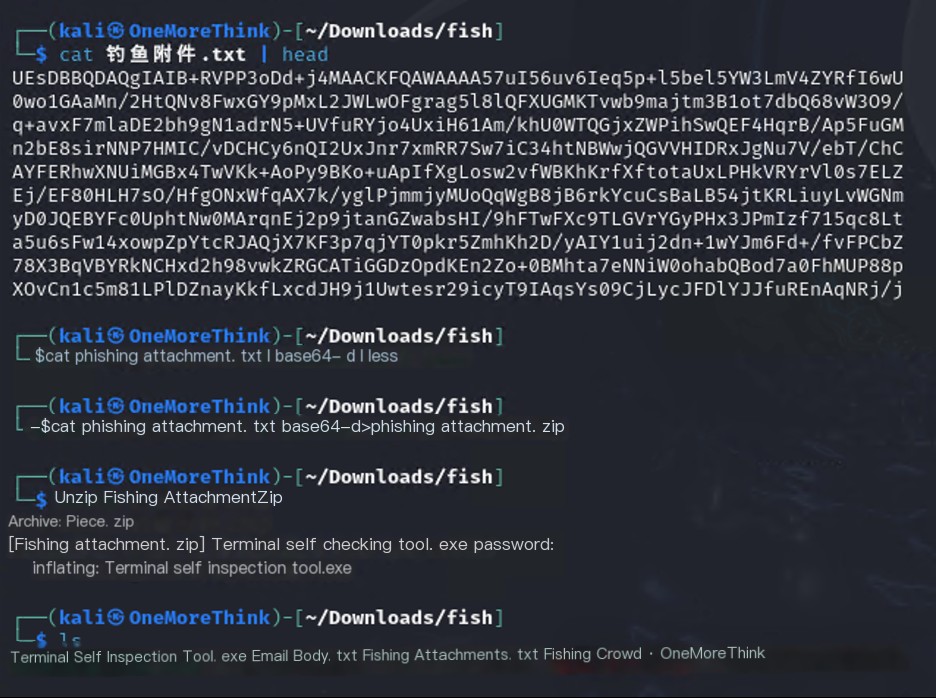
Upload the program to a file sandbox for analysis to obtain the control-end IP address of the Trojan program: 107.16.111.57.
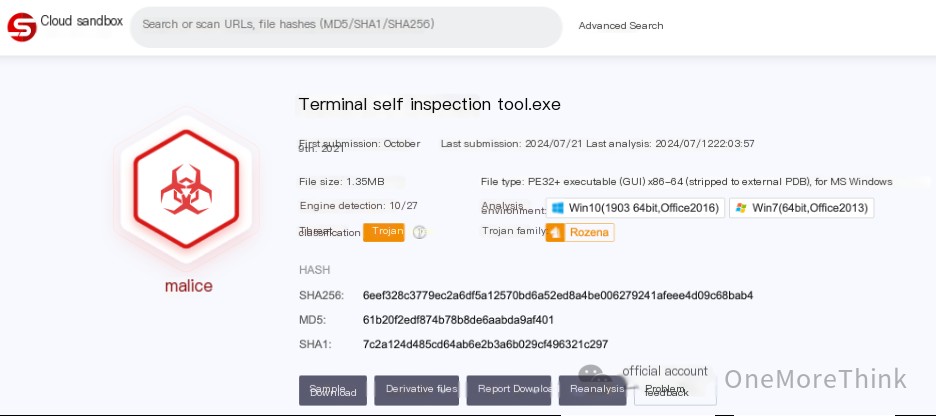
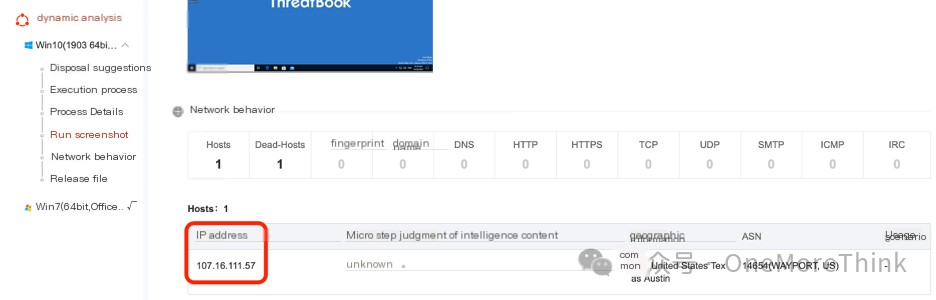
flag{107.16.111.57}
III. The hacker created a webshell on the compromised server. Analyze to obtain the webshell filename.
Analyze the files in /var/www/html/ using Dshield, and find the webshell filename: /var/www/html/admin/ebak/ReData.php.
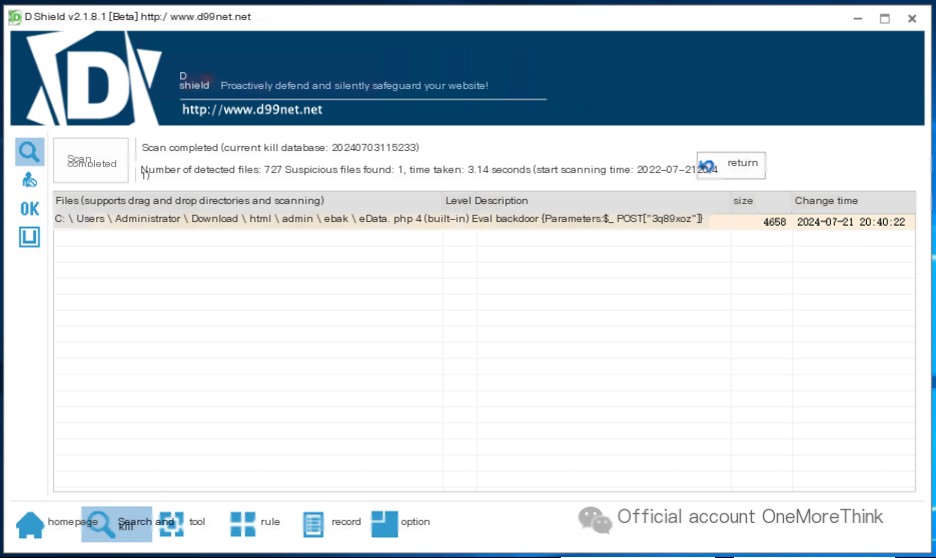
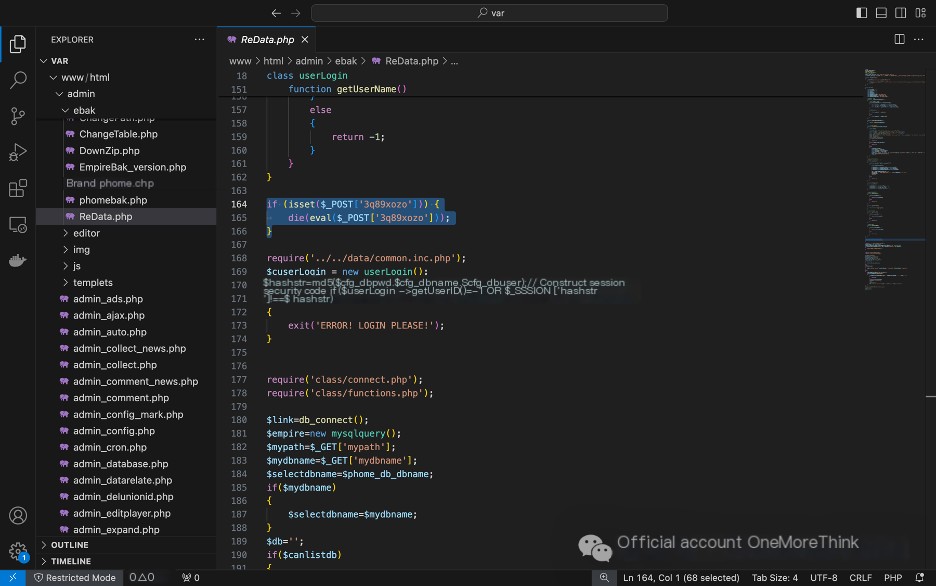
flag{/var/www/html/admin/ebak/ReData.php}
IV. The hacker created a covert communication tunnel using an internal network proxy on the compromised server. Analyze to obtain the filename of this tunnel program.
A suspected tunnel proxy configuration was found in /var/tmp/proc/my.conf.
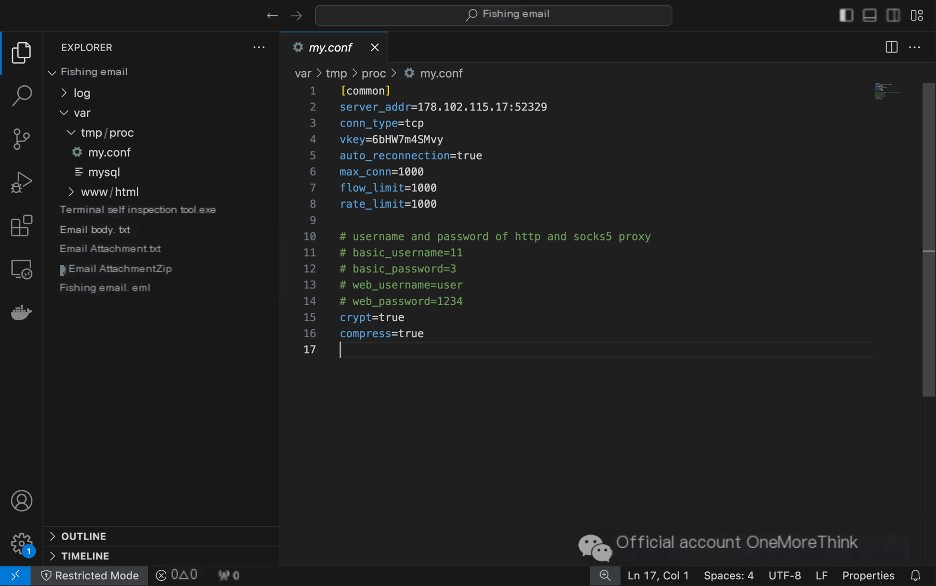
Use the command ./mysql -h to view the help information for the /var/tmp/proc/mysql program and confirm that it is a tunnel program.
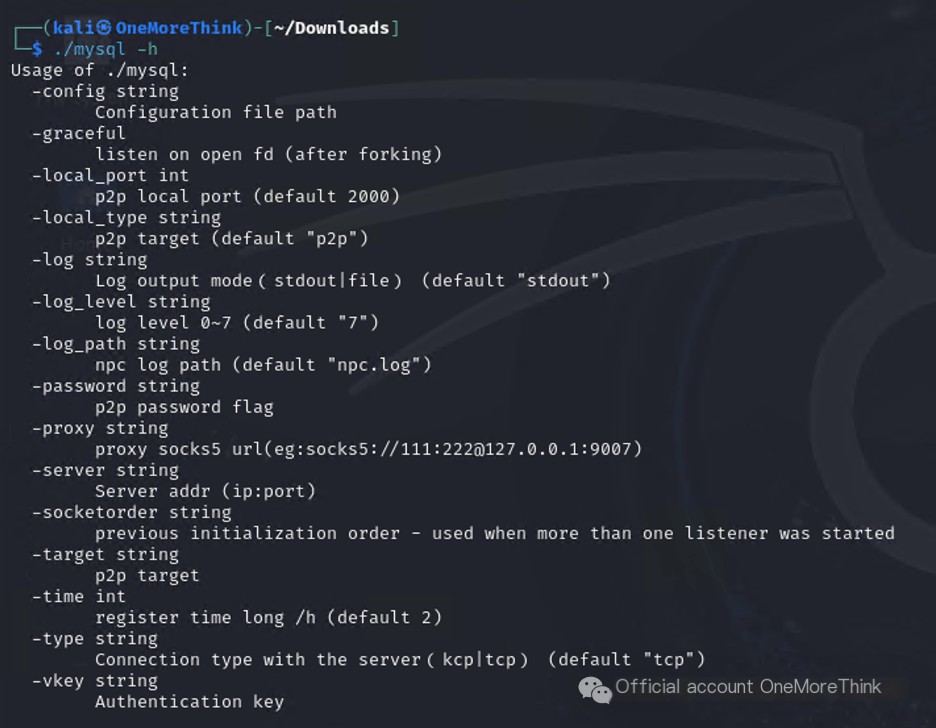
flag{/var/tmp/proc/mysql}


