I. ICMP Protocol Introduction
ICMP (Internet Control Message Protocol) is a connectionless and unreliable protocol at the network layer that transmits ICMP messages such as datagram error messages, network status information, and host status information.
1. ICMP Data Encapsulation
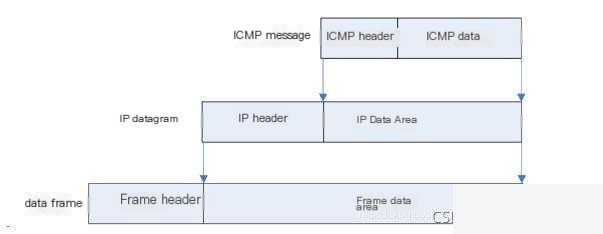
ICMP messages are encapsulated and sent using IP datagrams. IP datagrams carrying ICMP messages are forwarded in the network just like any other type of data, without additional reliability or priority. Since IP datagrams themselves are placed in lower-layer physical data frames for transmission, ICMP messages themselves can also be lost or contain transmission errors.
2. Types of ICMP Messages
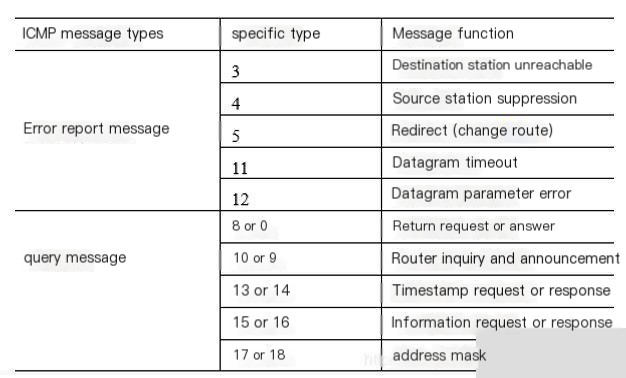
ICMP messages can be divided into two categories: ICMP error-reporting messages and ICMP query messages. Error-reporting messages are mainly used to return error report information to the source host of an IP datagram, while query messages are used by one host to request specific information from another host. Typically, query messages appear in pairs; a source host sends a query message, and upon receipt by the destination host, it returns a response message to the source host in the format agreed upon in the query message.
Note that ICMP error messages cannot correct errors; they only report errors.
II. Using Snort Rules to Detect Ping Unreachable Events
The ping command uses the ICMP protocol, and we now need to create Snort rules to alert when a ping unreachable event occurs. The specific Snort rule is as follows:
include classification.config
alert icmp any any -> any any (msg:"ICMP Destination Unreachable."; itype:3; icode:1; sid:48511; rev:4;)1. classification.config is in the Snort configuration file, as shown below:
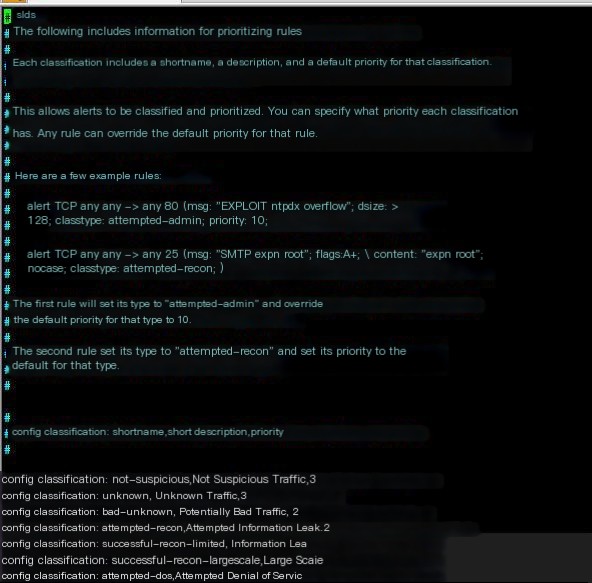
2. itype indicates ICMP type, showing Destination Unreachable.
3. icode is the ICMP related code, indicating Host Unreachable.
4. Use the command to capture packets:
ping 10.20.92.173 # Unreachable ping
tcpdump -i ens192 -w ping.pcap # Capture packets from network card ens192 and save to ping.pcap file5. Visible with Wireshark:
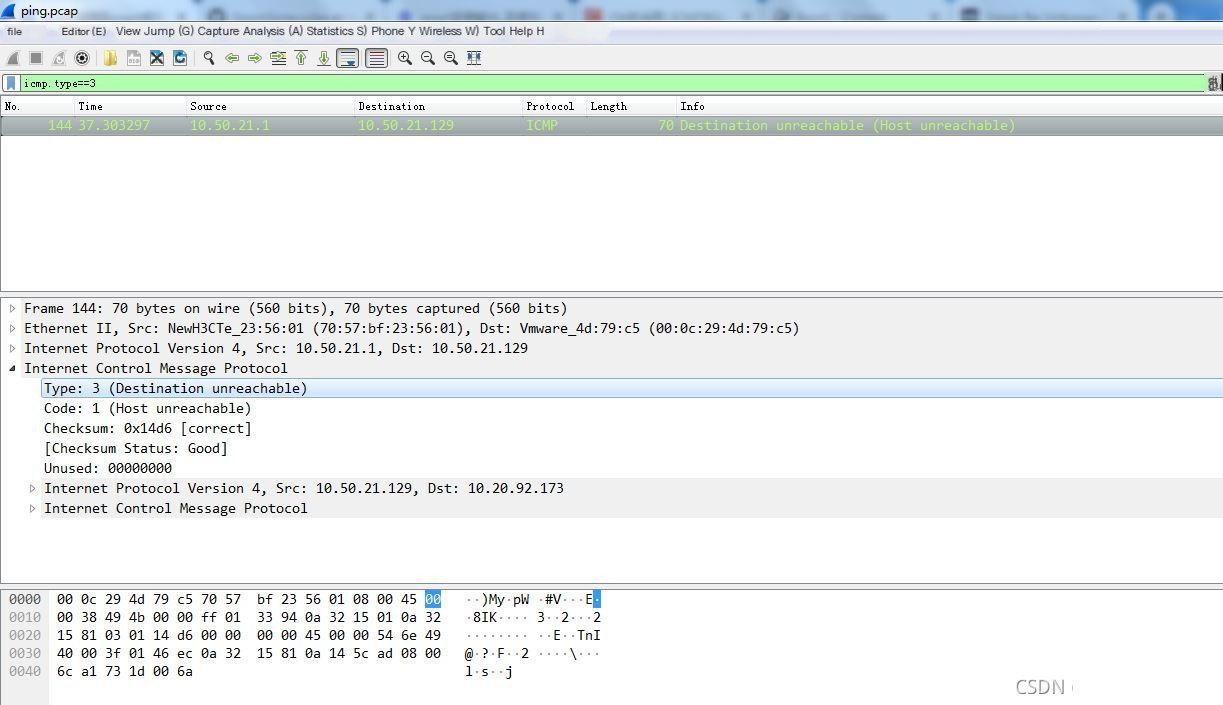
Where type corresponds to itype, and code corresponds to icode.
6. Run the command:
snort -A console -c snort1.conf -i ens192 # Start Snort
tcpreplay -i ens192 -M 10 ping.pcap # Packet replay testSnort alert is as follows:
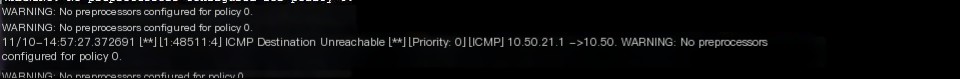
III. Adding ICMP Snort Rules
include classification.config
ipvar EXTERNAL_NET any
ipvar HOME_NET any
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP ISS Pinger"; itype:8; content:"ISSPNGRQ"; depth:32; reference:arachnids,158; classtype:attempted-recon; sid:465; rev:3;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP L3retriever Ping"; icode:0; itype:8; content:"ABCDEFGHIJKLMNOPQRSTUVWABCDEFGHI"; depth:32; reference:arachnids,311; classtype:attempted-recon; sid:466; rev:4;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP Nemesis v1.1 Echo"; dsize:20; icmp_id:0; icmp_seq:0; itype:8; content:"|00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00|"; reference:arachnids,449; classtype:attempted-recon; sid:467; rev:3;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP PING NMAP"; dsize:0; itype:8; reference:arachnids,162; classtype:attempted-recon; sid:469; rev:3;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP icmpenum v1.1.1"; dsize:0; icmp_id:666 ; icmp_seq:0; id:666; itype:8; reference:arachnids,450; classtype:attempted-recon; sid:471; rev:3;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP redirect host"; icode:1; itype:5; reference:arachnids,135; reference:cve,1999-0265; classtype:bad-unknown; sid:472; rev:4;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP redirect net"; icode:0; itype:5; reference:arachnids,199; reference:cve,1999-0265; classtype:bad-unknown; sid:473; rev:4;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP superscan echo"; dsize:8; itype:8; content:"|00 00 00 00 00 00 00 00|"; classtype:attempted-recon; sid:474; rev:4;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP traceroute ipopts"; ipopts:rr; itype:0; reference:arachnids,238; classtype:attempted-recon; sid:475; rev:3;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP webtrends scanner"; icode:0; itype:8; content:"|00 00 00 00|EEEEEEEEEEEE"; reference:arachnids,307; classtype:attempted-recon; sid:476; rev:4;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP Source Quench"; icode:0; itype:4; classtype:bad-unknown; sid:477; rev:2;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP Broadscan Smurf Scanner"; dsize:4; icmp_id:0; icmp_seq:0; itype:8; classtype:attempted-recon; sid:478; rev:3;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP PING speedera"; itype:8; content:"89|3A 3B|<=>?"; depth:100; classtype:misc-activity; sid:480; rev:5;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP TJPingPro1.1Build 2 Windows"; itype:8; content:"TJPingPro by Jim"; depth:32; reference:arachnids,167; classtype:misc-activity; sid:481; rev:5;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP PING WhatsupGold Windows"; itype:8; content:"WhatsUp - A Netw"; depth:32; reference:arachnids,168; classtype:misc-activity; sid:482; rev:5;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP PING CyberKit 2.2 Windows"; itype:8; content:"|AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA AA|"; depth:32; reference:arachnids,154; classtype:misc-activity; sid:483; rev:5;)
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"ICMP PING Sniffer Pro/NetXRay network scan"; itype:8; content:"Cinco Network, Inc."; depth:32; classtype:misc-activity; sid:484; rev:4;)
alert icmp any any -> any any (msg:"ICMP Destination Unreachable Communication Administratively Prohibited"; icode:13; itype:3; classtype:misc-activity; sid:485; rev:4;)
alert icmp any any -> any any (msg

