Author: sarleon Source: freebuf.comRewritten content: HTTPS authentication is a vital process that ensures secure communication over the internet by encrypting data between the client and server. It helps protect sensitive information from being intercepted by malicious parties. Implementing HTTPS authentication is crucial for maintaining privacy and data integrity.
01 Principle
The DNS determines which IP address our domain name will resolve to; it is an application layer protocol based on the UDP protocol.
The prerequisite for this attack is that the attacker controls your gateway (which can be a router, switch, or ISP). Generally speaking, within a WLAN, using ARP spoofing can achieve this effect.
When visiting a website, you go through several stages: For instance, accessing the homepage of freebuf:
1. Enter freebuf.com in the address bar
2. Access the local hosts file to find the IP corresponding to freebuf.com; if found, access that IP
3. If not found, proceed to this step, query the (remote) DNS server for freebuf.com’s IP, and access that IP
You can use Wireshark to capture packets to observe this process
This is a DNS request sent to baidu.com
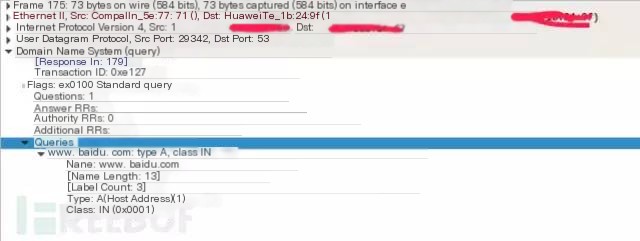 >
>
This is the response from the DNS server:
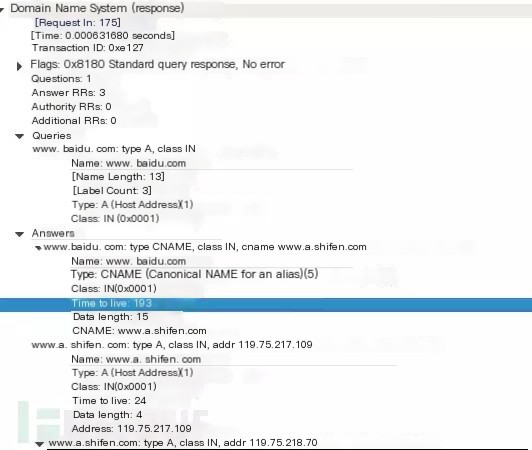 >
>
Man-in-the-middle hijacking occurs in step three: Because the attacker controls your gateway, when you send a request to find the IP for freebuf.com, the man-in-the-middle intercepts it and returns a malicious website’s IP to you. Your browser will treat this IP as the IP of the domain you intended to access! This IP is set up by the attacker and mimics the target site’s frontend interface. When you enter your username, password, or perform a payment on this interface, you fall into the trap.
Due to DNS hijacking, the URL of the redirected page is entirely correct, making this type of attack usually extremely hard to detect!
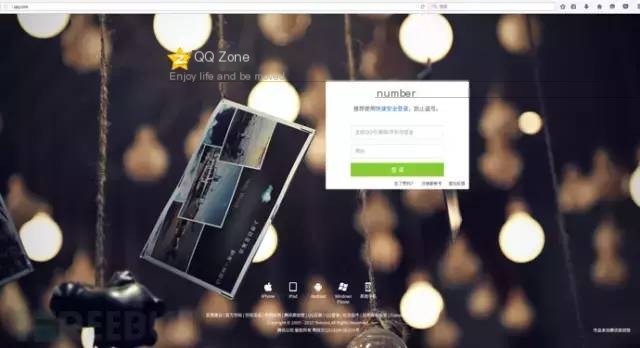
Attackers can create a highly polished frontend of the webpage! Nearly identical to the original page, with various links pointing to the correct places, except the login form is problematic. Once you enter a username and password, it will be captured by the attacker.
02 Prevention
Generally speaking, preventing such attacks is very challenging! Both the URL and the page are normal, and unless you have a deep understanding of web technology, there’s no way to start (if the attacker’s page reproduction is realistic enough). However, we still have some methods to guard against it:
1. Use SSL (HTTPS) for logins. Attackers can obtain the public key but not the server’s private key.
2. Be extremely cautious when the browser warns about certificate issues! Confirm that your network environment is secure and the website is trustworthy before proceeding.
3. Avoid logging in when connected to public Wi-Fi.
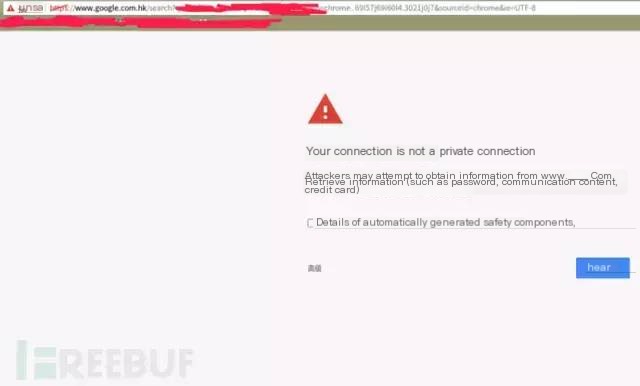
If you see a warning like the one above, there are two possibilities:
One is that the server’s HTTPS certificate is not configured correctly,
The other is that you may have encountered a man-in-the-middle attack, and the digital certificate cannot pass the browser’s verification.
Normally, only some corporate and school intranets, some personal sites, and (12306) would encounter certificate configuration issues. Other normal large websites, especially those we frequently use, would not have such problems. These are precisely the sites that require logins and often face phishing attacks. Therefore, if you encounter such a situation, never casually fill in your username and password.
The impact range of this type of attack is generally very small, limited to an intranet. Overall, there’s no need to worry excessively. However, if it’s an ISP hijacking, that’s a different story. Though ISP hijacking usually just inserts ads, it won’t boldly use this method for phishing attacks.
03 Attacker’s Objective
Phishing Attack to Steal Passwords
Inducing users to fill in login forms and changing POST addresses to their server addresses to acquire victim usernames and passwords. Special Note: There is a situation where after a user fills in the form, they hesitate and do not click the submit/login button; however, at this point, the inputted content has already been sent out via AJAX.
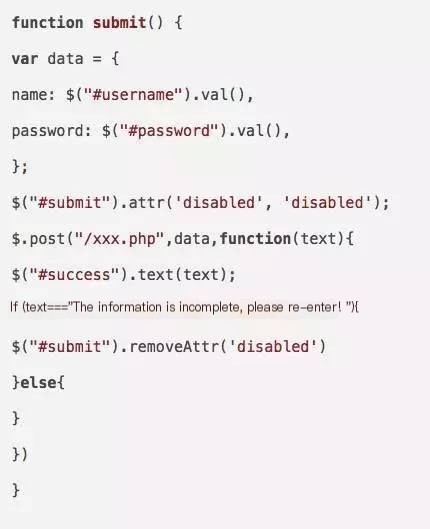
Generally, such a submit function is executed after the button is clicked, but an attacker can use the on-event to execute this function after every user input action, allowing sending without clicking.
Phishing Attack to Hijack Payments
Hijacking on the payment interface to redirect Alipay or bank card payments to the attacker’s account.
Ad Injection
This method of DNS hijacking is usually done by ISPs, involving large-scale hijacking.
(Like in the bottom right of the picture above, this is similar to ISP ad hijacking; of course, this might be the site’s own ad, couldn’t find a picture of ISP hijacking, so using this for demonstration)
There are two methods:
HTTP Hijacking
Insert a div with a fixed position, usually in the bottom right corner, to display ads in the intercepted HTML text.
DNS Hijacking
Hijack the domain name to a site owned by the attacker containing ads, and then use an iframe to introduce the site the user wants to visit.
04 Attack Reproduction
We can reproduce this attack method. On multiple machines under a single router, use one to perform the hijacking and another to simulate the victim for testing.
Preparation
Hijacking machine: Preferably use Kali LinuxSet up an HTTP server locally or remotely as a phishing site to mimic the target website.Preferably install a high-power wireless card.Install the hijacking tool ettercap (comes with Kali)The test machine should have a browser installed (obviously, if it’s a computer, it would have one; purely command-line Linux can use lynx).Connect both computers to the same wireless router or hub (preferably not a switch, as you need control of the switch itself for hijacking, whereas with a router, you just need to spoof).
Operation Guide
First, configure the DNS you want to hijack in the ettercap configuration file. The location of the ettercap DNS configuration file is /etc/ettercap/etter.dns. Opening this file, we can see some examples already built-in by the author.
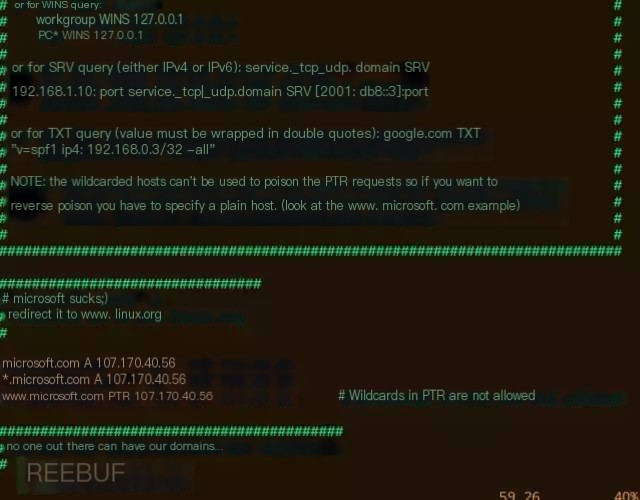
The author playfully resolved Microsoft’s homepage microsoft.com to linux.org‘s IP, hail open-source! Linux is supreme! Back to the point, we can refer to these examples to write our own hijacking rules. The format is domain DNS record type IP. What is a DNS record type?
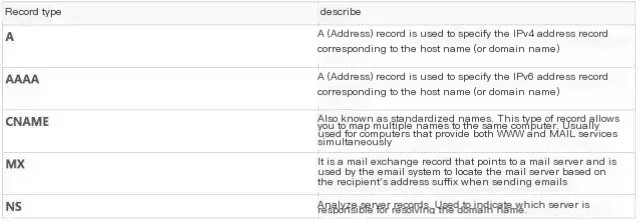
For more detailed descriptions, refer to Wikipedia’s DNS resolution records.
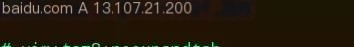
Generally, when performing DNS hijacking, we use an A record. For example, if we want to hijack Baidu to Bing (considering some friends don’t have a VPN), first use ping/traceroute/whois to get Bing.com’s IP 13.107.21.200.
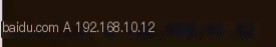
We then add a hijacking rule in this file.
When performing DNS hijacking, we need to hijack it to our own HTTP server. Use ifconfig (*nix) or ipconfig (Windows) to view the machine’s IP address, generally a local area network address 192.168.xxx.xxx, 10.xxx.xxx.xxx, 172.xxx.xxx.xxx.
The next step is to use a web server like Apache or nginx to set up our own server, using lamp is also fine, and there are plenty of tutorials online, will not elaborate here.
Next, open ettercap.

First select sniff->unified sniff Then open hosts->host list Select all the hosts, click add to target 1.
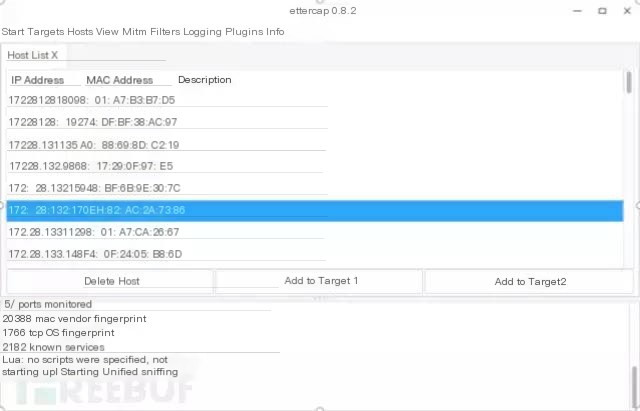
Then click Mitm->ARP Posining
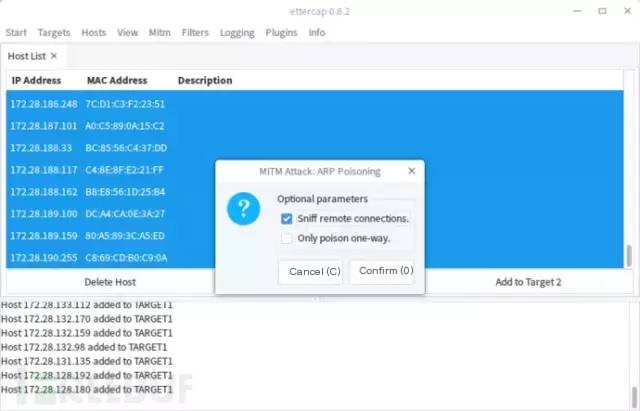
Select the first checkbox sniff remote connections
Then in plugin->manage plugins double-click dns spoof to activate the plugin.
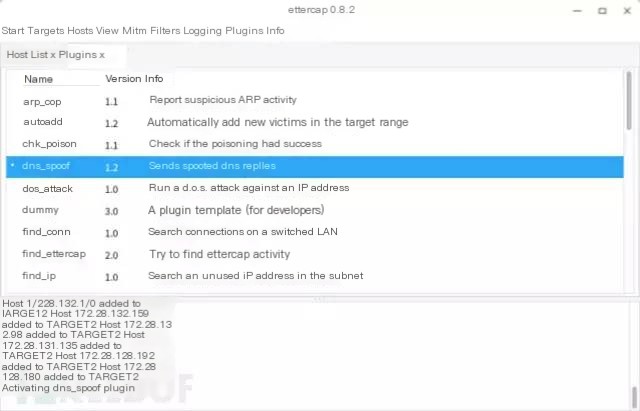
At this point, the target is now in a hijacked state. Use the test machine’s browser to visit the site you hijacked, and you will see your own server’s page. I haven’t made changes here; it’s Apache’s default page.
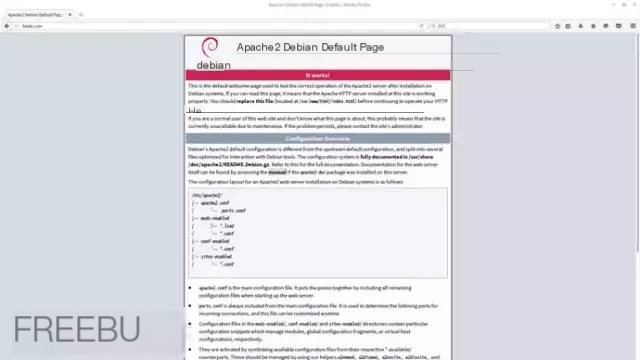
Of course, this attack has a considerable failure rate, due to the principles of man-in-the-middle attacks, network card issues, gateway restrictions, DNS caching, and other factors, so hijacking failures are also possible.
05 Final Words
Average people achieve success not through their innate talents, but by bringing ordinary talents to extraordinary heights.



