During forensic investigations, the Windows Recycle Bin is considered an important source of evidence because any items deleted through File Explorer and any Recycle Bin-aware programs are initially placed in the Recycle Bin. The Recycle Bin retains valuable information related to deleted items, such as the name of the deleted item, the original location of the item before deletion, the size of the deleted item, and the date and time the item was deleted.
Windows Recycle Bin Files
The Windows Recycle Bin was first introduced in Windows 95 and continues through Windows 11. The Recycle Bin is a temporary storage for items deleted by users. Users can then choose to permanently delete these items or restore them if they were deleted by mistake.
This makes it a very valuable file during investigations because we have the potential to discover steps taken by malware or attackers at specific times, such as deleting files or folders.
Download RBcmd for Windows Recycle Bin
We will use Eric Zimmerman’s RBcmd tool to parse Recycle Bin data.
https://ericzimmerman.github.io
C:\Users\Administrator\Downloads\RBcmd>RBCmd.exe -h Description: RBCmd version 1.5.0.0 Author: Eric Zimmerman ([email protected]) https://github.com/EricZimmerman/RBCmd Examples: RBCmd.exe -f "C:\Temp\INFO2" RBCmd.exe -f "C:\Temp\$I3VPA17" --csv "D:\csvOutput" RBCmd.exe -d "C:\Temp" --csv "c:\temp" Short options (single letter) are prefixed with a single dash. Long commands are prefixed with two dashes Usage: RBCmd [options] Options: -d Directory to process recursively. This option or -f is required -f File to process. This option or -d is required -q Only show the names of files being processed, not all output. Helps speed up exporting to JSON and/or CSV --csv Directory to save CSV formatted results. Be sure to enclose the full path in double quotes --csvf File name to save CSV formatted results. If present, overrides the default name --dt Custom date/time format to use when displaying timestamps. For options, see https://goo.gl/CNVq0k. Default is: yyyy-MM-dd HH:mm:ss [Default: yyyy-MM-dd HH:mm:ss] --debug Show debug information during processing [Default: False] --trace Show trace information during processing [Default: False] --version Show version information -?, -h, --help Show help and usage information
Unhide Files in Windows Recycle Bin
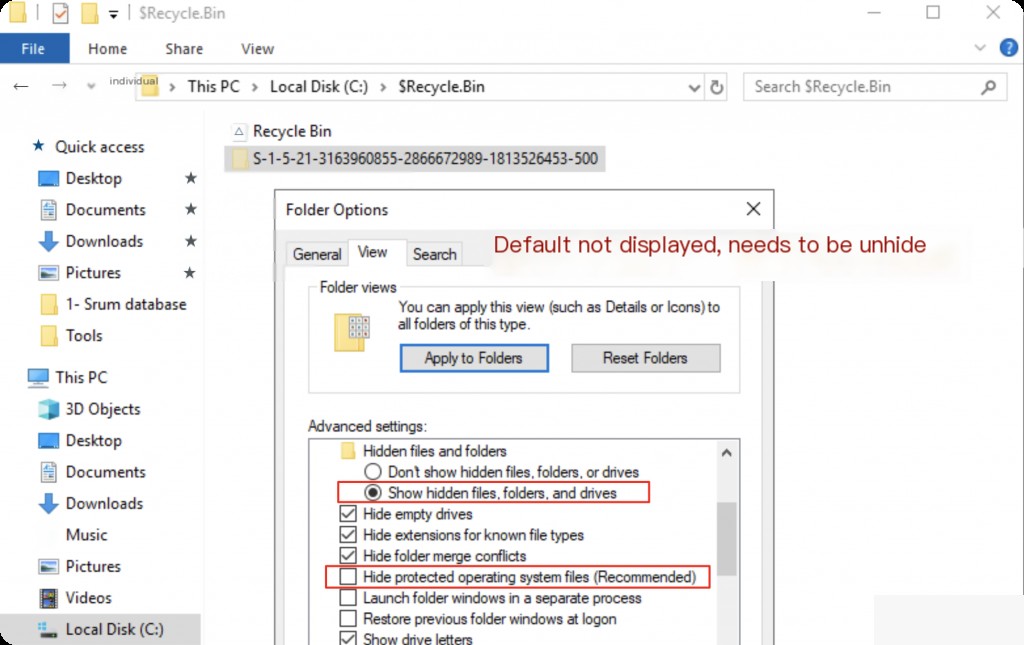
Files in the Recycle Bin directory are typically hidden and marked as system files. By default, Windows does not display these hidden system files. To view these files, you need to adjust the File Explorer settings to show hidden and system files:
- Open File Explorer.
- Click the “View” tab.
- Select “Options,” then in the Folder Options dialog that appears, click the “View” tab.
- In the “Advanced settings” list, uncheck “Hide protected operating system files (Recommended)” and select “Show hidden files, folders, and drives.”
- Apply the changes and confirm.
RBcmd Analyze Recycle Bin Data
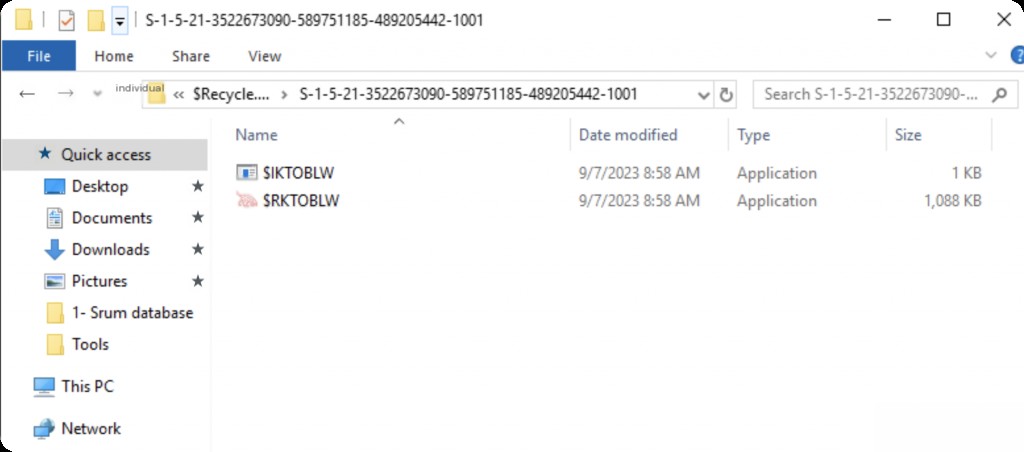
Recycle Bin artifacts are stored in files beginning with “$I,” located in the user’s SID subfolder within the Recycle Bin directory. The full path is as follows:
C:\$Recycle.Bin\{SID}\$I
These $I files contain metadata such as file path, size, and deletion timestamp. For each $I file, if the item has not been permanently deleted, there is a corresponding $R file. These $R files are the actual content of the deleted files themselves.
We can view the files in the Recycle Bin, use RBcmd to parse, and obtain data for analysis.
RBCmd.exe -d ./RecycleBinArtifacts --csv ./
After parsing, open the csv file in timeline explorer.
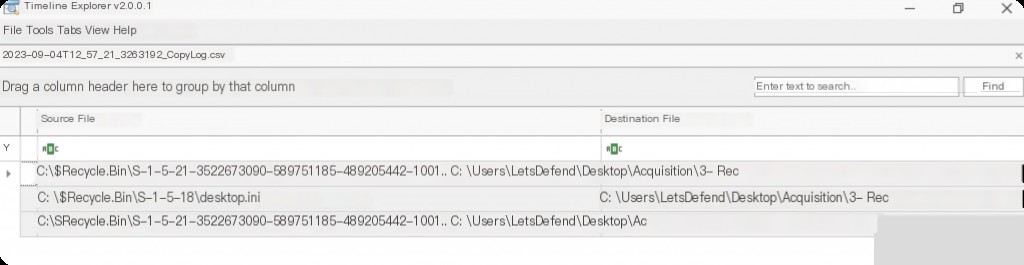
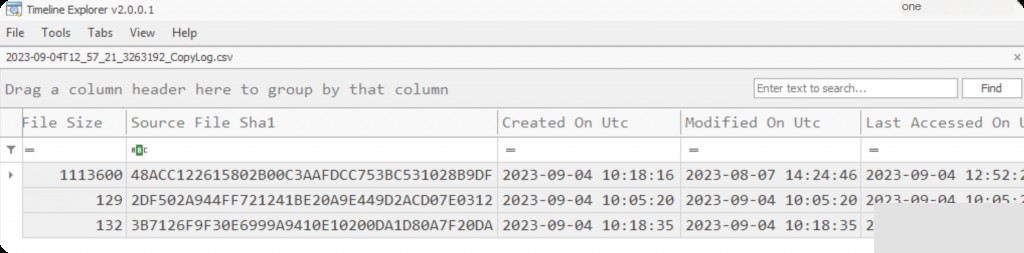
We can see the UTC time when the file was deleted, the original file name and full path, as well as the file size and hash.
Search Index
Windows Search is a desktop search platform initially introduced by Microsoft in Windows Vista and continued in later versions of Windows (Windows 7, 8, and 10). The service “provides content indexing, property caching, and search results for files, emails, and other content.” In other words, the Windows Search service acts as an internal dictionary running in the background, collecting and indexing the system’s content.
The search index database is located at:
C:\ProgramData\Microsoft\Search\Data\Applications\Windows
We can obtain partial content of different file types (such as docx, pdf, txt, etc.), browser history, even if the history has been deleted from the browser. These records provide perfect evidence for internal threat forensics.
Download SIDR
We will use the SIDR tool, which will effectively parse the search index database and output in csv format.
https://github.com/strozfriedberg/sidr
First, we obtain the search index database, then use the SIDR tool to parse it.
C:\Users\Administrator>sidr.exe -h
Copyright 2023, Aon
Usage: sidr.exe [options]
Arguments:
Path to the input directory (will recursively scan Windows.edb and Windows.db)
Options:
-f, --format Output report format [Default: json] [Possible values: json, csv]
-r, --report-type Send output results to file or stdout [Default: send to file] [Possible values: send to file, send to stdout]
-o, --output-dir Path to the directory where the report will be created (will be created if it does not exist). Default is the current directory
-h, --help Print help (use '--help' for more)
-V, --version Print version
SIDR Analyze Search Index
Copy the Windows directory of the search index to the same directory as sidr.exe to execute.
sidr.exe "./windows" -f csv -o ./
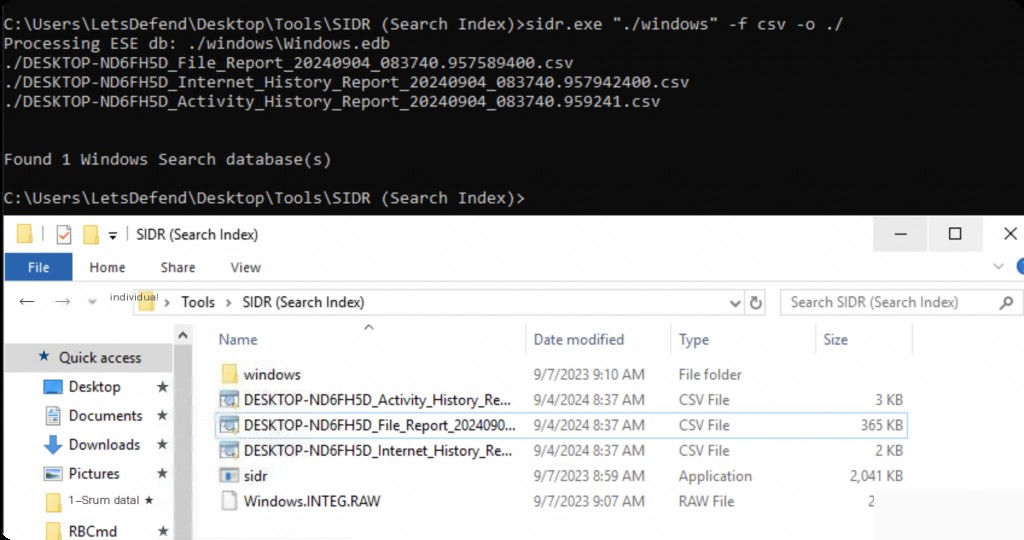
The first path is the directory where we obtained the search index. The path after “-o” is where the results are stored. The “-f” switch specifies the output format. The default is json, but we use csv for easier analysis.
FileReport and internet records are the files that help us the most in forensics, here we open the csv file with timeline explorer.
FileReport Analysis
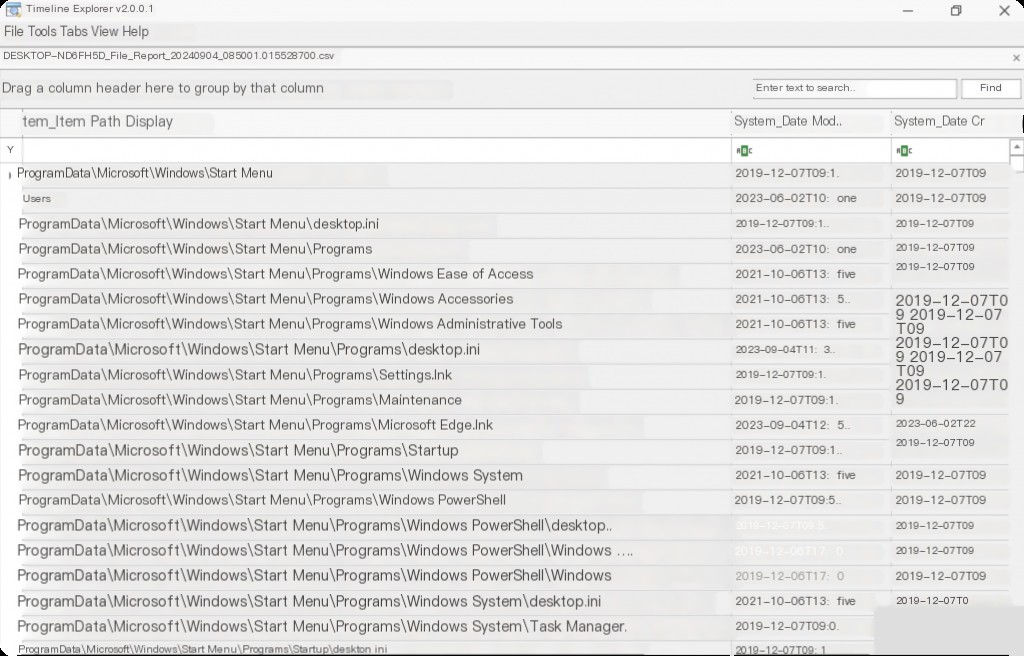
In the FileReport csv, we get the file name, modification, creation, access times, size, owner, the time it was indexed by Windows and added to the database, and most importantly, part of the file’s content. This tab is named “System Search Auto Summary.”
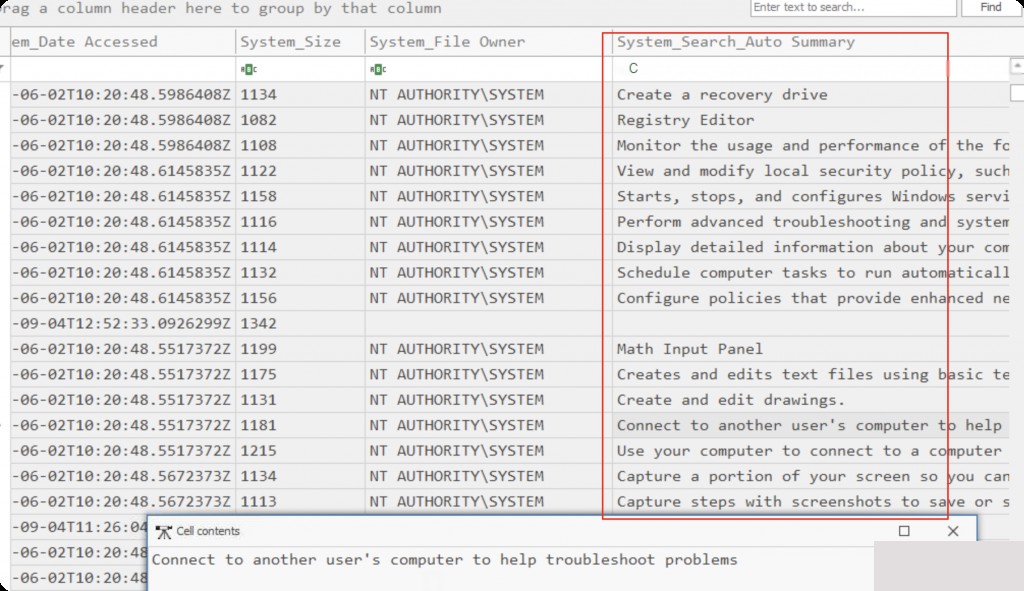
Suppose we are interested in files that have been permanently deleted from the system. If the file and its content were indexed, we can recover its content. Note that the search index retains records of deleted files for a few days, after which they are also removed from the database.
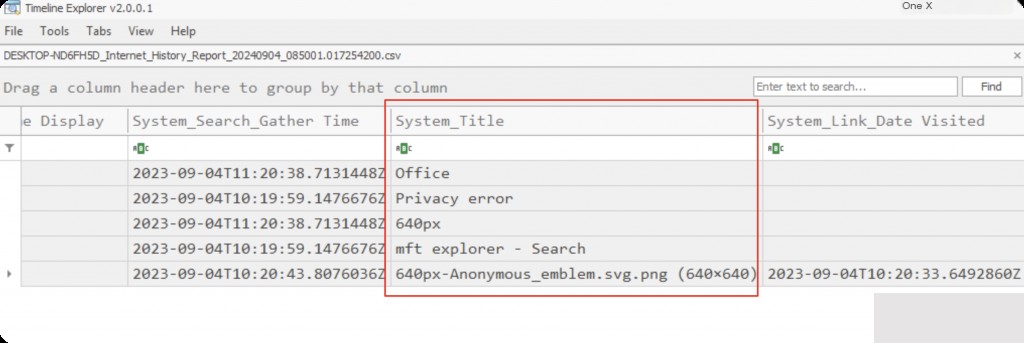
Internet History Report Analysis
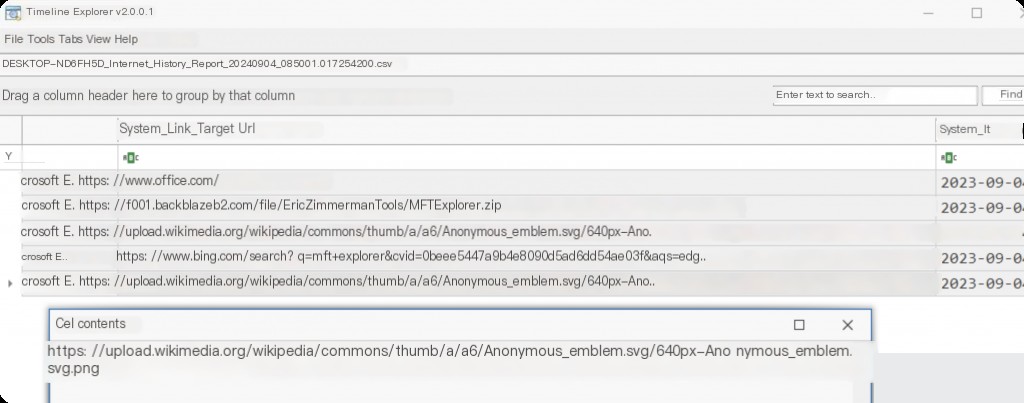
We can see the URLs and the access times of the URLs. It even records the title names of the web pages accessed.
Windows Search can be a valuable source of evidence during forensic processes. The database contains a wealth of data related to files, images, videos, directories, and other file types on the Windows system. What makes Windows Search even more valuable is that users may not be aware of it, as the service is enabled by default to run in the background, collecting and indexing potential evidence without the user’s knowledge.


