ssh logs show client authentication methods
During an emergency, I found an SSH connection method called Accept keyboard-interactive while inspecting the SSH logs. Since keyboard-interactive is not commonly encountered, I have compiled the various SSH login methods.
In Xshell, you can see the following authentication methods.
The most commonly used SSH methods are Password and Public Key, so I won’t elaborate on those.
What is keyboard-interactive authentication?
To summarize: keyboard-interactive and Password are essentially the same, both are password-based authentication methods. Keyboard-interactive authentication requires you to manually input the password.
However, during actual testing, the SSH server was configured with keyboard-interactive. Using Xshell as an example, the client selected the keyboard-interactive method and saved the password. The client will handle the password input process for you. Therefore, there is essentially no difference between keyboard-interactive and password authentication, except for the difference in SSH log records on the server.
By using the ssh -v parameter, you can see the details of the SSH connection process.
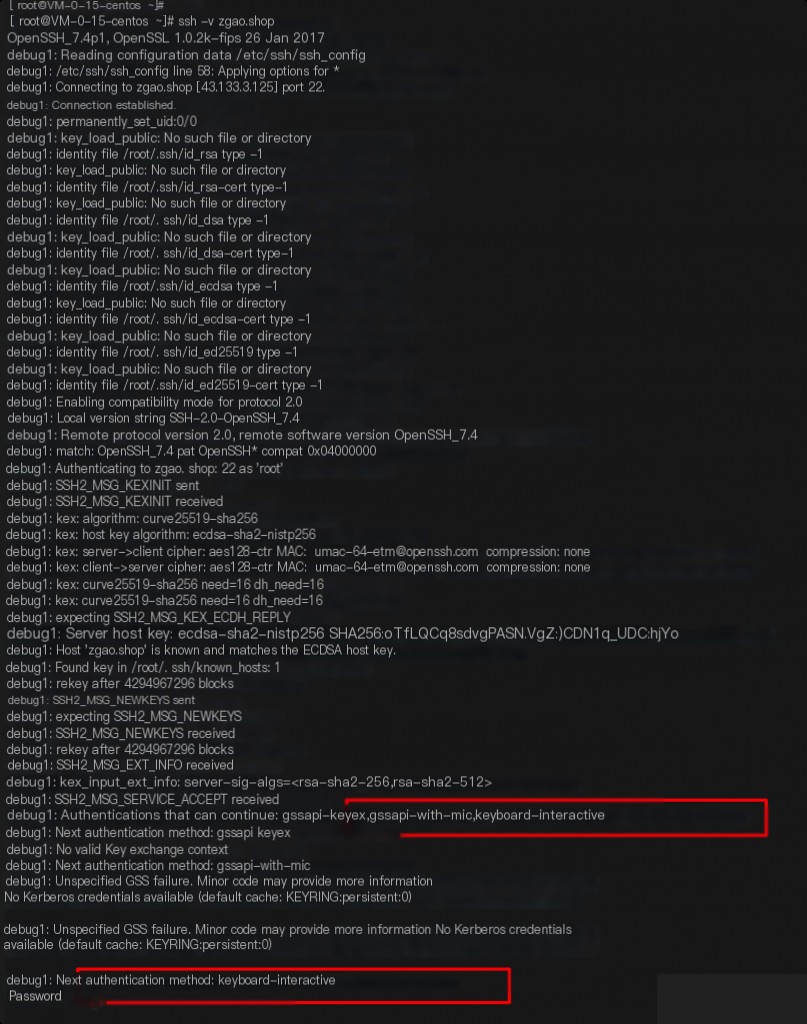
On the machine zgao.shop, I modified the configuration file to allow only keyboard-interactive authentication.
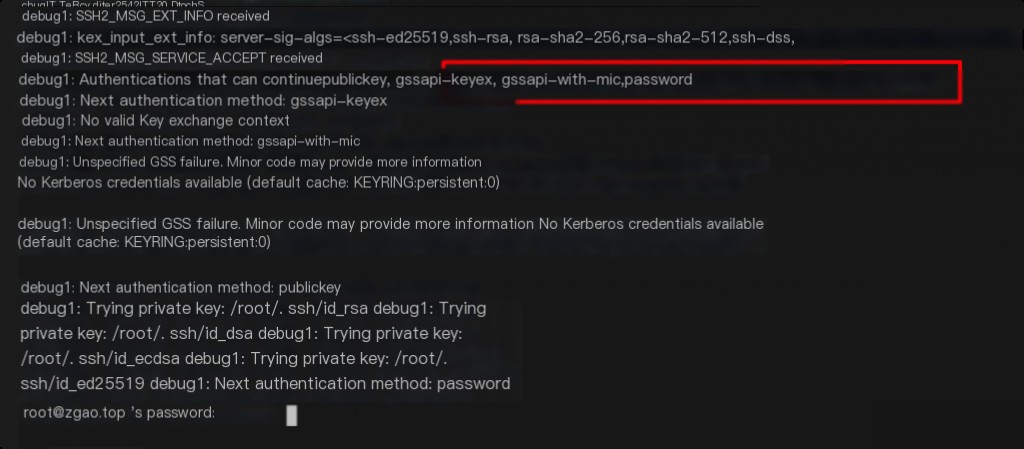
Similarly, on the machine zgao.top, I used the default configuration, allowing both password and public key authentication. The effects are identical.
At this point, modify the sshd configuration file on zgao.top, setting PasswordAuthentication to yes (default is off). This will enable keyboard-interactive authentication.
Now, all authentication methods are supported.
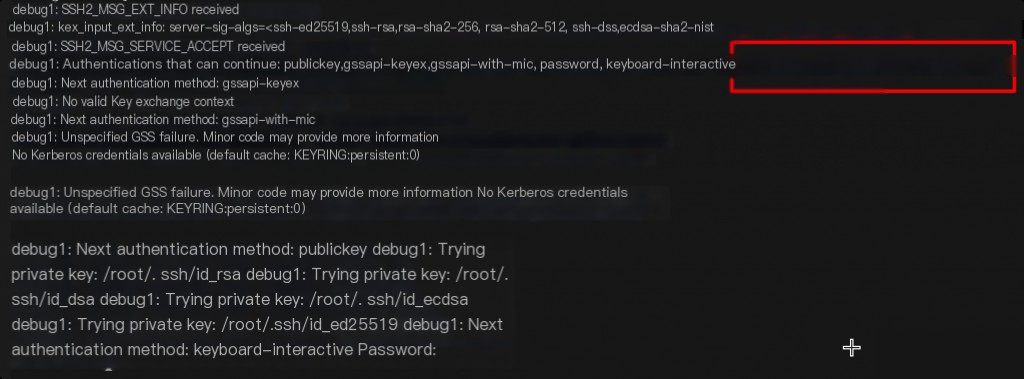
However, keyboard-interactive appears first, not Password authentication.
By examining the images above (paying close attention to the connection order), you can determine the order of SSH authentication methods.
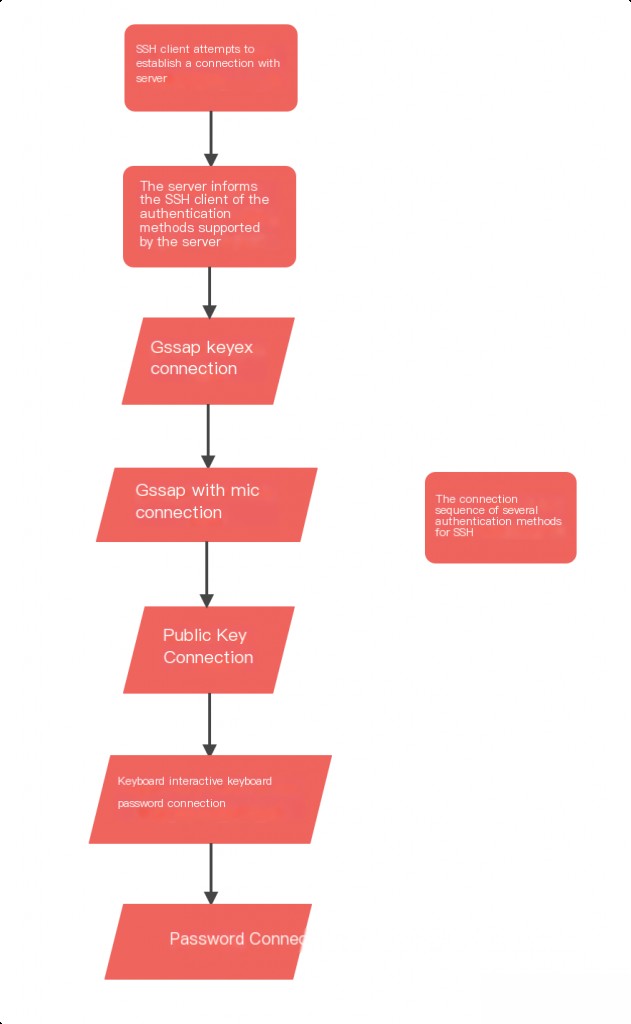
Password is the last method attempted among all SSH authentication methods.
What is GSSAPI?
This authentication method is rarely encountered. What is the specific configuration related to GSSAPI? The main configuration is GSSAPIAuthentication, which defaults to yes.
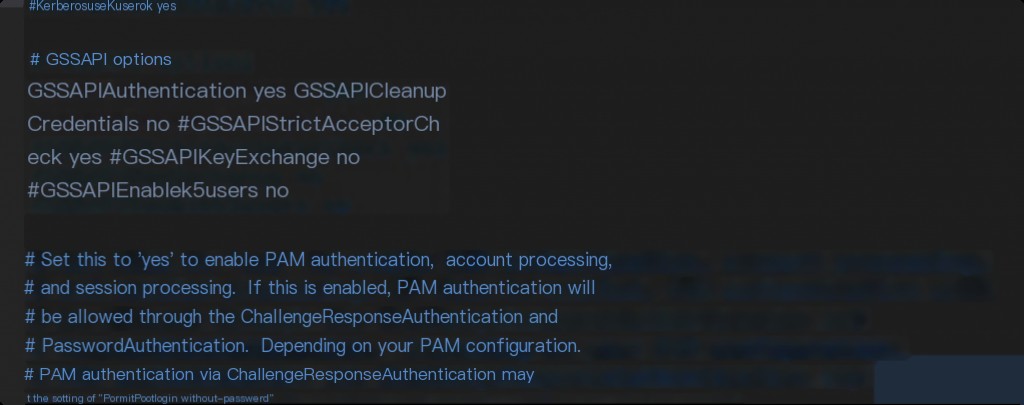
Searching for GSSAPI online reveals many pages discussing slow SSH logins and suggesting changing GSSAPIAuthentication to no to speed up SSH logins.
Here is some related information:
GSSAPI: It is a set of generic network security system interfaces. This interface encapsulates various client-server security mechanisms to eliminate differences in security interfaces and reduce programming complexity. Its most notable implementation is based on Kerberos. Generally, when referring to GSSAPI, it implies the Kerberos implementation.
GSSAPI-related authentication consumes more time, which can be observed in the SSH connection logs. Since GSSAPI is primarily based on Kerberos, resolving this issue involves configuring Kerberos on the system. Most users do not have Kerberos configured. Therefore, it is best to disable GSSAPIAuthentication on the SSH server, and the client can disable it as well.
What is PKCS11 authentication?
Mentioning PKCS11 brings up Yubikey. This authentication method is akin to storing the key on a USB drive.
Yubikey is a USB device (essentially a USB keyboard) with several uses:
- One-time password (OTP) generator, providing verification codes for online account logins (highly recommended! Much more secure than SMS verification codes);
- Personal password storage;
- Proof of personal digital identity (Oauth);
- PGP key storage;
- SSH key storage.
Benefits: It is portable, allowing you to log in to VPS on multiple computers without the worry of having your private key stored on a local computer and being forensically retrieved.
Xshell also provides CAPI, what is that?
After searching extensively, there is limited information available. It appears to be related to smart cards. I am not entirely sure, so if anyone has more knowledge, please feel free to share.


