Relevant Principles (TCP Basics)
Three-Way Handshake: TCP is a transport layer protocol built on the IP network layer, used for reliable end-to-end byte stream transmission. Process: 1. C sends a connection request to S, with the SYN flag set to 1, and a randomly set sequence number seq. 2. S returns an acknowledgment, ACK set to seq+1, SYN flag set to 1, random sequence number seq. 3. C returns an acknowledgment, ACK set to seq+1
Four-Way Handshake: The four-way handshake refers to the normal termination of a connection. Process: 1. C sends a FIN with seq set to the last sent seq+1 to S. 2. S replies to C with ACK=seq+1. At this time, C stops sending information to S but can still receive messages from S, which is half-duplex (i.e., unidirectional interruption). 3. After S has sent the remaining packets, it sends a FIN packet to C. 4. C responds with an ACK acknowledgment after receiving the message, and S stops sending messages to C, fully terminating the connection.
Sliding Window: The sliding window was mainly devised for enhancing transmission efficiency while ensuring “reliability.” If each packet waits for an ACK, the efficiency is too low. Therefore, after sending data, we may continue sending other packets within the sliding window size without waiting for an ACK. The WIN shown above indicates the sliding window size.
Rst Reset: RST stands for reset and is used to close connections abnormally. When a connection is closed by sending an RST packet, it does not wait for all buffered packets to be sent (like a FIN packet) and discards the buffered packets to send an RST packet directly. Upon receipt of an RST packet, the receiver does not need to send an ACK for confirmation. The TCP handler will send an RST packet when it perceives an abnormal moment.
Attack Examples
Connecting to the server
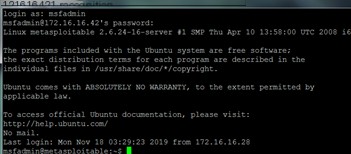
The attacker opens Wireshark for sniffing and sees the three-way handshake process.
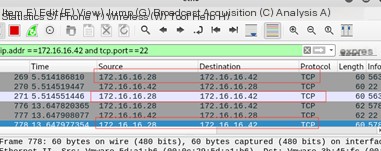
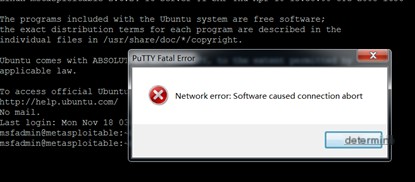
Using netwox 78 -i “172.16.16.42” to send an RST attack, it is found that the connection is successfully broken.

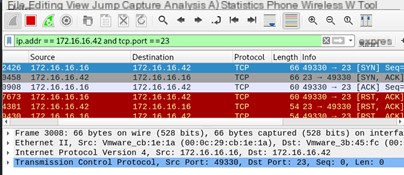
Wireshark packet capture shows that it has been reset.
Defense Measures
Deploy a switched network to replace hubs with switches. Disable source routing on hosts. Use a static binding IP-MAC mapping table to prevent ARP spoofing. Filter ICMP redirect messages. It is recommended to use a firewall to discard incoming packets with the RST flag set.


