Hello everyone, nice to see you again, I’m your friend, Full Stack Jun.
SSL: (Secure Socket Layer), located between a reliable connection-oriented network layer protocol and an application layer protocol, is a protocol layer. SSL achieves secure communication between the client and server through mutual authentication, ensuring integrity with digital signatures, and ensuring privacy through encryption. The protocol consists of two layers: the SSL Record Protocol and the SSL Handshake Protocol.
TLS: (Transport Layer Security), used to provide confidentiality and data integrity between two applications. The protocol comprises two layers: the TLS Record Protocol and the TLS Handshake Protocol.
SSL/TLS is positioned between the transport layer and the application layer, wherein application layer data is not transmitted directly to the transport layer but is passed to the SSL layer. The SSL layer encrypts the data received from the application layer and adds its SSL header.
The basic process of the SSL/TLS protocol is as follows: (1) The client requests and verifies the public key from the server. (2) Both parties negotiate to generate a “session key.” (3) Both parties use the “session key” for encrypted communication.
First, start Wireshark and open a browser to access a website using HTTPS encryption, browse, capture packets, and find that the contents of the packets cannot be seen (because the session is encrypted). Since the browser records the session keys used to encrypt TLS packets in the form of log files, you can specify this file in Wireshark to achieve decryption.
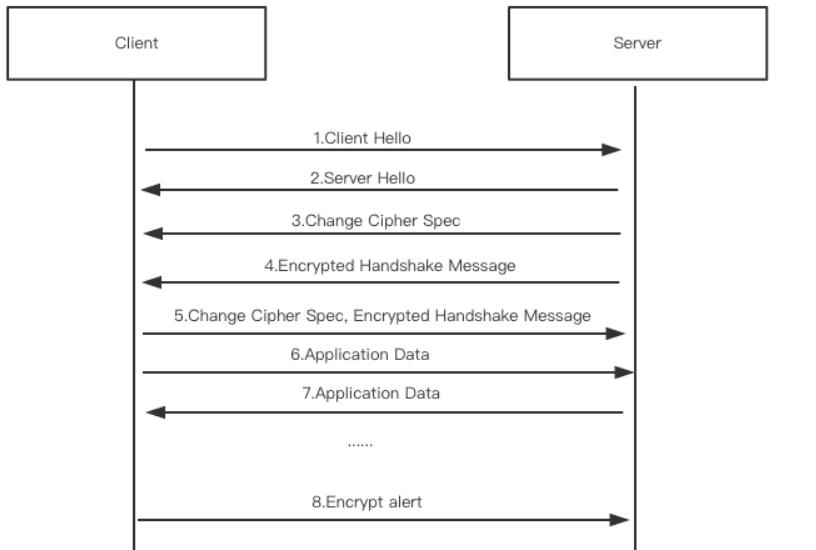
The figure below shows the process of establishing an SSL session:
Below is the packet capture operation:
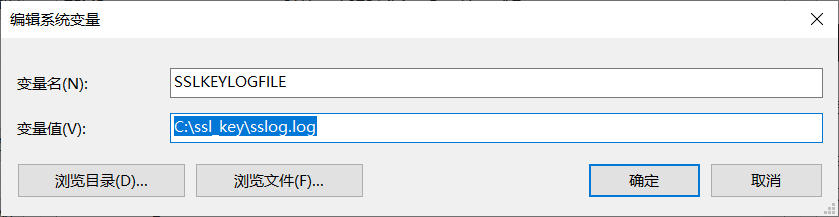
Configure Environment Variables
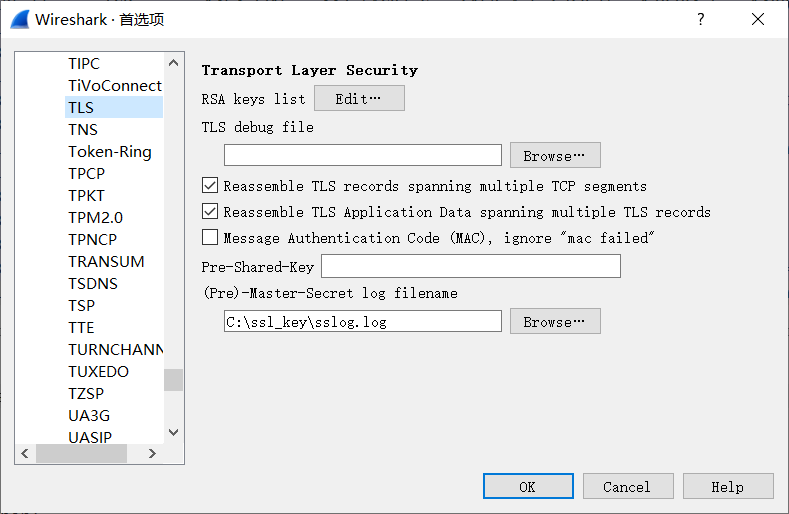
Configure Wireshark to set the file path
Restart the browser and Wireshark to start capturing packets! Filter the captured packets with the filtering rule: ip.addr == 23.99.125.55 && ssl
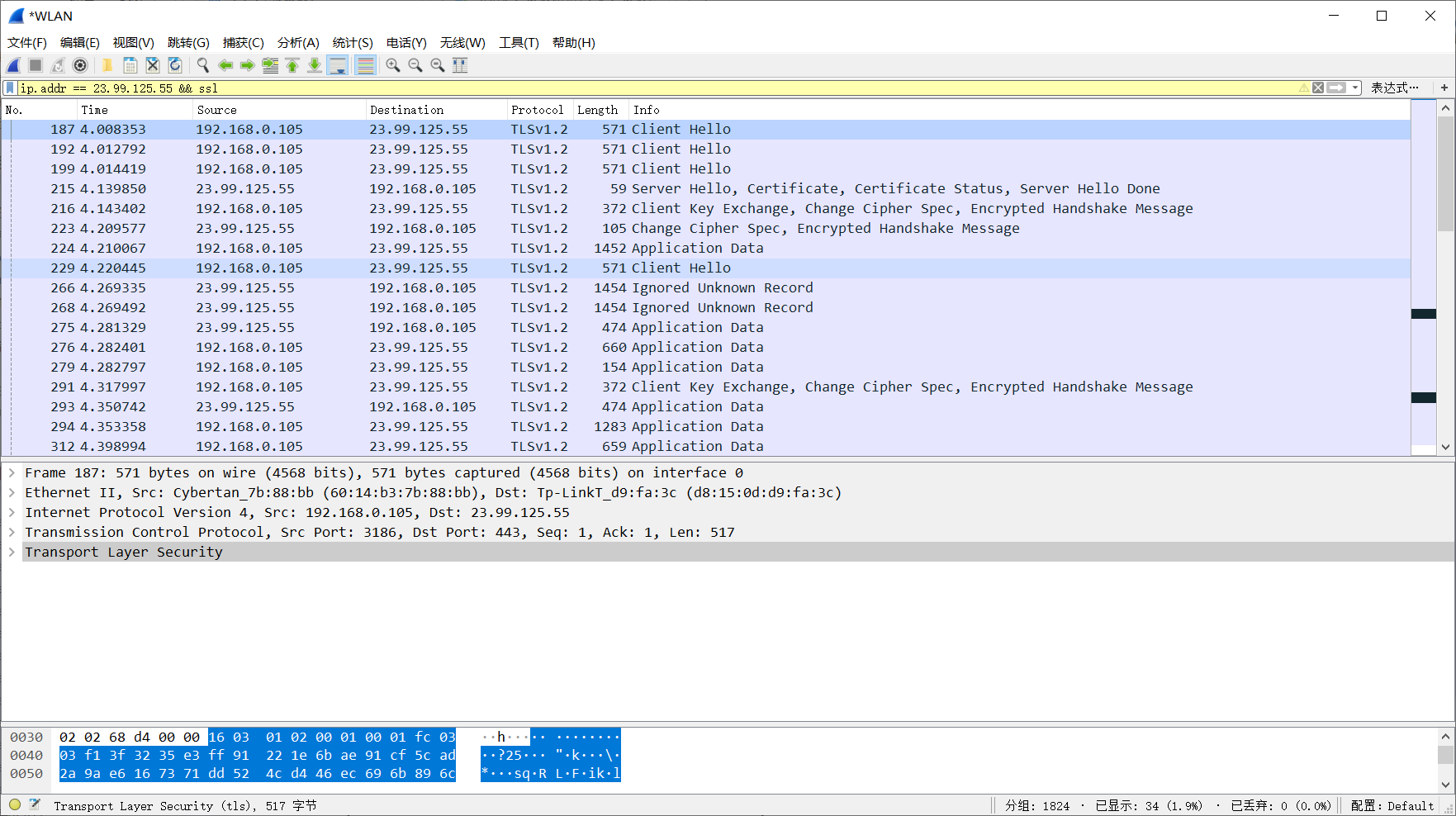
Using Wireshark to filter SSL traffic, you can see several distinct SSL session establishment packets, such as client hello, server hello, etc. Examine the details of the captured packets:
1. Client Hello
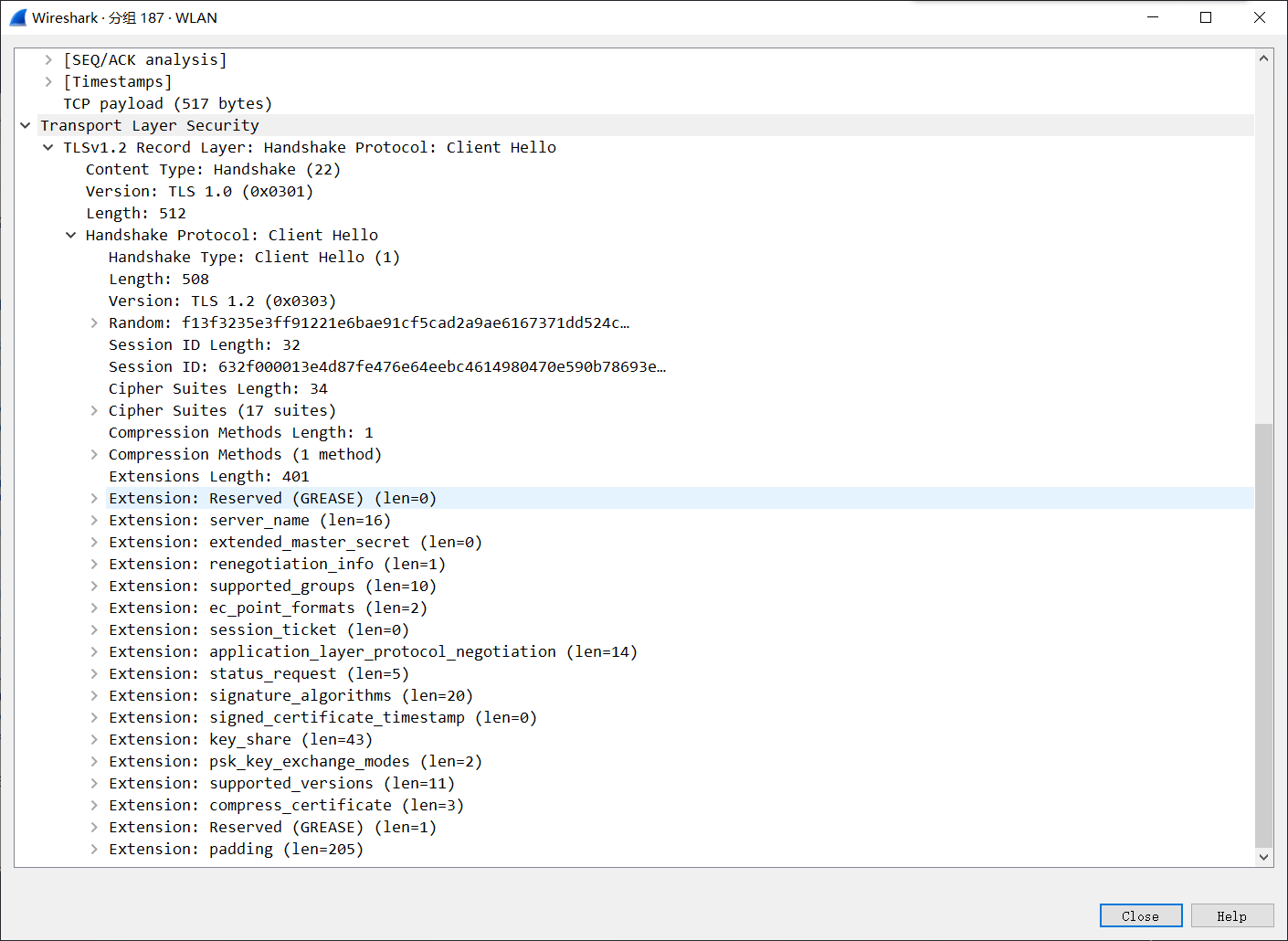
It’s not hard to see that in this handshake process, the client transmitted the following information in plaintext:
2. Server Hello
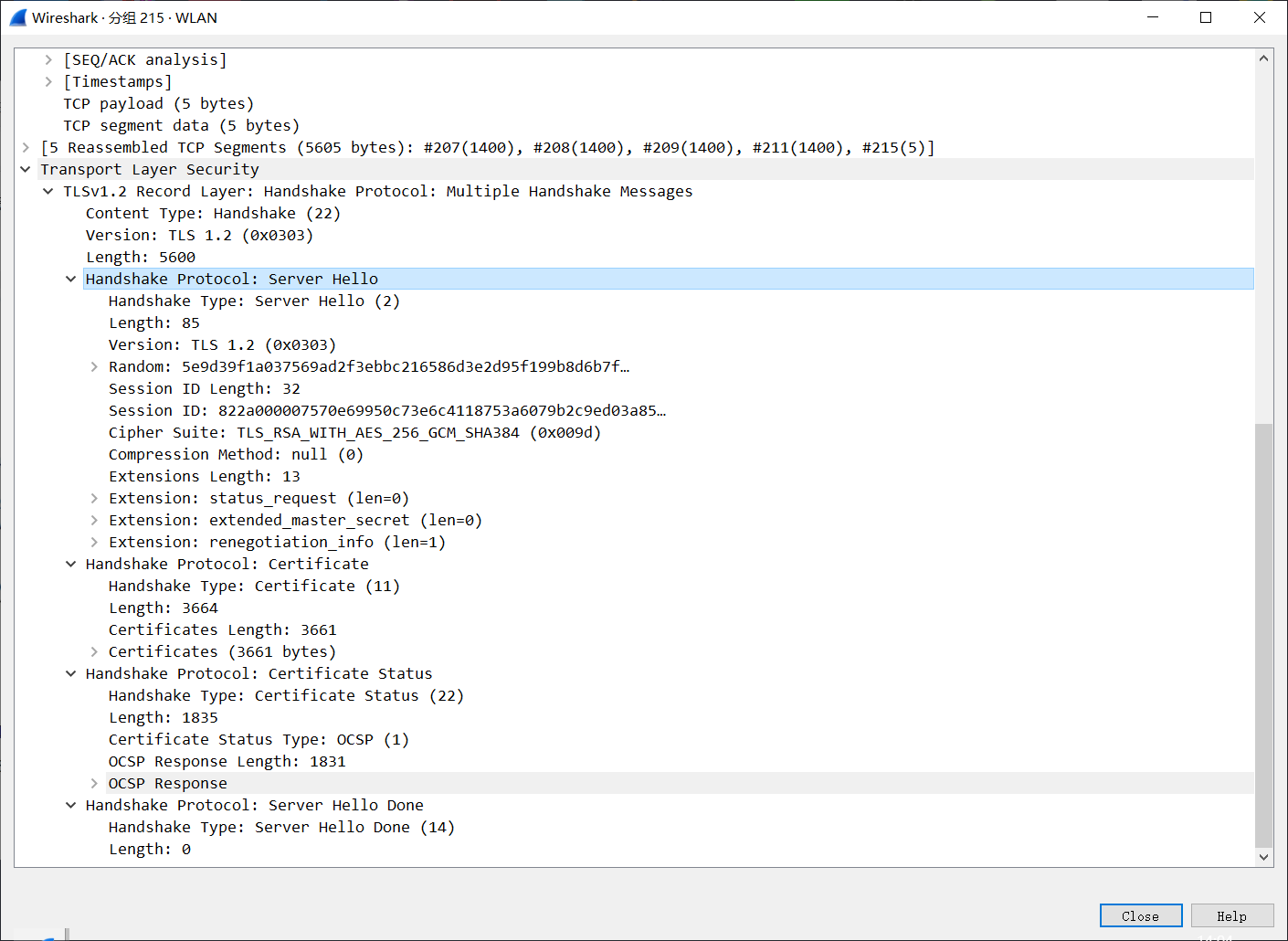
At this stage, the server returns the selected protocol version (Version), cipher suite, compression algorithm, random number, Session ID, etc., and at the same time, it sends its certificate (containing its public key) to the client (Certificate).
3. After the SSL handshake, the data transfer occurs, the server’s identity is successfully authenticated, and the encryption algorithm AES and key xxxxx are negotiated (the client and server use the same algorithm to calculate three random values without plaintext transmission). Everything is ready. The successful SSL handshake means that all application-layer protocols can transfer encrypted data. Therefore, hash all previous handshake messages, encrypt them, and send them to the server.
Application Data Application data transmission message. Because this is HTTPS, HTTP application protocol data can be encrypted and then transmitted.
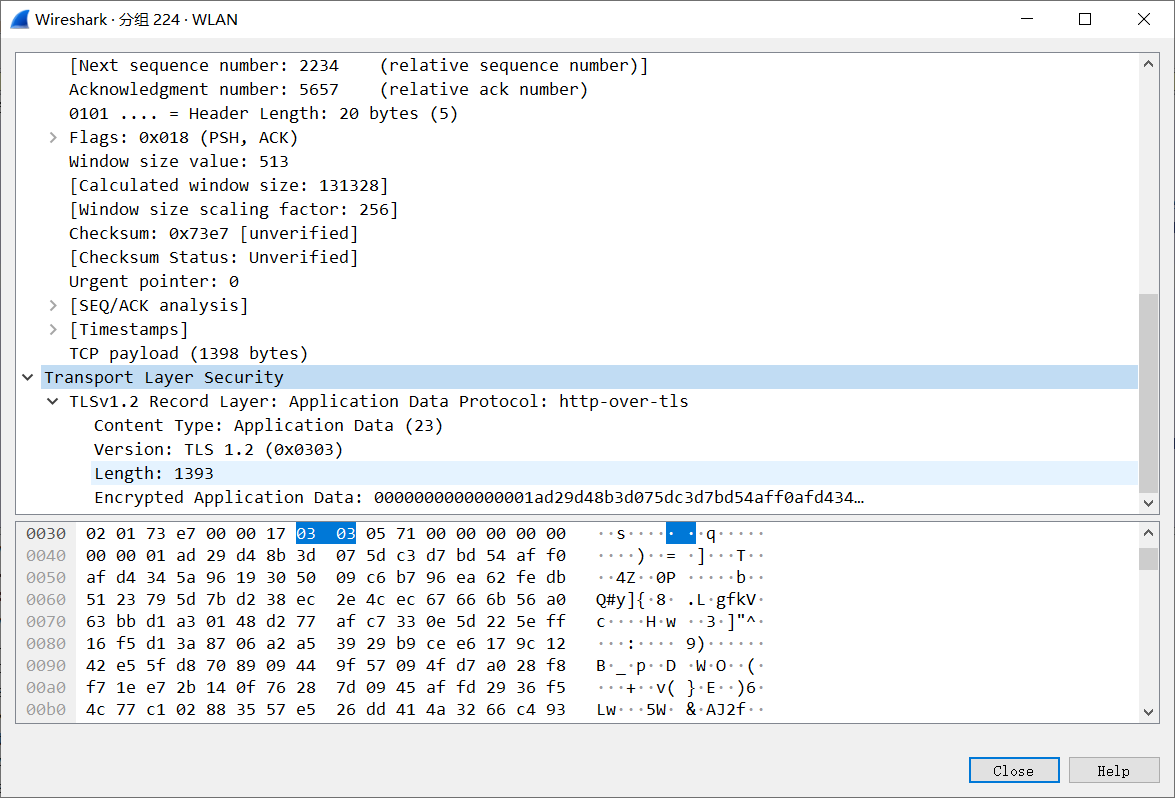
From here, without knowing the key, it is impossible to know what data is being transmitted or even what protocol’s content is being conveyed. Therefore, previously creating an SSL tunnel for the proxy server to blindly transmit HTTPS data required the CONNECT method to inform the proxy server which host and port number to connect; otherwise, the proxy server would be confused. Thus, the SSL protocol is very independent, it encrypts HTTP here, but it can encrypt other protocols as well. It acts as an intermediary layer between TCP and application-layer protocols, providing encrypted data transfer for upper-layer protocols.
Encrypted Alert SSL alert message, because it is encrypted content, Wireshark alone cannot display the contents of the alert. Alert messages are often just used by the client to signal the end of SSL transmission to the server, which aligns with the captured packet content. Therefore, this is merely a signal of the end of SSL transmission. After sending the Encrypted Alert, the client completes data transmission and prepares to terminate the TCP connection with four handshakes. Tried several times but couldn’t find this packet, possibly related to not disconnecting normally.



