As everyone knows, vehicle chassis systems communicate via CAN, with the common types being USB-CAN and SocketCAN. The former connects to a PC via a USB port, represented by brands like ZLG and Chuangxin (relatively inexpensive), while the latter connects to a PC through a network port, with brands like Kvaser.
USB-CAN generally has more resources available for Windows, including ready-made HMI and secondary development interfaces like Qt, C#, and MATLAB. However, Linux support only includes a test sample, requiring custom development. In contrast, SocketCAN has excellent support across platforms; on Linux, installing net-tools and the SocketCAN driver allows you to control through util commands.
Understanding USB-CAN
CAN stands for Controller Area Network, serving as a communication system between parts of a vehicle, developed by the German company BOSCH, known for its automotive electronics. It eventually became an international standard (ISO 11898) and is one of the most widely used field buses globally. Before using CAN as an in-vehicle communication system, manufacturers relied on point-to-point wiring. As the number of electronic units increased, this wiring became cumbersome and costly to maintain, which was resolved by adopting CAN.
The CAN bus can be likened to a noisy, crowded, slow version of Ethernet LAN, with traffic being UDP rather than TCP. It’s noteworthy that not all automotive control systems use CAN and that CAN is not the only communication protocol used in vehicle systems; others like Bluetooth, LIN, MOST, and FlexRay might also be used. In real-world scenarios, CAN is not the only attack surface; there can be many others.
ICSim USB-CAN Bus Device Simulator
Supplementing and improving content based on this article.
For those without SocketCAN devices, ICSim provides a possibility for research and development while practicing can-utils operations. Additionally, using a simulator can isolate the hardware environment to prevent damage.
In simple terms, ICSim (Instrument Cluster Simulator for SocketCAN) is an open-source vehicle dashboard simulator that consists of two modules: controls and ICSim. The controls module generates simulated vehicle data and sends it to a virtual CAN interface, while ICSim reads CAN frames from the virtual CAN interface (vcan0) and updates the state of the corresponding parts on the dashboard, such as speed, steering, and door status.
To install ICSim:
sudo apt-get install libsdl2-dev libsdl2-image-dev can-utilsgit clone https://github.com/zombieCraig/ICSim.gitConfiguration and compilation of ICSim:
./setup_vcan.shmakePost-configuration generates two executable files:
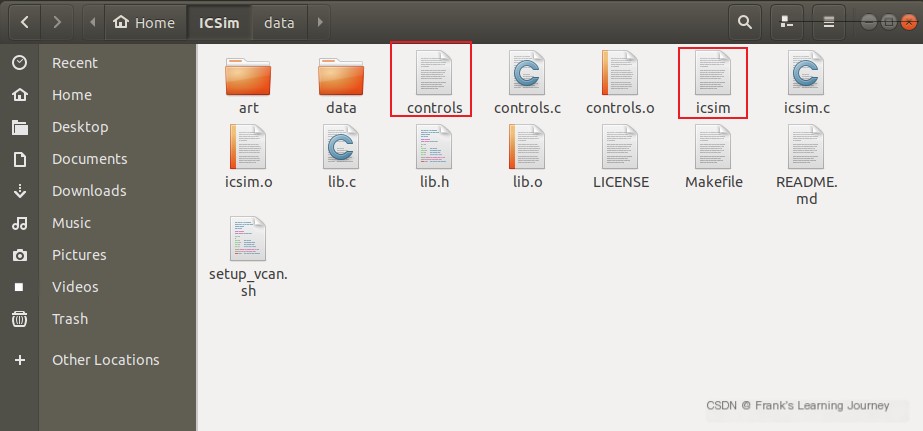 />Insert image description here
/>Insert image description here
Start ICSim:
./icsim vcan0./controls vcan0This will generate a simulated vehicle dashboard and control panel:
USB-CAN Door Test
The door status frame is continuously sent at intervals, but every time the door open button is pressed, the data (DATA) in the frame changes once. This change is used to identify the CAN frame (CAN reverse engineering).
Turn Signal Test
The turn signal frame is also continuously sent. When the button is pressed, the frame changes once. Use this change to identify the CAN frame (CAN reverse engineering).
Real Car CAN Testing
Tested through the OBD interface.
CAN-Utils
The Linux kernel has built-in support for SocketCAN, can-utils, vcan, etc., which serve to send and receive CAN data and perform encoding or decoding on the data.
can-utils is a set of Linux-exclusive utility tools that enable Linux to communicate with the CAN network on a vehicle. To send, receive, and analyze CAN packets, CAN utils need to be installed:
sudo apt-get install can-utilscan-utils primarily include five commonly used tools:
- cansniffer for sniffing packets (displays only changing frames) (cansniffer -c can0)
- cansend to send a frame of data (cansend can0 0C9#8021C0071B101000)
- candump to dump all received packets (candump can0)
- canplayer to replay CAN packets
- cangen to randomly generate CAN packets
Loopback test (self-send, self-receive):
candump can0&cansend can0 123#0011223344556677In a real car, insert the CAN device into the car’s OBD-II port and the computer’s USB port. Run the following command in the Linux prompt to start the CAN interface:
sudo ip link set can0 up type can bitrate 500000This will activate the can0 interface at a bitrate of 500 kbps (if you have only one device connected, it will always be can0), which is standard.
Linux’s SocketCAN provides built-in CAN support in the kernel, making it easy to write your additional programs. You can interact with the CAN bus just like you would with any other network, i.e., through sockets.
Wireshark
Wireshark is a network testing tool that supports Linux. Installation and startup are as follows:
sudo apt-get install wiresharksudo wiresharkAfter starting, it can read the corresponding NIC:
SavvyCAN
Following the introduction of can-utils and Wireshark, a more professional and convenient CAN analysis tool is introduced.
SavvyCAN is a CAN bus reversal and capture tool offering numerous additional functions. It not only allows for browsing, filtering packets, and arbitrating ID but also executing scripts on CAN frames, Fuzzing, and includes several reversal tools.
Install SavvyCAN (binary file):
wget https://github.com/collin80/SavvyCAN/releases/download/V199.1/SavvyCAN-305dafd-x86_64.AppImagechmod 744 SavvyCAN-305dafd-x86_64.AppImage./SavvyCAN-305dafd-x86_64.AppImageAfter starting, it looks like this:
The above shows an opened CAN Log file. To obtain ICSim data, it will be found that the binary version of SavvyCAN does not have the interface activated:
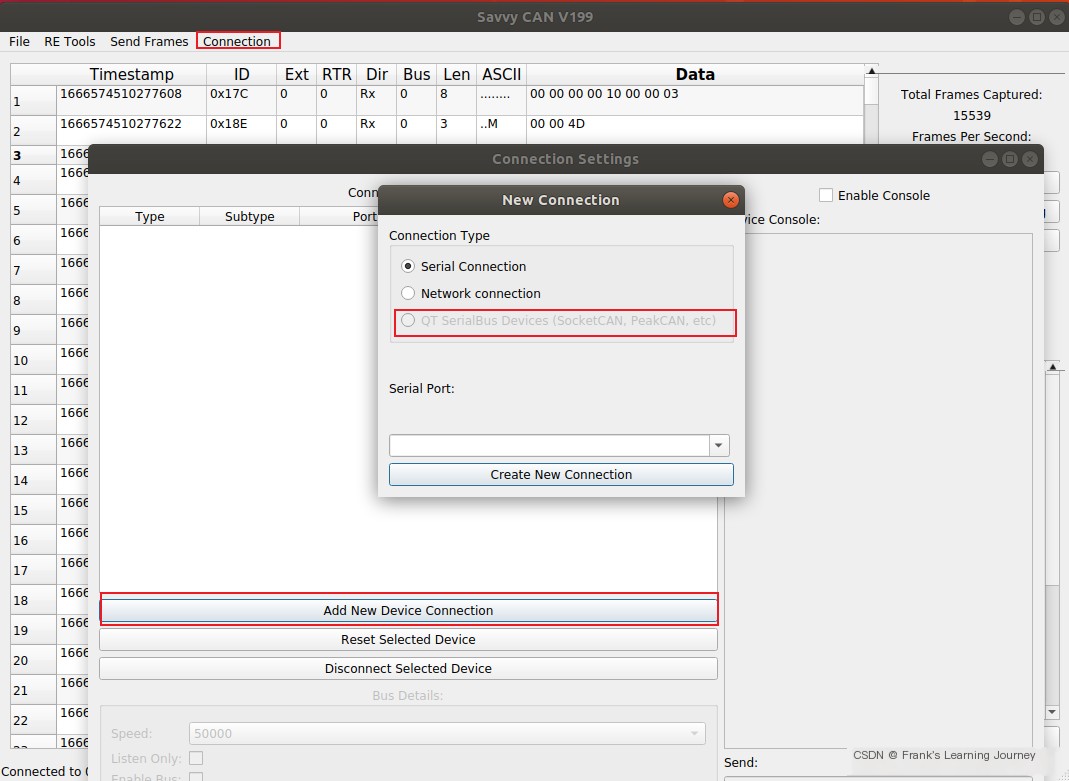 />Insert image description here
/>Insert image description here
Therefore, compiling the source code is necessary to unlock full functionality (first install Qt5):
git clone https://github.com/collin80/SavvyCANcd SavvyCAN/opt/Qt5.12.4/5.12.4/gcc_64/bin/qmake CONFIG+=debugmake./SavvyCANSee this blog for reference.
If you’re interested in automotive security, it’s worthwhile to delve deeper, and if possible, collect some real vehicle data.
The above.



