What is ARP Request Storm?
Before knowing the ARP request storm, let’s take a look at ARP. ARP, or Address Resolution Protocol, operates at the data link layer, interfacing directly with hardware to provide essential services to the higher layers. Given that LAN communication relies on MAC addresses and many programs utilize IP addresses, there needs to be a mapping from IP to MAC addresses. IP data packets are typically transmitted over Ethernet, which uses 48-bit Ethernet addresses, unlike the 32-bit IP addresses that Ethernet devices cannot natively recognize.
Therefore, the IP driver must convert the IP destination address into an Ethernet destination address. In Ethernet, a host must know the target host’s MAC address to communicate directly with it. This critical information is obtained through the Address Resolution Protocol. “Address resolution” involves converting the target IP address into the target MAC address before sending a frame. The fundamental role of the ARP protocol is to query the MAC address of the target device using its IP address to ensure seamless communication.
However, problems can arise, such as an ARP request storm, where excessive ARP requests flood the network, potentially disrupting communication and degrading network performance.
In a local area network, what is actually transmitted in the network is a “frame”, which contains the MAC address of the target host. When ARP works, it sends out an Ethernet broadcast packet, and the destination host responds with a data packet containing an IP and Ethernet address pair. If the number of request packets and response packets differs too much, this is abnormal.
Analyze ARP Request Storm in Network Diagnostics
In the diagnostic settings of the Cole Network Analysis System, ARP is also listed separately, including too many ARP requests without response, ARP scanning, and ARP request storm. As shown in Figure 1,
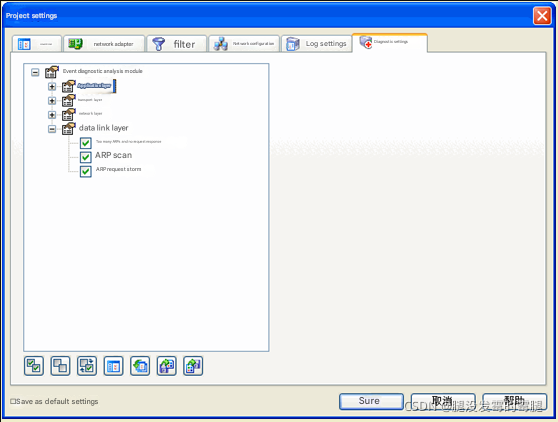
In Figure 1, we can see some information settings about ARP in the diagnosis of the Kelai network analysis system.
We use the Kelai network analysis system to analyze and diagnose the captured data. The network diagnostic information can be seen from the expert diagnosis view, as shown in Figure 2.
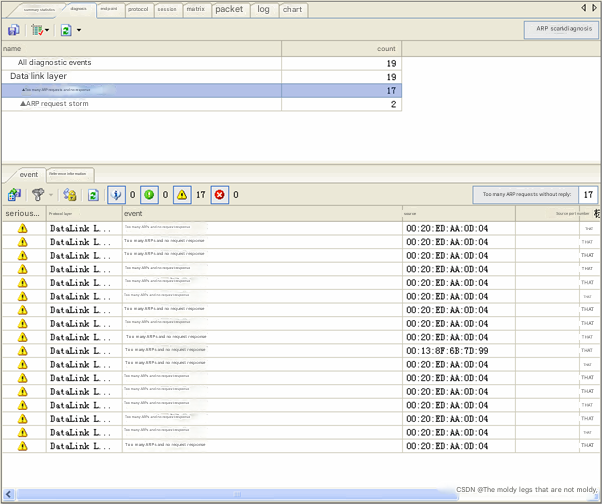
In Figure 2, we can see that there is a fault in the network, too many ARP requests without response, and an ARP request storm, which is abnormal. We can know the source and target of the fault in the event information under the diagnostic view and locate the source and target.
In Figure 2, the source is 00:20:ED:AA:0D:04. We locate the source and view the packet view, as shown in Figure 3.
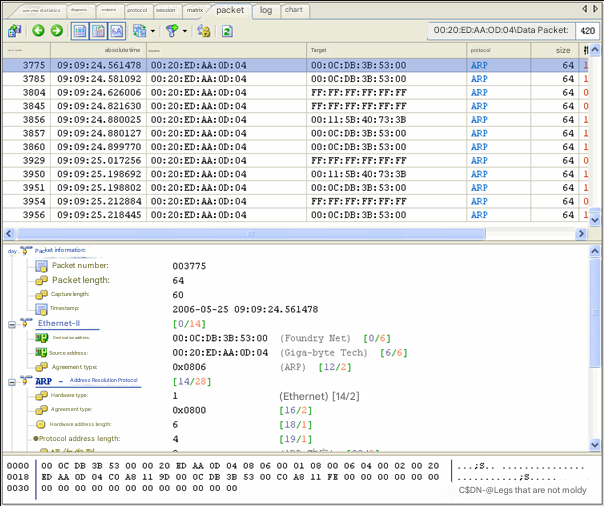
From Figure 3, we can see that the ARP request broadcast packets are almost always sent by 00:20:ED:AA:0D:04.
We click on the protocol view and see that the ARP request is much larger than the response, as shown in Figure 4.
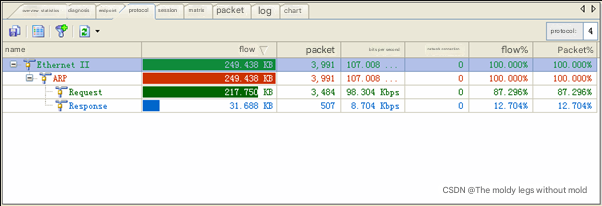
The detailed information on the ARP protocol can be clearly seen in Figure 3. The difference between the ARP request and the response is too large, which is impossible in a normal network.
Conclusion
Through the above analysis, we know that the host with MAC address 00:20:ED:AA:0D:04 may be under ARP attack. We disconnected the host from the Internet and used the Colai network analysis system to analyze the network. We found that the network was normal. Then we checked the faulty host separately and solved the problem.



