Introductory Note
The xHunt campaign has been active since July 2018, primarily targeting the government of Kuwait and shipping transportation organizations. Recently, researchers identified that xHunt attackers targeted a Microsoft Exchange server belonging to a Kuwaiti organization. While we cannot confirm how the attackers initially breached the Exchange server, based on the creation timestamp of tasks related to the incident, we found that the attackers had access to the Exchange server as early as August 22, 2019. During this campaign, the attackers deployed two backdoors: one called TriFive and a variant of Snugy (a web shell we refer to as BumbleBee).
TriFive and Snugy backdoors are fundamentally PowerShell scripts that facilitate unauthorized access to the compromised Exchange server and use different C2 (command and control) channels for communication. The TriFive backdoor utilizes an email-based channel that can draft emails in the deleted items folder of a compromised email account using Exchange Web Services (EWS). The Snugy backdoor, on the other hand, employs DNS tunneling for command and control.
For a detailed analysis, please continue reading below.
TriFive and Snugy Backdoors
In September 2020, we discovered that xHunt attackers had breached an organization in Kuwait. The behavior indicating command execution through the IIS process w3wp.exe was observed on the organization’s Exchange server. When sending these commands, the attackers used a web shell called BumbleBee, which had already been installed on the compromised server. In analyzing server logs, we identified two scheduled tasks created by the attackers, both executing malicious PowerShell scripts. We cannot yet determine if the attackers used any of these scripts to install the web shell, but we believe they accessed the server prior to the logging event.
The attackers created two tasks on the Exchange server, both named ResolutionHosts, located in the c:\Windows\System32\tasks\Microsoft\Windows\WDI folder. By default, this folder on Windows systems also stores a legitimate task named ResolutionHost, which, as shown in the figure, relates to the Windows Diagnostic Infrastructure (WDI) for interactive troubleshooting of system issues. We suspect the attackers chose this task name to conceal their activities.
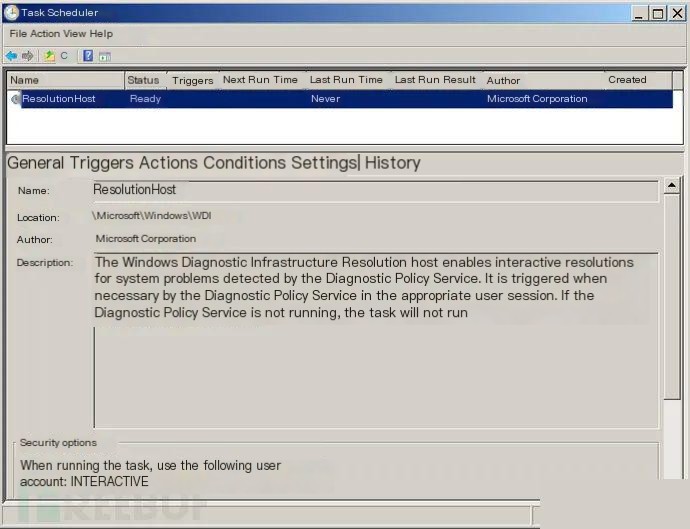
On August 28, 2019, and October 22, 2019, the attackers created the ResolutionHosts tasks to run two distinct PowerShell-based backdoors. They used these scheduled tasks as a persistence mechanism since the scheduled jobs repeatedly run these scripts at different intervals, as shown in the figure below. The tasks attempt to execute splwow64.ps1 and OfficeIntegrator.ps1, which are our so-called TriFive backdoor and a variant called CASHY200 (Snugy). These scripts are stored in separate folders on the system, likely to avoid both backdoors being detected and deleted simultaneously.
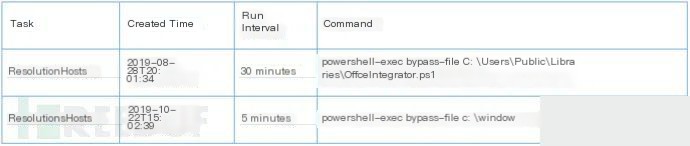
As shown in the figure, the TriFive backdoor runs every five minutes, while the Snugy backdoor runs every thirty minutes. We cannot confirm the reasons behind the interval difference, though it might relate to the stealthiness of the respective C2 channels. For instance, Snugy’s DNS tunneling C2 channel may necessitate longer intervals than TriFive’s email-based channel due to increased detectability risks.
How the attackers created the ResolutionHosts tasks remains unknown. However, we know when installing Snugy samples on other systems, the attackers used batch scripts to set up scheduled tasks named SystemDataProvider and CacheTask. For instance, the batch script below creates and runs a SystemDataProvider task, ultimately executing a Snugy sample called xpsrchvw.ps1:
schtasks /create /sc MINUTE /mo 5 /tn “\Microsoft\Windows\SideShow\SystemDataProvider” /tr “powershell -exec bypass -file C:\Windows\Temp\xpsrchvw.ps1” /ru SYSTEM & schtasks /run /tn “\Microsoft\Windows\SideShow\SystemDataProvider” TriFive Backdoor TriFive is a previously undetected PowerShell backdoor installed by xHunt attackers on compromised Exchange servers, executing via a scheduled task every five minutes. TriFive gains persistent backdoor access by logging into legitimate user mailboxes and retrieving PowerShell scripts from email drafts stored in the “Deleted Items” folder. The samples utilize legitimate account names and credentials of the target organization, indicating that credentials were acquired before installing the TriFive backdoor.
An email-based C2 was also employed in the Hisoka tool, although it retained drafts in the draft folder, whereas TriFive saved them in the “Deleted Items” folder.
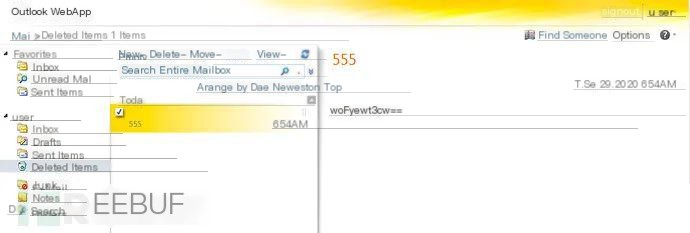
To issue commands to the backdoor, attackers need to log into the same legitimate email account and create a draft with “555” as the subject, containing commands in encrypted and Base64 format. The figure below provides an example email draft with the subject “555” and the content “woFyeWt3cw==,” which will be executed by PowerShell:
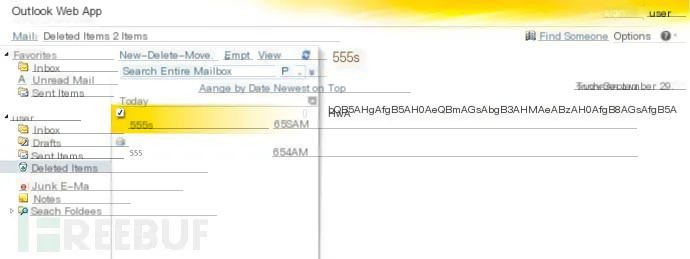
To execute commands provided by the attacker, the PowerShell script logs into the Exchange server’s legitimate email account and checks the “Deleted Items” folder for emails with the subject line “555.” The script opens the draft email, decodes the Base64 encoded message content, decrypts it by subtracting 10 from each character, and uses the built-in PowerShell cmdlet Invoke Expression (iex) to generate plaintext. Upon executing provided PowerShell code, the script encrypts the result by adding 10 to each character and Base64 encoding the ciphertext. It then sends the command results back to attackers, setting the encoded ciphertext as the draft email message body in the “Deleted Items” folder under the subject “555.” The figure below shows a sample draft email in the “Deleted Items” folder created by the TriFive script, with the subject “555” and message content “bQB5AHgAfgB5AH0AeQBmAGsAbgB3AHMAeABzAH0AfgB8AGsAfgB5AHwA”:
The TriFive PowerShell script doesn’t persist by looping through code; it achieves persistence through the previously mentioned ResolutionsHosts scheduled task.
Snugy Backdoor
The OfficeIntegrator.ps1 file found in the ResolutionHosts task is a PowerShell-based backdoor we refer to as Snugy, allowing attackers to identify hostnames of target systems and execute commands. Snugy is a variant of the CASHY200 backdoor, which attackers previously used in xHunt activities. In July 2019, Trend Micro created a detection signature for this backdoor, Backdoor.PS1.NETERO.A, indicating that this variant of CASHY200 has been in existence for over a year.
Snugy samples randomly choose from the following domains as their C2 domains:
hotsoft[.]icu
uplearn[.]top
lidarcc[.]icu
deman1[.]icuSimilar to earlier variants of the CASHY200 backdoor, Snugy variants use the following command to connect with custom domains and attempt to resolve the domain before sending ICMP requests:
cmd /c ping -n 1 . Snugy uses the following regex to extract IP addresses from the ping command output: \b(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\bBelow is the command and control server for processing Snugy instructions:
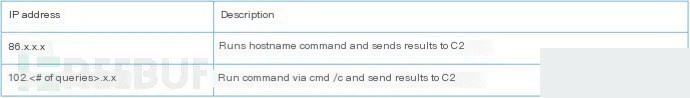
Snugy-generated subdomains contain a communication type field, defining the order of elements in the data section, as outlined in the C2 domain structure:
. xHunt Associated Infrastructure
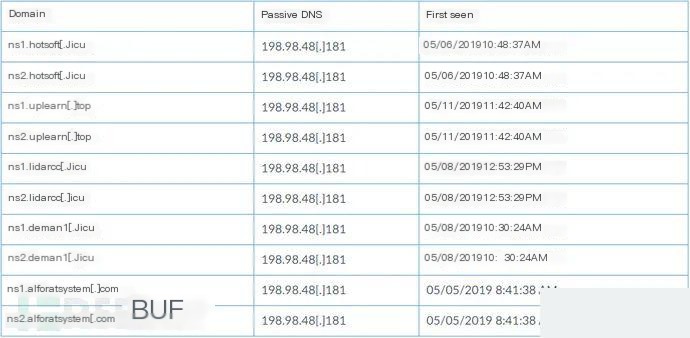
Indicators of Compromise (IoC)
TriFive Samples:
407e5fe4f6977dd27bc0050b2ee8f04b398e9bd28edd9d4604b782a945f8120f
Snugy Samples:
c18985a949cada3b41919c2da274e0ffa6e2c8c9fb45bade55c1e3b6ee9e1393 6c13084f213416089beec7d49f0ef40fea3d28207047385dda4599517b56e127 efaa5a87afbb18fc63dbf4527ca34b6d376f14414aa1e7eb962485c45bf38372 a4a0ec94dd681c030d66e879ff475ca76668acc46545bbaff49b20e17683f99c
Snugy C2 Domains:
deman1[.]icu
hotsoft[.]icu
uplearn[.]top
lidarcc[.]icu
sharepoint-web[.]com
Scheduled Task Names:
ResolutionHosts
ResolutionHosts
SystemDataProvider
CacheTask-


