WeChat ID freebuf
From WiFi Master Key causing password leaks, to the “315” evening broadcast by CCTV exposing the dangers of wireless, to JD.com recently experiencing internal network roaming due to wireless password leaks, we are compelled to start focusing on wireless security.
Since once wireless is breached, given the characteristics of the current wireless architecture, it’s virtually like being inside your home, with a high level of risk.
Regarding sniffing and hijacking the internal wireless network, you can take a look at two articles I wrote earlier: MITMf framework attack with man-in-the-middle SSL certificate hijacking. MITMf has received many updates recently, making it very interesting to use, and those who enjoy internal networks can pay more attention.
Enough with the ramblings; today I mainly want to talk to you about how to find hidden wireless SSIDs.
0x00 Let’s talk about the existing things
How to find hidden wireless hotspot SSIDs is not a new topic. A search online will reveal many tutorials like this one, but most require using some tools like Wireshark or CommView to assist in packet capturing operations. The general way and process is as follows:
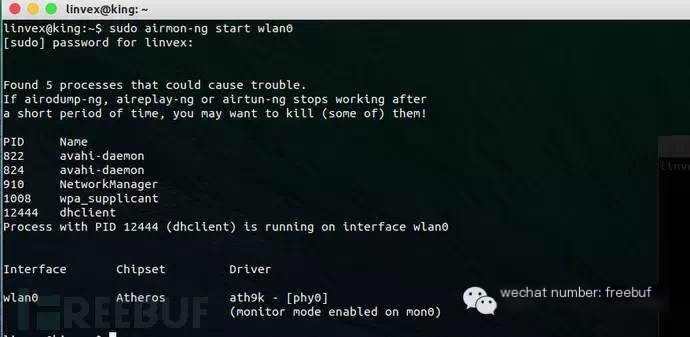 >
>
Like this:
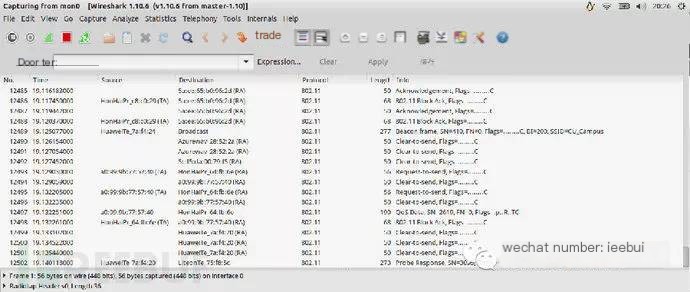 >
>
This is how we found our wireless hotspot. No need for further explanation; those interested please search on Baidu.
This method isn’t bad since I’m relatively lazy, which is why this article exists.
0x01 The general idea
The idea is as follows
1. Determine if there is a hidden wireless hotspot in the surrounding environment2. Obtain the wireless hotspot’s BSSID according to the characteristics of the hidden wireless hotspot3. Use aireplay to attack the target hotspot to force client disconnection and reconnection4. Capture packets during reconnection and filter packets to obtain useful information5. Obtain the hidden hotspot’s SSID
……To ensure the technical article reading experience, please click “Read the original text” at the bottom for the detailed process
0x07 Operating results
After introducing the tools, we run them, and the results are as follows:
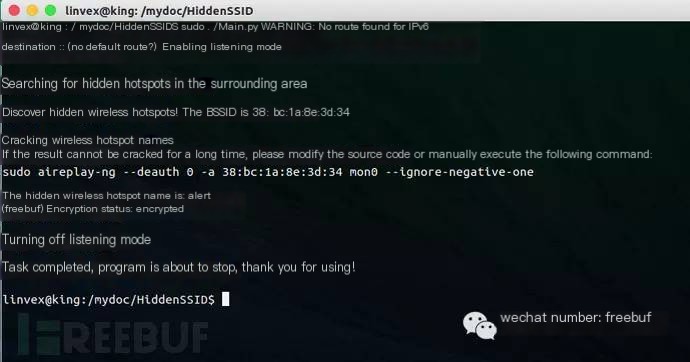
Plus, an image post-aireplay attack:
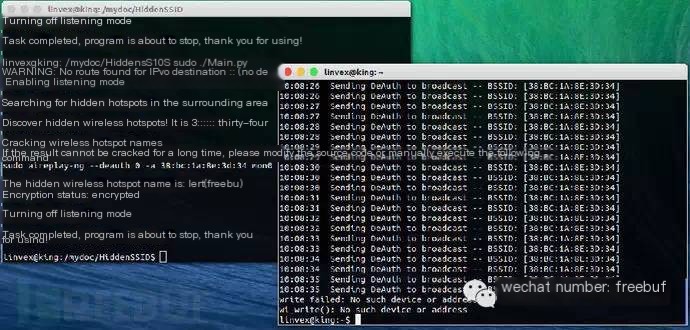
0x08 In Conclusion
As a usual summary, the tools aren’t difficult but are also far from perfect. If anyone has a better solution, feel free to critique and exchange ideas below. Feedback that doesn’t involve personal attacks is welcome 🙂
Currently working on other wireless gadgets, which I’ll share with you later. Bye-bye!
Lastly, the source code is available atRead the original text



