The maintenance records of Jumplists are considered an important source of evidential information during investigations. Analyzing Jumplist files can provide valuable information about a user’s historical activities on the system, such as file creation, access, and modification. Forensic experts can use the data extracted from Jumplist files to construct a timeline of user activities.
Jumplists
The Jumplist feature was first introduced in Windows 7 and continues to be used in higher versions of Windows, including Windows 11. This feature is designed to provide users with quick access to recently accessed application files and common tasks. This information remains on the system even long after the source files and applications are no longer present.
Types of Jumplists
There are two types of Jumplists in Windows:
- Automatic Destinations
- Custom Destinations
Each file consists of a 16-digit hexadecimal number, which is the AppID (Application Identifier), followed by the extension automaticDestinations-ms or customDestinations-ms. It is important to note that these files are hidden and will not be displayed even when hidden items are enabled in Windows Explorer. They can be viewed by entering the full path in the Windows Explorer address bar.
Automatic Destinations
Automatic destination Jumplist files are located in the following directory:
C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations
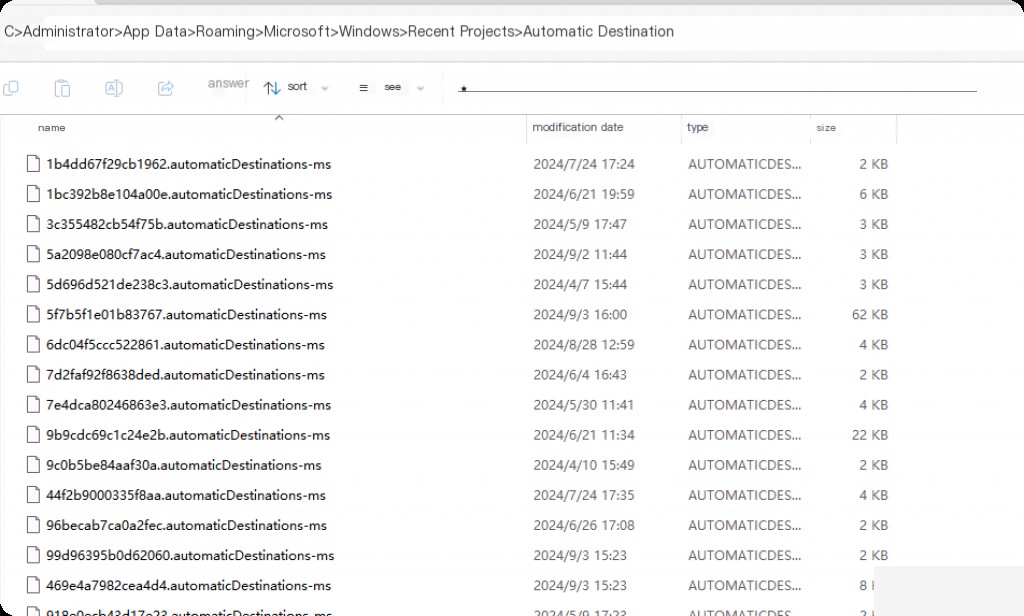
These Jumplist files are automatically created when a user opens a file or application. These files are in the Microsoft Compound File Binary (CFB) format, also known as OLE (Object Linking and Embedding) files. They contain individually hex-numbered SHLLINK streams and DestList streams.
Custom Destinations
CustomDestinations Jumplist files are located in the following directory:
C:\%UserProfile%\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations
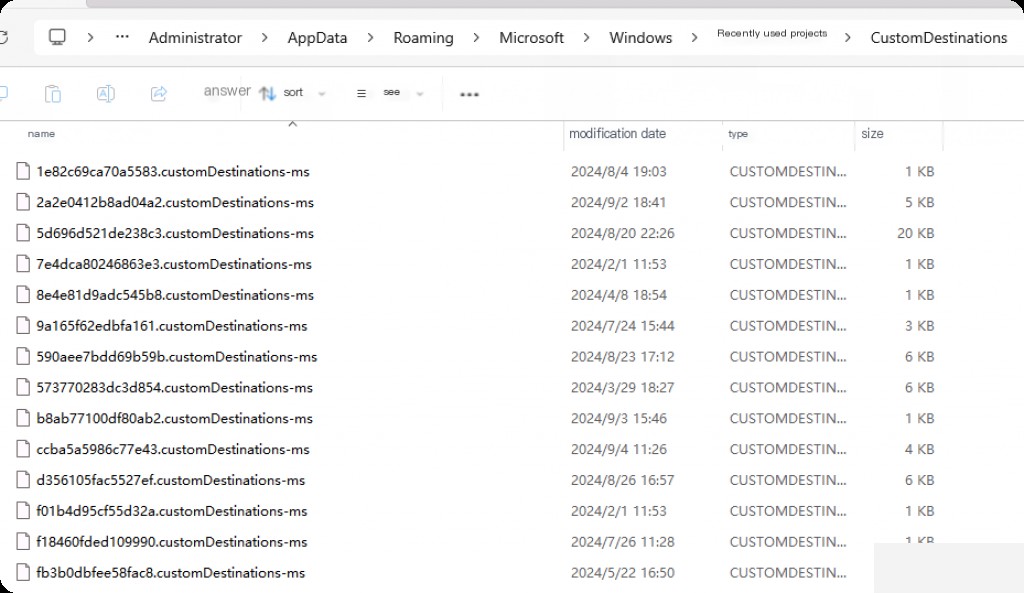
These are custom Jumplists created when a user pins a file or application to the taskbar or start menu. The structure of these files differs from AutomaticDestinations Jumplist files; it follows the sequential MS-SHLLINK binary format structure.
Jumplists provide information on recently accessed files and applications, recently accessed URLs from browsers, recently accessed documents, PDFs, ZIP files, and various settings information. Detailed analysis of these files can give us a good understanding of various activities on the terminal.
Download JumpList Explorer
We will use Eric Zimmerman’s Jumplist Explorer tool to analyze Jumplists.
Load and Analyze Jumplist Files
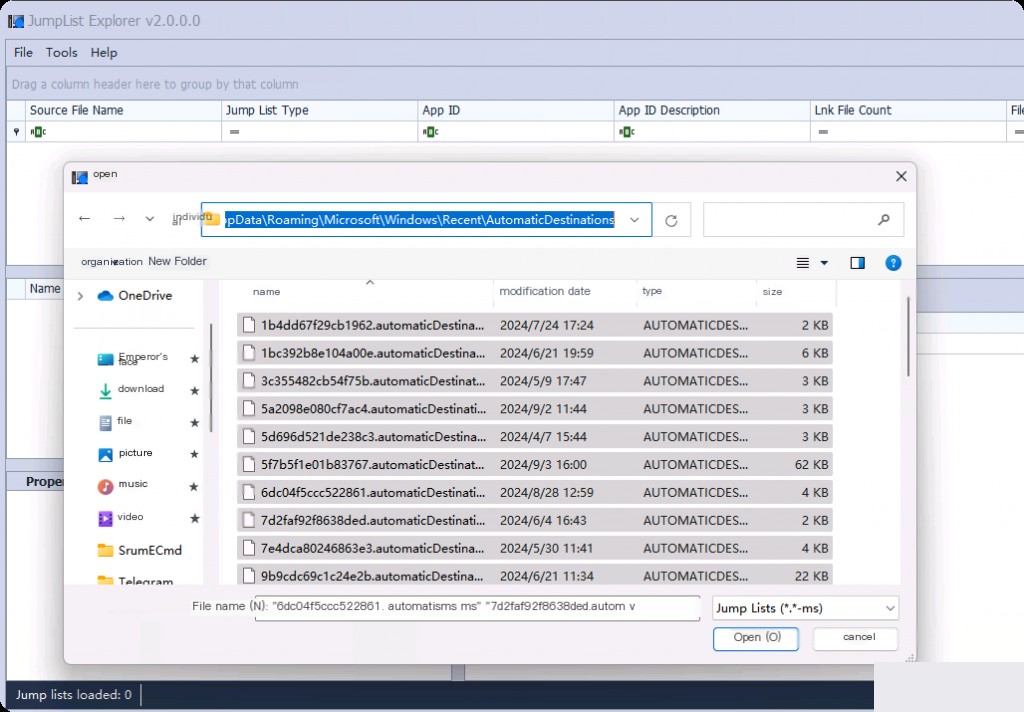
We can see the Jumplist files as these files are acquired and categorized. These are hidden in a live system. Select all these files under Automatic Destinations. Then do the same for Custom Destinations.
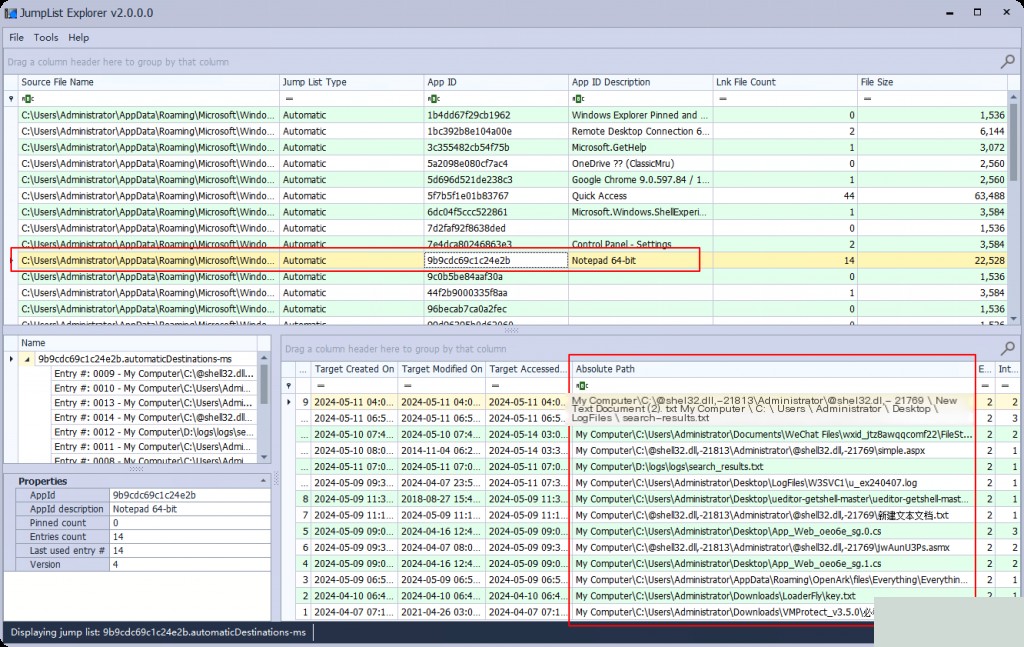
Suppose we want to find out which files were opened using Notepad. We go to the Notepad Jumplist, and we see the files accessed using Notepad.
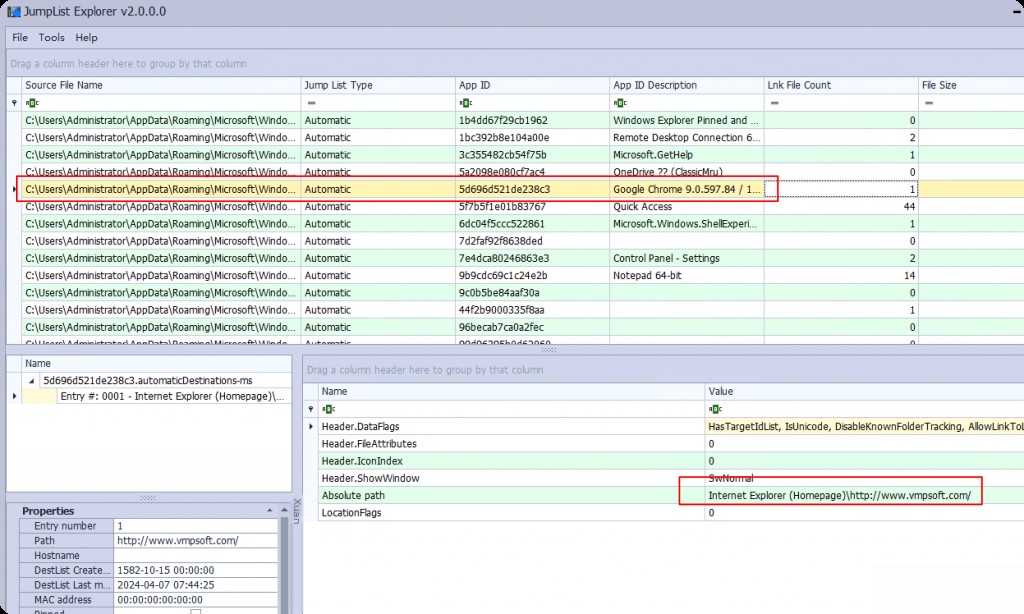
If we’re lucky, sometimes we can get pinned URLs from the browser or the most frequently visited URLs from the browser.
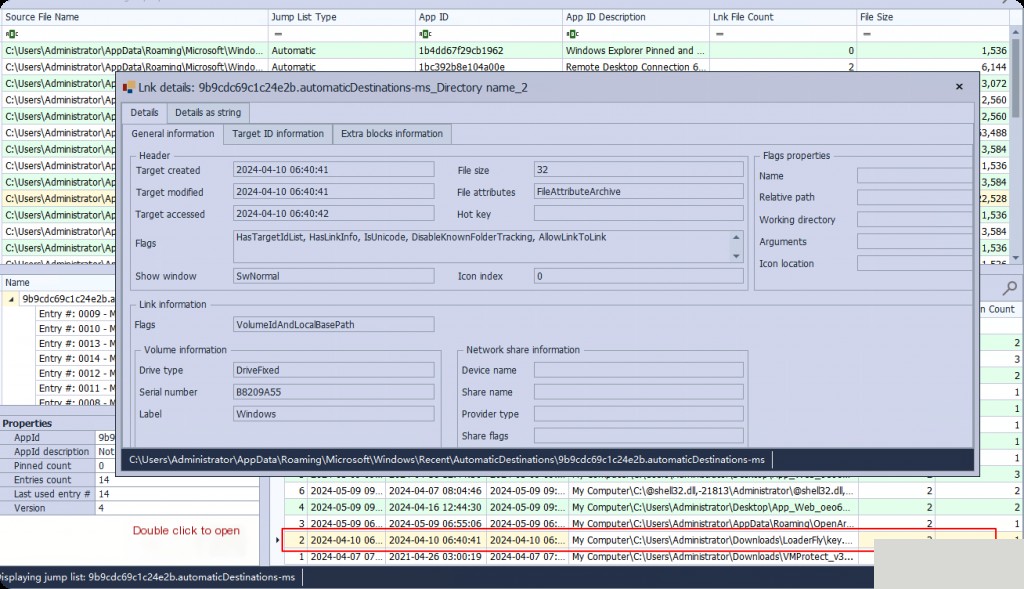
Most importantly, we can also use Jumplists to find folder access like shellbags. This can be done through the Jumplist files of the Windows Explorer program. We get all the folders accessed through File Explorer, their creation time, access time, and the number of times they were accessed/interacted with.


