MUI Cache for Multi-User Interface
MUI stands for Multi-Language User Interface. It is a technology that allows Windows systems to localize a single application into multiple languages. Developers create a .MUI file for each language supported by the application, enabling users to switch languages. MUI files generate MUICache keys in the registry. The MUICache key contains information about files executed on the system, which the operating system retrieves when using new applications.
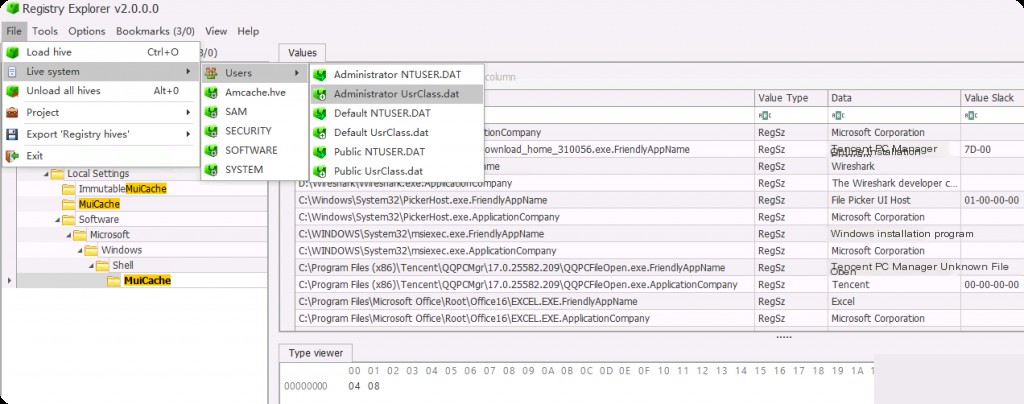
MUICache is located in the USRCLASS.dat hive, and it is unique to each user on the system. The path to this artifact is:
Local Settings\Software\Microsoft\Windows\Shell\MuiCache
MUICache retains 2 records for each executed .exe file, one containing the application company name data and the other containing the application name data (i.e., the original .exe file name).
MUICache can provide useful information about applications and tools installed and run through user accounts, and it can also indicate malicious activity on the system; because even if an attacker has deleted the application from the device, the information in the MUICache key will remain. Additionally, if the application’s value has been deleted from the key, it will reappear the next time the user runs that application.
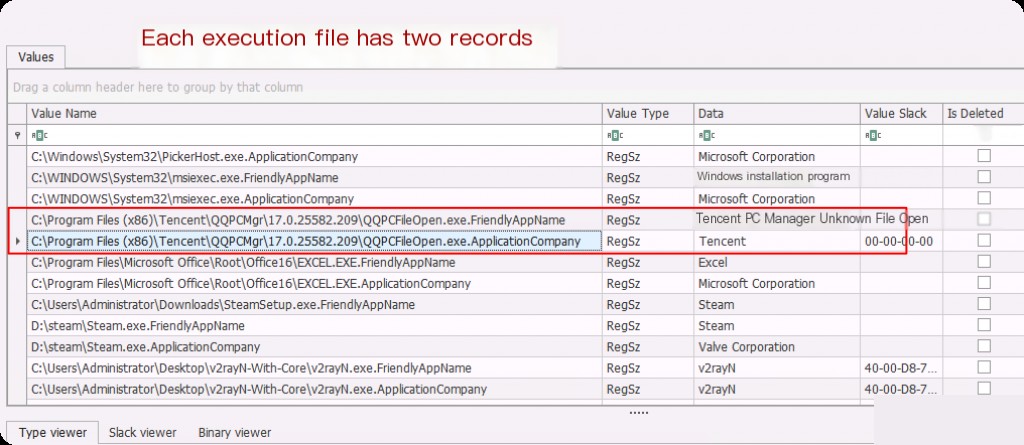
Here, “Tencent Computer Manager” is the program’s name, while “Tencent” is the company’s name.
Besides using the registry browser, NirSoft’s ” muicache_view ” is another tool that automatically displays MUICache entries.
Note: The muicache_view tool only runs on live systems, meaning it automatically retrieves muicache from the registry hive of the running system.
https://www.nirsoft.net/utils/muicache_view.html
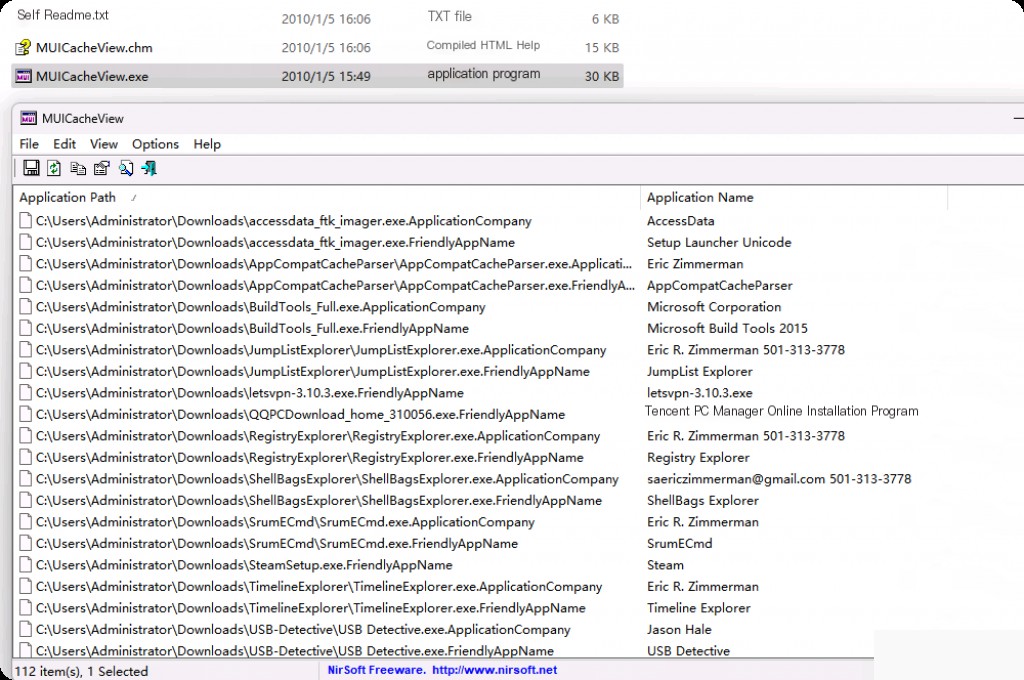
Open and run the tool, and it will display all entries in the live system.
Another important feature of MUICache is that it shows the original application name and the original company name that created the executable file. Even if we rename the application on the system and then open the MUICache data, it will still show the corresponding original application name.
Typically, attackers like to rename malicious tools to less suspicious names, for example, they might rename the sharphound tool to “WindowsCleaner,” but the MUICache artifact will have a data column showing the original exe file name.
UserAssist
UserAssist is a key in the registry that contains records of programs frequently executed by the user. Values such as file name, last execution time, and execution count can be found in the UserAssist key. Every GUI-based program launched from the desktop is recorded in this registry key.
C:\Users\Administrator\ntuser.dat: Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{GUID}\Count
The key contains two GUID subkeys, one starting with the value CEBFF5CD containing executable file execution records, and the other starting with the value F4E57C4B containing shortcut file or lnk file execution records.
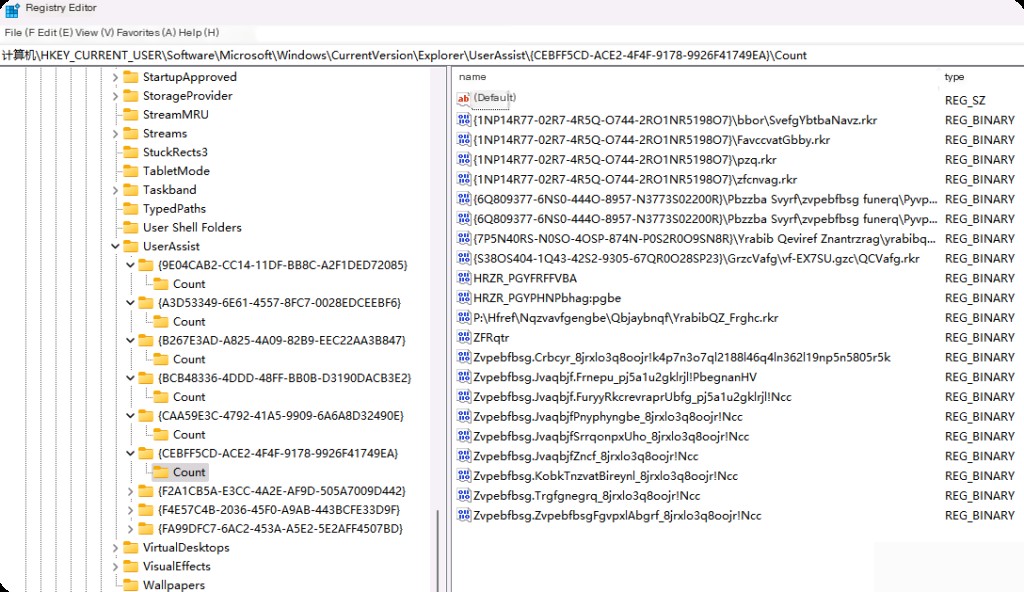
Note that the key value data is rot13 encoded, so we cannot read the key values directly. Records with the .rkr extension are exe records, so if we perform rot13 on exe, we get rkr. Similarly, records with the .yax extension are lnk records.
These records are for .exe files and are rot13 encoded. You can use any online rot13 decoder to decode them.
https://cryptii.com/pipes/rot13-decoder
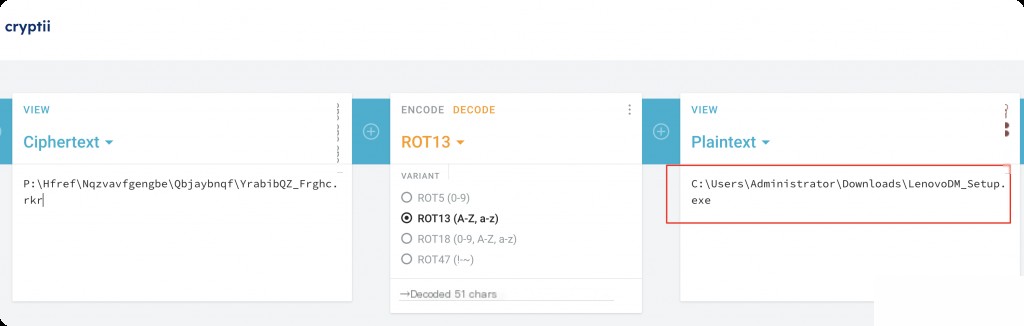
Using the key in the screenshot above as an example, after decoding, you can see the correct file path.
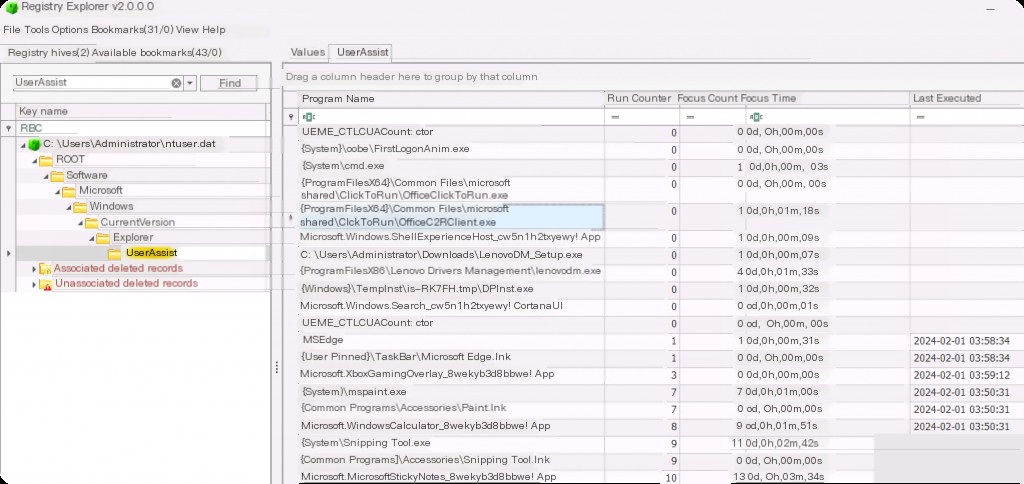
However, here you can see the correct file path, as Registry Explorer 2.0.0.0 automatically decodes it. It also shows the last execution timestamp of the file, the number of times the file was run, and the focus time, indicating the length of time the file was used.
Windows TypedPaths and Search Keywords
We can identify recent activities of a user account by analyzing TypedPaths and search keywords. This tool is very useful during forensic investigations as it can reveal the attacker’s intentions since they might use it to search for options to find target information.
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQuery
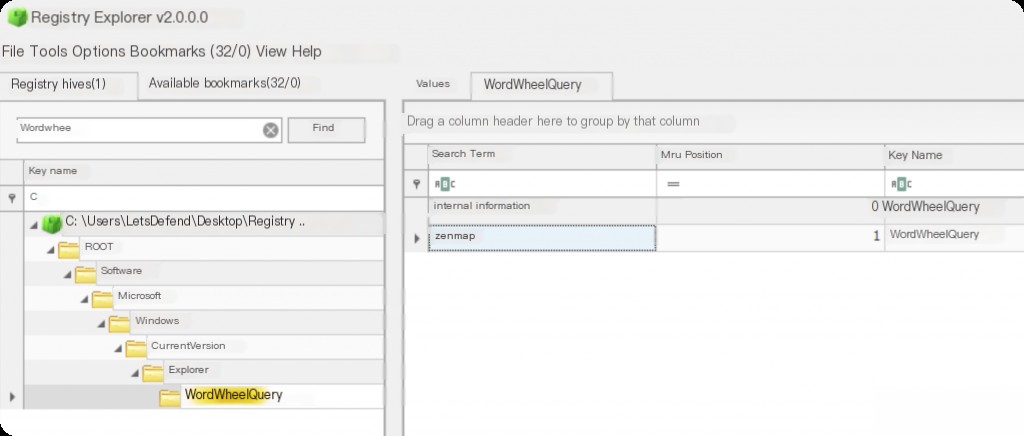
Search keywords are very useful during forensic processes, as attackers who are not very tech-savvy might use File Explorer search options to find information to exfiltrate rather than using complex custom scripts.
However, in my tests, I did not find this key in the registry of newer operating systems.
Another artifact related to File Explorer is Windows TypedPaths. In File Explorer, we can see an address bar that contains the path to the directory we are in. For example, if I go to the Program Files folder, we can see the full path to the current folder.
We can place any local folder path in the address bar, even network share/UNC paths for navigation. These artifacts are called “typed paths” because the registry key storing this information is named “typed paths.”
C:\Users\Administrator\ntuser.dat: Software\Microsoft\Windows\CurrentVersion\Explorer\TypedPaths
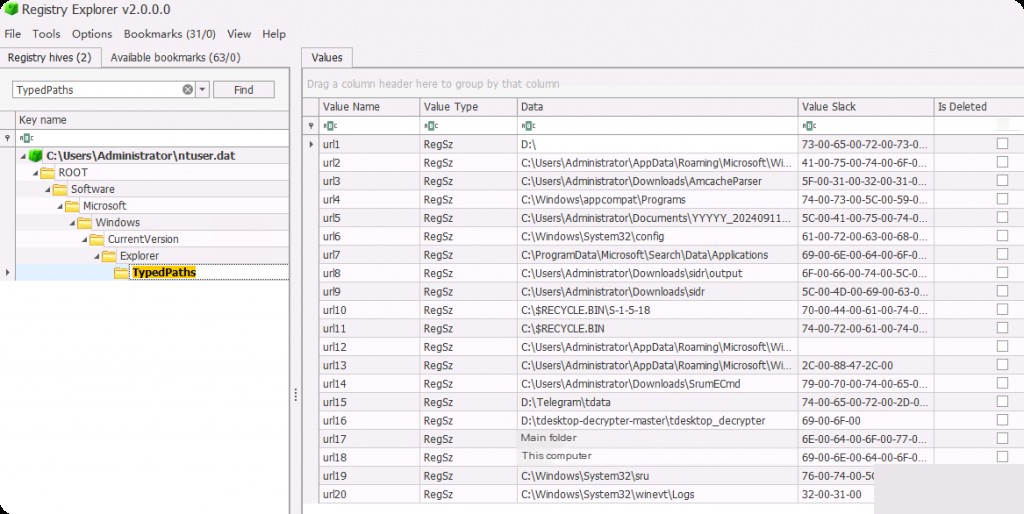
The registry key stores records of the last 25 typed paths, and once this number is exceeded, it starts overwriting the oldest values.
Internet Explorer History
Internet Explorer was discontinued on June 14, 2022. This means the product is no longer recommended for use and has effectively been replaced by Microsoft Edge. Although it may now be outdated, it is still necessary to know about it. It may still come in handy during forensic investigations because we cannot know if an attacker might use it.
Any URLs and websites browsed through Internet Explorer are stored in a registry key named ” typedpaths “.
NTUSER.dat\Software\Microsoft\Internet Explorer\TypedURLs
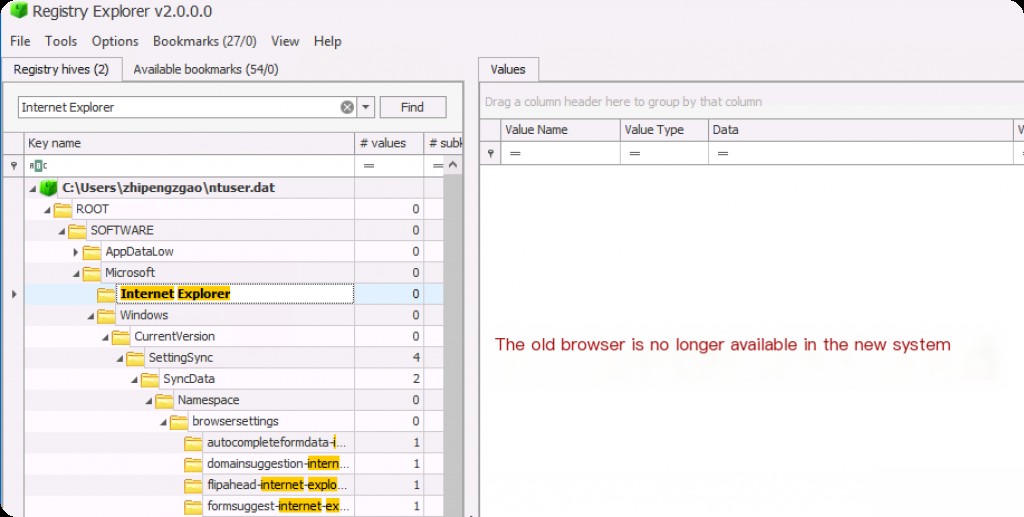
Although the key still exists, since IE is no longer available, it will not record corresponding access records.


