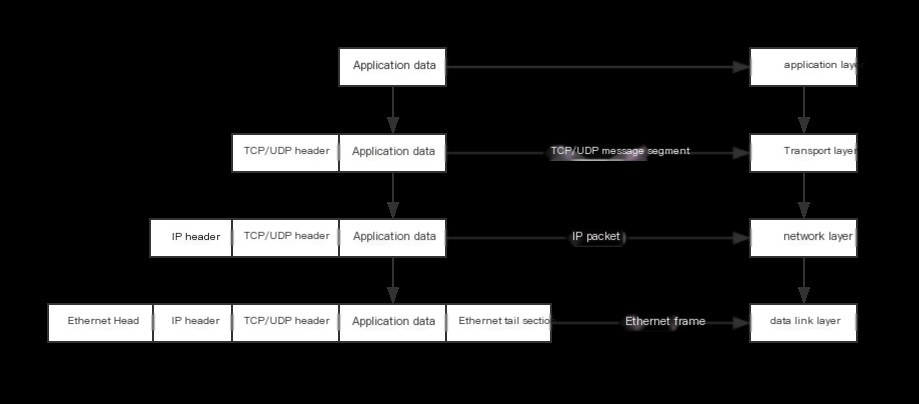
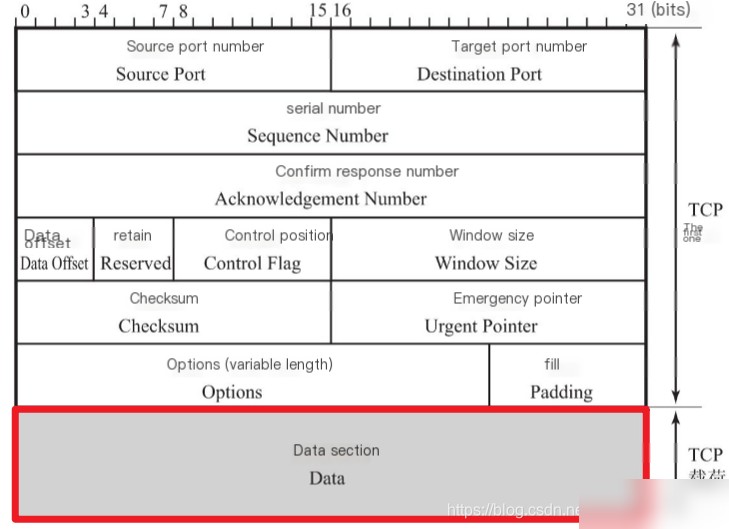
TCP Protocol
In the `snort` column, using [DVWA’s Reflected XSS Attack](https://blog.csdn.net/weixin_44288604/article/details/108624869) as an example, we can observe how protocol encapsulation plays a crucial role in the attack’s execution.
Problem Description
Reflected XSS uses the HTTP protocol and initiates attacks via the GET method. However, the protocol used in my snort rules is TCP. How does it detect HTTP? Here are the rule contents:
alert tcp anyany->anyany(msg:"DVWA-XSS_r vulnerability attack"; flow:to_server,established; uricontent:"DVWA-master/vulnerabilities/xss_r"; fast_pattern:only; uricontent:"name="; nocase; pcre:"/name[\s=]+?.+?(%3c|\x3c|<).+?(%3E|\x3E|>)/iU"; metadata:service http; sid:3; rev:1;)Some Thoughts
First, observe this packet. The main content of the attack is in the red part. Although using the “three-way handshake” or Wireshark’s TCP stream tracing can explain that the protocol used by snort should be TCP, it still feels forced. This is because TCP is a network layer protocol, and if analyzing packets, it should analyze the network layer and below, not the protocols above the network layer.
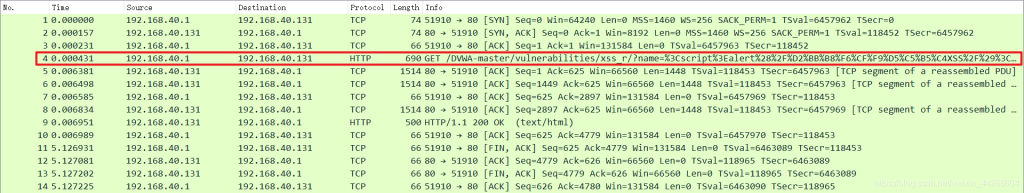
Correct Answer
1: It is incorrect to think that one should analyze the network layer and below. I came to this idea influenced by the red boxed part of Wireshark, assuming that if analyzing the network layer, one should be able to analyze the protocols of the network layer and data link layer.
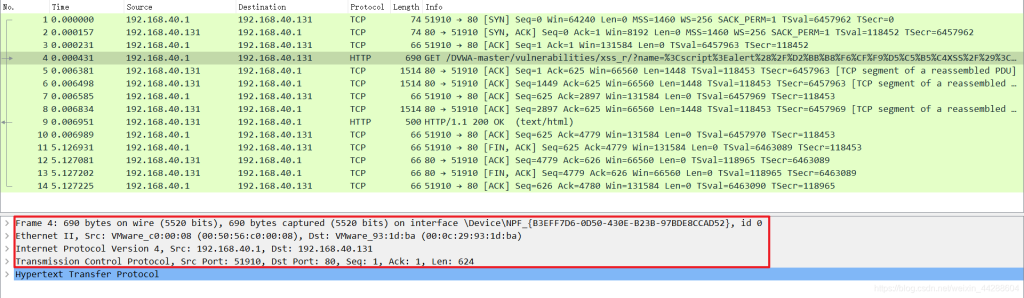
2: Snort can analyze the HTTP protocol using TCP because of protocol encapsulation. When a packet passes through a layer, it adds another layer. The content of the application layer is the data part of TCP, so analyzing the TCP protocol allows us to see the content of the TCP data part—HTTP.