First, let me clarify that the **nginx configuration vulnerability** is not related to the Nginx or PHP version. It is a parsing vulnerability caused by improper user configuration, specifically when a `/.php` suffix is added, leading to it being parsed as a PHP file. We are using the Vulhub vulnerability environment, so let’s first examine the provided images.
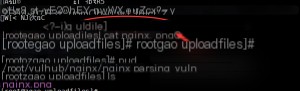
The image finally contains code that writes phpinfo, which we open in the browser. I won’t demonstrate the file upload part here because the vulnerability itself is not in the upload part. 
The image loads normally, but what happens if we add a `/.php` suffix to the image URL?
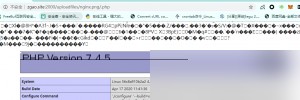
Now let’s see how the nginx configuration file is written and where the vulnerability occurs.
location ~ \.php$ {
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param REDIRECT_STATUS 200;
fastcgi_param SCRIPT_FILENAME /var/www/html$fastcgi_script_name;
fastcgi_param DOCUMENT_ROOT /var/www/html;
fastcgi_pass php:9000;}
From this incorrect configuration, we can see that nginx hands over files ending with ‘.php’ to fastcgi for processing. So, our constructed http://ip/uploadfiles/nginx.png/.php is also handed over to fastcgi for processing. 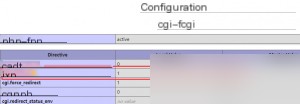
Using phpinfo, we check cgi.fix_pathinfo=1, which is often used in PHP to obtain the current request’s URL path information. Generally, this can be obtained through the environment variable $_SERVER[‘PATH_INFO’], and the cgi.fix_pathinfo option in the configuration file is related to obtaining this value.
The default value of cgi.fix_pathinfo is 1. Nginx by default does not set the value of the PATH_INFO environment variable, which needs to be set through regex matching in SCRIPT_FILENAME, but this can pose a security risk. It is necessary to set cgi.fix_pathinfo=0 to 0. However, once this is disabled, PHP cannot obtain PATH_INFO information, and programs that rely on PATH_INFO for URL beautification will fail.
Therefore, when fastcgi processes ‘.php’ files and finds that the file does not exist, the php.ini configuration file’s cgi.fix_pathinfo=1 takes effect. This configuration is used to fix the path, and if the current path does not exist, the upper path is used. Here, ‘/nginx.png’ is handed over to fastcgi for processing.
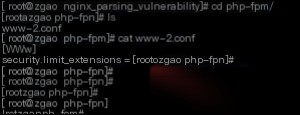
Additionally, the security.limit_extensions configuration item in php-fpm.conf restricts the types of files fastcgi can parse. When this setting is empty, fastcgi is allowed to parse files like ‘.png’ as code. Therefore, we can restrict the script extensions that fpm is allowed to parse, which helps prevent web server configuration errors. 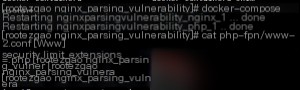
After modifying the configuration file and restarting the environment, it is equivalent to setting a whitelist, allowing only the php suffix to be parsed and executed.
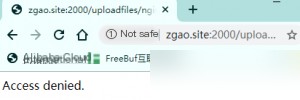
Therefore, to handle this vulnerability, if you really cannot disable the cgi.fix_pathinfo option, set the value after security.limit_extensions in php-fpm.conf to .php to minimize the vulnerability’s impact.


