One Firewall Technology Concepts and Classification
1. Introduction to Firewall Technology
- FirewallAllow authorized data to pass through, while rejecting unauthorized data communication. Isolation of the Intranet andInternetA layer of defense between the internal network and the open Internet, allowing communication. Visitors must first breach the firewall’s security barrier to access the target computer.
- In the absence of a firewall, each node within a local area network is exposed to other hosts on the Internet. At this point, the security of the internal network depends on the robustness of each node, and security is equivalent to that of the weakest node.The Weakest NodeAfter deploying a firewall, the firewall centralizes the security of the internal network onto itself. Network security is reinforced on the firewall system rather than being distributed across all nodes of the internal network.
- Basic Functions of a Firewall:
- As a central “choke point,” concentrate the security management of the intranet, ensuring all communications pass through the firewall;
- Allow only authorized network traffic, block unauthorized requests, prevent privilege escalation, and generate security alerts;
- Capable of withstanding attacks against itself.
- Firewalls operate at the OSI reference model levels:
|
The OSI Reference Model is a framework that describes the layers involved in network communication. It consists of seven layers: the physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and application layer. Firewall Technology plays a |
Firewall Technology |
|---|---|
|
Application Layer |
Application-level gateway |
|
Presentation Layer |
Encryption |
|
Session Layer |
Circuit-level gateway |
|
Transport Layer |
Packet Filtering |
|
Network Layer |
NAT |
|
Data Link Layer |
It appears there is no text content to translate. If you have any specific content or |
|
Physical Layer |
There is no text to translate. If you have any questions or need assistance with something |
- The History of FirewallsIt seems like your message might not have come through completely. Could you please provide the
- The first generation of firewall technology consisted of Access Control Lists **ACL (Access Control Table)** attached to border routers, utilizing packet filtering technology.
- The second-generation proxy firewall, that is to say,Circuit Layer GatewayandApplication Layer Gateway。
- In 1994, the Israeli company Check Point developed the first firewall product based on dynamic packet filtering technology.
- In 1998, the American network conglomerate NAI (Network Associates Inc.) introduced an adaptive agent technology.
- The Two Major Categories of FirewallsIt seems like there might have been an error in your input. Could you please provide thePacket Filtering FirewallandProxy FirewallThe former is represented by Checkpoint firewalls and Cisco’s PIX firewalls, while the latter is represented by NAI’s Gauntlet firewall.
|
Packet filtering firewall |
Proxy firewall | |
|---|---|---|
|
Advantages |
Work at the IP and TCP layers, resulting in fast packet processing and high efficiency; Provides transparent service, allowing users to avoid changing client programs. |
Packets are not allowed to pass directly through the firewall, preventing data-driven attacks and ensuring good security; it can generate various logs. It can flexibly and completely control incoming and outgoing traffic and content; it can filter data content. |
|
Packet filtering firewall |
Proxy firewall | |
|---|---|---|
|
Disadvantages |
Definition is complex, which can lead to issues due to improper configuration; allows packets to pass directly through, posing potential risks for data-driven attacks; cannot completely prevent address spoofing; only includes information about which machine the packet is from, not which user; does not support user authentication; does not provide logging capabilities. |
For each service, the proxy may require a different server; slower speed; lack transparency for users, as they need to change the client application; cannot guarantee protection against all protocol vulnerabilities; cannot enhance the security of the underlying protocol. |
- Components of a Firewall: A firewall can be a router, a PC, or a host, and it can also be a system composed of multiple hosts. The firewall should be placed at the network’s perimeter.Network Perimeteris the entire perimeter of a local network. The local network is connected to other networks through input and output points, all of which should be equipped with firewalls. However, firewalls should also be deployed within the network perimeter to provide additional, specialized protection for specific hosts.
- Classification of FirewallsI’m here to help with translating WordPress content while maintaining the HTML structure.
- Based onEmployed TechnologiesDifferent types can be classified into packet filtering firewalls and proxy service firewalls;
- It seems like there might be some text missing. Could you please provide the full content you need to be translated?Application ObjectCan be divided into enterprise-level firewalls and personal firewalls;
- BasisImplemented MethodsSoftware firewalls, hardware firewalls, and dedicated firewalls are distinguished from one another.
- Software firewall: Firewalls operate on specific computers, typically, this computer acts as the gateway for the entire network. Software firewalls, like other software products, need to be installed and properly configured on the computer before they can be used. Utilizing such firewalls requires network administrators to be well-acquainted with the operating system platform they are working on.
- Hardware Firewall: Composed of PC hardware, general-purpose operating systems, and firewall software. This runs on a custom PC hardware setup that includes a common PC system, flash drive, and network card, operating on a heavily minimized and secured version of systems like Linux, FreeBSD, or Solaris, with integrated firewall software. Features include low development costs, practical performance, good stability and scalability, and affordability. However, these types of firewalls depend on the operating system’s kernel, thus their security is influenced by the inherent security of the operating system, and the processing speed is also slow.
- Dedicated Firewall: Equipped with specially optimized hardware architecture and utilizing dedicated operating systems, these firewalls have significant advantages in stability and transmission performance—offering high speed, robust processing capability, and superior performance. Due to their use of dedicated operating systems, they are easy to configure and manage, with fewer inherent vulnerabilities, although they have limited scalability and come at a higher cost. Given the well-structured serialization of dedicated firewalls, users can select appropriate products based on their application environment.
2. Packet Filtering Firewall Technology
- Packet filtering(Packet Filter) is the core function of all firewalls, with packet filtering criteria established based on security policies. Typically, this is set by network administrators in the firewall device’s ACL. Compared to a proxy server, its advantage is that it does not consume network bandwidth to transmit information.
- Packet filtering rules are generally stored inRouter’s ACLIn ACLs, various rules are defined to indicate whether to permit or deny the passage of data packets.
- If no rule matches, the firewall will use the default rule. Generally, the default rule mandates that the firewall discard the packet. The core of packet filtering is the security policy, which is the design of the packet filtering algorithm.
- Stateless Packet Filtering FirewallI noticed that your message doesn’t contain any text to translate. Could you pleaseStateless packet filteringAlso known as static packet filtering or non-inspection packet filtering. The firewall, when examining packet headers, does not concern itself with the communication between the server and the client.Connection Status, merely checks all incoming and outgoing packet header information against pre-defined filtering rules to allow or deny packets.
- Advantages:Fast and efficient.The management of traffic is outstanding; since all communications must pass through the firewall, bypassing it is difficult; at the same time, it is transparent to users and applications.
- Drawback: It allows external networks to connect directly to internal network hosts; as long as the packets comply with ACL rules, they can pass through, so it cannot distinguish between “good” and “bad” packets; it is unable to identifyIP fraudI’m here to assist with translating WordPress posts into highly specialized American English, focusing on cybersecurity terminology. Please provide the content you would like translated, while I’ll focus on maintaining the original formatting and style.User Authentication, does not provide logging functionality; althoughFiltering ports is possible.However,Unable to filter services.。
- IP Spoofing: When an external host spoofs an internal host’s IP address, the firewall can block this type of IP spoofing. However, when an external host spoofs the IP address of a trusted external host, the firewall cannot block them. This is due to stateless packet filtering firewalls.Unable to maintain a record for pending communication., it must therefore determine whether the packet belongs to a previously allowed conversation based on the packet’s format. This thenMake it susceptible to IP fraud, and it’s unable to recognize the state of UDP datagrams and ICMP packets.
- Unable to Filter ServiceFor some more recent multimedia applications, the port number is unknown before a session begins.
- Stateful packet filtering firewallI’m here to help with translating the text content of your WordPress posts. Please provide theStateful Packet FilteringAlso known asStateful Packet Inspection (SPI) or Dynamic Packet Filtering, later evolved into stateful inspection technology, which is a compromise between packet filters and application-level gateways. It offers the speed and flexibility of packet filtering mechanisms, while also providing the application layer security advantages of application-level gateways.
- Stateful Packet Inspection Firewall: In addition to having a set of filtering rules, firewalls using SPI (Stateful Packet Inspection) technology must also inspect each packet that passes through it.All connections are being tracked., gather relevant information about the status of communications and applications to create a list of current connection states. This list should at least include source and destination IP addresses, source and destination port numbers, TCP sequence number information, and additional flags related to each specific TCP/UDP session. When a session passes through the firewall, the SPI firewall compares packets against the state table and the rule set, allowing only entries that match the state table and the rule set to pass through.
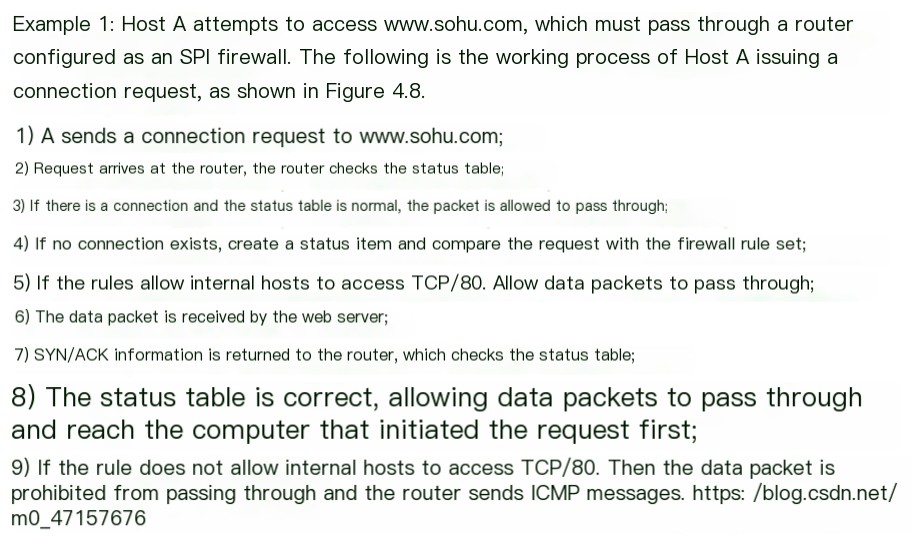
- Advantages: PossessesIdentify packets with deceptive source IP addresses.The ability; the levels of inspection can go fromFrom the Network Layer to the Application Layer; The ability to keep detailed records of each packet that passes through, including information such as the application’s request for the packet, the duration of the connection, connection requests made by internal and external systems, etc.
- Drawback: All this logging, testing, and analysis work might cause some network latency, especially when numerous connections are simultaneously active or when there are a large number of rules filtering network communications. However, the faster the hardware, the less noticeable this issue becomes.
3. Firewall Technology: Proxy Service Firewall
- Initially, proxy servers stored commonly used pages in a cache to improve the speed of network communication. Later on, proxy servers evolved into a technology capable of providing robust security features. Proxies can implement firewall functions at the application layer, and the proxy technology is aimed atEvery specific application has its own program.By using a proxy, it is possible to achieve more thanThe packet filtering is more stringent.Security strategy.
- A proxy server firewall is based onIt seems like you’ve entered a piece of text in Chinese, which translates to “software” in English. If you have WordPress posts that need translating, please provide the specificThe proxy server functions as a barrier, operating between internal users and external hosts, forwarding data between them. It stands as a true ‘wall’ between the intranet and the Internet. Visitors from the outside can only see the proxy server and cannot view any internal resources; meanwhile, internal clients do not notice the presence of the proxy server and can freely access external sites. The proxy can provide excellent access control, logging capabilities, and address translation functions, recording information going in and out of the firewall, making it easier for administrators to monitor and manage the system.
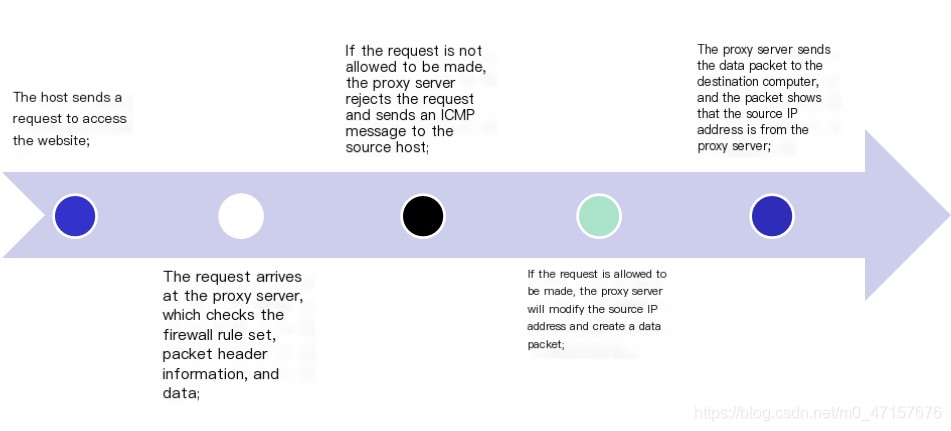
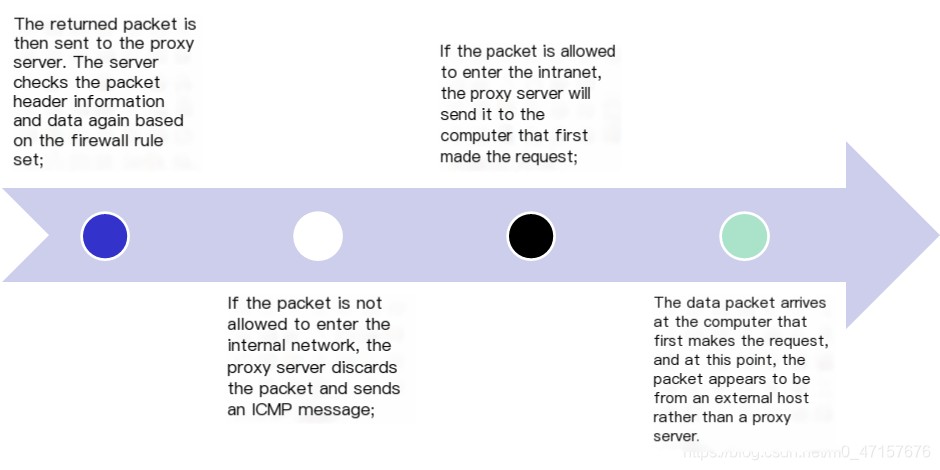
- Comparison of Proxy Servers and Packet FilteringIt seems like there might be an issue with the text you intended to provide. Could

4. Circuit-Level Gateway in Firewall Technology
- Circuit-level gateway not allowedTCP End-to-End Connection, but it is necessary to establish two connections. One of these connections isGateway to Internal Hosts, another isGateway to External HostOnce two connections are established, the gateway simply relays the data; that is, it merely copies bytes back and forth between the internal connection and the external connection, and then…Source IP address translated to own address, making the outside world think that the gateway and the destination address are connecting. Because the circuit-level gateway in the sessionOnce a connection is established, no further analysis of the transmitted content is performed, thus the security is slightly lower.。
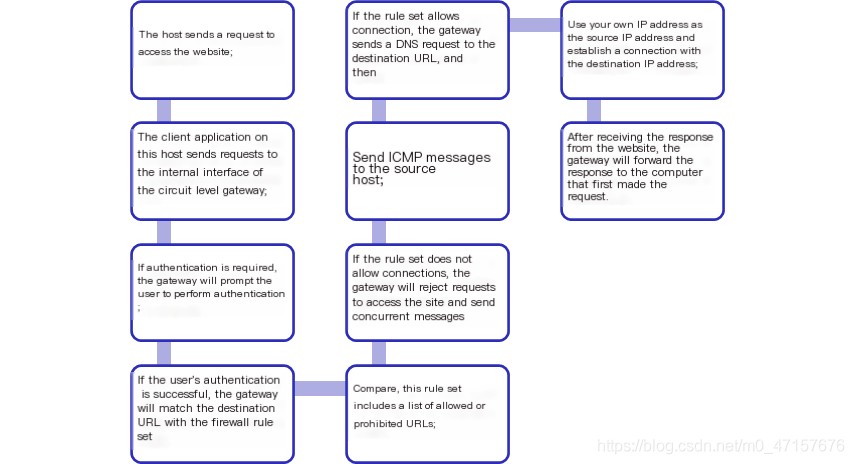
- Advantages: Provides Network Address Translation (NAT), offering network administrators significant flexibility in ensuring security when using internal network address mechanisms; possesses the same rules as a packet-filtering firewall, with all the benefits provided by a packet-filtering firewall.
- Disadvantages: It cannot effectively distinguish between good packets and bad packets, is susceptible to IP spoofing attacks; requires modifications to applications and executables; demands end-user authentication.
5. Application-Level Gateway in Firewall Technology
- Application-level gateways primarily operate at theApplication LayerWhen a client needs to use the data on a server, it first transfers the data.I understand you’re asking for assistance, but I need the specific text content from the WordPress posts to proceed with the translation. Please provide the content you need help with.Send to the proxy server, then the proxy server requests from the server based on this.Request DataThen, the proxy server transmits the data to the client. Since there is no direct data channel between the external system and the internal server, it becomes very difficult for external malicious threats to harm the internal network.
- In an application-level gateway, each protocol requires a corresponding proxy software. Common proxy service software includes HTTP, SMTP, FTP, and Telnet. However, for newly developed applications, there is no corresponding proxy service yet. Some application-level gateways also store frequently accessed pages from the Internet. When a page requested by the user is present in the server’s cache, the server will check if the cached page is the latest version (i.e., whether the page has been updated). If it is the latest version, it is submitted directly to the user; otherwise, the latest page is requested from the actual server and then forwarded to the user.
- Advantages: It can effectively isolate computer systems inside and outside the firewall, offering good security. It can also be used to implement robust data flow monitoring, filtering, logging, and reporting functions.
- Drawbacks:Implementation ComplexityFor end users who modify their applications to use proxy servers, this choice lacks transparency. Additionally, since proxy servers must utilize operating system services to execute the proxy process, they are often built on top of the operating system. As a result, the issue that arises isIncreased overhead, reduced performanceMoreover, since general-purpose operating systems are well-known, these systems are vulnerable to attacks.VulnerabilityIt is also public.
6. Adaptive Proxy Firewall Technology
- While application proxy firewalls offer excellent security, their speed tends to be inadequate.Adaptive proxy technology combines the security of proxy server firewalls with the high speed of packet filtering firewalls. The basic components of this type of firewall consist of two elements: the Adaptive Proxy Server and the Dynamic Packet Filter. In an adaptive proxy firewall, the initial security checks still occur at the application layer.is carried out to ensure the highest security of traditional firewalls; once a trusted identity is authenticated and a secure channel is established, subsequent packets can be redirected toNetwork LayerThis enhances the performance of the proxy firewall by more than tenfold without compromising security.
7. Composite Firewall
- Due to the firewall’s advantageous position (at the boundary between the internal network and the Internet), in practical applications, aside from basic filtering and access control, the firewall has also addedNAT、VPN、IDS、AAA、QoSencryption, content filtering, antivirus, routing management, network monitoring, etc. Initially, these functions were provided by separate devices located in either a serial or parallel position within the network. Currently, the common solution is to integrate these features into the firewall. When a firewall with these integrated functions operates correctly, network connections are both secure and efficient.
- Network Address Translation: Network Address Translation (NAT) is a technology that maps one IP address domain to another IP address domain, thereby providing transparent routing for endpoint hosts. NAT is commonly used for translating between private address domains and public address domains to address IP address shortages. Upon implementing NAT on a firewall, it allows forHiding the internal topology of a protected network, to a certain extent, enhance the security of the network. It can be implemented on border routers, packet-filtering firewalls, and proxy service firewalls.
- Virtual Private NetworkVirtual Private Network (VPN) is a private network constructed within a public network, where data travels through a secure “encrypted tunnel” across the public network. Currently, the security assurance of VPN primarily relies on firewall technology, routers equipped with tunneling technology, encryption protocols, and security keys. It is used for communication between company headquarters and branches, partners, and mobile office users via the public network while achieving the objective of security.
- Intrusion Detection SystemIntrusion Detection Systems (IDS) represent a proactive network security technology designed to protect against attacks. They detect and respond to unauthorized activities on computer networks and hosts. Usually, IDS is installed at several critical points within a computer network or system to gather and analyze data, identifying any behaviors or signs of attacks that violate security policies. These systems enhance the security management capabilities of system administrators, including security auditing, monitoring, attack identification, and response, thereby improving the integrity of the information security infrastructure.
- Authentication, Authorization, and Auditing: The AAA framework refers to Authentication, Authorization, and Accounting, which are the three main functionalities of a centralized authentication server as articulated by Cisco Systems. It forms a component of network security strategy. Authentication involves the verification of remote access users’ identities to determine whether the user is a legitimate network user. Authorization follows authentication and involves determining the resources a user can access and what actions the user is permitted to perform. Accounting is about recording all the actions users perform while using network services for purposes such as statistics, billing, and auditing, including service types, start times, and data volume.
- Service Quality: Quality of Service (QoS) is a security mechanism within a network. A network that implements QoS is an intelligent network, capable of providing priority service to data with high real-time requirements, such as audio and video streams, thus ensuring minimal latency. Without QoS implementation, applications like IP telephony, video conferencing, and mission-critical data would only be transmitted on a “best effort” basis, which may lead to instability in voice and video during network congestion.
- I’m here to help you translate WordPress posts into American English while maintaining the HTML structure and styles. If you have a specific text you would like to translate, please provide it, and I’ll take care of the content for you: A firewall should also incorporate advanced authentication measures, such as information confidentiality protection, integrity verification, and authorization management technologies. The more complete the network management security, the more complex the architecture becomes. Managing multiple security devices in the network also requires centralized network management.
8. Personal Firewall
If you have more text or specific HTML content you’d like translated, feel free to share!
- Personal firewall software consists of a “code wall” installed within the PC system, separating your computer from the Internet. It scrutinizes all data packets reaching both sides of the firewall, whether incoming or outgoing, to determine whether to block or allow them. In other words, it prevents unauthorized access to your computer from other Internet users while not hindering your normal web browsing.
- A good personal firewall must have low system resource consumption, high processing efficiency, a simple and comprehensible setup interface, and flexible yet effective rule settings.
Two Firewall Architectures
- Firewalls are an excellent choice for protecting network security. Setting up a firewall, choosing the appropriate type of firewall, and configuring it are the three key tasks to effectively utilize a firewall.How to set it upIt appears the submission contains only a punctuation mark or a character that may not be relevant for translationIt should be placed at what location?This is the issue to be discussed in this section.
1. Bastion Host
- Single-host Bastion Host: There is a bastion host with a network card functioning as a firewall, typically used forApplication-level gateway firewallConfigure the external router toAll incoming data is sent to the bastion host.On, simultaneously 将Configure all internal client settings so that all outgoing data is sent to this bastion host.The bastion host examines this data based on security policies. Its main drawback is that it is possible to configure a router to allow information to directly enter the internal network, completely bypassing the bastion host. Internal users can also configure their hosts to send information directly to the router, circumventing the bastion host.
- Dual-homed Bastion Host: A bastion host with dual network interfaces serves as a firewall, with each network interface connected to the internal and external networks, respectively. However, direct communication between the internal and external networks is not permitted, and data flows between the networks are entirely severed by the dual-homed host. It employsHost replaces routerImplement security control functions. Network control can be provided by running proxy software or allowing users to register directly onto it. When a hacker attempts to access the internal network, they must first breach the dual-homed bastion host, giving network administrators time to respond and prevent the intrusion.
- “Internal Bastion Host”The bastion host communicates with the internal network to forward information obtained from the external network. This type of bastion host has enabled more services and opened more ports to meet the needs of applications.
- External Bastion HostThe bastion host provides public services to the Internet, itDo not forward any requests to the internal network., but handles requests itself. It only provides very limited services and keeps only a few ports open to fulfill these kinds of services. It requires more defense and protection and should block any access to the intranet.
- Compromised Bastion Host: This bastion host is an intentionally exposed target for attackers, also known as a honeypot or trap. The primary purpose of setting it up is to lure illicit attacks, making hackers believe they have successfully breached the network and allowing them to continue their actions so that time is gained to track them. This bastion host contains only the minimal configuration needed to run the relevant programs.
2 Demilitarized Zone (DMZ)
- One of the most critical concepts used in modern web security design is according toFunctionalityOrDepartmentSegmenting the Network intoSubnetDifferent network segments have distinct security requirements.
- Ethernet is a broadcast network, meaning any machine on the network has the potential to view all communications on that network. If a hacker breaches the network, they can easily intercept all communications. For ease of configuration and management,Servers that need to provide services externally from an internal network are often placed in a separate subnet, which is known as the DMZ (Demilitarized Zone).The DMZ is located outside the internal network, with a network number different from the internal network, connected to the firewall, and provides public services.
- Methods for Creating a DMZ:
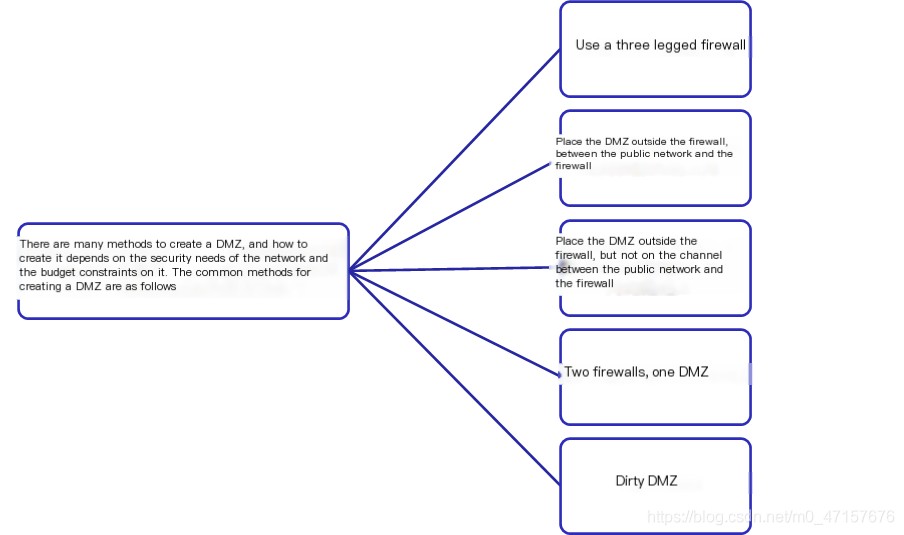
- Utilizing a three-tier firewall: Use a firewall with three interfaces (three-homed firewall) to create a demilitarized zone (DMZ), where each zone becomes a member of the interfaces on this firewall. The firewall provides isolation between zones and ensures the security of the DMZ.
- A DMZ is placed between the public network and the firewall.The traffic passing through the firewall should first go through the DMZ. The drawback is that the DMZ is exposed to the public-facing side, so this configuration is not recommended.
- The DMZ is placed outside the firewall and not on the pathway between the public network and the firewall.: The DMZ is located at an interface of the edge router, not directly connected to the firewall, creating an isolation layer from the DMZ to the firewall. In this configuration,RouterA mechanism that can be used to deny all access from the DMZ subnet to the firewall subnet enhances security by adding an extra layer of isolation. When a host located within the DMZ subnet is compromised and attackers begin utilizing this host to launch further network attacks, this additional layer can help slow down the progress of attacks aimed at the firewall.
- Two firewalls, one DMZ: The DMZ is protected by two firewalls. Firewall ① monitors communication between the DMZ and the Internet, while Firewall ② monitors communication between the DMZ and the internal network. Firewall ② serves as a backup device and can act as a failover firewall, stepping in immediately if Firewall ① fails. Although Firewall ① provides the DMZ with considerable security, its downside is that when accessing the internal network from the Internet, all traffic mustUsing the DMZ (Demilitarized Zone)All traffic from the intranet to the Internet also needs to bePass through the DMZWhen a DMZ device is compromised, attackers can intercept or attack this traffic. The solution is to use VLANs on the devices between the two firewalls. Another disadvantage is that it requiresUsing Two Firewalls, which increased the cost of the equipment.
- “Dirty” DMZ: Establish a boundary line between the insecure Internet and the semi-secure DMZ using a border router, resulting in a “dirty” DMZ. Here,Border RouterA standard router, acting as the first line of defense, utilizes built-in ACLs to implement packet filtering rules defined by network security policies, providing partially protected environments for bastion hosts. A dedicated firewall offers a second line of defense, ensuring better protection of internal network resources.
3. Blocking Router
- A Screening Router is a router placed between the Internet and an internal network, enabling it to perform packet filtering functions.This is the simplest firewall. A packet-filtering router can be implemented by the router. It serves as the sole passage for internal and external connections, requiring all packets to be inspected here. Install packet-filtering software on the router to achieve packet filtering functionality. Although it is not expensive, it still provides significant protection.
- The screened router architecture, also known as a filtering router architecture, has the major advantage of being simple in structure with relatively low hardware costs. Since the router provides very limited services, securing it is easier to achieve compared to securing a host.
- Drawbacks:
- Firewalls that rely solely on packet filtering rules to filter packets can accidentally allow undesirable traffic or block acceptable traffic due to any configuration errors.
- Only having a single device to secure the network means that if a hacker compromises this router, he will be able to access any resources within the internal network;
- A firewall router cannot conceal the configuration of the internal network; anyone with access to the firewall router can easily view the layout and structure of the internal network.
- A router without effective monitoring and logging capabilities, lacking alert functionality and user-level authentication, cannot notify network administrators of potential threats if a security breach occurs.
The Dual Homed Host Architecture
- Using a bastion host equipped with two network interface cards (NICs) as a firewall, each NIC is connected to the internal network and the Internet, respectively. The bastion host runs firewall software that can forward applications and provide services, among other functions. Communication between the internal and external networks must go through the bastion host. In this architecture, routing must be disabled so that networks on both sides of the firewall can communicate only with the dual-homed host, preventing direct communication between the two systems.
- Dual-host architectureSuperior toThe area to shield the router is: Bastion host system software can be used to maintain system logs, hardware copies of logs, or remote management logs. This is useful for future inspections. However, this does not help network administrators identify which hosts within the intranet may have been compromised by hackers.
- A fatal flaw in dual-host architectureVulnerabilityOnce an intruder compromises the bastion host and reduces it to merely a routing function, any online user can freely access the internal network.
5. Host-based Filtering Architecture
- In a dual-homed host architecture, firewalls do not use routers. However,Host Filtering Architecture FirewallThe Screened Host Firewall uses a router to isolate the internal network from the external network, with the router acting as the interface between the two.
- Host-based filtering architecture is also known asBlocking Host ArchitectureorFilter Host ArchitectureIn this architecture, a router that performs packet filtering is connected to the external network, where filtering rules are established to prevent people from bypassing the proxy server and connecting directly. At the same time, a bastion host is installed within the internal network, making it the only host that can be directly accessed from the external network. This ensures that the internal network is protected from attacks by unauthorized external users.
- Router-implemented packet filtering can permit internal hosts to open connections to the Internet for specific services or deny all attempts from internal hosts to connect to the Internet. Internal hosts should be required to send their connection requests through a bastion host.
- The proxy server should be installed behind the firewall. The firewall should have an interface with the Internet to provide protection for the proxy server located behind it. This protection is crucial because, when the proxy server is compromised by a hacker, it might mistakenly perceive the hacker as an internal client and allow them through the proxy server. This can lead to catastrophic consequences for the protected network.
6. Subnet Filtering Architecture
- The subnet filtering architecture is also known as the screened subnet architecture or filtering subnet architecture. It uses two machines to…Packet Filtering RouterEstablish a DMZ to separate the internal network from the external network.
- In this architecture, two packet-filtering routers are positioned at both ends of the DMZ, creating a screened subnet accessible by both the internal and external networks, while prohibiting direct communication through the screened subnet. Within the screened subnet, the bastion host serves as the sole access point, acting as an application-level gateway proxy.
- To infiltrate this type of network, a hacker must first compromise the external router. Even if they manage to breach the bastion host, they must still navigate through the internal router to enter the internal network. In this architecture, since the bastion host does not directly interact with internal network hosts, communication between two hosts in the internal network does not pass through the bastion host. Therefore, even if a hacker breaks into the bastion host, they can only observe communication from the Internet and some internal hosts to the bastion host, along with the return communication, but not the communication between hosts within the internal network. As a result, the DMZ adds a layer of security for the internal network.
- An internal router, also known as a blocking router or choke router, is tasked with protecting the internal network from breaches originating from the Internet and the DMZ, and it handles firewall packet filtering duties. It selectively permits outbound services from the internal network to the Internet. To minimize the number of intrusions on the bastion host, it is crucial to limit the services provided by the bastion host to the internal network.
- An external router, also known as an access router, protects the DMZ and internal network from intrusions originating from the Internet. It generally allows nearly all communications outbound from the DMZ and typically only performs minimal packet filtering; however, it must block any incoming packets from the Internet that have spoofed source addresses. Such packets claim to come from the internal network but in reality, they originate from the Internet.
7. Combination Architecture
- When building firewalls, it is uncommon to use a single technology; instead, a combination of various technologies is usually employed to address different issues.
- Multi-Bastion Hosting
- Merging Internal Router with External Router
- Integrating Bastion Host with External Router
- Combine bastion host with internal router
- Utilizing Multiple External Routers
- Utilizing Multiple Peripheral Networks
Three: Firewall Selection and Product Overview
- The current focal points in the development of firewall technology are primarily in the following four areas:Firewall Management—The Key to CybersecurityFunctions of a Firewall——The Basics of Firewall ApplicationsThe Performance of Firewalls——Conditions to Improve Network Transmission EfficiencyFirewall’s Ability to Withstand Attacks——Ensuring Network Security
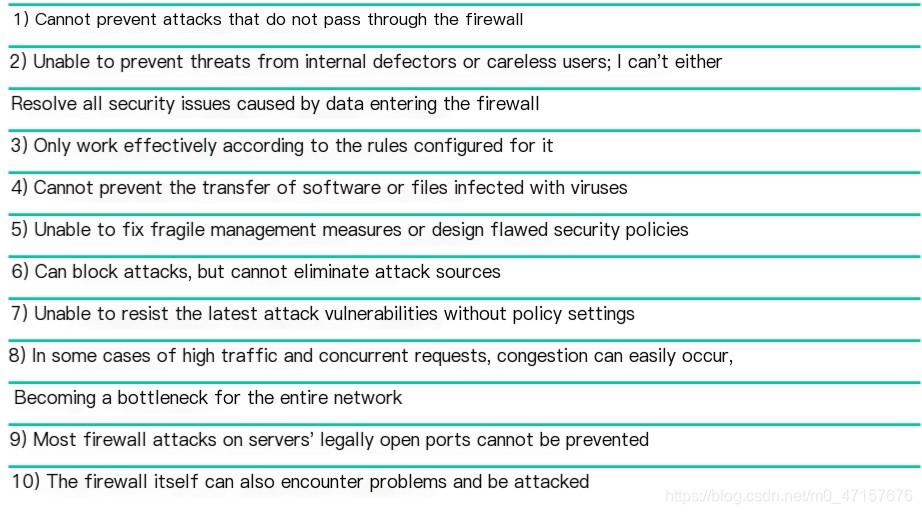
1. Limitations of Firewalls
2. Developing Firewall Security Policies
- The hardest part of installing a firewall is not dealing with the hardware and software, but rather explaining to those around you the restrictions you intend to impose.
- Security and complexity are inversely proportional.
- Security and usability are inversely proportional.
- To conduct a thorough analysis of cyber threats, it’s essential to distinguish between real threats, potential threats, and hypothetical threats, as well as known and unknown threats.
- Security strategies are not set in stone.
- Security is an investment, not a consumption; it requires strong support from the leadership of the company or organization.
3. Principles for Choosing a Firewall
- Network throughput, packet loss rate, latency, and the number of connections are all critical technical metrics. A high-quality firewall can effectively manage communication, offering different control strategies for users with varying levels and needs.
- The effectiveness, diversity, clarity of level targets, and difficulty of formulation of control strategies directly reflect the quality of firewall control policies.
4. Introduction to Typical Firewalls
- Checkpoint FireWall-1It seems like your message is incomplete. Could you please provide the text you need help translating?
- Status Detection Module(Inspection Module): Provides access control, client authentication, session authentication, NAT, and auditing functions;
- Firewall Module(FireWall Module): Includes a stateful inspection module, additionally providing user authentication, content security, and multi-firewall synchronization capabilities;
- Management Module(Management Module): Provides centralized, graphical security management functionality for one or more security policy enforcement points (a system with an installed FireWall-1 module, such as a stateful inspection module, firewall module, or router security management module). A management module can control up to 50 individual FireWall-1 instances.
- Cisco PIX FirewallI’m here to assist you. Please provide the WordPress post content that you need translated, focusing on the plain text while maintaining the HTML structure and styles.
- Confidential Interconnection ExchangePIX (Private Internet Exchange) serves to prevent unauthorized external users from accessing the internal network. Most PIX solutions can selectively protect one or more DMZs. The connections between the internal network, external network, and DMZ are controlled by the PIX Firewall.
- PIXThe core is a protective mechanism based on the Adaptive Security Algorithm (ASA), which maps internal host addresses to external addresses, rejects unauthorized packets from entering, and implements dynamic and static address mapping, thereby effectively cloaking the internal network topology. Through tunneling technology and outbound access lists, it effectively controls the access to various internal and external resources.
- ASAThis is a stateful security approach. Every incoming packet is inspected according to adaptive security algorithms and the connection state information stored in memory. The ASA remains operational, monitoring returning packets to ensure their validity.

- Neusoft NetEyeFounded in 1991 at Northeastern University, Neusoft Group is a leading software and solutions provider in China. The Neusoft NetEye firewall is built on a dedicated hardware platform, utilizing proprietary ASIC chips and a proprietary operating system, employing a “flow filtering” architecture based on stateful packet inspection. Surrounding the flow filtering platform, Neusoft has established a network security response team, an application upgrade package development team, and a network security laboratory. This not only delivers high-performance application layer protection to users but also includes timely support for new applications, custom development for special applications, and prompt response to security incidents.


