Palo Alto Networks found that attackers are increasingly inclined to pre-register backup domains, and the use of such strategically dormant domains in attacks is on the rise. For example, the attackers in the SolarWinds incident used C&C domains that were registered years before the actual attack.
A typical feature of APT attacks is the long-term lurking at high-value targets, and the malware they deploy tends to remain dormant within the compromised network for extended periods. Phishing and black hat SEO attackers also frequently use long-registered domains, which often gain a good reputation due to their long registration time, making it more challenging to detect these strategically dormant domains.
Strategically dormant domains show a spike in traffic when activated, which can be used to detect these domains. Palo Alto Networks can filter approximately 30,000 domains daily from Passive DNS data, all of which suddenly gain more than ten times the usual traffic on a certain day, and the proportion of malicious domains in these is more than triple that of new registered domains (NRD).
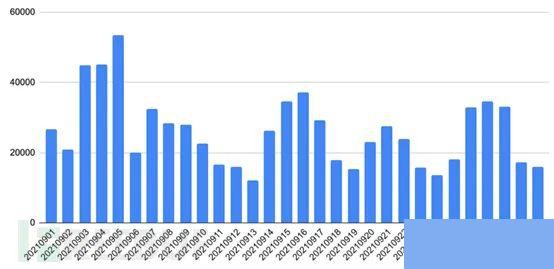
△ Figure 1 Number of strategically dormant domains detected daily in September 2021
In the SolarWinds supply chain attack, the SUNBURST trojan used DGA algorithms to steal domain information from compromised hosts. To detect similar APT attacks, Palo Alto Networks marked domains in the data containing a large number of newly discovered DGA subdomains as potential malicious domains. These malicious domains averaged 161 DGA subdomains each, carrying 43.19% of the sudden increase in traffic. Below are some typical examples for analysis.
Detecting Strategically Dormant Domains
It is well-known that abuse of newly registered domains is severe, but focusing only on these is not enough. Attackers are increasingly using domains registered long ago. Firstly, domains registered for a longer period are generally perceived as more reputable. Secondly, domains used by APT may have been dormant for several years.
During the domain’s dormancy, malware sends very limited “heartbeat” traffic to the C&C server. Only when the attacker decides to launch follow-up attacks on certain high-value targets does the domain receive more traffic.
For example, the C&C domain avsvmcloud.com used in the SolarWinds supply chain attack was registered in 2018 and remained dormant for two years before starting to receive significant traffic in March 2020. Through Passive DNS data, it was found that traffic to this domain increased by about 165 times after being activated.
Palo Alto Networks quantifies domain activity through DNS traffic within a specific time window. Domains are categorized into three types based on activity: dormant domains (bottom 75%), standard domains (between 75% and 95%), and active domains (top 5%).
Traffic for legitimate services typically grows gradually, but a domain that remains dormant for a long time before suddenly seeing a large amount of traffic is highly abnormal.
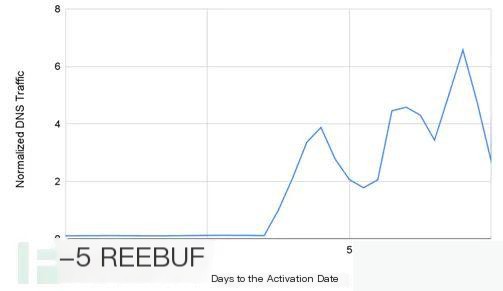
△ Figure 2 Relationship between time and traffic before and after activation
In September 2021, approximately 26,000 strategically dormant domains could be detected daily. As shown above, standardized requests resulted in an average traffic increase of 11.3 times.
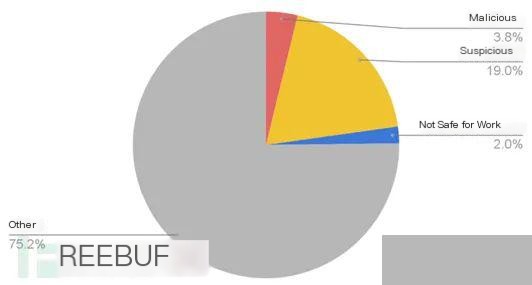
△ Figure 3 Composition of domain classification
These domains are categorized into Malicious, Suspicious, Not Safe for Work (NSFW), and Other, further assessing the threat posed by these domains. Malicious domains include those used for malware, C&C, phishing, or domains deemed malicious by any vendor on VirusTotal. Suspicious domains include parked, suspicious, and high-risk domains. Domains with pornographic, adult, gambling, and similar content are classified as NSFW, and other domains are marked as Other.
3.8% of strategically dormant domains are malicious, which is more than three times higher than the 1.27% of newly registered domains. The sum of Malicious, Suspicious, and NSFW approaches a quarter.
DGA Detection
SolarWinds
During the dormancy period of the SolarWinds supply chain attack, the SUNBURST trojan periodically communicated with the C&C domain avsvmcloud.com, though the traffic was limited.
After the attacker activated the malware, most of the sudden increase in DNS requests was for new subdomains. The SUNBURST trojan generated DGA domain requests in the format DGAstring.appsync-api.region.avsvmcloud.com, which contained encoded victim identity, the domain of the infected organization, and the status of the security products in use.
Upon receiving the request, attackers returned CNAME records pointing to different C&C servers based on the transmitted information.
Detection
To capture similar C&C traffic, Palo Alto Networks actively scans all subdomains of strategically dormant domains and identifies legitimate services based on WHOIS records and other additional information.
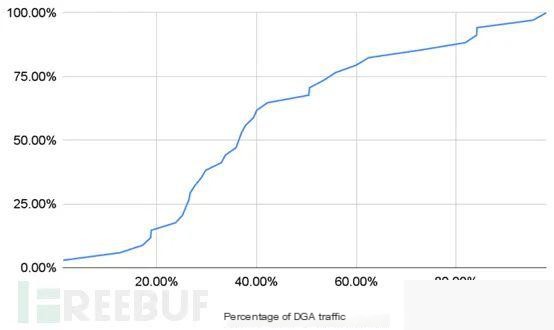
△ Figure 4 Cumulative Distribution of DGA Domain Proportion
On average, two suspicious domains can be identified daily. After activation, each strategically dormant domain roughly has 2443 new subdomains, among which 161 are DGA subdomains. The chart above shows the cumulative distribution function (CDF) of the DGA traffic percentage after activation, where half of the domains have over 36.76% DGA traffic.
APT
In July 2021, abnormal DNS traffic from Pegasus was detected. Two C&C domains detected (permalinking.com and opposedarrangement.net) were registered in 2019 and only generated a significant amount of DGA traffic when put into use in July 2021.
Pegasus can infect iOS and Android devices to collect credential information and track user behavior, including call logs and location records.
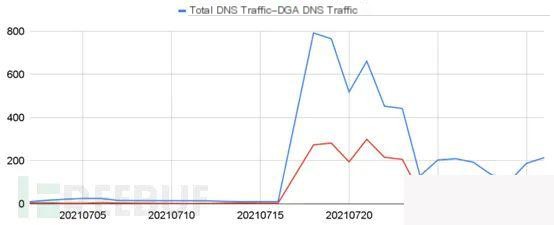
△ Figure 5 Domain Access Statistics
As shown above, prior to July 18, 2021, there were an average of 15 domain requests per day. After activation, DNS traffic increased 56 times. Overall, DGA traffic increased with the overall traffic, and the proportion of DGA traffic also significantly rose. Before July 18, the DGA traffic percentage was 23.22%, after which it was 42.04%.
Phishing
Attackers also use DGA subdomains in phishing attacks similar to those seen in the SolarWinds supply chain attack, effectively providing a layer of proxy between actual malicious websites. When specific parameters exist in the URL, visitors are redirected to another phishing DGA domain, gjahqfcyr.cn. Otherwise, users are redirected to legitimate banking websites.
Thus, this domain possesses a cloaking function, hiding actual phishing content from non-victims and crawlers. On October 2, 2021, an abnormal surge of DGA subdomains was found for ui1io.cn.
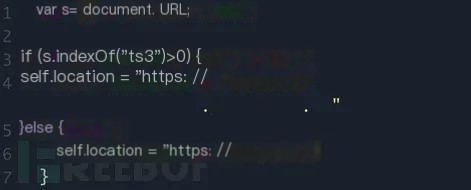
△ Figure 6 Page Redirect Logic
Phishing attacks will also use DGA strings to generate domains for domain squatting. These strings separate the deceptive part from the root domain, such as mailingmarketing.net, which was registered in 2020.
It was detected as a strategically dormant domain on September 23, 2021, with 47 new DGA subdomains. Due to the domain’s length, victims may only notice the initial part and assume it’s a legitimate login domain, especially since mobile browsers typically cannot display the full FQDN.
Wildcard Abuse
Some malicious actors also use DGA subdomains to construct infrastructure, like a wildcard record of fiorichiari.com directing all subdomains to the same IP address.
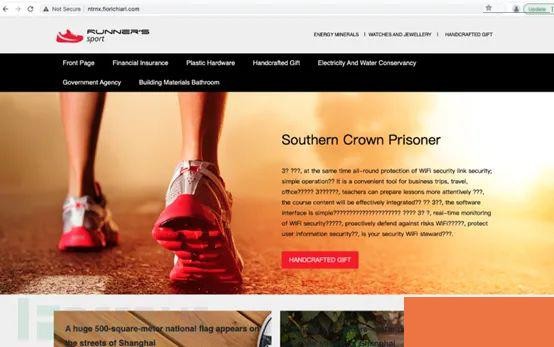
△ Figure 7 Website Deployed on Domain
The service operator registered the domain on July 27, 2021, followed by a sudden increase in DNS requests on September 29, 2021.
These domains are linked to randomly generated websites with text content filled using a website template populated with random strings, presumably used for black hat SEO purposes by malicious actors.
Conclusion
Attackers are increasingly inclined to register domains long before any attack actions. The malware used in APT can remain dormant for a long time, only to generate more traffic suddenly when activated. Based on this characteristic of sudden traffic increase, it’s crucial to detect strategically dormant domains.
Reference Source
Palo Alto Networks


