Abstract: Snort Workflow
The popularity of the Internet has deeply affected the whole world, making the whole world more closely connected. Although it brings convenience to people living in the global village, it also threatens people’s daily lives. Thus, an intrusion detection system plays an essential role in the research of intrusion detection, acting as an active and real-time security measure. It is mainly through the collection and analysis of computer external and internal information, to determine whether there is a suspicious intrusion phenomenon, to complete the warning of intrusion and achieve the role of defense, thereby reducing the harm of network intrusion to the lowest degree. This paper mainly discusses the overview of the intrusion detection system based on Linux. Snort is deeply analyzed in terms of the related technology and operation process of the structure of the intrusion detection system to expand and implement the relevant rules. In the design, we use Lipacp to acquire network packets, while Snort acts as the intrusion detector to analyze the packets in real-time. A MySQL database is used to store intrusion detection logs. Apache serves as the HTTP server, BASE acts as the web-based intrusion event database analysis platform, and Barnyard stores the alarm logs in the database. In order to implement BASE, Apache is used to provide network services, and BASE is used as the analysis platform to view and analyze the MySQL database. Finally, the debugging results are recorded and summarized.
Keywords: Snort; intrusion detection; IDS; network security
Introduction
As humanity entered the 21st century, because computer networks are open and interconnected, they are often subject to attacks by network “hackers” and other intrusive activities containing viral programs. To prevent and mitigate these hazards as much as possible, intrusion detection technology has become a critical research focus and challenge. Consequently, the Snort intrusion detection system was developed. It supports multiple platforms and its primary function is to capture network data packets for analysis, then match them against predefined rules, recording different attack patterns so that future occurrences can be swiftly detected using the rule database. This system effectively reduces detection errors, significantly improving the efficiency of intrusion detection, and allows secondary development of the detection model, making it increasingly crucial to develop Snort on the Linux platform.
However, Snort’s interface is not user-friendly; its user interface is still based on command-line character methods, making configuration and use cumbersome and prone to errors. Due to the design of Snort, comprising many interconnected modules, correct installation at every step is required. One misstep can lead to system-wide configuration errors, making it difficult for users to successfully and correctly complete the installation.
The Snort detection system has developed the most basic detection framework and supports third-party plugins’ deployment. Its source code is written in C, allowing secondary development, and has progressively garnered attention. Many countries have begun to study Snort’s analysis and research, applying it to small and medium enterprises. The current mainstream research includes:
- Constantly extending third-party plugins for attack detection, such as supporting various network protocol detection functionalities and optimizing a more user-friendly main interface for easier human-computer interaction, thereby expanding detection capabilities.
- Incorporating machine learning and deep learning into the system to continuously strengthen detection capabilities through self-learning, learning more rule sets, and improving rule match rates to enhance detection efficiency.
This project focuses on the design and implementation of an intelligent intrusion detection system based on the Linux platform. A CentOS host under Linux provides real-time intrusion detection functionality. The goal is to minimize user intervention on the host, thereby facilitating user control. To make the operation of the Snort system easier for users, a web-based control console is provided, reducing deployment complexities and making operations simpler. This paper is divided into four chapters:
Chapter One: Introduces the relevant concepts of intrusion detection based on Linux and explains technical principles with Snort as the core. Rulesets are also introduced in this chapter for a fundamental understanding of SIDS.
Chapters Two and Three: Respectively introduce the system’s requirements, database design, and the implementation of the intrusion system on the Linux platform. Mainly focusing on implementing SIDS, which is rich and comprehensive in functionality, this project chooses a web interface console with a database to achieve intrusion detection and log recording.
Chapter Four: Validates and analyzes the completed system. Each function implemented in the system is tested to ensure it can detect attacks accordingly, guaranteeing proper system operation.
1 Overview of Intrusion Detection and Snort
Intrusion detection is the process by which a computer receives data from the network and then inspects the collected information. If any attack or intrusion that poses a threat to the host is detected, the system will actively provide comprehensive protection for the host by combining software and hardware. Among various intrusion detection security management tools, Snort is currently the most mainstream and promising system.
1.1 Concept of Intrusion Detection System
Intrusion detection acts as a significant supplement to the firewall and aids in responding to network attacks, enhancing the security management features for system administrators (including security audits, monitoring, attack recognition, and response) to reinforce the integrity of the information security infrastructure. It collects information from several critical points in the computer network system and analyzes this information to determine whether any security policy violations or signs of attacks exist in the network.
The most crucial aspect of any intrusion detection system is how effectively it performs detection. Intrusion detection can generally be categorized into anomaly detection and misuse detection. Based on the information source, it can be divided into Host-based Intrusion Detection System (HIDS) and Network-based Intrusion Detection System (NIDS). HIDS investigates detection through the system logs and audit records of the host system, while NIDS analyzes network data packets. HIDS deployment is more cumbersome and costly, while NIDS deployment is simpler and cost-effective. HIDS has specific monitoring capabilities but heavily relies on the host’s logs. In contrast, NIDS has better real-time performance and portability but struggles with large-scale data detection. A comprehensive intrusion detection system, therefore, combines both HIDS and NIDS.
1.2 Snort System
Snort is a free, open-source, lightweight network intrusion detection system developed in C and based on Lipacp. It can be deployed cross-platform on various systems like Linux and Windows, offering data and rule-based functionalities to detect potential threats. As an open-source system, developers can freely modify Snort’s source code to expand its capabilities. This flexibility and ease of use make Snort an attractive option. Figure 1.1 illustrates the typical operating environment of Snort.
1.3 Features of Snort
Snort possesses multi-platform capability and scalability as an intrusion detection system. By obtaining data from the network, Snort is defined as a network-based intrusion detection system. It extracts features for each intrusion behavior, writes them into rules following specifications, thus forming a rule library. Snort then matches captured data packets against this rule library. If a match is found, the behavior is recognized as an intrusion. Snort’s characteristics are as follows:
- Snort can be deployed on multiple platforms, offering extensibility across different systems.
- It has real-time analysis and network packet acquisition capabilities, enabling swift responses to network intrusions while issuing alerts. The system provides multiple alerting methods.
- Snort supports flexible log formats, including Topdump’s binary format, ASCII character form, and XML format, making maintenance and inspection more convenient.
With its extensive functionalities, Snort stands out against other intrusion detection systems. It is currently at its peak development, with continuous enhancements being made by researchers and developers. Soon, Snort is expected to become the most extensive detection system.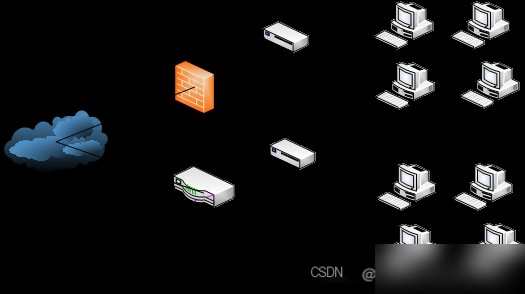
Figure 1.1 Schematic of Snort Deployment
1.4 Snort Rules
Snort is essentially a rule-based intrusion detection system that parses data packets to extract rules and matches them against a predefined rule chain in the rule library. Hence, the rule set comprises numerous rules organized based on attributes like source IP, destination IP, source port range, and destination port range. Intrusion detection then occurs in two steps: first, capturing network data packets, and second, matching these packets against the rule set. A successful match indicates a threat, prompting Snort to issue an alert. If no matches are found, the data is deemed secure.
- 4.1 Structure of Rules
Generally, Snort rules can be logically divided into two parts: the rule header and the rule options [10]. As shown in Figure 1.2.

**Figure 1.2 Snort Rule Structure**
The most important part of a Snort rule is the rule header. It consists of seven parts: rule actions, network protocol, source network address and port, direction flag, target address, and port. Snort restricts the actions through the protocol in the rule header. The basic structure of a Snort rule header is shown in Figure 1.3.

**Figure 1.3 Snort Rule Header Structure**
4.2 Rule Header
1. Rule Actions
Rule actions are located at the beginning of a Snort rule and execute the action that matches the rule conditions. Snort provides five predefined types of actions, and users can also define custom rule actions. The predefined actions are Log, Pass, Activate, Alert, and Dynamic.
– Log: Record to the log.
– Pass: Allow the packet to pass.
– Activate: Trigger an action based on the detection result.
– Alert: Generate an alert based on the result.
– Dynamic: Perform dynamic actions, which run in conjunction with Activate.2. Protocol
The protocol field is the second part of the Snort rule header, indicating the protocol type. Currently, there are four main types: TCP, UDP, IP, and ICMP. Future protocols may include IPX and OSPF. When the protocol is specified in the header, the specified protocol action is initiated.3. Network Addresses
Typically, addresses include two types: source network address and destination network address. A specific address can refer to an IP address. The keyword “any” represents any valid address. Network addresses can be specified using a slash and a number, e.g., /16 for a Class B network, /24 for a Class C network, and /32 for a specific address. The operator “!” can be used to exclude an address from the rule, notifying the Snort system to consider all IPs except the specified ones.4. Port Numbers
Port numbers have several operational rules. Any valid port number can be indicated using the keyword “any,” such as log tcp any any -> 192.168.17.0/24. Static port numbers, like port 80 for HTTP and port 23 for Telnet, can also be used. Port ranges can be indicated using the “:” symbol, e.g., 1:1024 represents ports 1 to 1024.5. Direction Indicator
The direction indicator specifies the direction of the source and destination determined by the rule. “->” indicates the source address on the left and the destination port on the right. “<-” indicates the destination address on the right and the source port on the left. “<>” can be used to represent bidirectional traffic conveniently.4.3 Rule Options
Rule options are the most crucial components in the Snort detection system. They define the alert information and the data packet characteristics to be inspected. Snort rule options are enclosed in parentheses, with each option separated by a “;”. When rule actions are executed, the conditions specified in the options must be met. An option includes two key parts: a keyword and a variable value [11]. Some common keywords include msg, flow, and ack.1.5 Summary of This Chapter
This chapter introduces the overall concept of the Snort system and its functions. I elaborated on the main rules of Snort, which are primarily composed of two parts. The characteristics and structure of these two parts were further discussed.2. Requirements Analysis and Overall Design
This chapter focuses on deciding the division of modules based on system analysis and their relationships. It explains the design of functional structures and clarifies the specific tasks each module needs to accomplish, providing an overall system and functional structure design. Finally, it details the specific design processes of each module, key business activities, the main design components of the system, and the database table design, determining the structure and specific content of the tables.
2.1 Necessary Functional Requirements Analysis
Functional requirements analysis is the foundation of any project, determining the essential functions needed by the system. This project achieves the following functionalities based on the survey results:(1) Capturing Network Packets
The first and most fundamental step in network detection is capturing network packets. Once the packets are captured by Lipacp, they are analyzed to check for any threats.(2) Analyzing Packet Information
Analyzing packet information is the core module of the system. Its primary function is to verify the risks of intrusion by inspecting the captured data.(3) Threat Alerting
Users originally could not see intrusion detection results directly, so alert messages display whether intrusion attempts have been detected.(4) Storing Detection Information
Detected information should not be discarded directly; it needs to be stored in a database for future reference and analysis, enabling users to view the information later and aiding in data statistics and visualization.2.2 Database Design
The system uses MySQL as its database. Since detection and analysis packet data are stored in the database, it is necessary to design tables based on packet information. Each protocol’s corresponding data is separately analyzed and stored in respective tables for ARP, ICMP, UDP, IP, and TCP. Figure 2.1 illustrates the relationships between these tables.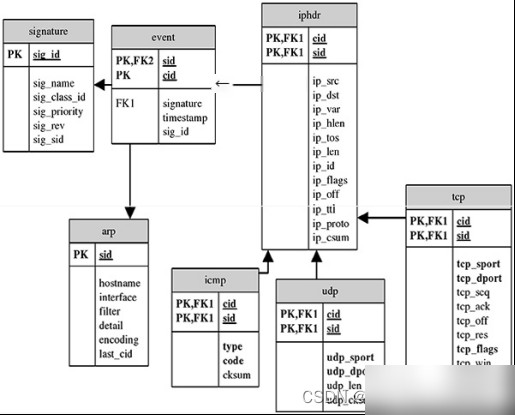
**Figure 2.1 Database Model Diagram**
Next, we introduce the data tables corresponding to each protocol:
(1) ICMP Protocol Information Table
Table 2-1 outlines the ICMP protocol packet header, recording main ICMP data such as sensor ID, event ID, type, and identifier.Table 2-1: ICMP Data Table
| Field Name | Type | Length | Note |
|————–|———-|——–|——————–|
| Sid | int | 20 | Sensor Identifier |
| Cid | int | 20 | Event Identifier |
| Icmp_type | tinyint | 20 | Type |
| Icmp_code | tinyint | 20 | Code |
| Icmp_csum | smallint | 20 | Checksum |
| Icmp_id | smallint | 10 | Identifier |
| Icmp_seq | smallint | 10 | Sequence Number |(2) UDP Protocol Information Table
Table 2-2 details the UDP protocol packet header, including destination port and other UDP information.Table 2-2: UDP Data Table
| Field Name | Type | Length | Note |
|————–|————|——–|——————————|
| Cid | int | 20 | Event Identifier |
| Sid | int | 20 | Sensor Identifier |
| Udp_sport | smallint | 10 | Source Port (≤ 1024) |
| Udp_dport | smallint | 10 | Destination Port (≤ 1024) |
| Udp_len | smallint | 20 | Datagram Length (≤ 1024) |
| Udp_csum | smallint | 20 | Checksum |(3) TCP Protocol Information Table
Table 2-3 identifies the TCP protocol packet header, including offset, sequence number, flags, and other information.Table 2-3: TCP Data Table
| Field Name | Type | Length | Note |
|————–|————|——–|——————————|
| Sid | int | 20 | Sensor Identifier |
| Cid | int | 20 | Event Identifier |
| tcp_sport | smallint | 10 | Source Port |
| tcp_dport | smallint | 10 | Destination Port |
| tcp_seq | int | 20 | Sequence Number |
| tcp_ack | int | 20 | Acknowledgment Number |
| tcp_off | tinyint | 10 | Offset |
| tcp_res | tinyint | 10 | Reserved |
| tcp_flags | tinyint | 10 | Flags |
| tcp_win | smallint | 10 | Window Size |
| tcp_csum | smallint | 20 | Checksum |
| tcp_urp | smallint | 20 | Urgent Pointer |(4) IP Packet Information Table
Table 2-4 records IP packet header information, including sensor ID, source IP, destination IP, protocol version, and other details.Table 2-4: IP Data Table
| Field Name | Type | Length | Note |
|————–|————|——–|——————————|
| Sid | int | 20 | Sensor Identifier |
| Cid | int | 20 | Event Identifier |
| ip_src | int | 10 | Source IP |
| ip_dst | int | 10 | Destination IP |
| ip_ver | tinyint | 20 | Protocol Version |
| ip_hlen | tinyint | 20 | Header Length (≤ 1024) |
| ip_tos | tinyint | 10 | Type of Service |
| ip_len | smallint | 20 | Total Length (≤ 1024) |
| ip_id | smallint | 20 | Data ID |
| ip_flags | tinyint | 10 | Flags |
| ip_off | smallint | 20 | Offset (≤ 1024) |
| ip_ttl | tinyint | 10 | Time to Live |
| ip_proto | tinyint | 20 | Protocol Type |
| ip_csum | smallint | 10 | Checksum |(5) Alert Metadata Table
Table 2-5 shows the metadata for alerts, including signature name and timestamp.Table 2-5: Event Data Table
| Field Name | Type | Length | Note |
|————–|———–|——–|——————————|
| Sid | int | 20 | Sensor Identifier |
| Cid | int | 20 | Event Identifier |
| signature | varchar | 10 | Signature Name |
| timestamp | varchar | 10 | Timestamp |(6) Rule-style Alert Information Table
Table 2-6 outlines alert rule information, including ID, name, class ID, priority, and other details.Table 2-6: Signature Data Table
| Field Name | Type | Length | Note |
|————- |———–|——–|——————————|
| sig_id | int | 10 | ID |
| sig_name | varchar | 50 | Name |
| sig_class_id | int | 10 | Class ID |
| sig_priority | int | 10 | Priority |
| sig_rev | int | 10 | Revision Number |
| sig_sid | int | 10 | Total Alert Types |2.3 Overall Snort Framework
The Snort architecture consists of four plugin modules: packet capture, preprocessor, detection engine, and alert module. The framework is shown in Figure 2.2.
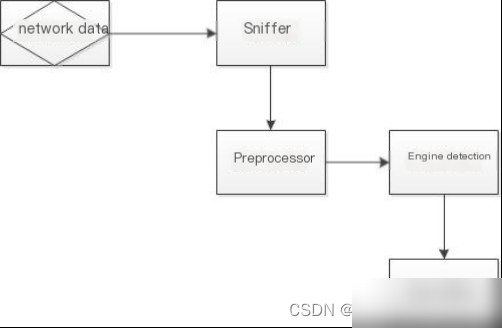
**Figure 2.2 System Architecture Diagram**
(1) Capturing Network Packets
Sniffing refers to capturing network packets. Two programs are needed for capturing packets: one to set the host’s network card to promiscuous mode and another to select different packet capture tools depending on the host’s system (Winpcap for Windows, Lipacp for Linux). This course is based on using Lipacp forFigure 2.3 Snort Workflow The first step of the Snort system is the initialization process, followed by parsing the rule file. A rule chain is formed from the rule file and stored in the rule library to prepare for future rule matching. Subsequently, using the Lipcap library, Snort captures packets from the network, which are then analyzed by the preprocessor using decoded packets. The results of this analysis are compared with the rule chain in the rule library. If an anomaly is detected, it is sent to the output module to alert the user through logs or warnings. Otherwise, the packet is discarded.
- 3.2 Operating Modes Snort can be run in three modes: sniffing mode, packet logging mode, and network intrusion detection mode. The most fundamental and primary mode is sniffing mode. It is closely related to packet logging mode; however, their output formats differ. Network intrusion detection mode is the most standard and requires certain plugin functionalities based on the specific needs.
1. Sniffing Mode Sniffing mode captures packets from the network, analyzes them, and displays them on the host, as shown in Figure 2.4.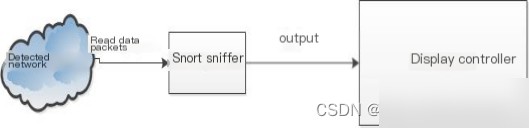
Figure 2.5 Snort Network Intrusion Detection Mode On Linux, this mode can be started with the command: snort –v When the sniffing mode is successfully activated, data analysis and statistics, including network protocols such as TCP, UDP, ICMP, etc., are performed. When sniffing mode stops, the statistical data is displayed on the host.
2. Packet Logging Mode Packet logging mode, built on sniffing mode, does not merely display data on the screen but rather stores it on the host’s memory. A new log directory is created in Linux, where Snort stores the data in text format, which can be customized based on user requirements.
3. Network Intrusion Detection Mode As shown in Figure 2.5, in network intrusion detection mode, Snort first captures network packets for analysis. If it finds matching intrusion rules in the rule library, it logs the packet and generates an alert. Otherwise, it discards the unmatched packets. On Linux, to run Snort in network intrusion detection mode, use the command: snort -i eth0 -c /etc/snort/snort.conf -A fast Where snort.conf is the configuration file, and eth0 represents the system’s network interface. Snort matches each packet against the rule set and takes appropriate actions for matching packets.Figure 2.5 Snort Network Intrusion Detection Mode
2.4 Chapter Summary This chapter introduces the system’s requirement analysis, database design, overall structure, and workflow. The necessary functionalities are designed based on the requirement analysis. Corresponding databases are designed based on these functionalities. The chapter also explains each step of the Snort system’s architecture and its operating modes. Taking specific rules into consideration helps in detecting information accurately. These steps will be crucial for designing the system in future.3 Detailed Design and Implementation of SIDS
Snort is a highly flexible intrusion detection system. It can be expanded based on user requirements to create a comprehensive intrusion detection system. However, this expansion also increases the system’s complexity. This text focuses on demonstrating Snort’s complete functionality by setting it up on Linux.
3.1 SIDS Implementation Plan Implementing SIDS depends on the different operational environments. Snort can run solely in sniffing mode, capturing binary-formatted data. One can use a text editor like gedit to view this data. However, this data is not saved permanently and is visible only during Snort’s runtime, which is not a great user experience. In such cases, a system with software extensions, such as a database and analysis table software, can be used to transmit captured data to a database and then to the analysis table. This method not only preserves the intrusion data but also provides a clearer view of the intrusion detection status.
Depending on user choices, the network intrusion detection system typically has the following combinations:
(1) Installing a standalone Snort sniffer for simple data packet retrieval.
(2) Installing a sniffer with a log storage system.
(3) A single sniffer with an admin system.
(4) Installing a database and analysis console sniffer.To enable the network intrusion detection system with comprehensive functions, the fourth combination, which includes software with databases and analysis consoles, is selected.
In this setup, there are four hosts named A, B, C, and D. Another host named E connects to D’s network and can communicate with D. Host D doubles as a server for Snort with BASE, MySQL, Apache, and other software on CentOS7. Host F is an external system capable of launching attacks on any host in the internal network. In the system topology (Figure 3.1), each device is assigned an alias to simplify the subsequent design and implementation steps.
Figure 3.1 Sniffer Deployment Mode with Database and Web Analysis Console To achieve the aforementioned functionality, the SIDS system must detect attacks on internal hosts and store the attacked logs using Barnyard into the MySQL database. This enables administrators to view the data clearly. phpMyAdmin, an open-source database management tool, can facilitate data analysis and research, allowing for data editing and deletion based on user needs.
The Snort system is enhanced with various third-party plugins for greater efficiency and user convenience, aiding more effective detection. The plugins and their functions are listed below:
(1) Lipacp captures network data packets.
(2) MySQL database stores alert information.
(3) Apache serves as the web analysis console server.
(4) PHP facilitates communication between MySQL and the web analysis console.
(5) BASE serves as the front-end display.
(6) ADODB standardizes the database storage method.
(7) Barnyard links BASE to the MySQL database.In simple terms, the first step involves Lipacp capturing network packets and storing them in the MySQL database. Next, the Apache server acts as an interface to transmit data. The intrusion detection analysis console BASE can access the MySQL database through Apache. Finally, administrators can view and manipulate detailed data on the BASE analysis console.
图 3.2 系统工作流程
3.2 准备工作
本课题是要设计一个全面的 Snort 入侵检测系统。第一步要认清目标对象。第二步根据目标对象,来选择所需要的需求功能,最后就是根据需求来选择对应的插件。
3.2.1 环境的准备
Snort 可以在不同的系统中进行二次开发的入侵检测系统,比如像 Linux、Windows 等系统。本课题选择的是在 Linux 系统下,这样可以很好为系统添加必要的插件。
如图3.1,在系统拓扑图中,部署一个 Snort 系统需要必备的软件和硬件的条件。选择主机 D 作为 SIDS 的计算机。主机 D 的系统是 Linux 下的 CentOS 7 的计算机。同时硬件是一个网卡来连接到内网中。需要安装的软件有 MySQL 数据库、Apache 服务器、Barnyard 工具、BASE 框架和其他所需要的插件。被检测的数据可以被管理员用计算机 E 分析。需要两台计算机作为测试机在内网中,选择 B 和 C 主机。计算机 F 是所在内网外的主机,用计算机 F 去入侵内网中的主机,主要是测试 Snort 系统是否可以检测到外网主机对内网的主机的入侵。结果验证 Snort 可以检测到内网的入侵,从而证明系统可行性。
2.3.2 各软件的准备
为了减少系统成本,选择开源和免费的第三方插件。如图表3.3中在官方网站中可以进行下载,下载得到的源码都是开源,根据用户的需求,在此基础上进行二次的开发。因为系统的原因,要选择相对的版本,才能更好的去配置,不同的版本会导致和系统的不兼容行,容易导致适配出错。
表 3.3 各辅助软件的信息
软件名称 | 官方网站 | 作用
— | — | —
Apache | http://httpd.apache.org/ | WEB服务器
PHP | http://www.php.net/ | PHP脚本支持
MySQL | http://www.mysql.com/ | 数据库支持
Libpcap | https://www.tcpdump.org/ | 网络抓包工具
Snort2.9 | http://www.snort.org | Linux 下的 Snort 安装包
BASE | http://www.cert.org/kb/acid | 基于 PHP 的数据分析控制台
ADODB | http://adodb.sourceforge.net | 为 PHP 提供数据库连接函数
Barnyard | http://www.securixlive.com/barnyard2/download.php | Snort 连接 MySQL 服务这些软件都是更新过的,本课题选择了比较稳定的版本去配置。有的版本跨度很大,所以差别也就越大,选择与 Snort 版本相贴近的插件更容易实现。为了系统能够稳定的运行选择表 3.4 软件的版本进行 SIDS 的实现【12】。
表 3.4 选定的软件
软件名称 | 压缩包
— | —
MySQL | mysql-5.7.29-linux-glibc2.12-x86_64.tar
Libpcap | libpcap-1.0.0.tar.gz
Snort | snort-2.9.7.0.tar.gz
PHP | php-7.2.2.tar.gz
Apache | httpd-2.4.32.tar.gz
BASE | base-1.4.5.tar.gz
ADODB | adodb519.tar.gz
Barnyard | barnyard2-1.9.tar.gz
Daq | daq-2.0.4.tar.gz3.3 SIDS 的实现
在这个章节中,将具体的介绍 Snort IDS 构建的全过程,为了保证每一步的安装都是成功的,在每安装一步的基础上,对其进行功能的检测,如果成功,则继续安装,否则重新安装本次过程。这样保证了系统的可行性和健壮性。第一步是建立一个 Snort 的嗅探器,这个嗅探器已经具备了入侵检测最基本的功能,在后面的章节中将通过构建需要的第三方插件来进一步的完善整个系统。
3.3.1 数据捕获功能实现
本节,将建立一个具有嗅探功能的基本的 Snort 入侵检测系统,一开始先部署 Snort、Libpcap 抓包器和 daq,两个安装包不像在 Windows 系统直接的安装,需要用命令行 tar -zxvf 将其解压到 /usr/local/src 目录中,然后在此目录下输入命令行 ./configure 和 make && make install。其中 ./configure 是来检测是否有 gcc,make 是来对其进行编译,make install 是 Makefile 中读取命令来安装的。
当上述的操作完成后,一个简单的网络入侵检测系统就可以启动了,它具备了获取数据包和记录数据包的两个最基本的功能。但是这样并不能完全显示告警信息。需要安装规则库,先解压 snortrules-snapshot-2970.tar.gz 到 /usr/local/src/ 下,之后将解压好的 Snort 文件夹移动到 /etc/snort/ 目录下。
命令示例:
# cd /etc/snort/
# cp /usr/local/src/snort-2.9.7.0/etc/* .
# cd /etc/snort
# chown -R snort:snort *
# touch /etc/snort/rules/white_list.rules /etc/snort/rules/black_list.rules这样规则库就部署成功了。在命令行输入“snort -T -i eth0 -u snort -g snort -c /etc/snort/snort.conf”,这时入侵检测系统就启动了,任何网络的入侵都将会被记录在如图 3.5,在图 3.5 中 Snort 将数据包的信息都显示出来了。
现在这个嗅探器,已经能够实现一个简单 IDS 的功能,如果要实现 SIDS 的功能,还需要添加其他的辅助软件和部件【13】。
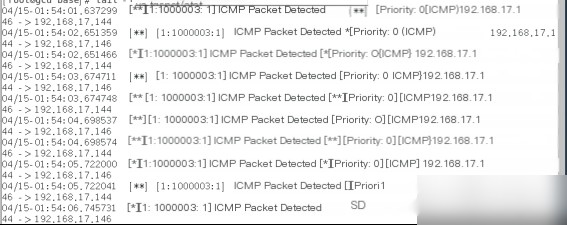
图 3.5 用嗅探器模式进行测试的数据包头信息
3.3.2 数据存储功能实现
MySQL 是一种关系型数据库管理系统,在 Web 应用方面是最好和为 Snort 网络入侵检测系统提供了数据库的支持。在启动数据库后,需要让 Snort 系统连接到数据中。在 Linux 中系统中,直接在命令行输入:
# yum install -y mysql-server mysql-devel
可以直接安装 MySQL,大大减少了在其他系统的配置过程。安装完后为数据库 root 用户设置密码,进入 MySQL 命令中。因为要将入侵的日志存入到数据库中,所以为 Snort 建议一个 snort 数据库,同时新设置一个用户名 snort 为 Snort 访问。设置与 root 相同的密码,便于用户去记忆。Snort 可以通过数据库插件将预处理器的日志输出写入数据库,但是以下配置将警报写入警报文件,而预处理器的日志输出以 Unified2 格式写入二进制文件。以供 Barnyard2 读取使用。
将第 521 行修改成如下内容:
output unified2:filename snort.log,limit 128
在 /usr/sbin/ 目录下新建名为 Snort 的软链接文件:
# ln -s /usr/local/bin/snort snort
上述准备做完之后,就是为 snort 这个数据库建立表。查看了 Snort 的源码,了解了 Snort 需要几个表,需要哪些字段,编写了 Snort 的系统的 SQL 脚本文件。用 SQL 语句 “source + 文件位置”,导入到 snort 用户中的 snort 数据库视图里。通过 phpMyAdmin 管理工具可以查看到数据库可视化的界面。可以清晰的看到创建的所有表,如图 3.6 中这些表分别存储了 Snort 检测到入侵的 TCP、UDP、ICMP 等数据信息【14】。

图 3.6 snort 中的视图表
3.3.3 编写规则功能实现
为 Snort 配置完数据库后,需要将 Snort 系统连接的 snort 用户的 snort 数据中,这里需要 Barnyard2 作为 Snort 连接数据库的接口,修改配置文件 barnyard2.conf,文件中定义了 6 种连接数据库的方式,本文中用到是 MySQL 数据库,所以在 barnyard2.conf 文件中修改为如下所示:
output database: log,mysql,user=snort password=123456 dbname=snort host=localhost
其中 `output` 表示是输出的意思,`database` 表示的是选择的数据包的类型,`user` 表示的是数据包的用户,`password` 表示的是数据库的密码,`dbname` 表示的是 user 用户数据库的名称,`host` 表示的是域名。
这样配置完之后,Snort 系统可以把检测到的数据存入到 MySQL 数据库中。到这个步骤之后,可以直接存储在数据库中,但是用户并不能直观的在界面显示,这里编辑一个 Snort 规则,用于测试 Snort 系统是否可以检测到入侵的信息。
添加测试规则:
# vi /etc/snort/rules/local.rules
规则如下:
alert icmp any any -> $HOME_NET any (msg:”ICMP Packet Detected”;sid:1000003;rev:1;)
规则头的规则工作包括:
1. Alert – 使用选择的警告方法创建警告并写入此包。
2. 记录此包。
3. Pass – 请将此包丢弃。
4. Activate – 告警并激活其他动态规则。
5. Dynamic – 根据激活规则,这个系统会一直保持闲置状态直到被激活,然后按日志规则运行。tcp、udp、icmp 和 ip 有四种类型。规则头的下列部分处理给定规则的 IP 地址和端口信息。关键词“any”可以用来定义所有的地址。方向运算符 “->” 表示遵循规则的流动方向。方向运算符左侧的 IP 地址和端口被认为是发生流速的源主机,而方向运算符右侧的 IP 地址和端口信息则是目标主机。然后规则选项是入侵检测引擎的核心,选项是半邀请的数字。规则选项关键字以及相关参数可分为:冒号。snort 有 42 个规则选项关键字。主要内容有:将信息打印到 msg – 告警和分组日志中。sid-snort 规则 ID。这些关键词用于识别唯一规则、rev – 规则版本的固有版本。该规则的意思是检测内网中的 ICMP 包,可以通过 ping 命令产生的数据包,最后将结果存入到 MySQL 数据库中。输入如下的命令:
snort -i eth0 -c /etc/snort/snort.conf -A fast
启动 Snort 入侵检测系统。
当出现如图 3.7 所示画面时,最后一行出现 “successful validated the configuration” 这就表明了 Snort 系统已经启动成功,正在运行当中,下面就可以对系统进行简单测试。
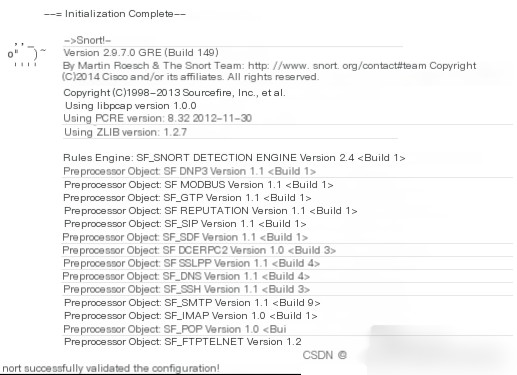
图 3.7 Snort 运行网络入侵检测模式
在 Snort 系统正常工作时,在主机 A 的命令图3.8 数据表:icmphdr
3.3.4 实现告警显示功能
在添加数据库功能后,Snort系统只能将数据存入数据库,并不能直观地显示入侵检测的效果。因此,为Snort系统提供了一个Web交互界面,用户可以在网页上查看入侵检测的效果图。使用Apache作为网页服务器,用PHP作为引擎读取MySQL数据库。1. 构建Web服务器
在Linux中,用命令行输入:yum install –y httpd
直接安装Apache服务器,减少了在其他系统上需要配置的程序,提供了快捷、方便的安装方式。使用命令行:
chkconfig –add httpd
配置Apache服务为自动启动,简化了繁琐的操作。这样,管理员可以在浏览器中输入以下网址:
http://localhost
其中localhost为主机D的网络地址,如图3.9所示,是管理员主机E的网址,显示Apache安装成功。
图3.9 成功安装Apache界面
2. 配置服务器文件
由于BASE是用PHP编写的程序,所以需要配置Apache支持PHP。用命令行输入:yum install –y mysql-server php php-mysql php-mbstring php-mcrypt mysql-devel php-gd
安装php所需的插件。安装配置后,PHP支持Apache服务。用以下方式测试:
在/var/www/html目录下新建test.php,文件内容为:php
在PHP中使用该代码行,来输出PHP安装信息。在管理员主机E上使用:
http://localhost/test.php
测试Apache对PHP的支持,如图3.10所示,标明Apache已经可以运行PHP。
图3.10 配置Apache支持PHP成功提示界面
3. 配置服务器对MySQL和图形界面的支持
在Linux命令行下输入:pear channel-update pear.php.net
pear install Image_Graph-alpha Image_Canvas-alpha Image_ColorImage_graph的前身是GraPHPit,它是用于图表操作的包,也是一个开源项目。为了安装方便,它被整合到Pear中,命名为Image_Graph(-alpha为其版本号),通过pear命令进行安装,简化了安装过程。
3.3.5 实现控制台功能
BASE是用PHP编写的工具,用于查看Snort输出到数据库中的数据,并提供图形分析工具,使管理员能够清晰分析入侵检测数据,提高了数据分析的功能,减少了数据冗余。解压缩base-1.4.5.tar.gz至/var/www/html目录下。BASE需要访问数据库的用户,前面章节中已经为此创建了用户snort。打开BASE的配置文件php.ini,修改如下配置:
error_reporting = E_ALL & ~E_NOTICE
测试BASE,在计算机E的网页浏览器中输入:
http://localhost/base/setup/index.php
如图3-11所示,是BASE配置成功的界面。从界面可以看到“Config Writeable”显示为“Yes”,这表示配置成功。“PHP Version”表示当前的版本号。
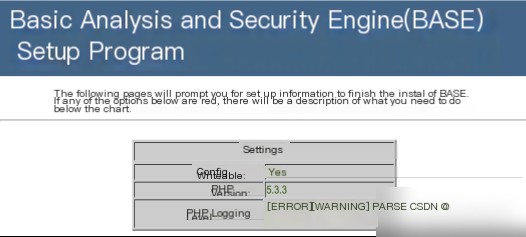
图3.11 BASE连接数据库成功
然后进入BASE的主页面,如图3.12所示,ICMP中显示100%,表示每一个数据包都被检测到。共检测了8269条入侵信息,表示BASE连接数据库已成功。这样,一个完整的SIDS已经搭建完成。
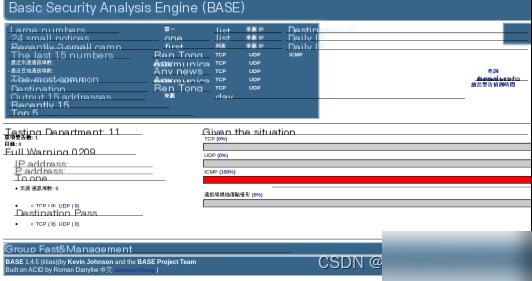
图3.12 Snort捕获的数据在BASE中的显示
3.4 本章小结
本章主要讲述了Snort入侵检测程序设计的各个模块实现。从数据存储模块、规则编写模块、告警显示功能和控制台模块。此外,讲述了系统需要的开发平台和使用的第三方插件。4. 系统测试与检测结果分析
完成上述所有功能的配置后,需要对SnortIDS进行最后的检测测试。首先,需要自己编写一个规则,然后通过编写的规则与规则库中的规则匹配,生成告警信息并将其存入数据库。规则如下:alert icmp any any -> any any (msg:”ICMP Packet Detected”; sid:1000003; rev:1;)
通过该规则,可以检测到ICMP包,并提示信息“ICMP Packet Detected”。
4.1 收集入侵数据
设置好规则后,使用内网的三台主机,分别为主机A、B和C,作为测试的入侵源地址。在计算机D上,输入以下命令:snort -i eth0 -c /etc/snort/snort.conf -A fast
这将启动Snort入侵检测模式。在计算机C的命令行中输入以下命令:
ping 192.168.17.148
这个命令会使主机C不断发送TTL的ICMP数据包给主机D,这些ICMP数据包被视为入侵信息,并将告警信息存入数据库中。
4.2 检测与解析
BASE提供多种查看入侵信息的方式,如时间、源IP、数据包内容等。通过对数据的查看,管理员可以获得所有有关攻击的信息。以下列出几种查看方式进行数据分析,并作为测试的方法。1. 总计信息展示
进入BASE首页,如图4.1右侧所示,显示了三种协议数据的比例。页面包括侦测器总数、单向警告数、全部警告数、源IP地址、目的IP地址等信息处理内容。如图4.1右侧显示的同一攻击有18次连接,总共检测到8269次入侵,都是由ICMP包产生的。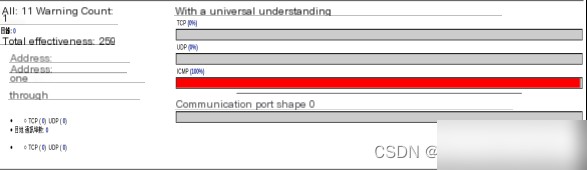
图4.1 统计信息查询
2. 详细数据信息查询
点击任意一条入侵信息查看,如图4.2所示,有ID、时间标记、来源地址、目的地址和通信级别等信息。管理员可以通过“通信级别”找到入侵来源。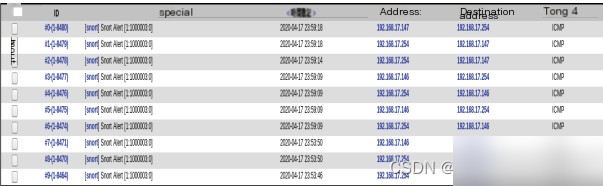
图4.2 详细查看入侵数据信息
3. 数据包内容显示
每一个被检测的数据包,包含详细信息,如图4.3。其中Meta部分包括数据包的硬件信息、编号、捕获时间、警告群组、探测器接口等;IP部分是数据包地址信息。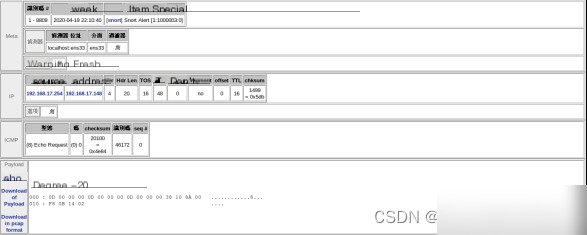
图4.3 查看单个数据包的内容
4. 图表分析方式
大量数据显示并不能直观地反应出入侵信息。这里提供图表显示的方法,功能十分强大。如图4.4和4.5。可以选择图表的方式、形状、X和Y轴参数和名称。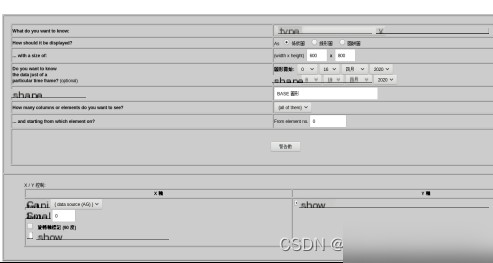
图4.4 图表查看方式选项
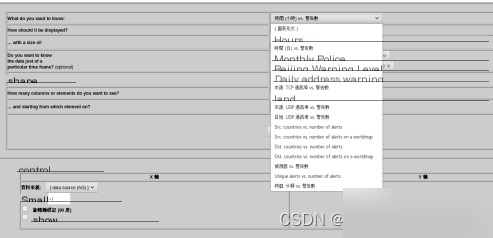
图4.5 图表查看方式种类选择
图表的形状有多种,比如圆形、线形、饼状形等。图表的方式也有很多,比如时间与警告数、来源IP与警告数、目的IP与警告数等。如图4.4和4.5显示。用户可以根据具体需求选择图表。
从以上入侵数据的查看和分析中,可以看出,通过规则捕获的数据是准确的,对入侵数据的内容分析也很全面。
4.3 本章小结
本章主要讨论了对Snort入侵检测系统整体功能的测试。上一章是对各模块分别测试,而这一章是对整个系统进行测试。结论
IDS可以在多个平台设计和部署。由于互联网的快速普及,网络入侵对用户的威胁越来越大。人们对Windows下的入侵检测进行了深入研究,但在其他平台上研究并不充分。本文选择在Linux系统下设计并实现IDS入侵检测系统,研究内容如下:(1)本文首先介绍了互联网信息安全的状态,和用户面临网络入侵的威胁。然后介绍了Snort技术,同时提出Snort系统的一些问题和不足。
(2)根据SIDS系统设计了整体结构,并编写了用于入侵检测的规则,为详细设计Snort系统做好准备。
(3)介绍了SIDS系统的完善设计和实现。同时扩展了单个系统的功能,提高了入侵检测效率和用户使用的便捷性。每个步骤的完成都进行了测试,确保系统正常运行。虽然SIDS已有诸多优点,但随着技术的发展和功能增强,还有许多需要改进的地方:
(1)由于互联网的数据量和维度大,增加了入侵检测负担,使得效率低下。可将机器学习和深度学习应用于入侵检测,获得相应模型,提高检测效率。
(2)Snort系统的BM算法有不足之处,匹配算法的不足也会降低检测效率。因此,需要优化BM算法。致谢
经过一个学期的努力,最终顺利完成了毕业设计。在此,我要感谢我的指导老师王飞老师和陈佳美老师自始至终对我的指导。无论是论文选题、开题、写作阶段,还是项目完成过程,老师们都悉心指导。老师们渊博的学识、严谨的治学作风和求实的工作态度深深影响了我,使我终生难忘。另外,还要感谢我的同学们,项目和论文写作过程中为我提供了许多帮助。我们并肩作战,这段经历见证了我们的同舟共济与共同奋斗。本文完成借助了很多书籍、期刊和论文文献,感谢这些作者们。
大学四年即将结束,回顾前几年的求学生涯,还要感谢母校,为我们提供了象牙塔,让我们享受学习的快乐、运动的畅快、同学的关怀、References
[1] Han Donghai, Analysis of Intrusion Detection System Examples [M]. Beijing: Tsinghua University Press, 2002:63-82 [2] Tang Zhengjun. Design and Implementation of Network Intrusion Detection Systems [M]. Beijing: Electronic Industry Press, 2002:112-136 [3] Tang Zhengjun. Source Code Analysis of Hacker Intrusion Prevention Systems [M]. Beijing: Machinery Industry Press, 2002:73-97 [4] Dong Yuge, Jin Hai, Zhao Zhen, Attacks and Protection – Network Security and Practical Protection Techniques [M]. Beijing: People’s Posts and Telecommunications Press, 2000:9-81 [5] Nie Yuanming, Qiu Ping. Network Information Security Technology [M]. Beijing: Science Press, 2001:154-162 [6] Wang Deshan, Wang Kechao. A Study on Firewall Technology in Computer Network Security [J]. Network Security Technology and Application, 2013.07:61-62 [7] Wu Guo, Chen Lei, Si Zhigang et al. Optimization Model for Network Security Situational Assessment Indicator System [J]. Computer Engineering and Science, 2017.05:861-869 [8] Ye Zhenxin. Study on the Interaction Model of Firewalls and Intrusion Detection Systems [D]. Shanghai Jiao Tong University, 2008 [9] Yin Xijie, Xu Jianguo. Research and Application of Multi-Firewall Technology in Enterprise Network Security [J]. Computer Applications and Software, 2015.08:292-295 [10] Li Shanping, Liu Wenfeng, Wang Huanlong et al. Linux and Embedded Systems [M]. Beijing: Tsinghua University Press, 2002:121-143 [11] Chen Xiaohua, Luo Daisheng, He Xiaohai. Application of Data Mining Technology in Network Intrusion Detection [J]. Journal of Southwest University for Nationalities (Natural Science Edition), 2003.06:762-765 [12] Ren Zheng, Chen Zhigang. Intelligent Network Intrusion Detection System Based on Data Mining and Planning [J]. Computer Engineering and Science, 2006.03:5-7+16 [13] Qin Yingqiong. Brief Analysis of the Application of Firewall Technology in Computer Network Security [J]. Network Security Technology and Application, 2013.11:77-81 [14] Pandeeswari N, Kumar G. Anomaly Detection System in Cloud Environment Using Fuzzy Clustering Based ANN [J]. Mobile Networks and Applications, 2015:1-12 [15] Ponsam J G, Srinivasan R. Multilayer Intrusion Detection in MANET [J]. International Journal of Computer Application, 2014.98(20):s [16] Zhang Xiang, Zhang Jicai, Wang Tao et al. Research on Open Source Intrusion Detection System—Snort [J]. Computer Applications, 2002, 22(11):96-97. [17] Peng Zhao. Research and Implementation of Network Intrusion Prevention System Based on Interaction [D]. Beijing University of Posts and Telecommunications, 2010. [18] Shi Guozhen, Zhang Meng, Fu Peng et al. Design and Implementation of Tools for IDS Device Detection [J]. Information Network Security, 2016, 5:23-29. [19] Li Wei, Yang Zhongming. A Review of Intrusion Detection System Research [J]. Journal of Jilin University (Information Science Edition), 2016,34(5):657-662.
- 3.2 Operating Modes Snort can be run in three modes: sniffing mode, packet logging mode, and network intrusion detection mode. The most fundamental and primary mode is sniffing mode. It is closely related to packet logging mode; however, their output formats differ. Network intrusion detection mode is the most standard and requires certain plugin functionalities based on the specific needs.


