background
The latest release of Wireshark 3.6.0 introduces a significant enhancement: the ability to analyze TCP conversation completeness. This new feature allows users to filter TCP streams based on various session elements, such as opening and closing handshakes and data payloads, using the tcp.completeness filter. By leveraging this functionality, network analysts can better evaluate TCP session integrity and troubleshoot issues more effectively.
Introduction to TCP Conversation Completeness
What is TCP Conversation Completeness? TCP Conversation Completeness, in theory, a complete TCP session should include both the most commonly understood opening handshake and closing handshake, and does not depend on whether there is or is no data transmission.
However, considering that most actual TCP session scenarios contain more data to be like a complete session, the following tcp.completeness field can be used to construct the session filter value:
- 1: SYN
- 2 : SYN-ACK
- 4 : ACK
- 8 : DATA
- 16: END
- 32 : RST
The above field values can be flexibly combined to form different TCP session integrity display filter expressions.
Analyzing TCP Sessions Using Completeness Criteria
TCP three-way handshake
For example, if you want to filter out a session in a packet file that contains only the standard TCP three-way handshake, you can use this expression 'tcp.completeness==7' because 1 (SYN) + 2 (SYN/ACK) + 4 (ACK) = 7.

Display in the packet detail view
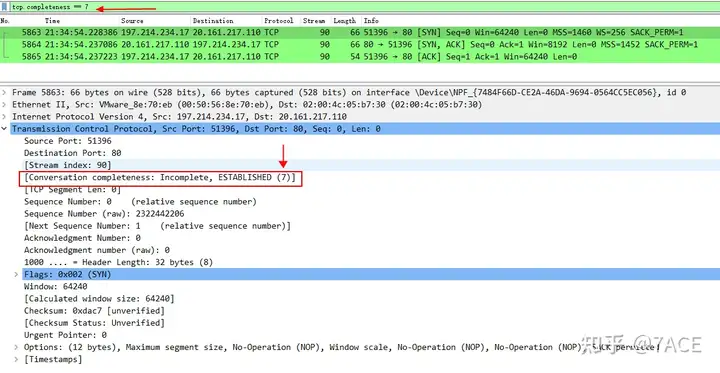
It is important to note that this TCP Steam 90 only has TCP three-way handshake packets, which can be filtered again for tcp.stream verification.
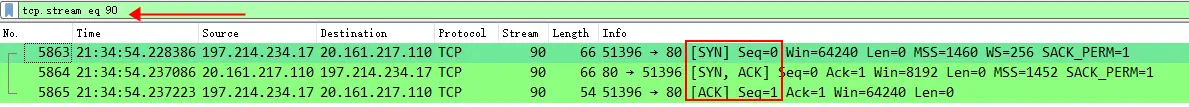
Therefore, if a TCP stream contains any data packets other than the TCP three-way handshake, the expression 'tcp.completeness==7' will not take effect, that is, the TCP stream cannot be filtered out.
Let’s take an example of a complete TCP flow in advance. This TCP flow includes TCP three-way handshake, data, and TCP four-way handshake complete data packets.
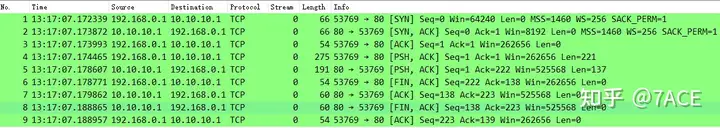
However, applying expressions 'tcp.completeness==7' cannot filter out any data packets.
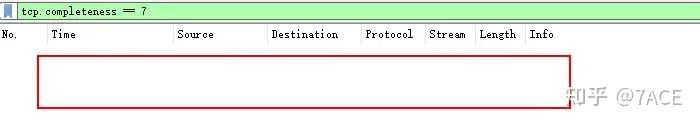
A previous article I wrote, “Quick Display Filtering of TCP Three-Way Handshake”, has a different focus than the new version of TCP integrity session filtering. The previous article is more about solving the filtering problem of the third ACK in the TCP three-way handshake.
TCP four-way handshake
Similarly, if you want to filter out a session in the data file that contains only the standard TCP four-wave handshake, you can use this expression 'tcp.completeness==20' because 4 (ACK) + 16 (FIN) = 20.
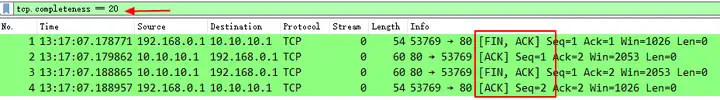
Display in the packet detail view
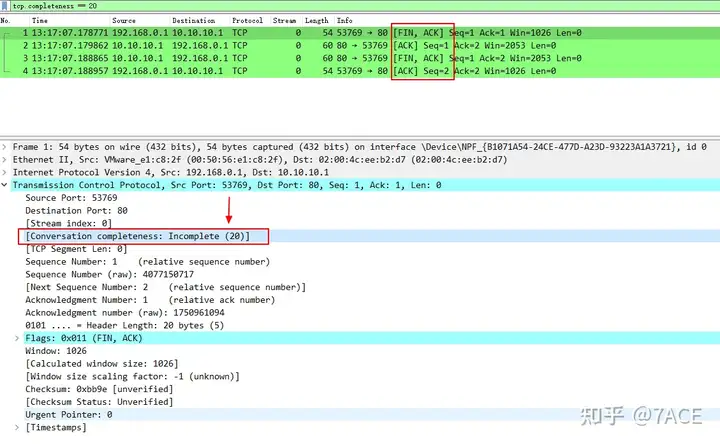
It is also important to note why an expression is used here 'tcp.completeness==20'instead of an expression 'tcp.completeness==16'. This is also the difference between the theory and practice in the standard TCP four-wave handshake. Students who are interested can think divergently.
TCP RST close handshake
In the TCP session, the connection can be closed by FIN or RST. A simple example of connecting to an unopened port on the other end is as follows
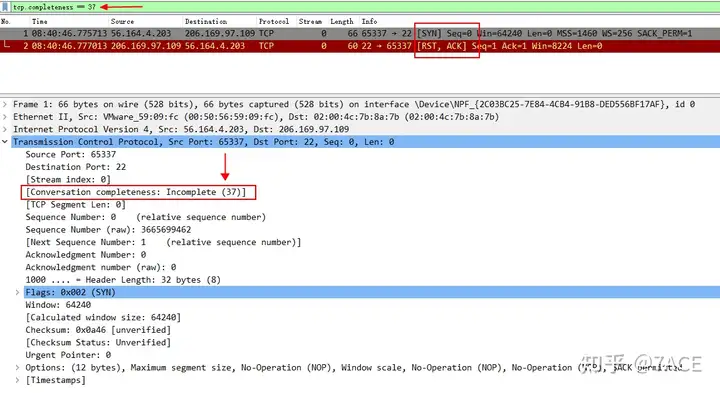
Again the expression used here is 'tcp.completeness==37' , 1 (SYN) + 4 (ACK) + 32 (RST) = 37.
TCP Full Session
Finally, back to the real TCP session case, a complete session with data transmission will be filtered by a more combined expression. Considering that the closing of the connection can be associated with a FIN or RST packet, or even both, the most complete filter expression is:
tcp.completeness == 31 or tcp.completeness == 47 or tcp.completeness == 63Considering the convenience of demonstration, the following are simple examples of three expressions respectively.
The most standard TCP complete session is , 'tcp.completeness==31'because 1 (SYN) + 2 (SYN/ACK) + 4 (ACK) + 8 (DATA) + 16 (FIN) = 31.
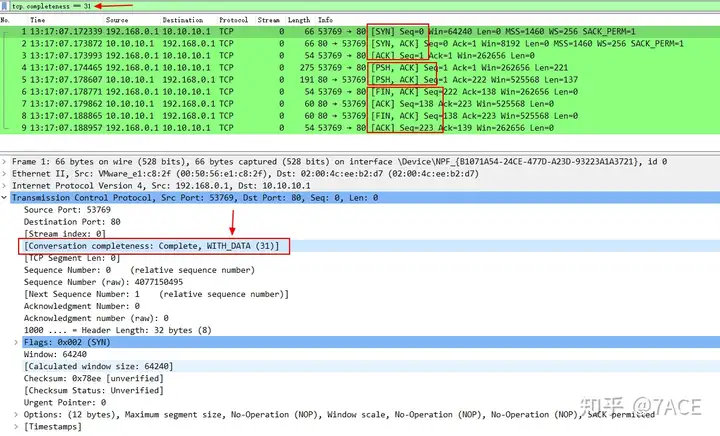
The complete TCP session that closes the connection with RST is 'tcp.completeness==47'47 because 1 (SYN) + 2 (SYN/ACK) + 4 (ACK) + 8 (DATA) + 32 (RST) = 47.
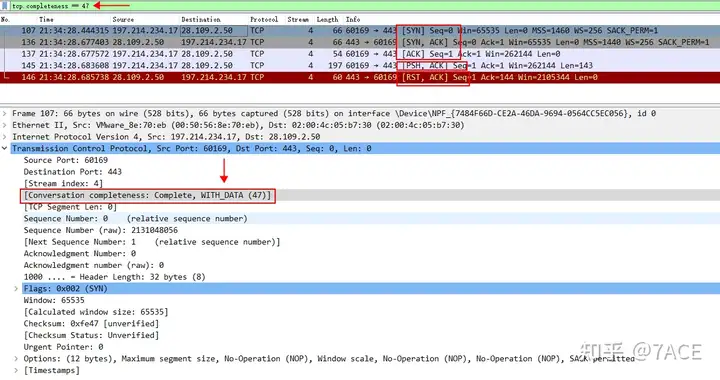
A complete TCP session with simultaneous FIN + RST, 'tcp.completeness==63'because 1 (SYN) + 2 (SYN/ACK) + 4 (ACK) + 8 (DATA) + 16 (FIN)+ 32 (RST)= 63.
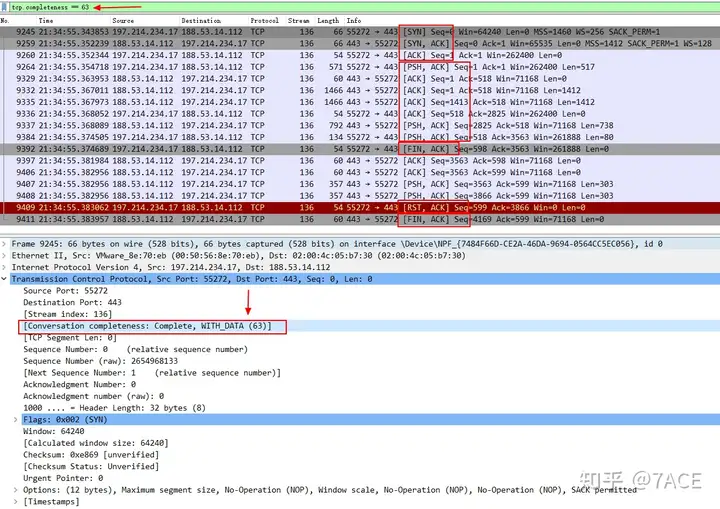
Summary of TCP Completeness Filtering
In summary, TCP session integrity policy checking greatly facilitates the analysis and processing of TCP flows and is a good technique for troubleshooting.



