Chapter 5: Tactics, Techniques, and Procedures of Ransomware as a Service Groups
You have already learned a lot about human-operated ransomware, gained a good understanding of their attack processes and countermeasures, and understood why it is so important to respond to incidents appropriately.
However, to effectively respond to incidents, it is not enough to just understand the attack lifecycle, as attackers often use various tactics, techniques, and procedures (TTPs) to achieve their goals.
The existence of Ransomware as a Service (RaaS) complicates the situation further because attacks using these programs may involve many affiliates, and even for the same ransomware variant, the TTPs of different participants can vary significantly.
This chapter will help you understand in detail the behaviors of attackers at various stages of the attack lifecycle (based on MITRE ATT&CK). Specifically, we will discuss the following topics:
- Gaining Initial Access
- Executing Malicious Code
- Maintaining Persistent Access
- Privilege Escalation
- Defense Evasion
- Credential Access
- Lateral Movement
- Data Collection and Exfiltration
- Deploying Ransomware
Gaining Initial Access with Ransomware as a Service
Gaining initial access to the target network is a necessary part of any intrusion, and ransomware attacks are no exception.
Due to the diverse range of attackers involved in ransomware attacks, incident response experts may encounter almost any technique in their work.
Nevertheless, one of the most commonly used techniques by ransomware operators is compromising external remote access services, such as Remote Desktop Protocol (RDP), so we will start here.
External Remote Access Services (T1133)
Attacks using external remote access services are very common. For example, according to Group-IB’s “Ransomware 2020/2021” report, over 50% of ransomware attacks start with the compromise of exposed RDP servers. The COVID-19 pandemic exacerbated this issue, as many companies had to create workstations for remote employees, further weakening the protection of global servers.
The default port for Remote Desktop Services is 3389. If we use search engines like Shodan to search for devices connected to the internet, we can see thousands of such servers, which is why attacking these servers has become one of the most common techniques (see Figure 5.2).

Figure As shown in the image, gaining initial access through external remote services is quite simple, especially during the COVID-19 pandemic. But this is not the only method. Let’s discuss another common technique—exploiting public-facing applications.
Exploiting Public-Facing Applications (T1190)
In ransomware attacks, exploiting public-facing applications is another common technique.
You already know that ransomware operators often target RDP servers: they can perform brute force attacks or simply buy access on the black market or from initial access brokers.
But they can also exploit vulnerabilities in RDP implementations to execute code remotely, such as BlueKeep (CVE-2019-0708). This vulnerability is known to be actively exploited to this day, especially by those associated with the LockBit ransomware.
Similarly, attackers exploit various vulnerabilities to gain VPN access. Let’s look at some of the most common vulnerabilities.
Vulnerabilities in Fortinet, FortiOS, and FortiProxy (CVE-2018-13379) allow various ransomware operators to access system files, including files containing credentials, which can then be used to gain VPN access.
Another vulnerability in Pulse Secure Pulse Connect Secure (CVE-2019-11510) is also a file read vulnerability that allows attackers to obtain private keys and user passwords. This vulnerability has been actively exploited by those associated with the REvil ransomware.
Finally, a vulnerability in SonicWall SMA100 (CVE-2019-7481) has also been actively exploited by the HelloKitty ransomware operators.
Of course, the initial access vulnerabilities exploited by attackers are not limited to RDP and VPN. For example, Clop ransomware operators exploited vulnerabilities in Accellion FTA:
- CVE-2021-27101: SQL Injection vulnerability
- CVE-2021-27102: Operating System Command Injection vulnerability
- CVE-2021-27103: Server-Side Request Forgery (SSRF) vulnerability
- CVE-2021-27104: Another Operating System Command Injection vulnerability
These vulnerabilities allowed attackers to upload web shells to vulnerable servers and use them for data theft, as companies use Accellion FTA to securely transfer large files.
Another vulnerability exploited by ransomware operators is in Citrix Application Delivery Controller (ADC) and Gateway (CVE-2019-19781). This vulnerability allows attackers to execute commands on the target server.
Finally, in 2022, attackers exploited vulnerabilities in Microsoft Exchange servers, including ProxyLogon (CVE-2021-26855) and ProxyShell (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207).
Ransomware attackers add these vulnerabilities to their toolkit. For example, those associated with Conti exploited the ProxyShell vulnerability to load web shells on target servers for further actions in the post-exploitation phase.
Public-facing servers and applications are hot targets for ransomware operators, but their numbers are usually limited. Additionally, they may have the latest security updates installed and/or use strong passwords. Therefore, attackers have to look for other weak points, such as ordinary users within the corporate network. In this case, phishing is a suitable choice.
Phishing (T1566)
Historically, phishing has been one of the favorite methods for attackers to gain initial access to target networks.
Currently, cybercriminals often use trojans (or bots) sent via spam to achieve this goal. These malicious programs include Bazar, Qakbot, Trickbot, Zloader, Hancitor, and IcedID.
Attackers typically send these malicious programs via email attachments (such as Microsoft Office files, scripts in compressed files) or emails containing malicious links.
Attackers show remarkable creativity when crafting phishing emails. Sometimes these emails look very convincing, even security experts might mistake them for legitimate emails. Figure 5.5 shows an example of a phishing email sent by Hancitor operators.
Figure 5.5. Example of a phishing email sent by Hancitor operators
Clicking the phishing link directs the user to a page that downloads a malicious Microsoft Office document. Attackers do not always send emails with links; sometimes they attach the infected files directly in the email.

Figure 5.6. Example of a phishing email sent by Qakbot operators
After downloading the file, the victim needs to open it and, in most cases, enable macros for the malicious content to be written to disk or downloaded from a server controlled by the attackers. These malicious documents often prompt users to enable macros.
Figure 5.7. Example of malicious document content
Once the victim enables macros, the malicious content is activated. However, if the victim’s spam protection is robust, it is not easy for attackers to send infection links or attachments. They need to act more creatively—and they do!
The cybercrime group Wizard Spider—operators of Bazar, Trickbot, Ryuk, Conti, and Diavol—uses phishing emails containing paid subscription information and provides a phone number in the email for the victim to call to cancel the subscription. There is no actual subscription—this is voice phishing (vishing). The phone operator directs the victim to visit a fake website to download a form needed to cancel the subscription. Figure 5.8 shows an example of a fake website.
Figure 5.8. Example of a fake website
The sole purpose of these fake websites is to deliver malicious documents. Identifying whether a user is encountering a vishing attempt is relatively simple. Sometimes, just asking a few clarifying questions and delving into the topic can expose the scammer.
Another example is malicious advertising. For instance, Zloader operators create malicious ads, and if a victim searches for certain keywords on Google, she will be redirected to a website controlled by the attackers, which hosts malicious files.
Figure 5.9. Example of a fake website spreading Zloader
Sometimes, attackers use more sophisticated initial access techniques, such as supply chain attacks.
Supply Chain Compromise (T1195)
Supply chain attacks usually require more effort. While these attacks are very profitable, they are not common and are rarely heard of or discussed. However, some known attack instances have led to the deployment of ransomware.
The first such operation was carried out by REvil ransomware operators, who compromised the Italian version of the WinRar website to spread copies of REvil.
Another more interesting case is where individuals associated with the Darkside ransomware compromised the SmartPSS software website and began delivering the SMOKEDHAM backdoor. More details about this attack can be found on the FireEye blog: https://www.fireeye.com/blog/threat-research/2021/06/darkside-affiliate-supply-chain-software-compromise.html.
So, we discussed the most common initial access tactics. Next, we will look at how attackers launch malicious code on the target system.
Launching Malicious Code through Ransomware as a Service
There are various methods for this. Let’s look at the most common methods in ransomware attacks.
Once attackers gain access to the target system, they need to launch malicious code or dual-use tools to perform post-exploitation tasks.
User Execution (T1204)
As you know, many attackers gain initial access through phishing, and in most cases, the victim needs to open an attachment or link to launch the malicious code. Only then can the attackers gain initial access.
We can look at this method from another angle. For example, if ransomware operators enter the network through a public RDP server, they usually gain access to high-privilege accounts, such as administrator accounts. Therefore, in this case, they can act as malicious users themselves, executing various commands and tools.
Command and Scripting Interpreter (T1059)
At certain stages of the attack lifecycle, ransomware operators may use various command and scripting interpreters.
In the case of phishing, Windows Command Shell, PowerShell, Visual Basic, and even JavaScript are very common. Let’s look at some examples.
Attackers use infected Microsoft Word documents to spread Trickbot and execute malicious VBScript scripts.
This script may look complex, but it is not. It simply downloads Trickbot (inlinelots.png) from 172.83.155[.]147, saves it to C:\Users%user%\AppData\Local, and launches it via rundll32.exe—that’s it!
Another example is IcedID. Attackers spread this trojan via compressed files containing malicious JavaScript files. The script launches cmd.exe, which in turn launches powershell.exe.
If we decode the base64, we see that it downloads the next stage of the attack code from a server controlled by the attackers.
As you can see, the use of command and scripting interpreters is very common, but in these cases, the victim usually needs to launch the script or enable macros. Of course, this is not the only option; sometimes attackers exploit software vulnerabilities to automatically launch malicious code. Nevertheless, using PowerShell for criminal activities might not go unnoticed, but in reality, PowerShell monitoring systems generate a lot of noise, sometimes making it easy to narrow down the search.
Exploitation for Code Execution (T1203)
We have already discussed how attackers exploit vulnerabilities in public-facing applications to gain initial access, but in some cases, they may also exploit vulnerabilities in office software, such as Microsoft Office. Nevertheless, it is strongly recommended to patch vulnerabilities in public-facing applications before focusing on internal vulnerabilities.
A good example is the recent MSHTML vulnerability (CVE-2021-40444), which the Wizard Spider group actively exploited to spread Bazar and Cobalt Strike.
Attackers often abuse built-in tools. Besides command and scripting interpreters, another example is Windows Management Instrumentation (WMI).
Windows Management Instrumentation (T1047)
Windows Management Instrumentation (WMI) is a commonly used tool by various ransomware operators to launch code locally and remotely, for example, when moving laterally within a network. Cobalt Strike, a post-exploitation framework very popular among ransomware-related individuals, has built-in functionality to use WMI to launch code remotely.
As you know, human-operated ransomware attacks can last quite a long time, so attackers need to maintain persistent access to the compromised network even after a restart.
Persistence in Ransomware as a Service
In the post-exploitation phase, attackers usually need to maintain persistent access to the network, so during incident response, you may encounter various persistence methods. This step is almost as important as gaining access to the network itself. Using additional backdoors ensures that attackers can return at any time. Let’s look at some of the most common methods.
Valid Accounts (T1078)
Especially in the case of RDP or VPN attacks, attackers use valid accounts to access the corporate network. Since they may use multiple compromised accounts simultaneously, this method can be used to maintain persistence in the compromised network. More importantly, using legitimate credentials, ransomwareCreating scheduled tasks is one of the most common methods used by Trojans involved in ransomware attacks. Here is an example of a command line used by Qakbot for persistence.
The scheduled task will start Qakbot every six hours.
Server Software Component (T1505)
As you know, using publicly available applications is a common method for ransomware operators to gain initial access. To ensure persistent access, they often use web shells.
A web shell is a script deployed on a publicly accessible web server that allows attackers to execute various commands via a command-line interface.
We have discussed the most common methods ransomware operators use to maintain persistent access in compromised networks. Now let’s look at how they escalate privileges.
Privilege Escalation in Ransomware as a Service
In many cases, attackers do not have sufficient privileges after gaining initial access to the target system. To escalate privileges, they use various methods. We will discuss the most common ones.
Exploiting Privilege Escalation Vulnerabilities (T1068)
During different stages of a ransomware attack lifecycle, including the privilege escalation phase, attackers may exploit various vulnerabilities. For example, ProLock ransomware operators exploited a vulnerability in the CreateWindowEx function (CVE-2019-0859) to gain administrator-level privileges.
Another example is the REvil ransomware, which can exploit a vulnerability in the win32.sys driver (CVE-2018-8453) to escalate privileges.
Therefore, many common vulnerabilities can be used to gain higher-level privileges. If companies fail to patch and mitigate these vulnerabilities, they may face severe issues.
Creating or Modifying System Processes (T1543)
Windows services are commonly used by various attackers, including ransomware operators, to locally or remotely start malicious code. Windows services can also be used for privilege escalation as they can run with SYSTEM privileges. Anomalies related to Windows services should be monitored, and their malicious use should be regularly analyzed to improve monitoring.
Code Injection (T1055)
Another very common method is code injection. Attackers can execute arbitrary code within the address space of processes with high privileges. This method can also be used to bypass certain defenses. For example, Trickbot uses wermgr.exe (Windows Error Reporting) for injection, while Qakbot uses explorer.exe (Windows Explorer).
Abusing Access Control Mechanisms (T1548)
Windows has several access control mechanisms, and ransomware operators will find various ways to bypass these mechanisms. A good example is User Account Control (UAC). This mechanism allows programs to request user confirmation to elevate privileges. To bypass it, Trickbot exploits WSReset.exe, which is used to reset Windows Store settings.
Privilege escalation is not the only obstacle attackers face; various widely used defenses also pose challenges.
Defense Evasion in Ransomware as a Service
In most cases, ransomware operators need to use various evasion techniques at different stages of the attack lifecycle. They may disable or remove security software, obfuscate or encrypt data, or delete traces on compromised hosts.
Exploiting Defense Evasion Vulnerabilities (T1211)
Attackers may exploit various vulnerabilities to evade defenses. One instance is the Robinhood ransomware operators exploiting a vulnerability in the Gigabyte driver (CVE-2018-19320). This allows attackers to load another unsigned driver to terminate processes and services related to security products, ensuring the successful deployment of ransomware.
Deobfuscating/Decoding Files or Information (T1140)
Malware and ransomware often use various obfuscation techniques, such as encryption and encoding, to evade detection mechanisms. One common obfuscation technique is base64 encoding.
A typical example is using PowerShell to launch a Cobalt Strike SMB Beacon.
As mentioned earlier, Cobalt Strike is a widely used post-exploitation framework used by many ransomware-related attackers. Initially, the toolkit was developed to simulate attacks, but unfortunately, it has also become popular among actual attackers.
Modifying File and Directory Permissions (T1222)
Attackers often need access to protected files. These files may be encrypted.
Many ransomware strains use the built-in icacls tool, which allows users to view and modify the security descriptors of files and folders. Here is an example of Ryuk ransomware using this tool.
The command removes all access restrictions on files and folders.
Impairing Defenses (T1562)
Most environments have at least minimal defense mechanisms that attackers must bypass to achieve their goals. For example, they may need to disable antivirus software or clear Windows event logs.
In an attack on Kaseya (https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689), REvil operators used the following script.
As you can see, part of the script aims to disable various features of Windows Defender, the built-in antivirus software in Windows.
In most cases, attackers also need to deal with other defense mechanisms. Common methods include using tools like Process Hacker or GMER to terminate processes and services related to antivirus software.
Clearing Host-Based Artifacts (T1070)
Ransomware operators often need to remain active in the network for as long as possible, so they try to make it difficult for network defenders to track their activities by deleting logs and files.
In a recent incident response, we saw attackers use a very simple but effective command.
This simple command allows them to clear all event logs.
Executing Signed Binary Files (T1218)
The last defense evasion method we will discuss is executing code through signed binary files. Ransomware operators can use legitimate binary files as intermediaries to execute malicious code. The most common options are rundll32.exe and regsvr32.exe.
Here is an example of attackers using rundll32.exe to launch a Cobalt Strike Beacon.
Another example is IcedID. This time, attackers used regsvr32.exe.
Of course, attackers can use other signed binary files. For example, in a recent attack campaign, Zloader operators used msiexec.exe to try to bypass defenses.
Next, we will discuss common methods attackers use to obtain credentials.
Credential Access through Ransomware as a Service
Since ransomware operators often try to encrypt as many hosts as possible, they need to be able to move laterally or at least remotely start malicious code. To operate covertly and efficiently, they usually first obtain credentials with elevated privileges, but their main target is domain administrator accounts.
There are many methods attackers can use to obtain authentication data. We will discuss the most common ones.
Brute Force (T1110)
You already know that RDP, VPN, and other external remote access services are often used in ransomware attacks. These services are often inadequately protected, allowing initial access brokers or ransomware operators to successfully obtain legitimate accounts through brute force attacks.
Operating System Credential Dumping (T1003)
Another widely used method is credential dumping. Ransomware operators still frequently use Mimikatz, despite it being easily detectable. Some attackers even manually download it from the official GitHub repository to the compromised host.
This is not the only tool used for credential dumping. A tool we encounter more and more frequently is LaZagne, which can extract credentials not only from volatile memory but also from various password stores, such as web browsers.
Another example is using the ProcDump tool, which is typically used to create memory dumps of the Local Security Authority Subsystem Service (LSASS) process.
Attackers can download these dumps and use tools like Mimikatz to extract credentials from them.
Ransomware operators do not even need to download additional tools to dump credentials—they can use built-in Windows features. For example, members of the Conti gang use the MiniDump function of the COM+ services to create dumps of lsass.exe.
If attackers can access a domain controller, they can also create a dump of the entire Active Directory domain database, which is stored in the NTDS.dit file.
The Conti gang uses the built-in ntdsutil tool to create a copy of the NTDS.dit file.
This file can be used by ransomware operators not only to obtain credentials but also to gather information about the domain.
Kerberos Ticket Theft and Forgery (T1558)
Since it is not always possible to create snapshots or crack credentials, attackers continuously find new ways to obtain valid accounts. Recently, credential acquisition methods like Kerberoasting have become increasingly popular among ransomware operators.
Attackers exploit Kerberos Ticket Granting Tickets (TGT) or intercept network traffic to obtain tickets provided by the Ticket Granting Service (TGS). For example, Ryuk ransomware operators use Rubeus for Kerberoasting attacks.
Once the required level of credentials is obtained, ransomware operators are ready to move laterally within the network.
Lateral Movement in Ransomware as a Service
Before starting lateral movement, attackers need to gather information about the network they have infiltrated. These activities may include network scanning and Active Directory reconnaissance.
Two of the most common network scanning tools used by various ransomware operators are Advanced IP Scanner and SoftPerfect Network Scanner.
One of the most commonly used Active Directory reconnaissance tools is AdFind, a legitimate command-line query tool.
Here is an example of Netwalker ransomware operators using this tool.
AdFind allows attackers to gather information about users, computers, inter-domain trusts, subnets, and more. This information can help them find the most valuable hosts, such as those containing backups and confidential information.
Another popular Active Directory reconnaissance tool is ADRecon, widely used by REvil ransomware operators.
As in previous stages, attackers can use built-in Windows features for network reconnaissance. For example, members of the Conti ransomware gang use PowerShell cmdlets for network reconnaissance.
Exploiting Remote Services Vulnerabilities (T1210)
Lateral movement is another strategy where vulnerabilities are actively exploited. Many attackers prefer to use common vulnerabilities, a notable example being EternalBlue (CVE-2017-0144), a vulnerability in the Server Message Block (SMB) protocol, which was infamously exploited by the WannaCry ransomware in 2017.
This vulnerability still exists in many enterprise networks, making it a popular target for attackers, such as the LockBit gang.
Other common lateral movement vulnerabilities include SMBGhost (CVE-2020-0796) and Zerologon (CVE-2020-1472).
Using Remote Services (T1021)
Ransomware operators use various remote services, such as RDP, SMB, etc., to move laterally using valid accounts. If attackers gain initial access through RDP, they typically use the same protocol to connect to other hosts in the compromised network, where they deploy malware, remote access tools, and, of course, ransomware.
Attackers favor RDP, so their toolkit even includes pre-configured scripts to modify settings to establish RDP connections with target hosts.
Other sub-techniques include SMB and Windows Remote Management (WinRM).
Using Alternate Authentication Material (T1550)
Ransomware operators do not always obtain plaintext passwords, so in some cases, they must use password hashes or Kerberos tickets for lateral movement. Pass the Hash (PtH) and Pass the Ticket (PtT) attacks can be executed using Mimikatz or post-exploitation frameworks likeVarious web services, such as MEGA and DropMeFiles, are very popular among ransomware operators. They can use a web browser to upload collected data to storage or automate the process using tools like RClone.
Here is an example of data exfiltration using RClone.
Sometimes attackers even develop specialized tools for data collection and exfiltration.
Automated Exfiltration (T1020)
LockBit operators not only provide ransomware for deployment to their affiliates but also offer a data-stealing tool called StealBit.
This tool automatically extracts all available files from the compromised host, excluding system files, registry files, and some other file extensions. Once all the collected data is stolen, the final step can be taken—deploying the ransomware.
Ransomware Deployment
The ultimate goal of any ransomware attack is to deploy the ransomware directly. By this point, backups have been deleted (or will be encrypted first), security products have been disabled, and data has been stolen.
One of the most common deployment methods is to copy the ransomware via SMB and execute it using PsExec (a legitimate tool from the SysInternals toolkit). Attackers often use it for remote execution.
Here is an example of Netwalker ransomware operators using this tool for remote execution.
Another example is Egregor malware operators, who use Windows Management Instrumentation Command-line (WMIC) for deployment.
Let’s look at another example—Ryuk ransomware. This time the attackers used the Background Intelligent Transfer Service (BITS) for deployment.
The ransomware itself usually implements multiple techniques. Let’s take a look at them.
Disabling System Recovery Capabilities (T1490)
Almost every ransomware has built-in functionality to delete or disable system recovery capabilities. A very common example is the ability to delete shadow copies. The final step is to encrypt the data.
Data Encryption (T1486)
The main goal of any ransomware attack is to encrypt files on the compromised host. Developers use various encryption algorithms, including AES, RSA, Salsa20, ChaCha, and custom algorithms. Without the key provided by the attackers, it is unfortunately impossible to decrypt the files. Victims pay the ransom, which incentivizes the creators of ransomware to carry out more attacks.
We have examined the entire lifecycle of an attack, focusing on the most common methods used by ransomware operators. It is important to note that the TTPs of criminals change periodically, so it is crucial to stay informed about the latest cyber threat information.
Conclusion
Modern human-operated ransomware attacks are not just about encrypting data. To deploy ransomware across an enterprise, attackers must prepare extensively from initial access to data exfiltration, providing many detection opportunities for cybersecurity teams. However, as incident response experts, we must have a thorough understanding of the current TTPs used by ransomware operators to respond quickly and effectively to attacks.
Since TTPs can change over time, incident response experts and other security personnel must be able to collect, process, and disseminate actionable information about ransomware-related cyber threats.
In the next chapter, we will explore various open sources for collecting cyber threat intelligence.
Chapter 6: Collecting Cyber Threat Intelligence Related to Ransomware
As you know, ransomware operators may use a wide range of tactics, techniques, and procedures (TTPs), so understanding what they specifically used in the attack you are dealing with is very useful. Some of these tactics and methods are short-term, while others are long-term, depending on the attackers’ ultimate goals.
Typically, the first thing you learn when starting an incident response (IR) is the type of ransomware used by the attackers. Many types of ransomware are spread in a “Ransomware as a Service” (RaaS) model, and different affiliates may have different approaches to the attack lifecycle, so their TTPs may vary.
With this in mind, having reliable Cyber Threat Intelligence (CTI) is very helpful in responding to attacks. Commercial CTI platforms are certainly useful, but even these sources may not have all the information you need, so learning to gather detailed information for current or future response activities is very important.
In this chapter, we will discuss some sources of cyber threat intelligence, specifically including:
- Threat Research Reports
- Community
- Attackers
Threat Research Reports
Most cybersecurity companies publish various reports on threats, including those related to ransomware attacks, making these sources convenient tools for collecting cyber threat intelligence. Threat research reports are an important part of assessing the threat landscape. These reports help both technical personnel and non-specialists assess the current situation of the company and compare it with the overall threat landscape.
Of course, no single report is comprehensive, so it is best to study a threat based on research from different cybersecurity solution providers. Some reports contain Indicators of Compromise (IoCs) and other important data worth sharing with the public. Some of these reports can help others prepare to respond to attackers and their attacks.
In this section, we will discuss various reports related to the Egregor ransomware and try to gather as much TTP information as possible.
We start the discussion with the Group-IB report “Egregor Ransomware: The Legacy of Maze Lives On,” which I co-authored. The report is available at the following link: Group-IB Egregor Report.
All ransomware attacks begin with initial access to the target network. According to the report we analyzed, Egregor’s affiliates used Qakbot distributed via phishing emails to gain access. Targeted phishing is one of the most common and very effective methods for gaining network access. Attackers know they can target regular users who may lack the technical skills to recognize the attack.
So, what is Qakbot? Initially, it was a banking trojan first discovered in 2007. Now, it is primarily used to load other tools, such as Cobalt Strike Beacon, and to send spam on a large scale from infected hosts to infect more devices. Many ransomware operators, including ProLock, Egregor, REvil, Conti, and others, use this trojan to gain initial access to target networks.
The Group-IB report also includes information about Qakbot’s persistence mechanisms in infected systems. These mechanisms include placing instances or shortcuts (LNK) in the startup folder, recording program paths in the Run key of the system registry, and creating scheduled tasks.
In the post-exploitation phase, Cobalt Strike was used. This commercial full-featured post-exploitation framework was initially created to simulate advanced attacks but quickly became part of real attackers’ toolkits, allowing them to use many methods described in MITRE ATT&CK.
According to the report, attackers also used ADFind to gather Active Directory (AD) information. As you learned in the previous chapter, this tool is quite common in ransomware attacks.
To achieve lateral movement, Egregor’s affiliates scripted necessary changes in the registry and firewall to use Remote Desktop Protocol (RDP). The script was propagated via PsExec, a legitimate tool from the Sysinternals Suite that allows commands to be executed on remote hosts. Legitimate tools and various scripts are the main means to help attackers stay stealthy.
Another common method used by Egregor-related personnel is process injection via Cobalt Strike Beacon. This technique can be used for lateral movement within the compromised network. Such methods allow attackers to hide the commands they use, not exposing their presence.
To exfiltrate confidential data from the network, Egregor’s operators used Rclone, a command-line tool for managing files in cloud storage. They also used obfuscation techniques, renaming the Rclone executable to svchost.exe.
To disable antivirus protection, attackers used Group Policy and scepinstall.exe to remove System Center Endpoint Protection (SCEP). Such attacks are a clear example of attackers abusing legitimate features of modern operating systems.
Egregor’s affiliates used various script-based methods to deploy ransomware, including:
- Abusing Background Intelligent Transfer Service (BITS) to download ransomware from attacker-controlled servers and run it via rundll32;
- Sharing the C:\ drive of remote hosts as a network resource, copying ransomware to C:\Windows, and running it via rundll32;
- Copying and running ransomware via PowerShell sessions on remote hosts.
As you can see, even a single report can be a good source of information, but additional data is never harmful.
Let’s study another report, this time published by Cybereason, titled “Cybereason vs. Egregor Ransomware.” The report is available at the following link: Cybereason Egregor Report.
We need to analyze the report, extract data we do not yet have, and turn it into actionable CTI.
First, from Cybereason’s report, we see that Egregor’s affiliates not only infected target networks via Qakbot but also used Ursnif and IcedID. Like Qakbot, these two malware families were previously banking trojans but are now widely used to load other tools. Attackers often develop new features to make their attacks more profitable.
Additionally, according to the report, Egregor’s operators used SharpHound (the data collector for BloodHound, commonly used by penetration testers and attackers to find connections in Active Directory) to gather information about users, groups, computers, etc.
We successfully collected more CTI, so let’s study another document, this time a report from Morphisec titled “An Analysis of the Egregor Ransomware.” The report is available at the following link: Morphisec Egregor Report.
According to this report, Egregor’s users gained initial access through vulnerabilities in firewalls, entering the Virtual Private Network (VPN), this time without using trojans.
Attackers used legitimate remote access software, such as AnyDesk and SupRemo, to maintain access to the infected network. In 2021, AnyDesk became one of the most common tools used by attackers for backup access.
To terminate unwanted processes (such as those belonging to antivirus software), attackers used the free anti-rootkit tool PowerTool and collected information about the infected network using the popular free tool SoftPerfect Network Scanner.
To obtain credentials, Egregor’s operators used Mimikatz, a tool commonly used by penetration testers and attackers to extract passwords and other authentication materials—hashes, PINs, and Kerberos tickets—from memory.
Attackers exfiltrated data via various cloud services, such as WeTransfer and SendSpace, as well as the MEGA Desktop App. To execute scripts on remote hosts, attackers used PsExec to run ransomware on these hosts.
Finally, to cover their tracks, attackers used SDelete, a command-line tool for irreversibly deleting files. Let’s summarize the results obtained from the analysis of all three reports.
Egregor’s operators infected target hosts via phishing emails or gained initial access through VPN vulnerabilities.
Egregor’s operators used various persistence mechanisms, including the startup folder, the Run key in the system registry, and scheduled tasks.
To gather information about the infected network and Active Directory, Egregor’s operators used ADFind, SharpHound, and SoftPerfect Network Scanner.
In the post-exploitation phase, Cobalt Strike was used.
There are thousands of incident response experts worldwide, and some of them are willing to share the data they obtain from their work. We’ve already discussed threat research reports, but creating these reports usually takes a considerable amount of time. Therefore, response experts often use other platforms to briefly introduce the new knowledge they’ve gained. One of the most popular media platforms is Twitter.
If you encounter a ransomware attack and have identified the type of ransomware, you can find a lot of information about the attackers and their TTPs (Tactics, Techniques, and Procedures) on Twitter. The most important thing is to understand the attackers. Typically, ransomware operators use specific tools and processes at certain stages of the attack lifecycle.
Let’s start with the ransomware RagnarLocker and look at the following tweet from Peter Mackenzie, Director of Incident Response at Sophos (Figure 6.1): Twitter link.
What can we learn from this tweet? First, we see that attackers associated with RagnarLocker may use ProxyLogon (Common Vulnerabilities and Exposures, CVE-2021-26855) to gain initial access to the target. ProxyLogon is a vulnerability in Microsoft Exchange Server that allows attackers to bypass authentication and impersonate an administrator.
To gather internal network information, RagnarLocker operators used Advanced IP Scanner, a free network scanner developed by Famatech Corp, which is quite popular among various RaaS (Ransomware-as-a-Service) users.
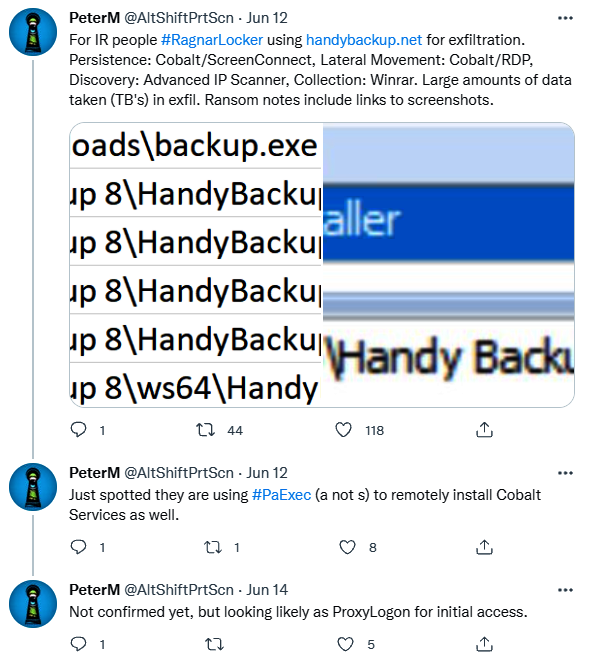
Figure 6.1 shows information related to RagnarLocker.
Like many other attackers, RagnarLocker’s partners extensively use Cobalt Strike during the post-exploitation phase, including lateral movement (and RDP). To load instances onto remote hosts, attackers used PaExec, an open-source alternative to Sysinternals’ PsExec.
To maintain backup access to the compromised network, RagnarLocker operators used ScreenConnect, a legitimate remote management software. Attackers can exploit such software to access compromised networks, even though the software is designed for legitimate purposes.
Attackers used WinRAR to compress the collected confidential data and Handy Backup, a commercial backup solution, to steal data from the target host. During the data exfiltration phase, attackers often use compression and password protection, but these behaviors can be detected through various clues.
As you can see, even a few Twitter messages can provide a lot of valuable information. Let’s look at another tweet from the same author (Figure 6.2).
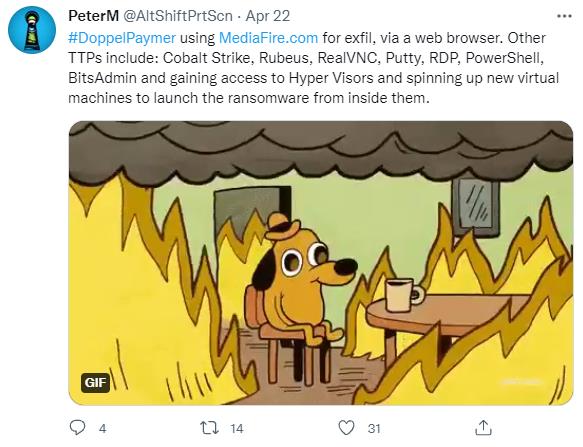
Figure 6.2 shows information related to DoppelPaymer.
Like RagnarLocker’s attackers, DoppelPaymer operators actively use Cobalt Strike during post-exploitation.
Additionally, we see that attackers use Rubeus, a fairly popular toolkit for interacting with and attacking Kerberos.
Another legitimate remote access tool used by attackers to ensure backup access is TightVNC.
Finally, DoppelPaymer operators use RDP for lateral movement—a very common method used by attackers for initial access and to access remote hosts within the target network.
Interestingly, the method of creating virtual machines (VMs) to run ransomware within them was initially attempted by Maze and RagnarLocker’s partners but is now also used by other groups, including DoppelPaymer.
As shown in Figure 6.3, DoppelPaymer operators have a dedicated data leak site (DLS) for storing stolen information. According to analysis sources, they use MediaFire to store data.
As you can see, we can obtain a lot of valuable data about ransomware attackers from just one tweet.
Let’s look at another tweet from Taha Karim, Director of Threat Analysis at Confiant (Figure 6.3).
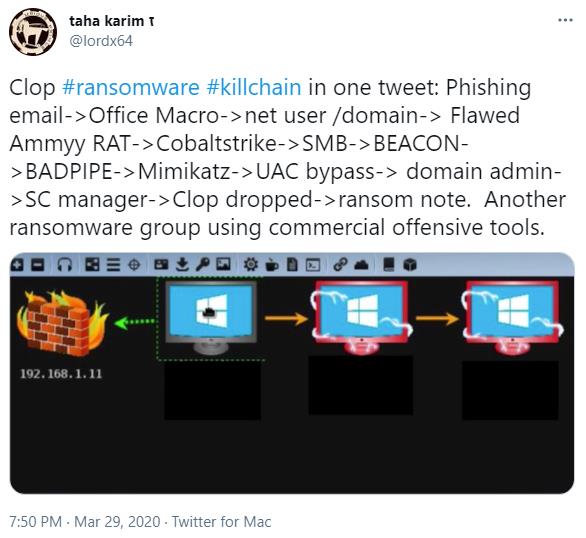
Figure 6.3 shows information related to Clop.
Notably, this tweet was posted long before any information about Clop operators’ TTPs was publicly available.
As the tweet indicates, Clop operators use phishing campaigns to infect victims with the FlawedAmmyy RAT. FlawedAmmyy is a common remote access trojan (RAT) often associated with TA505. This RAT is based on the leaked source code of Ammyy Admin, allowing attackers to secretly manipulate infected hosts.
We already know that Cobalt Strike is very popular among attackers, and Clop users are no exception. As you can see, it allows attackers to bypass User Account Control (UAC) and use common credential dumping tools like Mimikatz. Despite leaving many traces, ransomware propagators still actively use it.
Finally, the tweet shows that Clop users abuse the Service Control Manager (SCM) to deploy ransomware across the enterprise.
Unfortunately, it’s not always possible to obtain enough information to understand the TTPs used by attackers during the attack lifecycle. Additionally, information about the ransomware itself may be needed. Here is a tweet from Andrey Zhdanov, who actively tracks BlackMatter ransomware samples (Figure 6.4).
Figure 6.4 shows information related to BlackMatter.
As you can see, there is not much information about TTPs in this tweet, but there is a link to the sample being analyzed and some information about its capabilities.
Twitter is not the only media platform for collecting such analysis: LinkedIn is another useful source. Additionally, you can always request incident response experts and CTI analysts to share the data they find, so don’t hesitate to engage with the global community.
Let’s discuss a more interesting CTI source—attackers themselves.
Attackers
As you know, this book is about human-operated ransomware attacks. Our adversaries are humans, and people communicate and share information, which often happens on underground forums.
In this section, we will examine forum messages collected by the Group-IB Threat Intelligence platform.
The first post was created by an attacker named FishEye, associated with collaboration programs like REvil and LockBit.
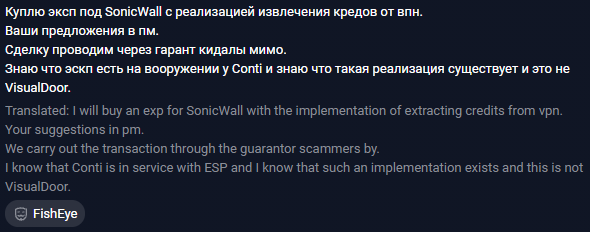
Figure 6.5 shows FishEye’s post.
The attacker wants to obtain a working exploit for a SonicWall VPN vulnerability. He mentions that Conti ransomware operators have already used it in their activities.
It’s likely that the attacker is referring to a vulnerability in SonicWall Secure Mobile Access (SMA) 100 series products (CVE-2021-20016). This vulnerability can be exploited remotely, allowing criminals to access credentials, which they can use to enter the internal network and use these credentials during the post-exploitation phase.
The next post was published by the notorious representative of REvil, UNKN (Figure 6.6).
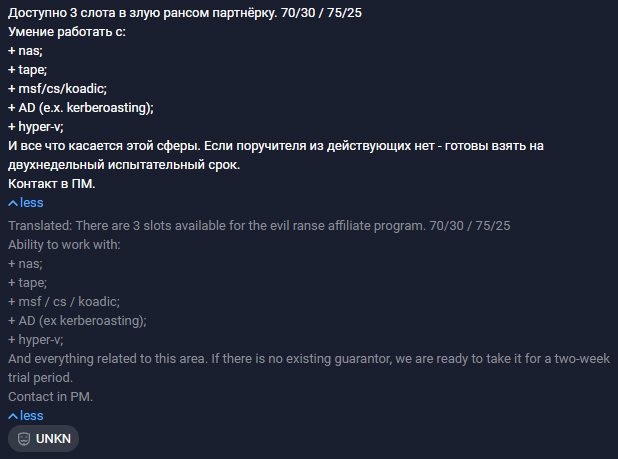
Figure 6.6 shows UNKN’s post.
The post invites collaboration in REvil’s RaaS program and describes the requirements for partners. First, we see that potential participants need to be able to handle backup technologies—Network Attached Storage (NAS) and tape data storage.
Secondly, the attacker points out that potential partners need to be able to use various post-exploitation frameworks. Here are some of them:
- Metasploit Framework
- Cobalt Strike
- Koadic
Additionally, participants need to be able to attack Active Directory, including kerberoasting attacks, which allow attackers to extract service account hashes and crack passwords in an offline environment.
Finally, since many modern enterprise networks use virtualization technologies, participants need to understand and be able to attack technologies like Hyper-V.
As you can see, in some cases, attackers share a lot of information about their potential TTPs. They also frequently comment on various issues discussed on forums. For example, here is a comment from LockBit ransomware operator LockBitSupp about data theft methods (Figure 6.7).
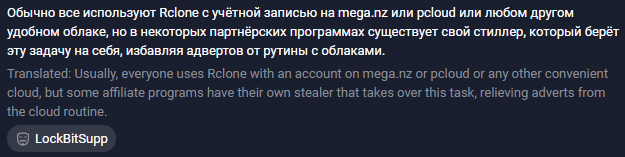
Figure 6.7 shows LockBitSupp’s post.
The attacker describes a popular method used by ransomware operators to steal data from compromised networks. According to the post’s author, criminals usually use Rclone and accounts from common cloud storage providers like MEGA and pCloud. He also mentions that some RaaS programs provide dedicated data theft tools (stealers). In fact, he is advertising the StealBit tool provided for LockBit ransomware users.
Another post by the same attacker involves disabling antivirus software across the enterprise (Figure 6.8).
Figure 6.8 shows LockBitSupp’s post.
Abusing Group Policy Objects (GPO) is not only used to disable security products; it is also a widespread method for executing various scripts across the enterprise. Notably, LockBit ransomware itself has built-in functionality to abuse GPOs to propagate its copies within enterprise networks.
The last post we will discuss was published by a LockBit ransomware user named uhodiransomwar (Figure 6.9).
Figure 6.9 shows uhodiransomwar’s post.
In this conversation, the attacker shares a list of compromised Pulse Secure VPN servers that other hackers can use to gain initial access to networks. It’s likely that these servers are vulnerable to CVE-2019-11510, which allows attackers to obtain valid credentials using arbitrary file read methods.
As you can see, there are indeed many opportunities to collect useful CTI that can significantly simplify your work in responding to ransomware-related incidents.
Conclusion
In this chapter, we discussed various CTI sources related to ransomware. We analyzed several public reports and extracted valuable data that allowed us to reconstruct parts of the attack lifecycle and turn it into CTI.
We learned how to analyze social media to gather threat information shared by members of the cybersecurity community.
Finally, we examined underground forums to understand how to obtain CTI directly from our adversaries—the ransomware operators.
Now that you have learned a lot about human-operated ransomware attacks and have a clear understanding of how these attacks occur, you are ready to delve into the investigation process.
In the next chapter, we will discuss the primary sources of digital forensic evidence that enable incident response teams to reconstruct ransomware attacks and determine what was done at each stage of their lifecycle.
Chapter 7: Digital Forensic Evidence and Its Primary Sources
You have already learned a lot about human-operated ransomware attacks, including the most common tactics, techniques, and procedures (TTPs) used by attackers, and how to accelerate incident investigations by collecting useful cyber threat intelligence. Now, it’s time to focus on the investigation process itself.
You may have heard of Locard’s exchange principle, but I’ll remind you: criminals always leave traces at the crime scene and take something with them. These traces can be used as evidence.
This sounds familiar, doesn’t it? Ransomware users leave their tools
- Collect and analyze volatile memory
- Collect non-volatile memory data
- Master File Table
- Prefetch files
- Shortcuts (LNK files)
- Jump Lists
- System Resource Usage Monitor
- Web browsers
- Windows Registry
- Windows Event Logs
- Other logs
Collect and Analyze Volatile Memory
Since many attackers use off-the-shelf tools—i.e., tools already present in the target infrastructure, analyzing volatile memory helps find critical traces that are essential for incident response experts to accurately reconstruct the intrusion methods. Otherwise, attackers might evade the security team’s notice.
Volatile data is typically stored in a device’s Random Access Memory (RAM), and extracting this data usually involves creating a memory dump.
There are many tools available for dumping volatile memory. Here are some of them:
- AccessData FTK Imager (Download link)
- Belkasoft RAM Capturer (Download link)
- Magnet RAM Capturer (Download link)
Note: Never copy the data collection tools and the acquired memory dump files to the same device. Use an external hard drive or network resources. Why? Because you might accidentally overwrite potential sources of digital traces!
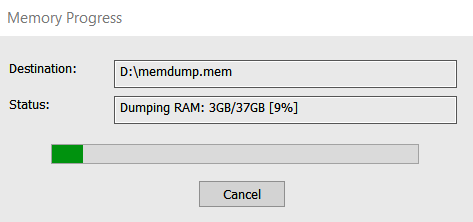
Figure 7.1 shows an example of memory capture using AccessData FTK Imager.
The most popular memory dump analysis tool is Volatility, an open-source platform for forensic investigation of memory dumps. At the time of writing, this tool has two versions:
- Volatility 2 (Download link)
- Volatility 3 (Download link)
Both versions require at least some command-line operation skills, but they are not difficult to learn thanks to clear instructions.
If you prefer not to use the command line, you can try PassMark’s Volatility Workbench—a graphical user interface (GUI) for Volatility.
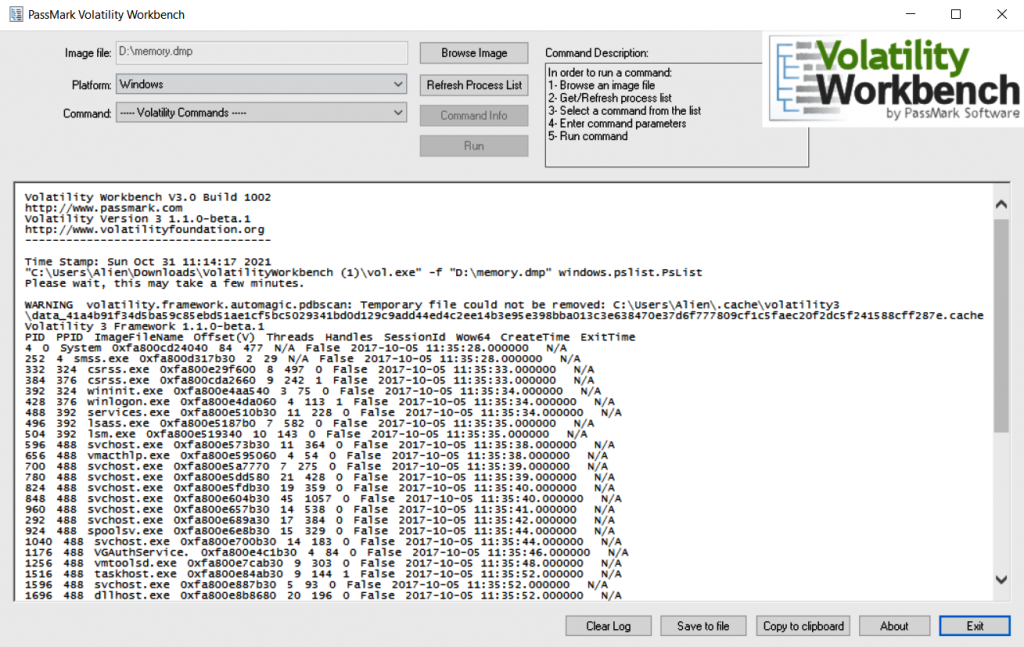
Figure 7.2 shows the process of launching Volatility plugins through PassMark Volatility Workbench.
Memory dump analysis helps uncover a lot of evidence related to attacks, which can then serve as important Indicators of Compromise (IoC) for enterprise-wide threat detection.
PassMark Volatility Workbench has versions for both Volatility 2 and Volatility 3. Both versions can be downloaded from here.
Memory dumps are not always the best analysis method. You might not know which hosts need to be checked, and analyzing memory dumps from hundreds of machines is a time-consuming and inefficient strategy.
Some tools allow incident response experts to perform real-time analysis. For example, Process Hacker is a tool popular among attackers but can also be used by defenders. It allows for the inspection of volatile memory data, including running processes, their command lines, and network connections, among other features. Figure 7.3 shows an example of real-time analysis using Process Hacker.
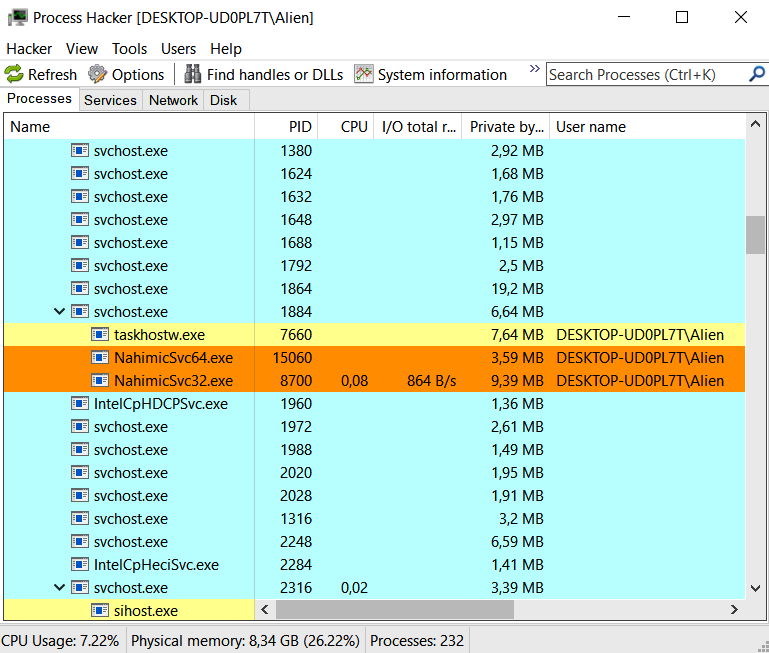
Figure 7.3 shows the inspection of running processes using Process Hacker.
Process Hacker can be downloaded from here. Interestingly, volatile memory traces can be found not only in memory dumps. Some system files also contain memory remnants:
pagefile.sys—This file is located in the root directory of the system drive (usually C:\) and is used to store currently unused memory pages, also known as swap files or virtual memory. Although it cannot be analyzed using Volatility, other tools can be used, such as page_brute.hiberfil.sys—The Windows hibernation file, also stored in the root directory of the system drive, is used to save the machine’s state during hibernation. This file can be converted using the Volatility plugin imagecopy and then analyzed like a regular memory dump.
We will return to discussing file system evidence and how it can help us investigate ransomware attacks. But first, we need to learn how to collect non-volatile memory data—data accessible when the system is turned off.
Collect Non-Volatile Memory Data
Before diving into various sources of non-volatile memory data, let’s understand how to acquire this data. You might have heard of forensic imaging—a bit-by-bit copy of a digital storage device. Sometimes we still create such images, for example, for the first compromised host, as it may contain a lot of various evidence related to attacker activities. AccessData FTK Imager can be used to create these images.
However, there may be quite a few compromised hosts, and cloning each system is a labor-intensive task. In such cases, you can create selective images that include a set of files and some additional data, such as network connection information.
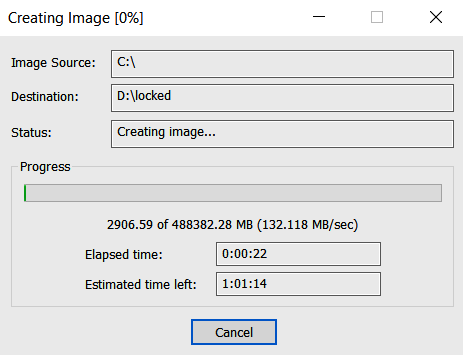
Figure 7.4 shows an example of creating an image using AccessData FTK Imager.
Live Response Collection (Download link) is a good tool developed by Brian Moran for collecting initial data.
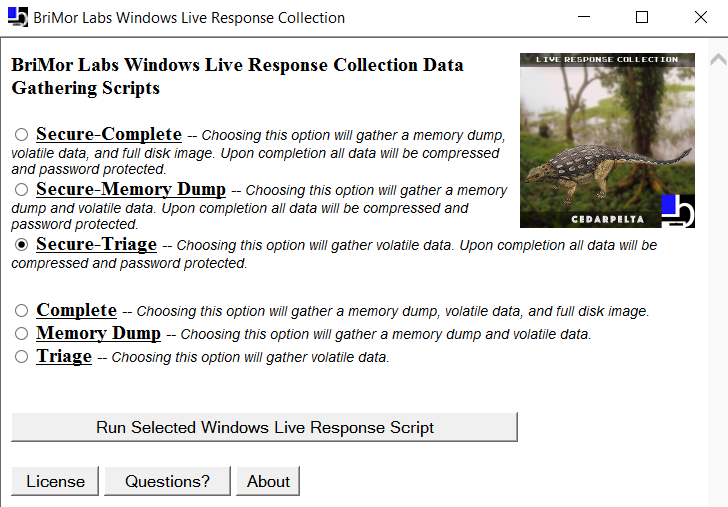
Figure 7.5 shows an example of creating an initial processing image using Live Response Collection.
Interestingly, this tool can not only collect initial data but also copy memory and even create full images. Remember, these tools should be run from an external hard drive or network resources.
If you need more targeted operations, you can use Kroll Artifact Parser and Extractor (KAPE), which allows incident response experts to perform highly focused and compact data collection. It has both graphical and command-line versions (Figure 7.6) and can be used enterprise-wide.
Additionally, KAPE is not only used for data collection but also for automating data processing. There are also some agent solutions, including open-source ones, that can collect data in real-time. A good example is Velociraptor.
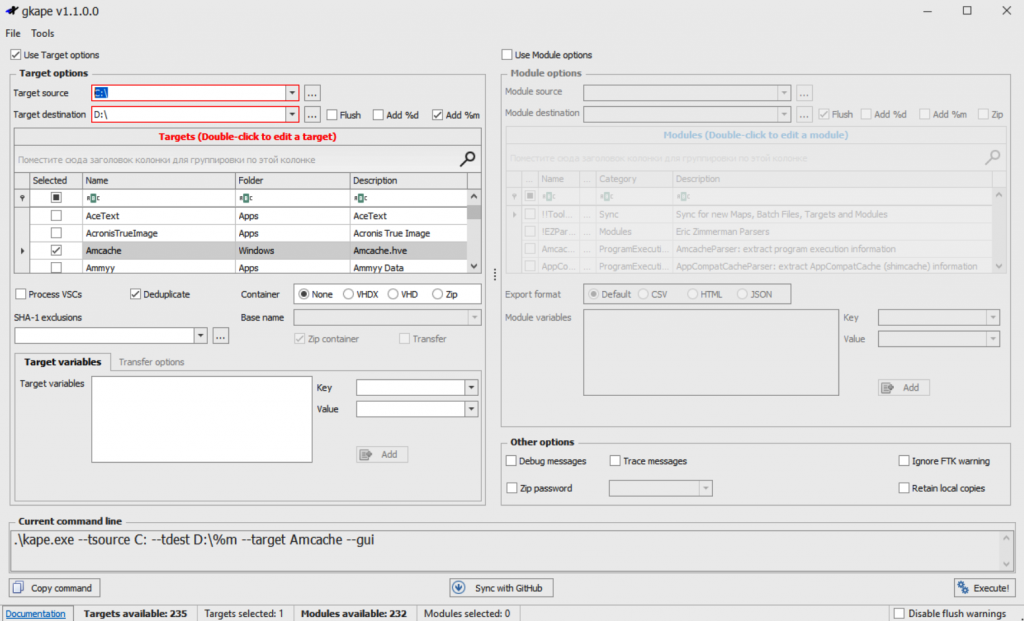
Figure 7.6 shows targeted data collection using KAPE.
Many EDR/XDR solutions also allow for the collection of forensic evidence. The figure below shows the data collection parameters of the Group-IB Managed XDR framework.
EDR/XDR solutions themselves are very valuable sources of forensic evidence as they continuously collect information about running processes, network connections, file and registry changes, etc. As you can see, there are quite a few options for collecting volatile and non-volatile data. Now, let’s explore the sources of various digital forensic evidence.
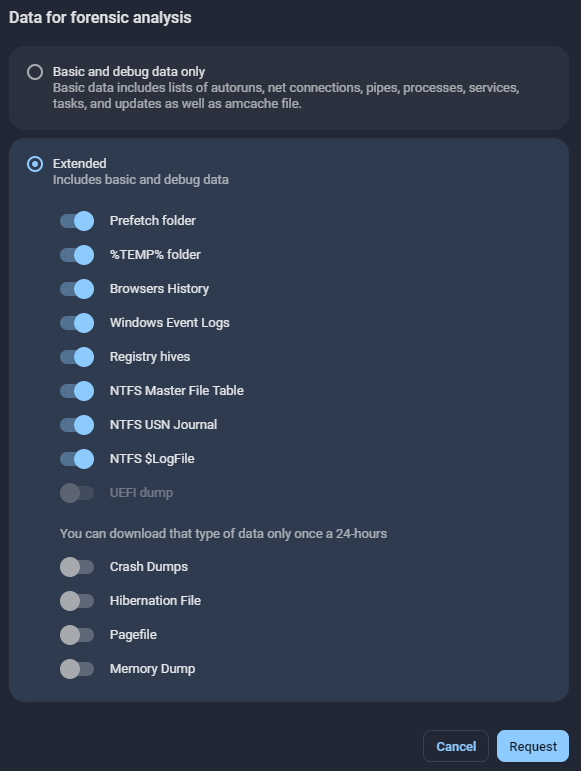
Figure 7.7 shows the data collection parameters of the Group-IB Managed XDR framework.
Master File Table
The file system contains many different pieces of evidence that can help with investigations. The Windows Registry and various logs also belong to the file system, but they are quite complex and will be discussed separately.
The most common file system type you will encounter when investigating ransomware attacks is the New Technology File System (NTFS). Currently, this is the most common file system in Windows operating systems—as you already know, the primary target of ransomware users. Although interest in Linux systems has increased, attackers typically gain access to these systems by compromising Windows infrastructure, so we will focus on this operating system.
As incident response experts, we are primarily concerned with metadata analysis, so let’s examine a major component of NTFS—the Master File Table (MFT). It contains information about file names, locations, sizes, and timestamps. We can use the information extracted from the MFT to build a timeline, which helps us recover information about files created and used by the attackers.
This information can be extracted from the $MFT metafile. Metafiles, including $MFT, can be extracted using various digital forensic tools. One example tool is AccessData FTK Imager.
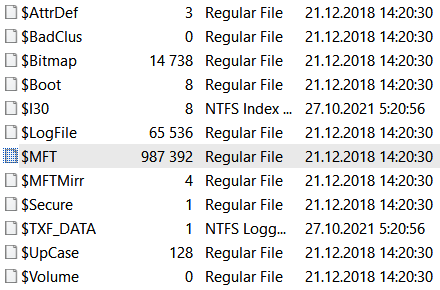
Figure 7.8 shows $MFT and other NTFS metafiles displayed in AccessData FTK Imager.
I won’t tire you with the internal structure of NTFS—there are many excellent resources on this topic, such as Brian Carrier’s “File System Forensic Analysis”.
What to do after extracting the $MFT metafile? You can view it directly or parse it first and then analyze the extracted data.
I will reference Eric Zimmerman, the 2019 “Forensic Investigator of the Year” and SANS instructor, and his famous free digital forensic toolset. These tools can be obtained from here.
If you prefer to view the $MFT directly, you can use MFTExplorer. Unfortunately, these viewing tools are not fast, so I recommend parsing the metafile first. For this, there is a separate tool—MFTECmd. Using it, you can convert the data from the $MFT into an easy-to-read comma-separated values (CSV) file, which you can analyze using your favorite tool, such as Microsoft Excel.
Another tool available in Eric Zimmerman’s toolset is Timeline Explorer. Below is an example of an $MFT file analyzed through Timeline Explorer.
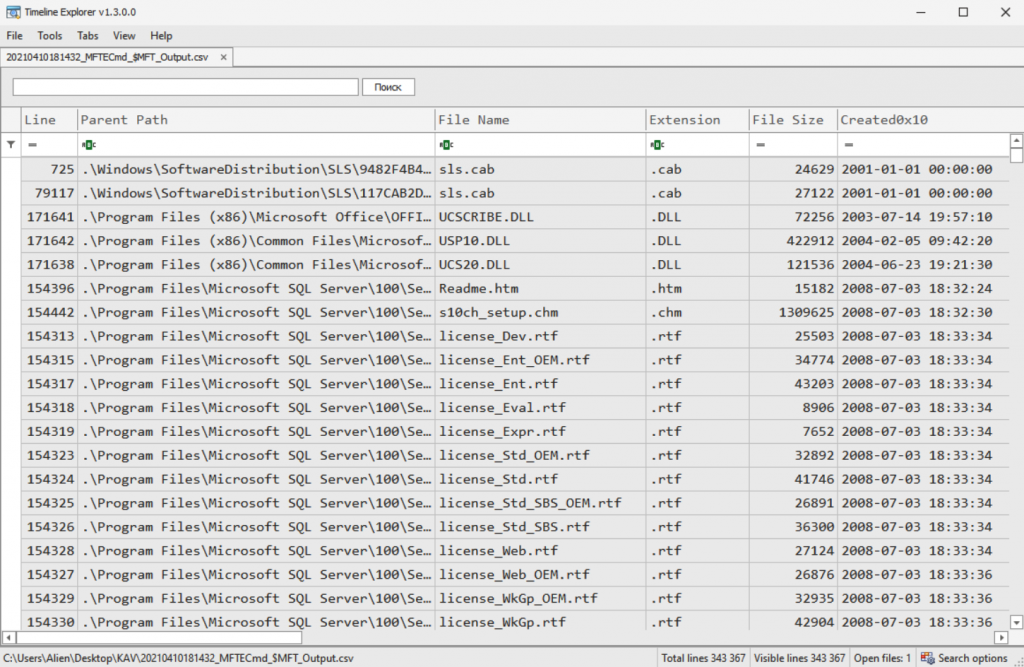
Figure 7.9 shows an analyzed $MFT file opened in Timeline Explorer.
Timeline Explorer allows you to select columns to focus on. It also has convenient filtering features that enable you to easily exclude unwanted content. In the Windows operating system, there are many sources of evidence useful to incident response experts. Let’s start with sources that help collect execution traces, beginning with prefetch files.
Prefetch Files
Prefetch files are located in the C:\Windows\Prefetch folder and are used to improve system performance by preloading code for frequently used applications.
These files have a .pf extension and contain timestamps of program execution and the number of executions, as well as a list of folders and files interacted with by the executable. Prefetch files can be analyzed using PECmd.
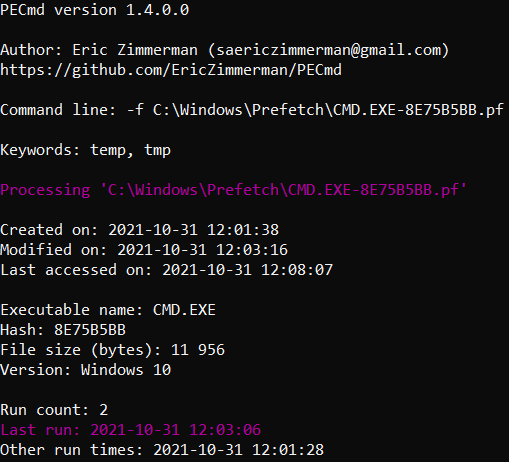
Figure 7.10 shows part of the output from PECmd.
Of course, prefetch files are not the only source of program execution traces. Other sources will be discussed in the “Windows Registry” and “Windows Event Logs” sections. Now let’s look at evidence of file access—LNK files and Jump Lists.
LNK Files
LNK files (or “shortcuts”) are automatically created by the Windows operating system when a user (or attacker) opens a local or remote file. These files can be found in the following locations:
- C:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\
- C:%USERPROFILE%\AppData\Roaming\Microsoft\Office\Recent\
These files contain data such as timestamps for the LNK file itself and the file it points to (i.e., the opened file, which may have been deleted).
There is a tool that can parse these files—LECmd.
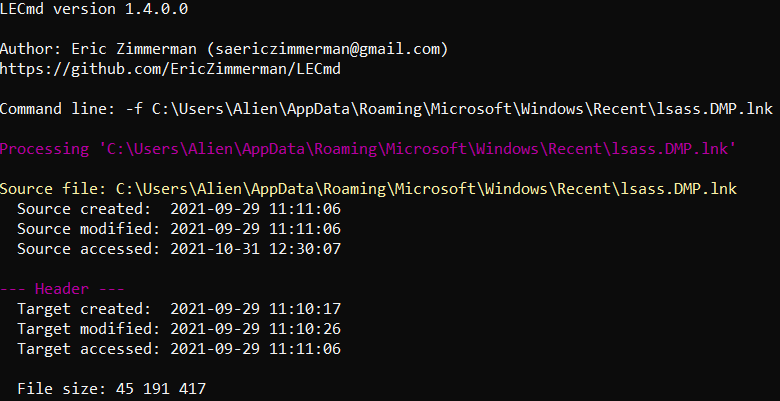
Figure 7.11 shows part of the output from LECmd.
The screenshot shows evidence of an attacker using a very common credential dumping method to perform an LSASS dump. Now let’s look at another similar digital forensic evidence source related to the file system—Jump Lists.
Jump Lists
Jump Lists are a feature of the Windows taskbar that allows users to view a list of recently used items. Incident response experts can use this feature to examine the list of recently accessed files.
These files can be found in the following folder:
- C:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations
There is a graphical interface tool that can view the contents of these files—JumpList Explorer.
As shown in Figure 7.12, Jump Lists contain not only file information but also information such as hosts accessed via RDP. This is very useful when tracking lateral movement within a network.
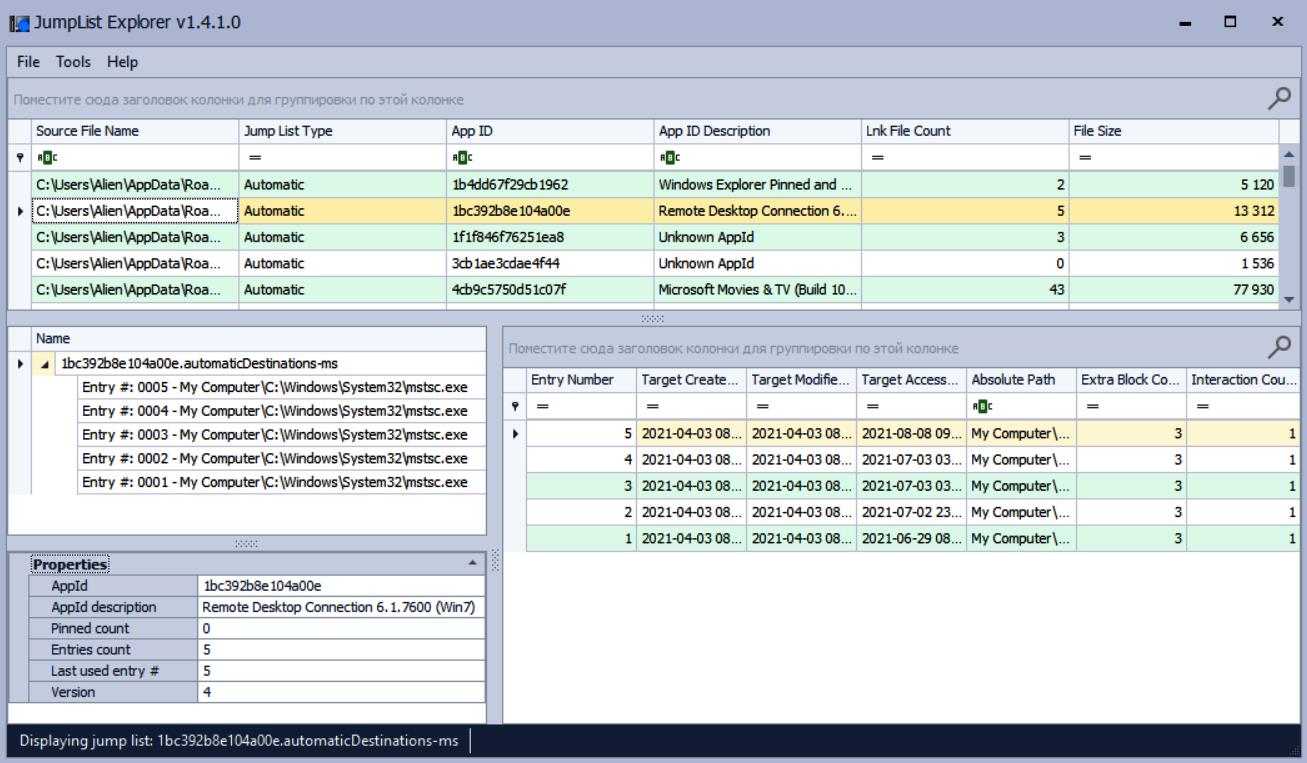
Figure 7.12 shows the process of viewing Jump Lists using JumpList Explorer.
Now let’s look at one of the tools for investigating data theft—System Resource Usage Monitor (SRUM).
System Resource Usage Monitor
Windows uses this feature to monitor system performance, which helps incident response experts obtain the amount of data sent/received by each application per hour, which is crucial when investigating data theft.
The SRUM data database is located in the C:\Windows\System32\SRU folder.
You may also need the SOFTWARE registry hive file from the C:\Windows\System32\config folder for proper data analysis.
Both files can be processed using SrumECmd. The generated files can be viewed using Timeline Explorer (Figure 7.13).
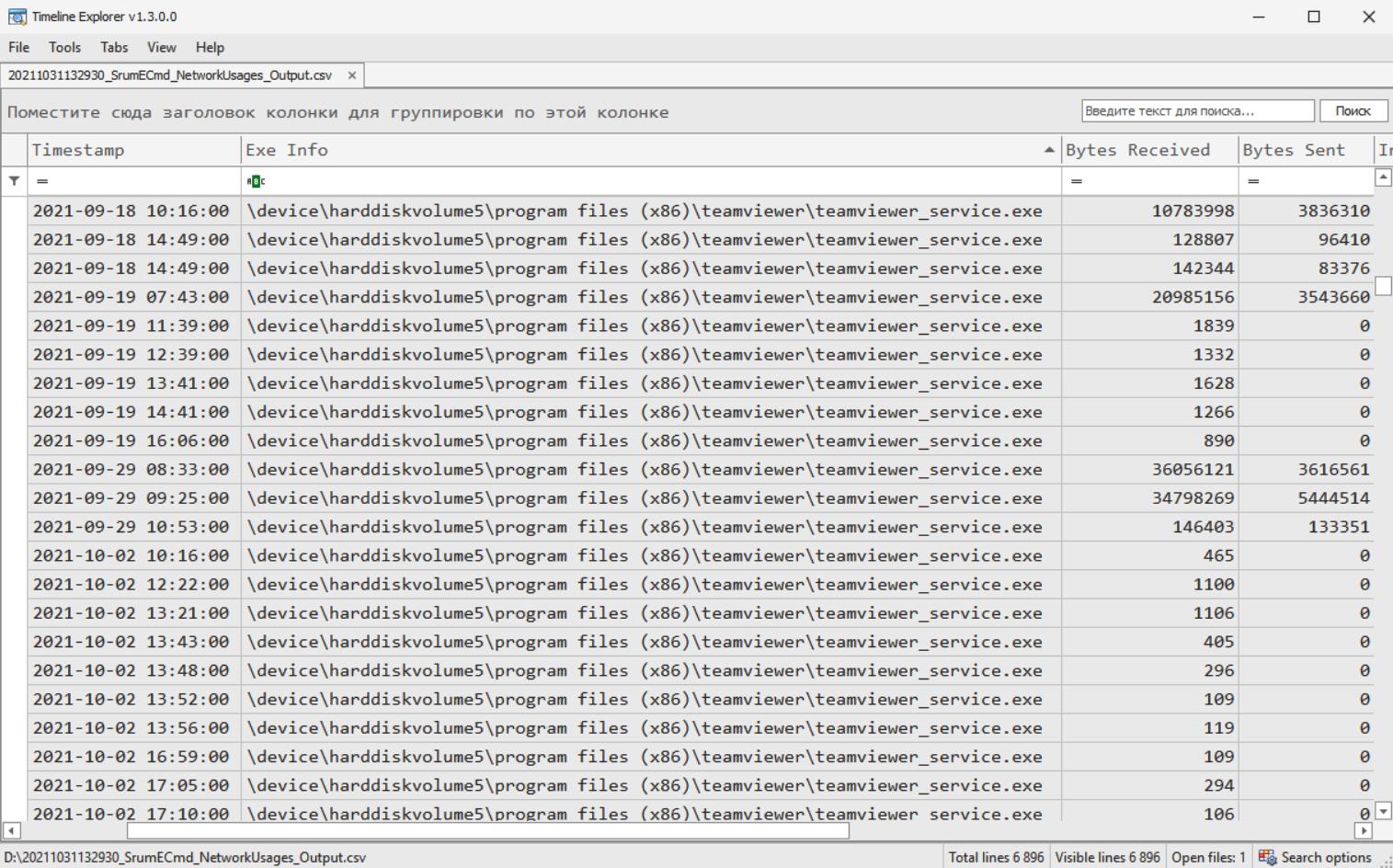
Figure 7.13 shows the analyzed SRUM data viewed through Timeline Explorer.
What other tools do attackers use to steal data and duplicate tools? Of course, web browsers!
Web Browsers
Web browsers are widely used by regular users who may fall victim to phishing attacks and are also used by attackers to download additional tools and steal data.
Let’s focus on three major browsers—Microsoft Edge, Google Chrome, and Mozilla Firefox.
The main evidence sources related to browsers are browsing history. Its analysis can reveal the sources from which attackers downloaded tools or where they stored data. This data is usually stored in SQLite databases and can be found in the following locations:
- Microsoft Edge: C:\Users%USERNAME%\AppData\Local\Microsoft\Edge\User Data\Default\History
- Google Chrome: C:\Users%USERNAME%\AppData\Local\Google\Chrome\User Data\Default\History
- Mozilla Firefox: C:\Users%USERNAME%\AppData\Roaming\Mozilla\Firefox\Profiles\.default\places.sqlite
SQLite databases can be manually analyzed using tools like DB Browser for SQLite (download link), or using specialized browser forensic tools like BrowsingHistoryView (download link).
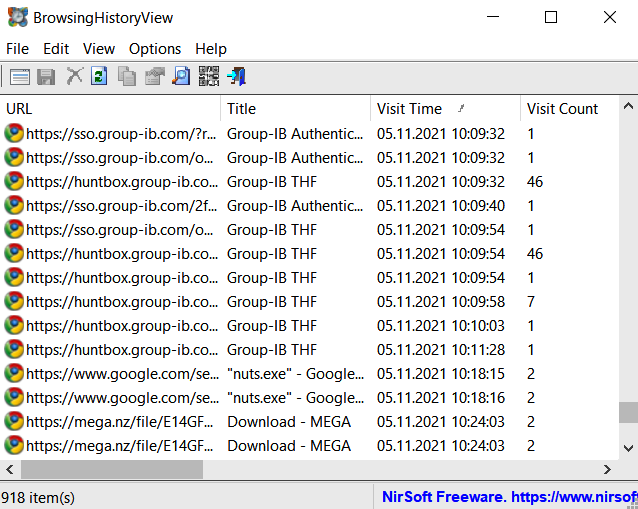
Figure 7.14 shows the process of analyzing web search history using BrowsingHistoryView.
Useful forensic evidence also includes cookie files and cache.
Cookie files allow web browsers to track and save information about each user session, including visited websites. This information is also stored in SQLite databases:
- Microsoft Edge: C:\Users%USERNAME%\AppData\Local\Microsoft\Edge\User Data\Default\Cookies
- Google Chrome: C:\Users%USERNAME%\AppData\Local\Google\Chrome\User Data\Default\Cookies
- Mozilla Firefox: C:\Users%USERNAME%\AppData\Roaming\Mozilla\Firefox\Profiles\.default\cookies.sqlite
Another browser-related evidence is its cache, which stores local copies of web components for faster loading during subsequent visits.
Here are the locations of cache files for different browsers:
- Microsoft Edge: C:\Users%USERNAME%\AppData\Local\Microsoft\Edge\User Data\Default\Cache
- Google Chrome: C:\Users%USERNAME%\AppData\Local\Google\Chrome\User Data\Default\Cache
- Mozilla Firefox: C:\Users%USERNAME%\AppData\Roaming\Mozilla\Firefox\Profiles\.default\Cache
Several tools can interpret the data stored in cache files. Some tools include ChromeCacheView (download link) and MozillaCacheView (download link), but there are other tools as well.
Another source of digital evidence is the Windows Registry.
Windows Registry
The Windows Registry is a hierarchical database that stores various configuration parameters and important information about program launches and user activities.
The locations of registry files are as follows:
- SAM, SYSTEM, and SOFTWARE files are located in the C:\Windows\System32\config folder.
- NTUSER.DAT and USRCLASS.DAT files are user-specific, with NTUSER.DAT located in the C:\Users%USERNAME% folder and USRCLASS.DAT located in the C:\Users%USERNAME%\AppData\Local\Microsoft\Windows folder.
- The Amcache.hve file is located in the C:\Windows\AppCompat\Programs folder.
- The Syscache.hve file is located in the C:\System Volume Information folder. It is only present in Windows 7 and Windows Server 2008 R2 but can be very useful as it contains SHA1 hashes of executed binaries.
Now let’s look at the most common sources of evidence that can be found when analyzing Windows Registry files:
- UserAssist (NTUSER.DAT\Software\Microsoft\Windows\Currentversion\Explorer\UserAssist{GUID}\Count) contains information about GUI programs launched by the user, including the number of launches and the last execution date and time.
- ShimCache (SYSTEM\CurrentControlSet\Control\Session Manager\AppCompatCache) contains information about executed programs, including their paths, sizes, and last modification dates.
- Amcache (Amcache.hve\Root\File{Volume GUID}#) contains information about executed programs, including their paths, SHA1 hashes, and first execution timestamps.
Of course, program launch traces are not the only digital evidence that can be extracted from the Windows Registry. Another important type of evidence is traces of recently used files and folders. Let’s look at the most common ones:
- Most Recently Used (MRU) (NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU) contains a list of recently used files based on file extensions.
- Recent files (NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs) is another source containing information about recently used files.
- Shell bags (USRCLASS.DAT\Local Settings\Software\Microsoft\Windows\Shell\Bags) contain a list of recently used folders, including network shares and removable devices.
These are just some examples of valuable evidence that can be found in the Windows Registry. Other examples include system persistence mechanisms, traces of remote access, etc.
There are various methods to analyze the registry. It can be done manually, focusing on keyword searches based on existing indicators of compromise. For example, you can use Registry Explorer (download link)—another useful tool developed by Eric Zimmerman, which allows you to view extracted registry files and the current registry, including deleted keys and values.
I recommend this tool for manual analysis, but it also provides many plugins for automated analysis of common evidence.
Figure 7.15 shows the SYSTEM registry file from a running system opened in Registry Explorer.
Another excellent registry analysis tool is Harlan Carvey’s RegRipper (Download Link). It comes in both graphical and command-line versions, along with various plugins for analyzing registry evidence. You can also write additional plugins yourself.
The next valuable source of digital forensic evidence is the Windows Event Logs.
Windows Event Logs
Logging is a built-in mechanism for the Windows operating system and its various applications to record different events. It can also be an extremely valuable source of evidence related to ransomware attacks.
Sometimes, attackers delete these logs to cover their tracks, which in itself can be a reliable indicator that the host has been compromised.
By default, log files are located in the C:\Windows\System32\winevt\Logs folder and have the .evtx extension.
Windows Event Logs can also be collected using SIEM (to ensure proper logging) or EDR/XDR solutions.
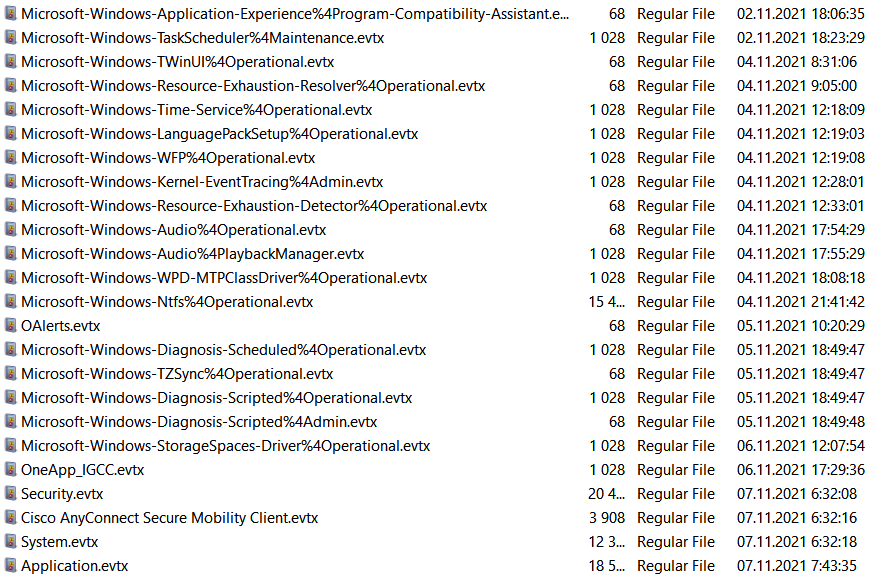
Figure 7.16 shows Windows Event Log files listed in AccessData FTK Imager.
Let’s look at some commonly used log files and event IDs.
Security Logs
- 4624—Successful logon to the system.
- 4625—Logon failure.
- 4720—User account created.
- 4732—Member added to a security-enabled local group.
System Logs
- 7045—A service was installed in the system.
- 7040—The start type of a service was changed.
- 7036—A service was stopped or started.
Windows PowerShell
- 400—Indicates the start of a command or a session.
Microsoft-Windows-TerminalServices-LocalSessionManager/Operational
- 21—Session logon succeeded.
- 24—Session disconnected.
- 25—Session reconnected.
Alerts
- 300—Alert created by Microsoft Office.
Microsoft-Windows-TaskScheduler/Operational
- 106—Scheduled task created.
- 200—Scheduled task started.
- 201—Scheduled task completed.
Microsoft-Windows-Windows-Defender/Operational
- 1117—The Malware Protection Platform has taken action to protect your system from malware or other potentially unwanted software.
This is not an exhaustive list, but we can see that there are many useful events that can help with incident response.
Events occurring in the Windows environment are not only recorded in the Windows Event Logs; other logs might also be useful to us.
Other Logs
Finally, let’s list some other logs that might play a crucial role in your investigation.
Antivirus Logs
As you know, ransomware operators might use many tools—meaning some of these tools will be detected by antivirus software. Antivirus logs can be very useful.
Firewall Logs
These logs can be a valuable source of information about network connections, including intrusion attempts. This is an extremely valuable source of forensic data, especially if data retention is long and you have some network compromise indicators.
VPN Logs
VPNs are a popular initial vector for network access, so VPN logs might also reveal some information about the attacker’s network infrastructure. GeoIP analysis can be very useful—you might find connections from countries unrelated to the company.
Proxy Logs
If you have network indicators or want to track anomalous events, check if proxy logs are available.
Web Server Logs
If you suspect ransomware operators used a web shell for initial persistence, make sure to check web server logs.
Mail Server Logs
Mail servers can also be vulnerable: recall how the Conti group used ProxyLogon to gain initial access. That’s why mail server logs can be very useful.
Now, you have a better understanding of various digital forensic evidence sources and are ready for the most interesting part—investigation.
Conclusion
In this chapter, we discussed the most common digital forensic evidence sources that can help incident response teams investigate ransomware attacks.
We explored the most popular evidence sources in the file system, registry, various logs, and learned how to extract data from volatile and non-volatile memory and convert the collected data into formats suitable for in-depth forensic analysis.
Now, you are ready to move on to more practical tasks—reconstructing an actual ransomware attack based on various digital forensic evidence.
In the next chapter, we will discuss several initial access scenarios and use the knowledge gained to understand how attackers gain initial access and perform post-exploitation.
Chapter 8: Initial Access Methods
In Chapter 7, we discussed various digital forensic evidence sources available in the Windows operating system. Now it’s time to analyze specific examples and understand how to use this evidence to reconstruct the lifecycle of a ransomware attack.
Let’s start with traces of the most common initial access methods—abusing external remote access services and phishing attacks.
Attacking external remote access services, especially public RDP servers, is extremely popular. Over 50% of successful attacks start by brute-forcing these servers.
Phishing attacks are similar—the precursors to ransomware attacks are often various bots massively spread via email and social networks.
In this chapter, we will discuss two cases based on real attack scenarios. We will cover the following topics:
- Collecting evidence to investigate attacks on external remote access services
- Investigating brute-force RDP attacks
- Collecting evidence to investigate phishing attacks
- Investigating phishing attacks
Collecting Evidence to Investigate Attacks on External Remote Access Services
To determine the initial attack vector, you first need to collect relevant data. Typically, my team has a brief list of possible intrusion methods based on observed attacker behavior. In fact, in real investigations, we usually only figure out the initial access method at the end of the analysis, as it often starts with investigating an encrypted host and mitigating the consequences. But in this chapter and the next, we will look for evidence step by step, as if we were tracking the lifecycle of a ransomware attack from start to finish. In real investigations, you can also perform the same analysis steps in reverse order.
In many ransomware-related incidents, the victim does not have advanced security products installed, so we will focus on methods and evidence that are almost always available.
Analyzing the abuse of external remote access services typically involves log analysis. These logs might be firewall logs, VPN logs, or the most common Windows Event Logs, especially when it comes to RDP attacks.
Interestingly, in many cases, when we are almost certain that the attack started with the compromise of a public RDP server, the client’s IT team will try to convince us that the organization has no such servers—despite firewall rules clearly indicating the presence or recent presence of such servers (the rules were just deleted). Sometimes the IT team wants to make your job more difficult and hide evidence because, in many incidents, human factors play a significant role—those who made the attack possible do not want to be caught.
Since we decided to focus on popular and, more importantly, free tools, we will use KAPE to collect data.
If you have already identified the server, you can directly connect an external hard drive and run the graphical version of KAPE, select the objects of interest, and start collecting data.
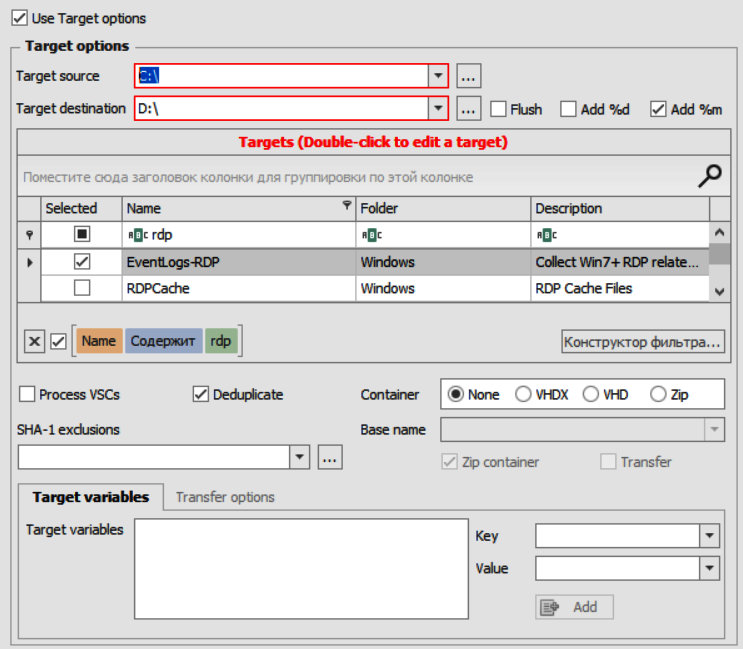
Figure 8.1 shows the process of collecting Windows Event Logs related to RDP using KAPE.
As shown in Figure 8.1, KAPE has a preset configuration for collecting logs related to RDP. Figure 8.2 shows the specific log files collected by this tool.
This way, we can obtain the following files:
- System.evtx
- Security.evtx
- Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
- Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
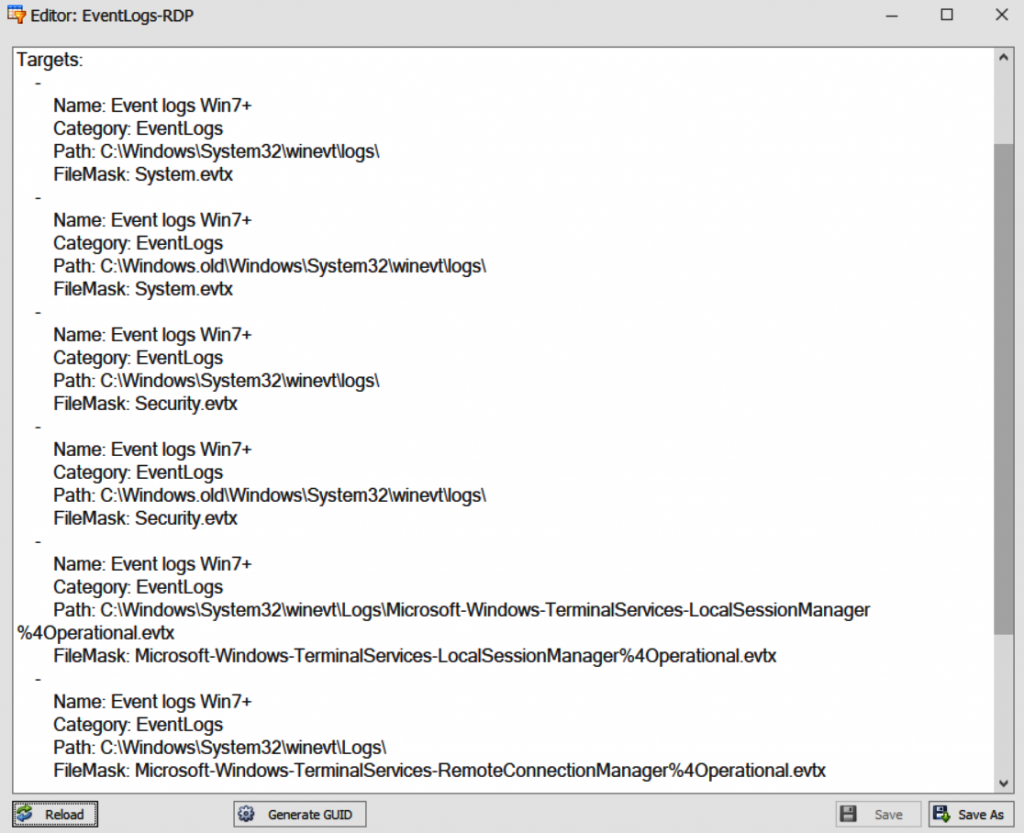
Figure 8.2 shows the Windows Event Log files collected for EventLogs-RDP configuration.
If there are multiple servers, or you are unsure which server to choose, you can use the command-line version of KAPE. For example, you can place it on a shared network drive and use Group Policy to collect data from multiple hosts simultaneously.
Investigating Brute-Force RDP Attacks
Therefore, we used KAPE to obtain some Windows Event Log files from a server believed to have been compromised through a brute-force attack for further analysis. Let’s focus on the Security.evtx file, as it contains many records suitable for this type of investigation. Here are two main event IDs useful for analyzing brute-force RDP attacks.
- 4624—Successful logon to the system
- 4625—Logon failure
The second event helps us identify intrusion attempts, while the first event shows successful logons.
You might need an event ID reference manual to understand what to focus on when investigating specific types of events.
Let’s review the collected event logs. First, check for the presence of events with ID 4625. Here, I will introduce another tool from Eric Zimmerman’s collection—EvtxExplorer. You can use it to analyze event log files and save the data in a readable format, such as CSV. The generated file can be analyzed using Timeline Explorer.
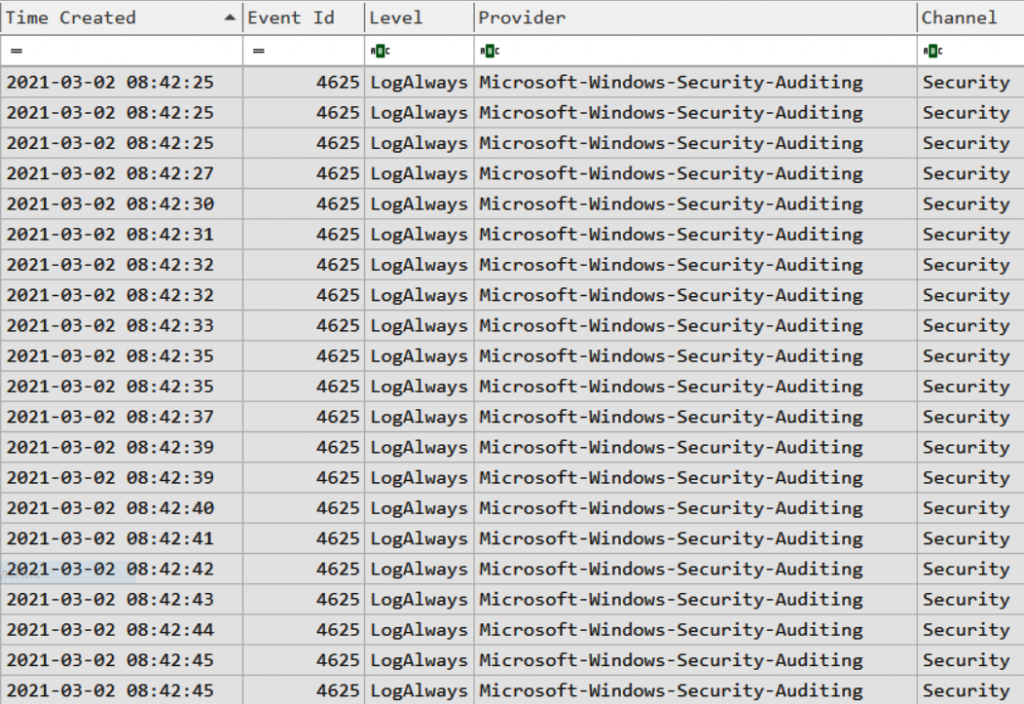
Figure 8.3 shows events with ID 4625 extracted using EvtxExplorer.
We obtained 196,378 events with ID 4625—this means the server was subjected to a brute-force password attack. But was the attack successful? To find out, we need to look at events with ID 4624 (Figure 8.4).
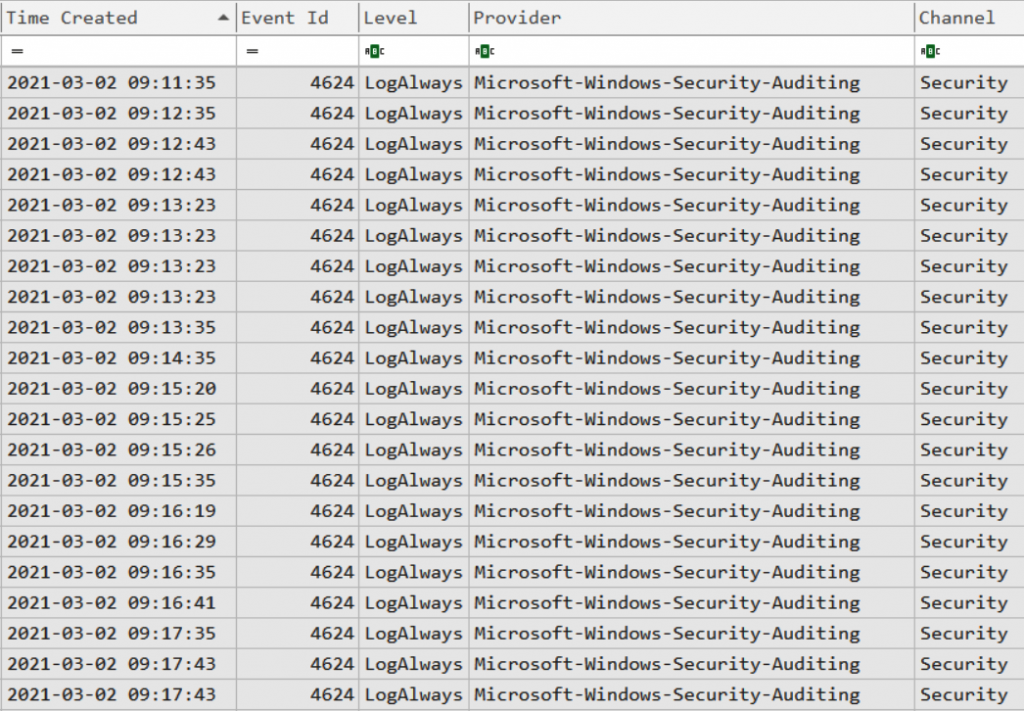
Figure 8.4 shows events with ID 4624 extracted using EvtxExplorer.
There are many such events, but we need to focus on two things: abnormal connection sources and logons to the system via RDP (type 10).
Filtering by type 10 leaves only two events. Both connections came from the same IP address—185.191.32.164. Let’s try to find out more information.

Figure 8.6 shows the startup interface of the Live Response Collection.
This time, we need to collect initial data from various evidence sources and dump volatile memory for analysis using the Volatility Framework.
The collected data is divided into two folders—ForensicImages and LiveResponseData. The memory image is located in the ForensicImages folder. Now we are ready to move into the analysis phase.
Investigating Phishing Attacks
To examine the memory image obtained through Live Response Collection, we will use Volatility 3. As we recall from Chapter 5, “Tactics, Techniques, and Procedures of Ransomware Gangs,” one of the most popular methods used by malware is process injection. Let’s start with the simplest approach by running the malfind plugin to analyze the memory image.
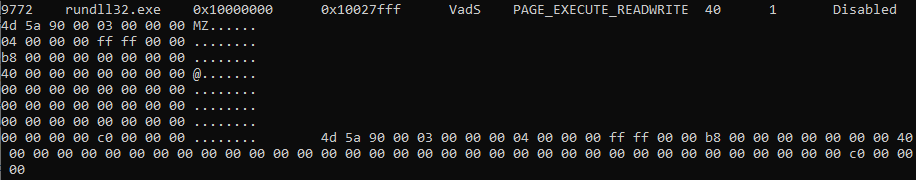
Figure 8.7 shows part of the output from malfind.
This plugin helps find hidden code, injected code, and code in the form of DLLs, making it very useful for detecting process injection.
Through malfind, we extracted some evidence, but the most interesting is the PID 9772 related to the process rundll32.exe. According to the output, this is likely code injection. Typically, IT experts and junior security analysts might overlook the legitimate file rundll32.exe, but it needs careful examination as it often becomes a target for attackers.
Let’s proceed by checking the process tree using the pstree plugin.
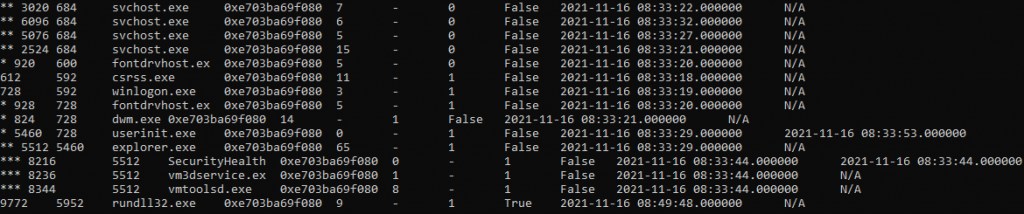
Figure 8.8 shows part of the results from pstree.
This plugin displays the running processes in a tree structure.
Now we have more information about the discussed process—it has a parent process with PID 5952. Unfortunately, there is no information about this PID process. But this is not a problem—let’s approach it from another angle. We can use the cmdline plugin to collect command line parameter information for each process.
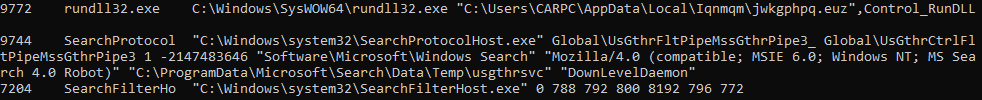
Figure 8.9 shows part of the output from cmdline.
As you can see, rundll32.exe is used to launch a file without an extension, with a randomly generated name—jwkgphpq.euz. This is very suspicious. Additionally, the file is located in a randomly named folder, another common characteristic of malicious activity.
Now we can almost confirm that rundll32.exe is used to launch a malicious file. Let’s try to find out if there are any suspicious network connections. To extract this information, we need the netscan plugin.
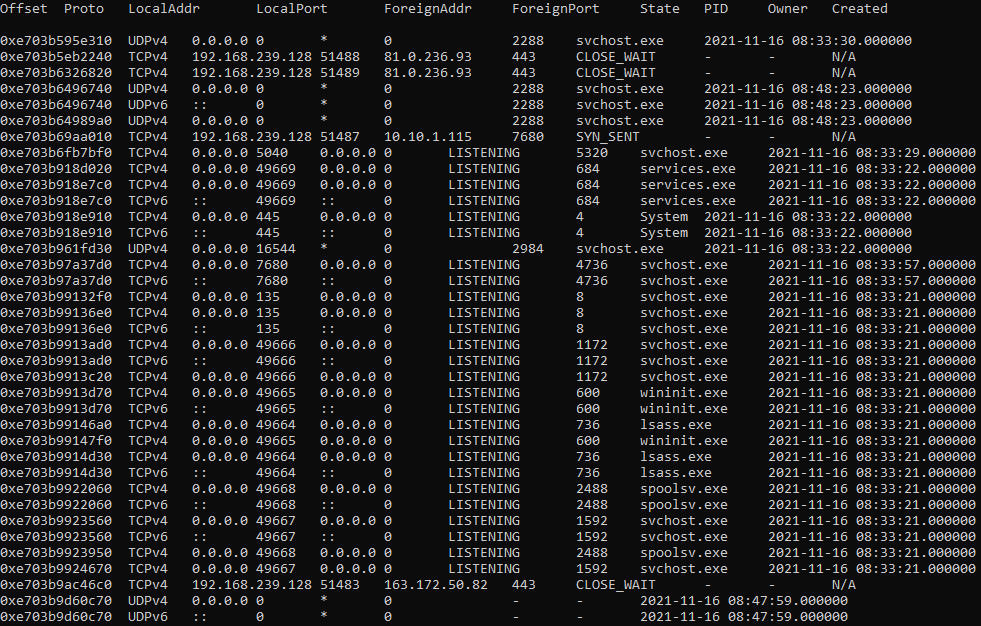
Figure 8.10 shows part of the output from netscan.
The first suspicious IP address is 81.0.236.93. Let’s use the Group-IB chart to gather more information about it.
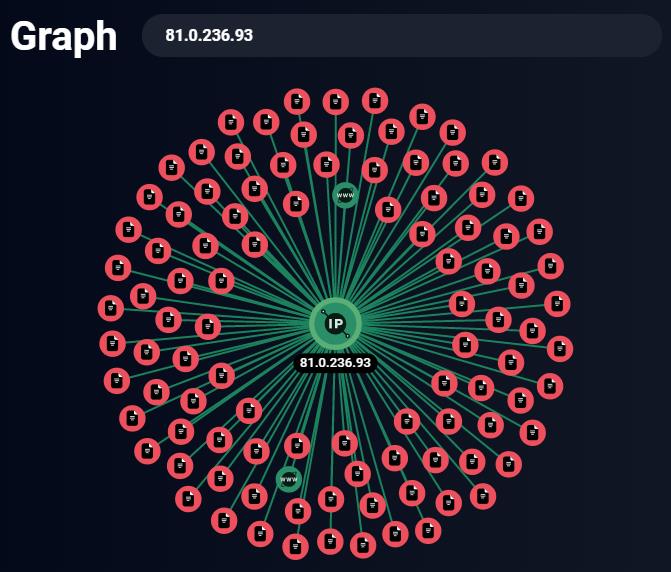
Figure 8.11 shows the suspicious IP address in the Group-IB chart.
As you can see, this IP address is associated with many malicious files. By clicking on one of the files, we can get more details. Being able to switch perspectives and correlate evidence is an important skill in investigating incidents.
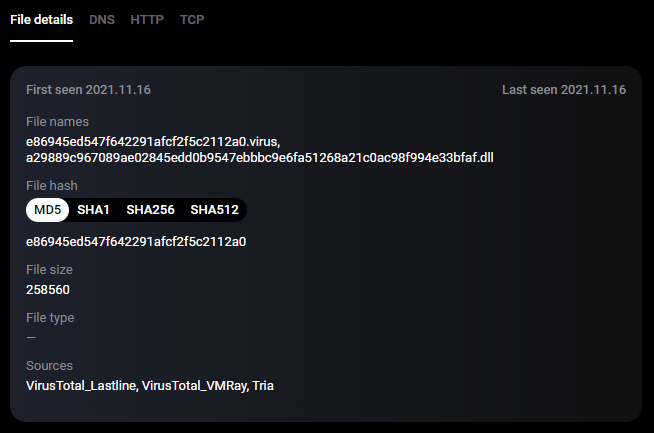
Figure 8.12 shows the malicious file information in the Group-IB chart.
We found a DLL file with a name very similar to the one we discovered earlier. This is likely similar malware.
Let’s dig deeper—using the analysis feature. Now we have not only a network indicator but also a hash value. Additionally, as you can see in Figure 8.12, the file is available on VirusTotal. Let’s find it using the obtained hash value (Figure 8.13).
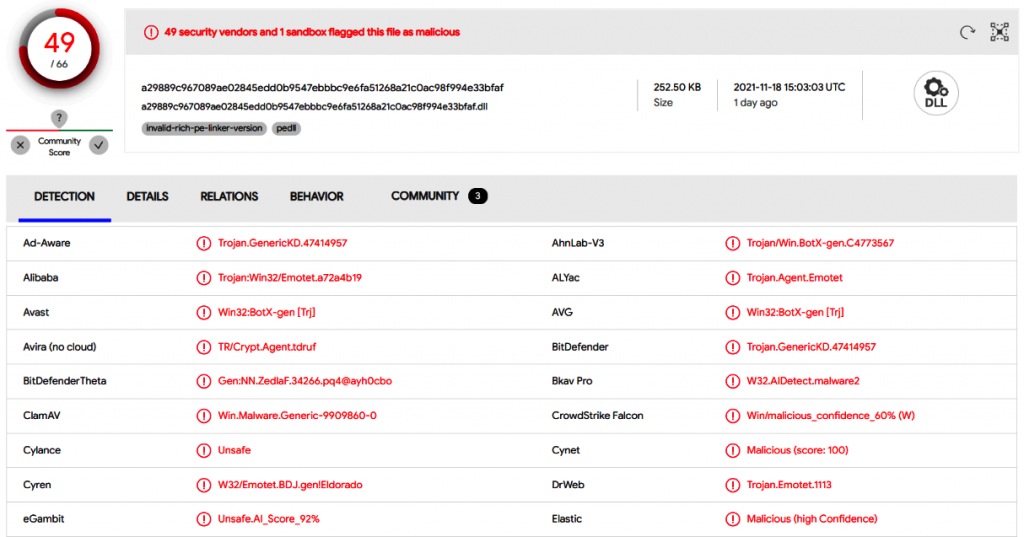
Figure 8.13 shows the malicious file information on VirusTotal.
It looks like Emotet. Despite its operators being arrested (see Chapter 1, “The History of Modern Ransomware Attacks”), in November 2021, Emotet’s infrastructure began to recover, and many companies faced its spam campaigns again.
Although we have identified the malware family, let’s go further. For example, try to extract more indicators from netscan. If you look at the output, you can notice another suspicious IP address—163.172.50.82. This address is also associated with several malicious files.
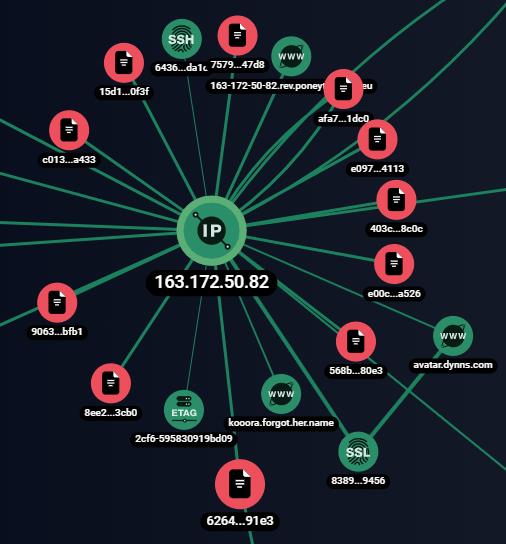
As shown in Figure 8.14.
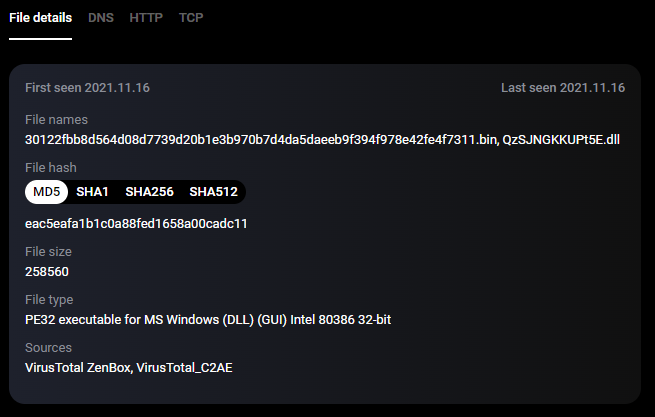
Let’s take a closer look at one of the files (Figure 8.15).
As you can see, the results are very similar to the previous one. Let’s use the hash value on VirusTotal again (Figure 8.16).
It’s Emotet again! Both IP addresses we obtained through memory forensics are associated with malicious activity.
Now let’s analyze non-volatile data. Live Response Collection not only provided us with the memory image but also gathered many evidence sources we discussed in the previous chapter, such as prefetch files.
We already know we are dealing with Emotet. This bot typically spreads through phishing emails with malicious attachments, such as Microsoft Word documents or Excel spreadsheets.
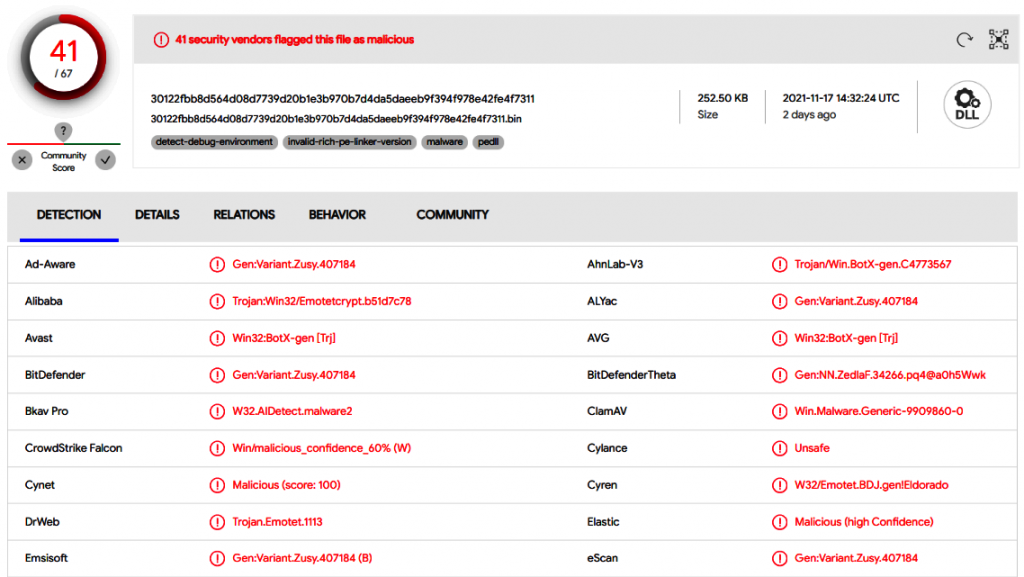
Figure 8.16 shows the malicious file information on VirusTotal.
If you look at the collected files, it’s easy to find the prefetch file for winword.exe. Let’s parse it using PECmd and check the referenced files within it.
Figure 8.17 shows part of the output from PECmd.
Very interesting—there is a suspicious DOCM file in the temporary folder used by Microsoft Outlook: the victim likely received it via email.
We also see the username CARPC, so now we can obtain the NTUSER.DAT registry file and use RegRipper to extract data related to this user.
First, analyzing the registry key that stores recently opened document information, we see the suspicious DOCM file was opened by the user on November 16, 2021, at 08:49:55 (UTC).
Another interesting finding is the jwkgphpq.euz value and its data in the Software\Microsoft\Windows\CurrentVersion\Run key.
Looks familiar, doesn’t it? This is the persistence mechanism used by Emotet!
Now let’s check the event logs. As we know, attackers often use PowerShell to download files from remote servers, so it’s essential to check the Windows PowerShell event logs when investigating phishing attacks.
Indeed, there is an interesting record in that log.
What does this mean? PowerShell was used to download a file from one of the seven URLs listed earlier. The program was saved to the C:\ProgramData folder and launched via rundll32.exe. More importantly, this event occurred after the suspicious DOCM file was opened.
To summarize: On November 16, 2021, at 08:49:55 (UTC), user CARPC opened a malicious document FILE_24561806179285605525.docm received via email. After opening the document and enabling protected content, PowerShell was launched to download and start Emotet from a remote server. The bot copied itself to C:\Users\CARPC\AppData\Local\Iqnmqm\jwkgphpq.euz and ensured persistence on the infected system by recording the path in Software\Microsoft\Windows\CurrentVersion\Run. The remote server IP addresses used for control and management were 81.0.236.93 and 163.172.50.82.
Conclusion
In this chapter, we discussed two very common initial access methods used by ransomware operators—attacking external remote access services and phishing.
As you can see, when reconstructing malicious behavior, you can rely on evidence from various sources—from volatile memory to Windows event logs. Additionally, we can use various data collection tools and filter the collected data. This is very important, especially when you need to collect and analyze data from multiple hosts simultaneously.
Of course, initial access is just the beginning of a ransomware attack, so incident response experts need to be able to discover many other pieces of evidence.
In the next chapter, we will focus on various post-exploitation activities, such as network reconnaissance and credential harvesting.


