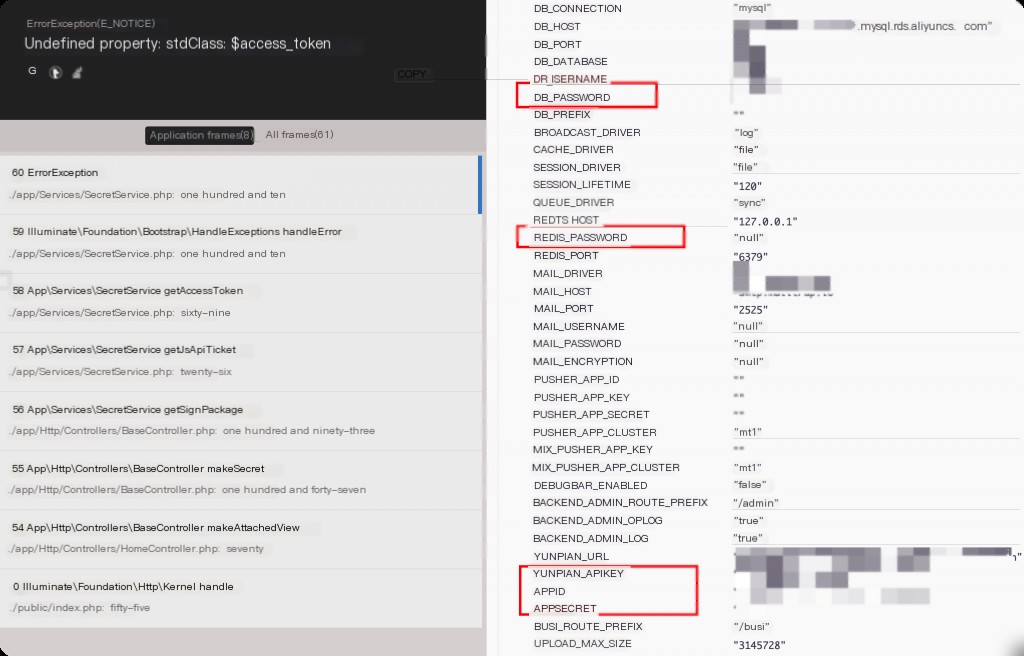
In penetration testing, it is common to encounter situations where certain frameworks have debug mode enabled, leading to the leakage of account passwords or keys. Therefore, a summary of common development framework debug modes is provided.
Laravel
Laravel is a popular PHP web development framework, widely used abroad. By default, Laravel does not have debug mode enabled. You can enable debug mode by modifying the .env file to APP_DEBUG=true and restarting. If developers do not disable debug mode after the project goes live, sensitive information may be exposed on the public internet.
Shodan Search Syntax
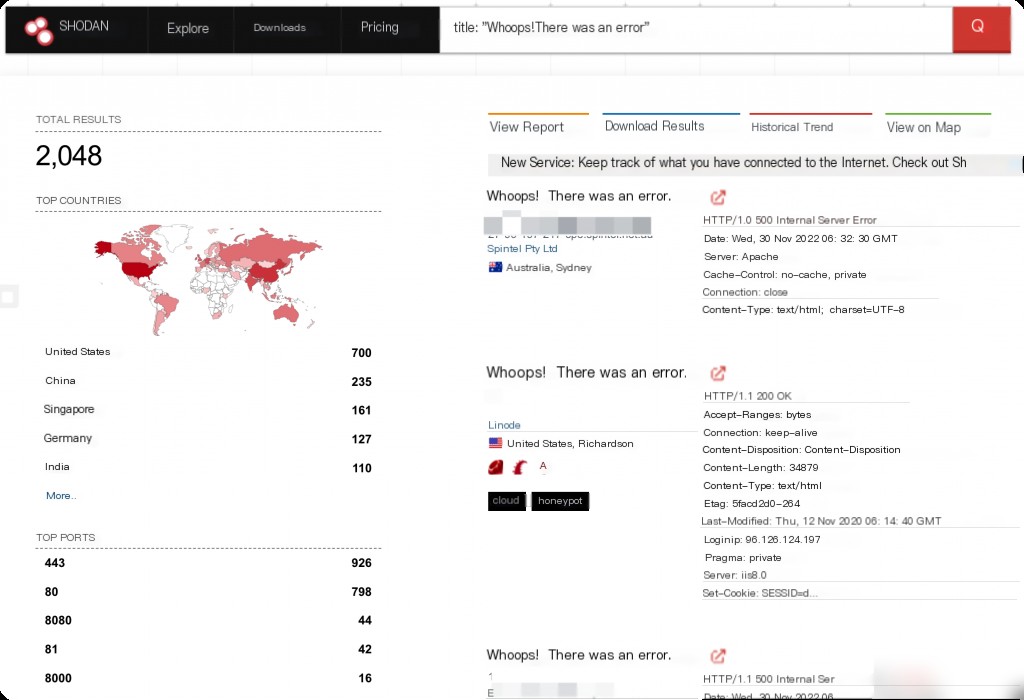
http.title:"Whoops! There was an error"
ThinkPHP
ThinkPHP generates logs in the Runtime directory when DEBUG is enabled.
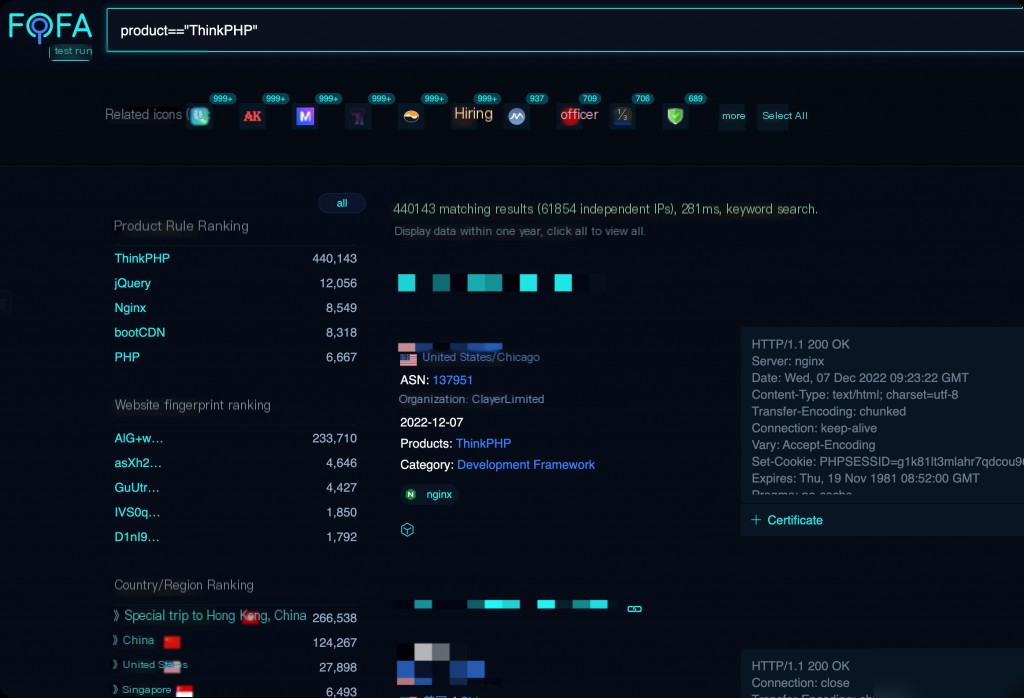
fofa Search Syntax
product=="ThinkPHP"
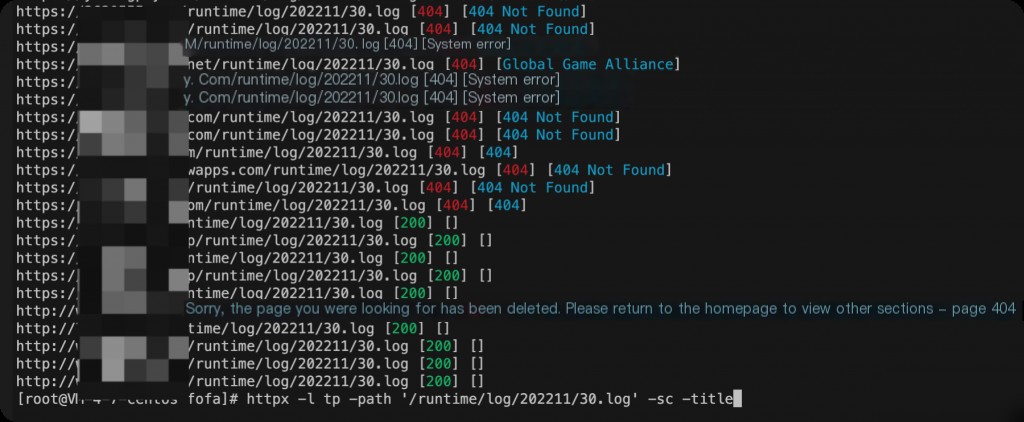
TP3:
/Runtime/Logs/ /App/Runtime/Logs/ /Application/Runtime/Logs/Admin/ /Application/Runtime/Logs/Home/ /Application/Runtime/Logs/App/ /Application/Runtime/Logs/Ext/ /Application/Runtime/Logs/Api/ /Application/Runtime/Logs/Test/ /Application/Runtime/Logs/Common/ /Application/Runtime/Logs/Service/ /Application/Runtime/Logs/
TP5:
/runtime/log/
The log format is as follows: logs with a timestamp prefix.
tp3 19_01_01.log 1550651608-19_02_20.log tp5 /runtime/log/201808/07.log /runtime/log/201808/07_cli.log
Thus, logs can be easily guessed, and they contain records of executed SQL statements.
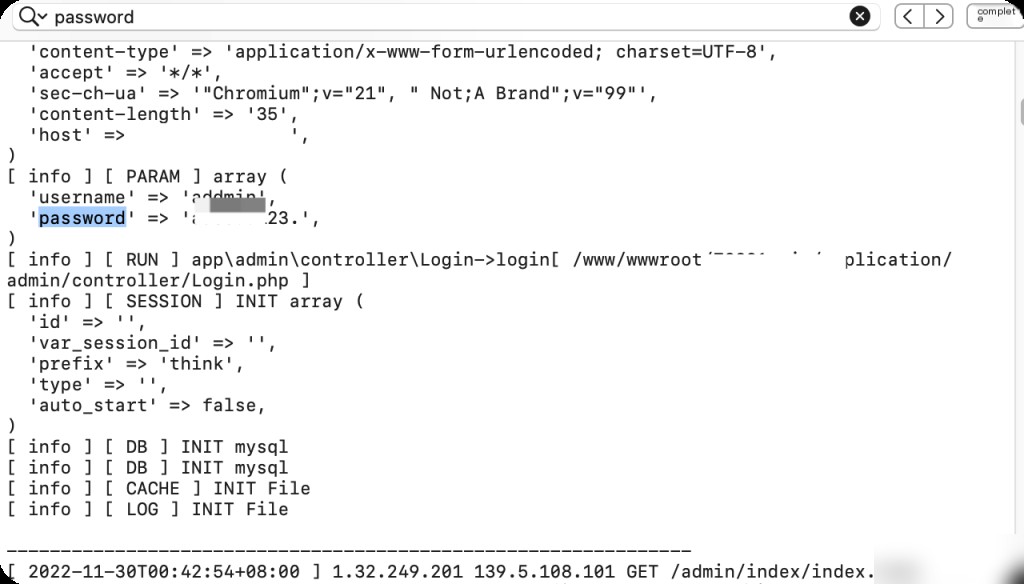
Search for the keyword “password” in the logs to find SQL statements.
Django
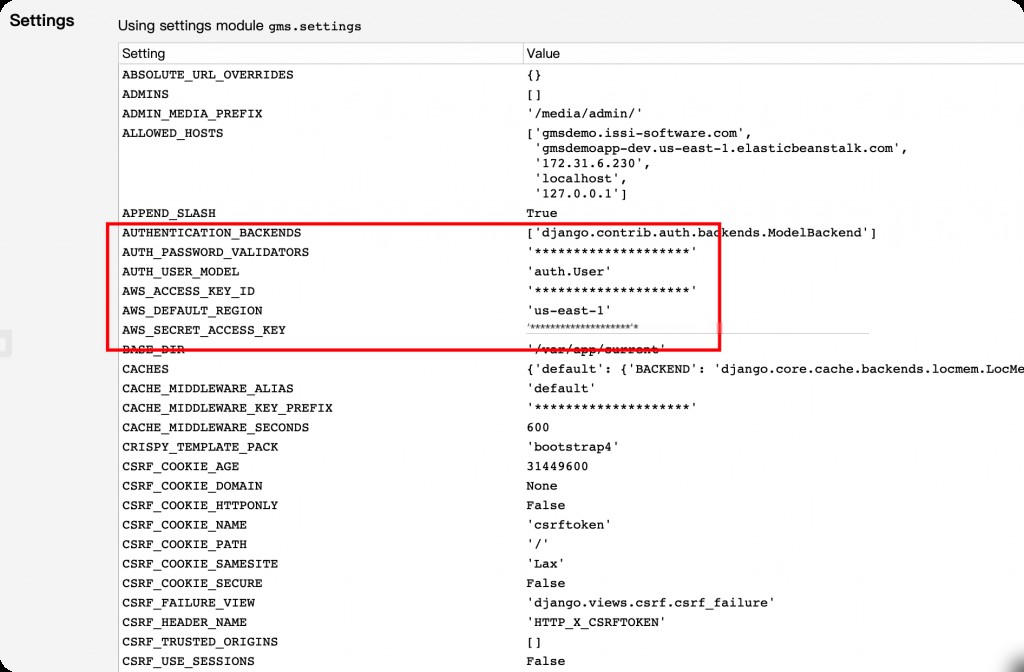
Django’s debug mode handles sensitive information by displaying all passwords and keys as asterisks, making it relatively safer.
Shodan Search Syntax
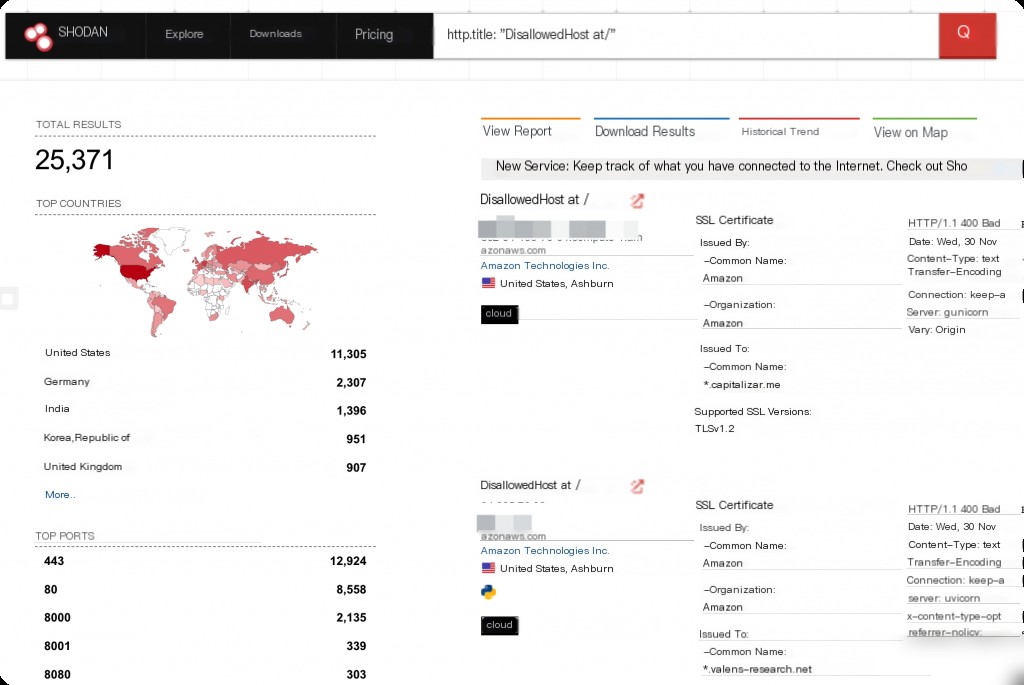
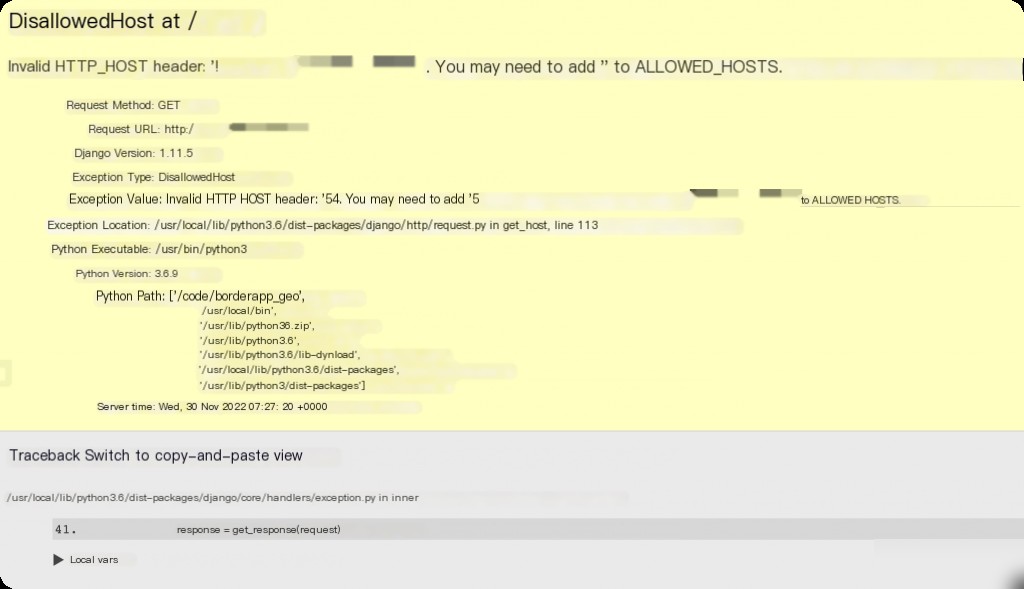
http.title:"DisallowedHost at /"