1. Purpose of the experiment
- Be familiar with and master the basic use of Wireshark;
- Understand the interaction between network protocol entities and the exchange of messages;
- Analyze Ethernet frames, MAC addresses and ARP protocols.
2. Experimental Environment
The computer connected to the Internet has a Windows operating system and is installed with software such as Wireshark and IE.
3 Preliminary Knowledge
3.1 Wireshark installation
Download address: https://www.wireshark.org/#download
Pay attention to the operating system version, especially the difference between 32-bit operating system and 64-bit operating system.
Just choose the default settings during installation.
3.2 Packet Sniffer
To deeply understand network protocols, we need to observe their working process and use them, that is, observe the message sequence exchanged between two protocol entities, explore the details of protocol operation, make protocol entities perform certain actions, and observe these actions and their effects. This observation can be done in a simulation environment or in a real network environment such as the Internet.
The basic tool for observing the messages exchanged between running protocol entities is called a packet sniffer, also known as a packet capturer. As the name suggests, a packet sniffer captures (sniffs) the messages sent and received by your computer.
Figure 1 shows the structure of a packet sniffer.
Figure 1
On the right side of Figure 1 are protocols and applications (such as web browsers and FTP clients) running normally on a computer. A packet sniffer (the part in the dotted box) consists of two main parts: the first is a packet capturer, whose function is to capture a copy of every link layer frame sent and received by the computer; the second component is a packet analyzer, whose function is to analyze and display the contents of all fields of the protocol message (it can identify various network protocols currently in use).
3.3 Introduction to Wireshark
Wireshark is a packet sniffer that can run on Windows, UNIX, Linux and other operating systems. It is open source free software.
When you run the Wireshark program, its graphical user interface is shown in Figure 2. Initially, there is no data displayed in the windows. The Wireshark interface has five main components:
Figure 2
Command menus: The command menu is located at the top of the window and is a standard drop-down menu.
Protocol filter box (display filter specification): Fill in the name of a certain protocol here. Wireshark will filter the packets in the packet list window based on this and only display the packets you need.
Listing of captured packets: Displays the contents of captured packets in rows, including: packet number, capture time, source address and destination address, protocol type, and protocol information. Click a column name to sort the packet list by the specified column. The protocol type is the type of the highest layer protocol for sending or receiving packets.
Details of selected packet header: Displays the header details of the selected packet in the captured packet list window, including the header information of each layer of the packet. To view the information of a layer, double-click the corresponding layer or click the “+” at the beginning of the layer.
Packet content window: Displays the complete contents of the captured frame in hexadecimal (left) and ASCII (right) formats.
4. Experimental Procedure
4.1 Basic operations of wireshark
(1) Check your IP address and MAC address. In Windows, use the command prompt to check. Enter CMD in the Run window, or open the command prompt in the Start menu “Windows Accessories”/”Windows System”. Enter ipconfig -all in the command prompt to check the local physical address and IP address. In MAC, go to System Preferences – Network – Select Connected Network to check the local physical address and IP address.
(2) Start the Wireshark software and select the network card interface on which you want to capture data packets.
(3) Stop capturing after a few seconds and observe the captured data packets.
(4) In the filter conditions, select to view the data packets sent from your own IP address, use the filter condition “ip.src==IP address found in step 2”, and check in the packet details window whether the source MAC address is the physical address of the local machine found in step 2.
(5) Reset the filter conditions, select to view the data packets received by your MAC address, use the filter condition “eth.dst == physical address found in step 2” (note that the hexadecimal characters in the address are separated by colons), and check whether the destination IP address is your own IP address in the packet details window.
(6) Considerations:
Every time I send or receive a data packet, do my IP address and MAC always correspond?
Try to write a rule to find all HTTP protocol packets.
Try writing a rule to find all DNS packets sent from your own IP address.
4.2 Packet structure of ARP protocol
(1) Enter arp in the command prompt to view the parameters of the arp tool. Enter arp -a to view the local arp cache table and record the following table (if not enough, you can add rows):
Enter arp -d (if it does not work, find cmd.exe in C:/windows/system32, right-click and select “Run as administrator”) to delete the local arp cache table. Use arp -a to view the arp cache table again to see what changes have occurred.
ARP packets are reduced
Enter “ping gateway address” and check the arp cache table again to see what changes have occurred. Based on the results of the above experiments, try to analyze the working mode of the arp cache table.
(4) Run the Wireshark packet capture and analysis tool to start capturing. Before or during capturing, run arp -d to clear the ARP cache table and then enter “ping gateway address” in the command prompt. After a while, stop capturing and observe the captured data packets.
Note : In many cases, you do not need to “ping the gateway address”. The system will automatically run the ARP protocol and obtain the physical address of the gateway. Therefore, when you check the cache table after deleting it, you will find that the ARP entry of the gateway still exists.
(5) In the filter column, set the filter condition to arp data packets.
(6) Check the ARP data packet sent from the local MAC address, check the link layer frame structure and ARP protocol packet structure of the first packet of the captured data packet, take a screenshot and record the following table.
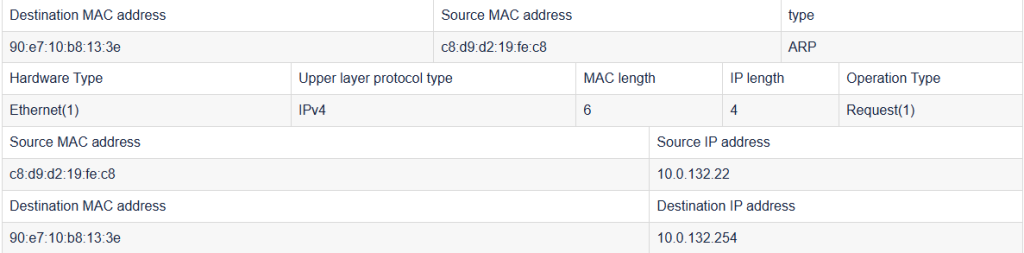
Consider and answer the following questions based on the captured packet information:
What is the destination MAC address in the arp packet structure? Why is it this value?
90:e7:10:b8:13:3e After the destination host receives the ARP request, it will send an ARP reply containing the MAC address of the destination host.
What are the functions of the hardware type, upper layer protocol type, and operation type in the arp packet structure?
Hardware type : This field has 2 bytes and is used to indicate what type of network the ARP packet is running on. For example, if it is the most commonly used Ethernet, the value is 1.
Protocol type : This field has 2 bytes and is used to indicate the type of upper-layer protocol using the ARP packet. For example, if it is the most commonly used IPv4 protocol, the value is 32.
Operation Type : This field has 2 bytes and is used to indicate the type of the ARP packet. Currently, there are only two types: ARP request (value is 1) and ARP reply (value is 2).
Check the ARP data packet sent from the gateway MAC address, check the data link layer frame structure and ARP protocol packet structure of the captured data packet, take a screenshot and record the following table.
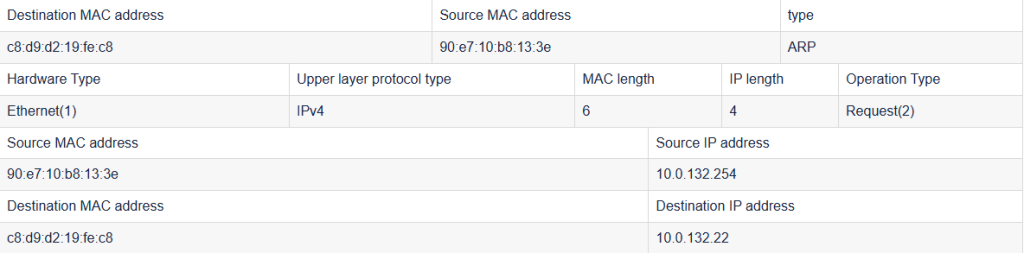
Answer the following questions based on the captured packet information:
Judging from the MAC address in the frame header, who sent this data frame to whom?
The host sends to the local machine
What is the change between the operation type field in the arp packet structure and the corresponding field in step ( 7) ?
Request(1)→Request(2)
The source IP address and MAC address are swapped with the destination IP address and MAC address
(6) Think: Based on all the experimental results of today’s experiment,
What are the triggering conditions for the ARP protocol to work?
In Ethernet, when a host communicates directly with another host, it must know the MAC address of the target host. But how is this target MAC address obtained? It is obtained through the address resolution protocol. The so-called “address resolution” is the process of the host converting the target IP address into the target MAC address before sending a frame. The basic function of the ARP protocol is to query the MAC address of the target device through the IP address of the target device to ensure smooth communication.
Analyze how the complete working process of the ARP protocol works in the host?
- Each host will have its own ARP cache area to establish an ARP list to indicate the correspondence between IP address and MAC address.
- When the source host wants to send data, it first checks whether the MAC address of the destination host in the ARP list corresponds to the IP address. If yes, it will send the data directly. If not, it will send the data to the local host. All hosts on the network segment send ARP packets.
- When all hosts in this network receive the ARP packet, they first check whether the IP address in the packet is their own IP address. If not, they ignore the packet. If it is, they first take out the IP and MAC address of the source host from the packet and write them into the ARP list. If it already exists, they overwrite it. Then they write their own MAC address into the ARP response packet to tell the source host that they are the MAC address they are looking for.
- After the source host receives the ARP response packet, it writes the IP and MAC address of the destination host into the ARP list and uses this information to send data. If the source host has not received the ARP response packet, it means that the ARP query has failed.
What are the possible security risks of the ARP protocol?
- Fake ARP reply
- Peer-to-peer fake query
- Automatic timed ARP spoofing
- Interference with the gateway
- Estimated ARP resolution time



