Once the IP address is determined, you can send datagrams to the host associated with it. However, the IP address functions at the network layer, so is there a corresponding address at the data link layer that can tell the other host its address? Yes, that address is the MAC address. The MAC address is stored in the MAC address table, which is used to map IP addresses to physical addresses on a local network.
Understanding MAC Addresses
The full name of MAC address is Media Access Control Address, which translates to Media Access Control Address. It is the unique identifier of an Ethernet or network adapter on a network. MAC addresses are able to distinguish different network interfaces and are used in multiple network technologies, especially most IEEE 802 networks. The MAC address is also called the physical address, hardware address, and sometimes permanent address. MAC addresses are primarily used to identify nodes interconnected in the data link layer, as shown in the image below:
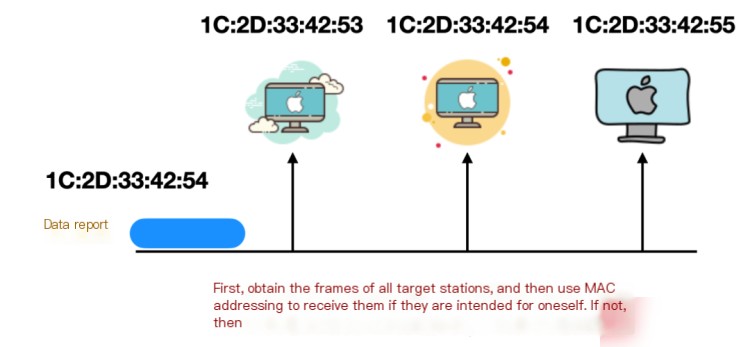
MAC addresses are 48 bits long and are generally burned into the ROM in the case of using a Network Interface Card (NIC). Therefore, the MAC address of any network card is unique.
The structure of the MAC address is as follows:
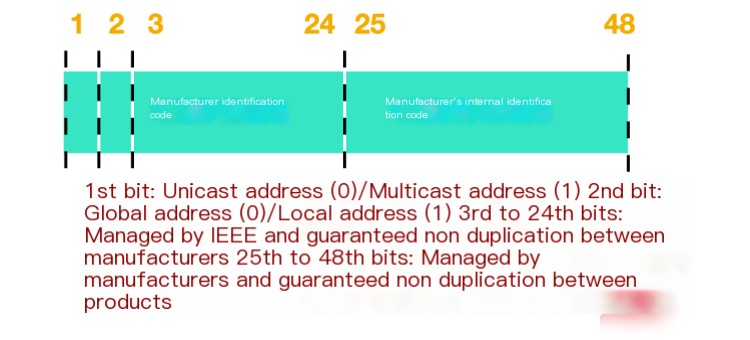
Within the MAC address, bits 3 to 24 represent the manufacturer identifier code. Each NIC manufacturer has a specific unique identification number. Bits 25 to 48 are used internally by the manufacturer to identify each network card. Therefore, it can be ensured that there will not be network cards with the same MAC address worldwide. There are exceptions where MAC addresses might repeat, but it generally doesn’t pose a problem as long as the two MAC addresses belong to different data link layers.
Composition and Forwarding Principle
The MAC address table records the correspondence between MAC addresses of other devices learned by the device and the interfaces, as well as the VLAN information associated with the interfaces.
The MAC address table is used to guide unicast forwarding of packets. When forwarding packets, the device queries the MAC address table according to the destination MAC address of the packet:
If the MAC address table contains an entry corresponding to the destination MAC address of the packet, the packet is directly forwarded through the outgoing interface recorded in the entry;
If there is no entry in the MAC address table corresponding to the destination MAC address of the packet, the device will broadcast the packet in the VLAN, excluding the incoming interface.
Learning and Aging
Generally, the MAC address table is automatically learned and established by the device based on the source MAC addresses in the received data frames.
If there is no entry in the MAC address table, the device will add the new MAC address, along with its corresponding port and VLAN ID, as a new entry to the MAC address table.
If the MAC address table already contains the entry, the device updates it by resetting the age timer of the entry.
The device only triggers MAC address learning and refreshing when it receives a data frame.
All interfaces of the device default to VLAN1. If no modifications are made, all MAC address table entries will have a VLAN ID of VLAN1.
The device does not perform MAC address learning for BPDU MACs (e.g., 0180-c200-xxxx).
To adapt to network changes, the MAC table needs continuous updates. Automatically generated entries (i.e., dynamic entries) in the MAC table are not permanent. Each entry has a lifespan, and entries that are not updated within this lifespan will be deleted. This lifespan is referred to as the aging time, defaulting to 300 seconds. If an entry is updated before the lifespan ends, its aging time is recalculated.
MAC Address Entries
Learned by the interface from the source MAC address in the packet, entries can age.
Dynamic entries will be lost after system reset, interface board hot plug, or interface board reset.
Checking dynamic MAC address entries can help determine if there is data forwarding between two connected devices.
By viewing the number of specified dynamic MAC address entries, you can obtain the number of users communicating under the interface.
Static Entries
Manually configured by the user and distributed to each interface board, these entries do not age.
Static entries saved remain after system reset, interface board hot plug, or interface board reset.
Once interfaces and MAC addresses are statically bound, packets from other interfaces with this source MAC address will be discarded.
A static MAC address entry can only be bound to one outgoing interface.
Once an interface and a MAC address are statically bound, it won’t affect the interface’s dynamic MAC address learning.
Static MAC address entries binding can ensure legitimate user usage and prevent other users from using the MAC for attacks.
Black Hole Entries
Configured by the user and distributed to each interface board, these entries do not age.
Saved entries remain after system reset, interface board hot plug, or interface board reset.
After configuring a black hole MAC address, any packet with that MAC as the source or destination MAC address will be discarded.
By configuring black hole MAC address entries, illegal users can be filtered out.
What is ARP?
ARP stands for Address Resolution Protocol. It is a protocol used to map IP addresses to MAC addresses, essentially asking the corresponding MAC address for a target IP. The ARP protocol is extremely important in IPv4.
- Note:
ARP is only used in the IPv4 protocol; the IPv6 protocol uses Neighbor Discovery Protocol, which is integrated into ICMPv6. - In short, ARP is a protocol for addressing problems, using an IP address as a clue to locate the MAC address of the next host that should receive the data packet. If the target host is not on the same link, it will look up the MAC address of the next-hop router.
How ARP Works
The IP address hides the physical address from the upper layer to make the Internet appear as a unified address format. However, in actual communication, the IP address cannot be recognized by the physical network, which still uses physical addresses. Therefore, it is essential to implement the mapping from IP addresses to physical addresses.
For Ethernet, when an IP packet is sent over the Ethernet, the Ethernet link does not recognize the 32-bit IP address. Instead, Ethernet nodes are represented as 48-bit MAC addresses. Hence, we must establish a mapping (MAP) between IP addresses and MAC addresses, and this process is what we call Address Resolution.
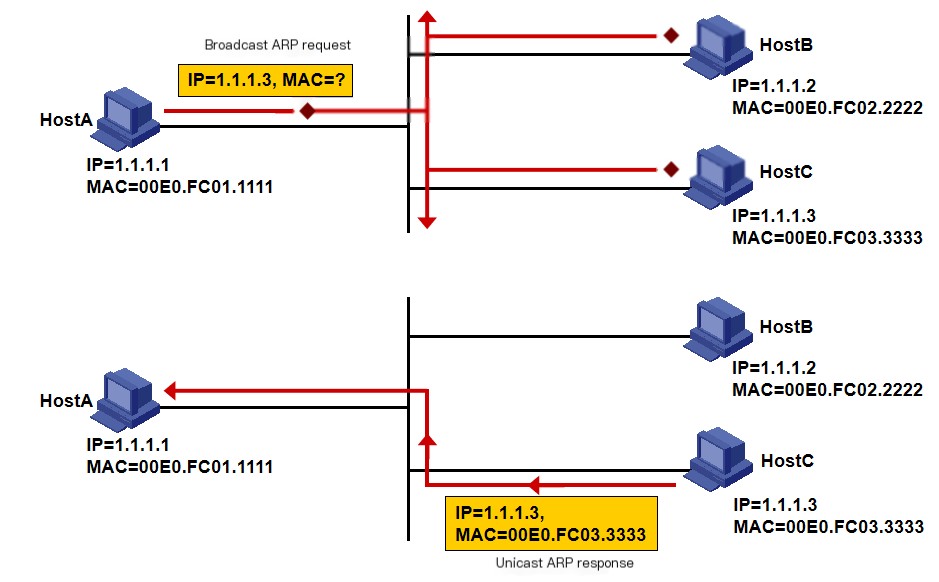
As depicted in the image, assume HostA and HostB are on the same subnet. If HostA wishes to send an IP packet to HostB, the address resolution process is as follows:
1. HostA first checks its own ARP entries to determine whether they contain an entry corresponding to HostB’s IP address. If the entry is found, HostA directly encapsulates the IP packet into a frame with the MAC address in the ARP entry and sends the frame to HostB.
2. If HostA cannot find the corresponding entry in its ARP table, it temporarily caches the data packet, then broadcasts an ARP request. The sender’s IP address and sender’s MAC address in the ARP request packet are HostA’s IP address and MAC address, the target IP address is HostB’s IP address, and the target MAC address is full zeros.
3. The ARP request packet is sent as a broadcast, allowing all hosts on the subnet to receive the request. HostB compares its IP address with the target IP address in the ARP request packet. Since they match, HostB stores the sending host (HostA’s) IP and MAC addresses from the ARP request packet into its own ARP table and sends an ARP reply to HostA with its MAC address using unicast. Other hosts do not respond since the request’s target IP address does not match their own.
4. Once HostA receives the ARP response packet, it stores HostB’s MAC address in its ARP table and encapsulates the IP packet into a frame with this MAC address as the destination, sending it to HostB.
What if on different links?
This is where Proxy ARP comes in. Typically, ARP is isolated by routers, but routers employing Proxy ARP can forward ARP requests to adjacent segments, allowing nodes across multiple segments to communicate as if on the same segment.
ARP Cache
Now that the MAC address can be determined by sending an ARP request once before sending an IP packet, is it necessary to go through the whole process of broadcasting -> encapsulating ARP response -> returning to host every time a packet is sent?
Consider how a browser operates. A browser has built-in caching that can save recently frequently used addresses. ARP works similarly. The key to ARP’s efficient operation is maintaining the ARP cache (or table) on each host and router.
This cache maintains the mapping relationship between each IP and MAC address. By mapping the MAC address obtained from the first ARP request to an ARP cache table, subsequent datagrams to this address are sent without resending the ARP request. Instead, the MAC address in the cache table is used directly for sending datagrams. Each time an ARP request is sent, the corresponding mapping in the cache table is cleared and updated.
Using the ARP cache reduces the usage of network traffic and prevents extensive ARP broadcasting to a certain extent.
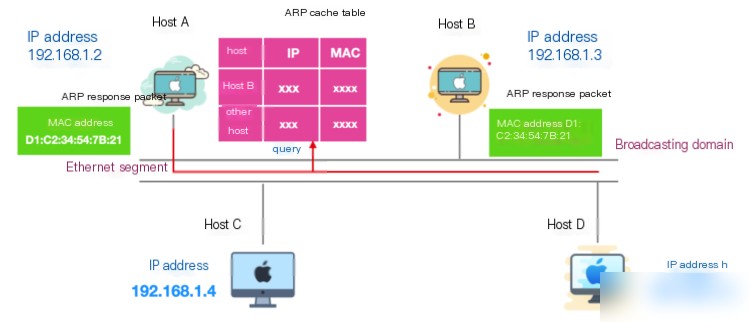
Generally, after sending an ARP request once, the chance of sending the same request again is quite high. Thus, using the ARP cache can reduce the frequency of ARP packet transmissions. Moreover, not only can the ARP requesting party cache the ARP recipient’s MAC address, but the recipient can also cache the requester’s IP and MAC address as illustrated in the following image:
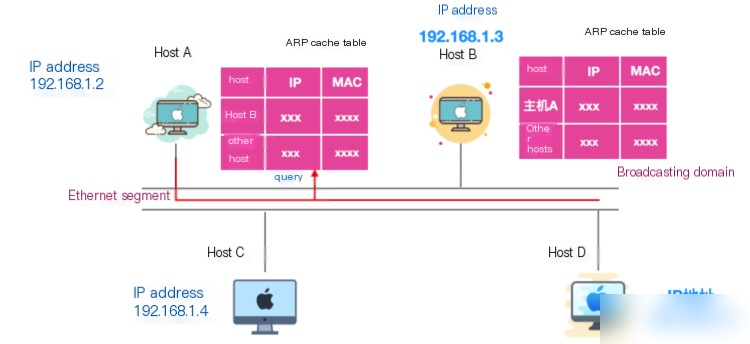
However, the MAC address cache has a certain lifespan. After this duration, the cached content will be cleared.
You can use the arp command in Linux or Windows to view the ARP cache. The -a option displays all cache entries in both systems. To query caches in Linux, use arp;
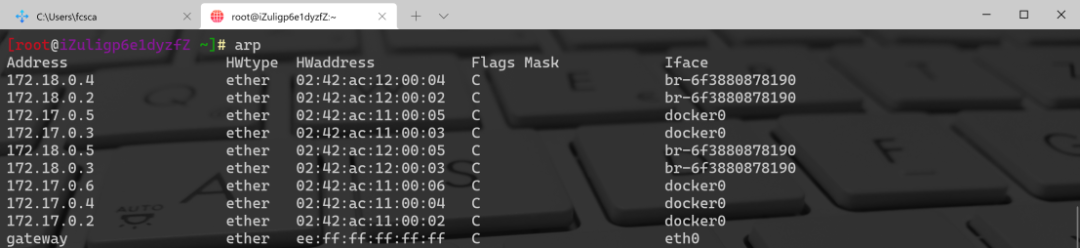
It primarily contains five items:
- Host name — corresponding to an IP address
- Hardware address type
- Hardware address
- Flags
- Local network interface
Flags are mainly divided into three types: C, M, or P. C indicates dynamic learning by the ARP protocol. M can be added via arp -s. P indicates published, where the host responds to any incoming ARP request. This option is destined for configuring Proxy ARP. For example, in Windows, to query ARP cache;
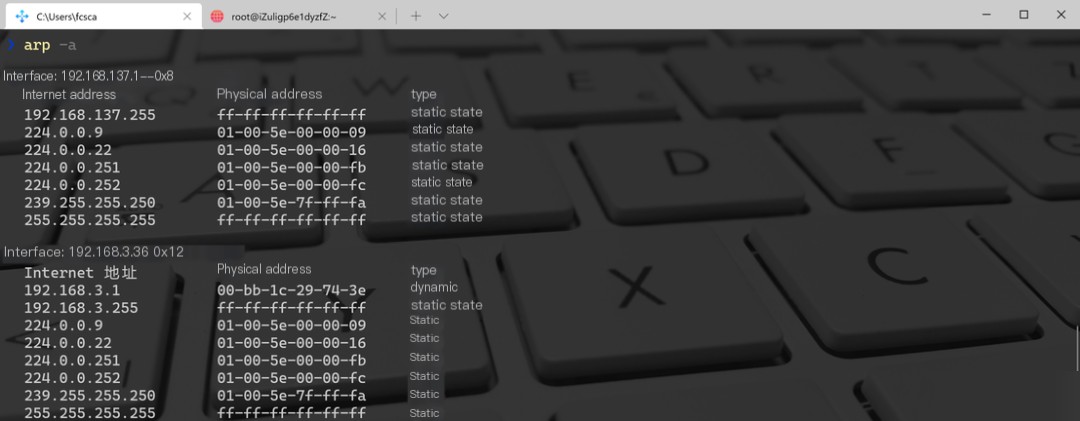
The ARP program on Windows shows IPv4 addresses, and its interface is a hexadecimal number. The Windows version also indicates whether the address is entered manually or learned dynamically by ARP. In the above example, there are both static and dynamic. A 48-bit MAC address is displayed as six hexadecimal numbers, separated by “:” in Linux and by “-” in Windows.
ARP Structure
As mentioned earlier, when ARP wants to know the MAC address, it first sends an ARP request. What information does this request carry? Below is the typical ARP request or response message format used for converting an IPv4 address in Ethernet.
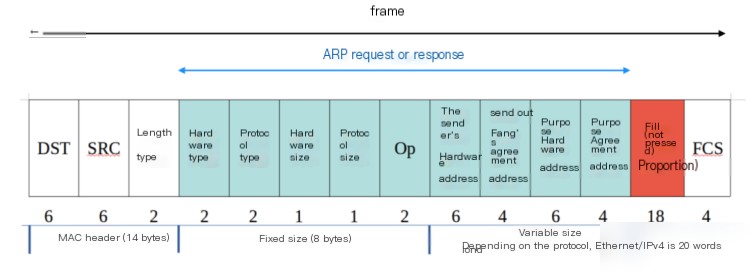
The first 14 bytes form the standard Ethernet header, with the first two fields, DST and SRC, respectively representing the Ethernet destination address and Ethernet source address. The Ethernet destination address, if it is ff:ff:ff:ff:ff:ff, signifies a broadcast address where all Ethernet interfaces in the same broadcast domain can receive these frames. The ARP request length/type follows immediately, where the value for ARP requests and responses is 0x0806.
- The hardware type indicates the type of hardware address, with common types being MAC physical or Ethernet addresses. For Ethernet, this value is 1.
- The protocol type specifies the mapped protocol address type, with a value of 0x0800 for IPv4 addresses.
- The hardware size and protocol size specify byte counts for hardware and protocol addresses, respectively. For ARP requests or replies in Ethernet using IPv4, their values are 6 and 4, respectively.
- The Op field designates if it is an ARP request (Op = 1), ARP response (Op = 2), RARP request (Op = 3), or RARP response (Op = 4).
- Following the Op are the sender hardware address (MAC address), sender protocol address (IPv4 address), target hardware address, and target protocol address.
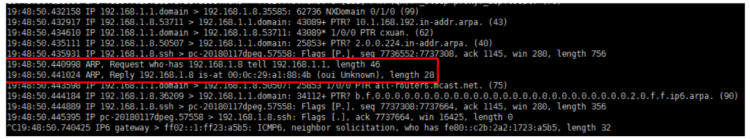
ARP Packet Capture Practice
Demonstrating ARP packet capture on both Mac and Linux platforms;
In a Mac environment, we use WireShark for packet capture, which can be downloaded from the official website at:
https://www.wireshark.org/download.html
After the download is complete, read the installation instructions, which will reveal the need to install two plugins. Install as prompted and then open WireShark to begin packet capture. Below is a captured ARP data packet:
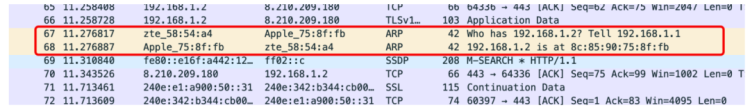
One convenient aspect of this software is the different color markers for various data packets, which is excellent. Now, view the ARP request:
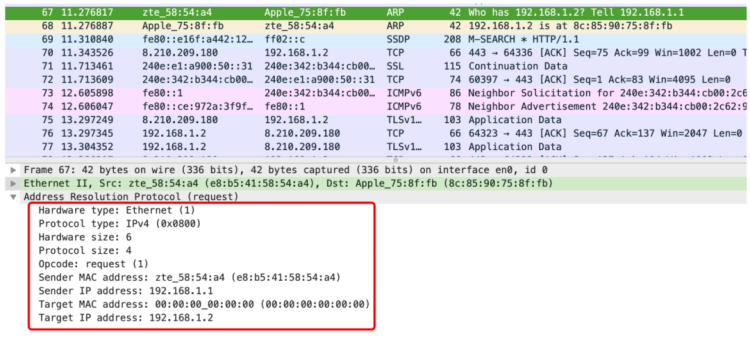
This shows a complete ARP request packet, with the hardware type used being Ethernet, protocol type IPv4 with a default value of 0x0800, a hardware size of 6 bytes and a protocol size of 2 bytes. The Op stands for Opcode, with Op = 1 indicating it is an ARP request, followed by the sender’s hardware and protocol addresses, and the recipient’s hardware and protocol addresses. The ARP response is shown as follows:
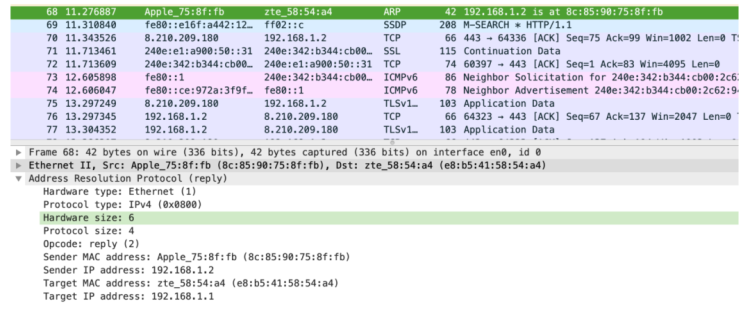
It shows Op = 2, indicating an ARP response. In a Linux environment, tcpdump can be used to capture ARP packets. If tcpdump is not found, you can install it using yum install -y tcpdump. With tcpdump -i ens33, you can print out the packets on the ens33 address. Below is a captured ARP packet.
ARP Cache Timeout
1. ARP Cache
- The key to ARP’s efficient operation is maintaining the ARP cache (or table) on each host and router
- This cache maintains the latest mapping of network layer to hardware addresses for every interface using address resolution
- When an IPv4 address is mapped to a hardware address, it corresponds to an entry in the cache, with the typical expiration time being 20 minutes from the time of entry creation
2. ARP Cache Timeout
- A timeout is generally associated with every entry in the ARP cache (as we’ll see later, the arp command allows administrators to set cache entries to never time out)
- In most implementations, the timeout for complete entries is 20 minutes, while the timeout for incomplete entries is 3 minutes
- These implementations usually restart the 20-minute timeout for a cache entry whenever it is used. [RFCl122] is the RFC describing host requirements, stating each entry should start the timeout even when used, but many implementations don’t do this and instead reset the timeout after every use
RARP
Opposite of ARP, RARP (Reverse Address Resolution Protocol) reverses ARP, allowing MAC addresses to map to IP addresses, often used when connecting small embedded devices such as printers and servers to a network.
There are generally two ways to set IP addresses, manual setting and DHCP dynamic acquisition:
However, for embedded devices without any input interfaces and the inability to obtain a dynamic address via DHCP, RARP becomes necessary. A RARP server must be prepared, registering the device’s MAC address and IP address on this server. When the device connects to the network, it sends an IP and MAC address query request to the server, which provides its IP address and MAC address.
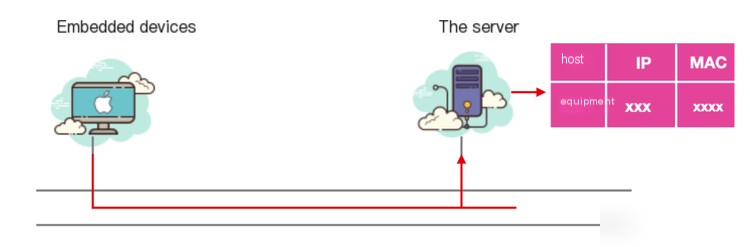
When the host only knows its hardware address, RARP resolves its IP address, commonly used for diskless workstations to obtain their IP addresses before starting up.
When first booting, a diskless workstation only knows the MAC address of its network card and must obtain its IP address, broadcasting a RARP request to the network. Upon receiving the broadcast request, the RARP server sends a response message, allowing the diskless workstation to obtain the IP address.
For a RARP server to respond to requests, it must first know the correspondence between physical and IP addresses. Thus, the RARP server maintains a mapping table of “physical address to IP address” for the local network segment. When a diskless workstation sends a RARP request, all machines on the network receive it, but only the RARP server processes the request and responds based on the requester’s physical address. The RARP request includes the requester’s physical address, which the server uses to find its IP address. As the server already knows the requesting diskless workstation’s physical address, it responds with a unicast response instead of a broadcast.
While ARP and RARP requests use broadcasting, ARP, and RARP responses generally use unicast to save network resources.
ARP Attack
ARP is an inherently insecure protocol, and several ARP-related attacks have emerged, mainly using Proxy ARP functions to impersonate a host and respond to ARP requests to steal legitimate users’ communication data by forging ARP packets, impacting network transmission speed and compromising user privacy with severe consequences.
Types of ARP Attacks
ARP attacks mainly include the following types:
- ARP Flooding Attack: By sending a large number of ARP packets to the gateway, the gateway is unable to respond normally. First, many ARP request packets are sent, followed by a flood of bogus ARP response packets, causing an uptick in the gateway’s CPU usage, making it challenging to respond to normal service requests. Also, the gateway’s ARP cache becomes filled with erroneous data, preventing proper update and maintenance of the legitimate ARP cache, depleting network bandwidth resources.
- ARP Host Spoofing Attack: The ARP host spoofing attack is among the most common forms of ARP attacks. Attackers use ARP spoofing to ensure traffic information sent by attacked hosts within the local area network to the gateway is actually sent to the attacker. Hosts update their ARP, believing the MAC in their ARP cache corresponds to the attacker’s MAC. Consequently, data streams intended for transmission through the gateway are sent to the host, resulting in data leakage.
- Gateway Spoofing Attack: Gateway spoofing involves misleading the gateway to send data meant for other hosts to the attacker by assuming the role of the gateway. An attacker doesn’t target individual hosts but aims to intercept data of all local area network users flowing through the gateway, leading to data leakage and higher virus infection risks for users’ computers.
- Man-in-the-middle Attack: A man-in-the-middle attack simultaneously tricks the hosts and the gateway within the local network, with user data sent to the gateway and gateway data sent to a single attacker, causing leaks of user and gateway information.
- IP Address Conflict Attack: By scanning physical hosts within the local area network for their MAC addresses, attackers target these MAC addresses for attacks, resulting in IP address conflicts among the hosts in the network, affecting normal network usage.
Detecting ARP Attacks
Firstly, diagnose whether there is an ARP attack.
1. When there is a noticeable slowdown in internet speed or a sudden disconnect, you can use the arp -a command to check the ARP table (Click “Start” button – choose “Run” – enter “cmd” and click “OK” button, enter “arp -a” command in the terminal). If the gateway’s MAC address has changed or many IP addresses point to the same physical address, it’s indicative of ARP spoofing. Use “arp -d” to clear the ARP list, then re-access.
2. Utilize ARP firewall software (such as 360 ARP firewall or AntiARPSniffer, etc.).
How to Judge if a Switch is Under ARP Attack and How to Address It
If a network is under an ARP attack, the following phenomena may occur:
1. Users experience disconnections, frequent networking drops, slow internet, business interruptions, or inability to connect online.
2. High device CPU usage, managed device stalling, devices downstream disconnect, fluctuating device master-backup status, device port indicator flashing red quickly.
3. Ping checks yield delays, packet losses, or connectivity issues.
If machines in the LAN are under ARP virus attack, finding and rooting out the infected source can lead to recovery. How can one swiftly pinpoint the source machine of the attack?
1. Use the arp -a command. When noticing slower internet or frequent disconnections, use the arp -a command to check the ARP table. If there is a change in the MAC address of the gateway or multiple IP addresses direct to a single MAC address, it’s an indication of an ARP attack.
2. Employ the ARP firewall software to check. If the network card is in promiscuous mode or the speed of ARP requests or total ARP requests sent is large, that machine is likely the culprit. After locating it, gather virus information for removal.
3. Check the “system history log” on the router. ARP attack trojan programs send massive packets, obstructing LAN communications due to the limitations of their processing capabilities, leading users to feel their internet speed decreasing. When these programs stop running, users resume online connections, requiring one more disconnection during the switch. This message represents a change in MAC address, initiated by an ARP attack trojan beginning executions, causing MAC updates to match the virus host MAC in the router’s user statistical records, with all users showing identical MAC addresses to the virus host. Once the program stops running, real MAC address restoration occurs on routers for hosts within the local network.
ARP Attack Methods:
- Simple Spoofing Attack
This common attack involves sending forged ARP packets to trick routers and target hosts into thinking it’s a legitimate host, thus completing the spoofing. These usually occur within the same subnet since routers won’t forward packets from one subnet externally; however, different subnet attacks can be accomplished by using ICMP protocol to inform routers of new route selections.
- ARP-based DOS
This newly emerged attack method, known as Denial of Service (DOS), occurs when a host receives many connection requests. Due to limited handling capacity, the host cannot serve normal requests, resulting in service denials. During this process, if ARP is used to hide oneself, the logs of the attacked host show no real IP attackers nor affect the attacker’s machine.
- MAC Flooding
This is a relatively dangerous attack capable of overflowing the switch’s ARP table, disrupting network communications entirely.
- Sniffing in Switched Environments
In earlier small LANs, HUBs were used for interconnections, broadcasting every packet to every connected machine. Using software, one could sniff the entire LAN’s data. Modern networks employ switched environments, where data transfers between specified target communications are locked. On the basis of ARP spoofing, a host can masquerade as an intermediary transfer station to eavesdrop communications between two machines.
Defense Against ARP Attacks
- Set ARP Cache Timeout
Setting a timeout value for entries in the ARP cache can effectively prevent ARP table overflow by shortening the timeout.
- IP+MAC Access Control — Recommended
Relying solely on IP or MAC to establish a trusted relationship is insecure; an ideal security contact is built on IP+MAC, which is one reason for mandatory binding of IP and MAC in our campus network access policy.
- Static ARP Cache Table
Each host maintains a temporary IP-MAC corresponding table, and ARP attacks deceive by altering this cache for malicious purposes. Employing static ARP to bind correct MACs is an effective solution. The arp -a command can check the current ARP cache table contents in the command line.
- Automated Query
During normal intervals, record the database of IP-MAC correspondences and regularly check if the current IP-MAC relationships hold correctly. Regular inspections of switch traffic logs and packet loss rates are recommended.
ARP itself does not cause significant harm, but when combined with other uses, its risk becomes immeasurable. Due to ARC inherent issues, preventing ARP attacks can be challenging. Regular network status monitoring and traffic tracking are favorable practices for webmasters.
Conclusion
ARP is a basic protocol in implementing TCP/IP and usually operates without users or applications being aware of it. ARP can be used to map IP addresses to MAC addresses.



