Preface: Cyber-attacks
In recent years, the severity of security threats posed by cyber-attacks has increased exponentially, with several major data breaches occurring almost every month. While various models of IDS/IPS are not new technologies, considering the latest trends in cyber-attack techniques, the implementation of IDS and IPS remains a crucial subject to understand and consider.
What is IDS in Cyber-attacks?
IDS is an abbreviation for “Intrusion Detection Systems”. Professionally speaking, it monitors the operations of networks and systems in accordance with certain security policies, detecting attempts, actions, or results of attacks as much as possible to ensure the confidentiality, integrity, and availability of network system resources.
An easy analogy: If a firewall is the lock on a building’s door, then the IDS is the surveillance system inside the building. Once a thief climbs through a window or an insider crosses boundaries, the real-time monitoring system can detect the situation and issue a warning.
What is IPS
Intrusion Prevention System (IPS) is the next generation of Intrusion Detection Systems (IDS), addressing weaknesses in IDS such as promptness, false positives/negatives. IPS can identify the intrusion, correlation, impact, direction, and appropriate analysis of events, then send the suitable information and commands to firewalls, switches, and other networking devices to mitigate the event risks.
After introducing the basic concepts, let’s take the open-source snort as an example to actually build and test it.
Snort
 >
>
Introduction
Snort is a powerful network intrusion detection/prevention system (NIDS/NIPS) with features such as multi-platform (Multi-Platform), real-time (Real-Time) traffic analysis, and network IP packet (Pocket) recording.
Snort employs rule-matching mechanisms to detect whether network packets violate predefined security policies. Installed on a single host, it can monitor the entire shared network segment. Once intrusion and probing activities are detected, various real-time alert methods, such as sending alarm information to the system log, alert files, or console screen, are available. Snort can detect various network attacks and features packet capture, analysis, and log recording functionalities. Compared to expensive and large commercial products, Snort has many advantages such as small system size, easy installation, easy configuration, flexible rules, and plug-in (extension) expansion.
Components
Snort mainly consists of a packet protocol analyzer, intrusion detection engine, logging, and alerting modules. The protocol analyzer’s role is to parse the protocol stack packets for submission to the intrusion detection engine for rule matching. The intrusion detection engine matches packet characteristics based on rule files, triggering specific responses when packet characteristics meet detection rules. Logging records parsed packets into text or Tcpdump binary format for log files, with text format facilitating packet analysis and binary format improving recording speed. Alert information can be sent to system logs or sent to alert files in either text or Tcpdump binary formats; it also allows selecting to disable alert operations. Alert information recorded to alert files can be in comprehensive or quick mode, with comprehensive alerts recording all fields in the packet header and alert information, while quick alerts record only some fields of the packet header information.
Build
rpm Package Installation
Here we use version 2.9.16-1 as an example. For the latest version, visit the official website https://www.snort.org
yum install -y https://www.snort.org/downloads/snort/snort-2.9.16-1.centos7.x86_64.rpmDuring snort installation, an error might occur: missing libnghttp2.so.14()(64bit), use the following command to install the necessary dependencies
yum install -y epel-release -yyum install -y nghttp2Test: snort, if no error occurs, the installation is successful.
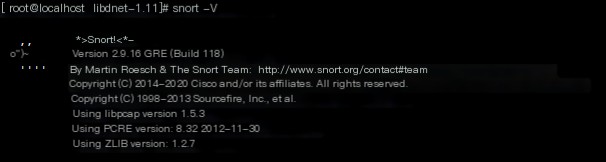 >
>
If an error occurs snort: error while loading shared libraries: libdnet.1: cannot open shared object file: No such file or directory use the following command to install the necessary dependencies
wget http://prdownloads.sourceforge.net/libdnet/libdnet-1.11.tar.gztar -xzvf libdnet-1.11.tar.gz./configuremake && make installSource Code Compilation and Installation on CentOS
Install dependencies
yum install -y gcc flex bison zlib zlib-devel libpcap libpcap-devel pcre pcre-devel libdnet libdnet-devel tcpdump openssl openssl-develwget https://www.snort.org/downloads/snort/daq-2.0.6.tar.gzwget https://www.snort.org/downloads/snort/snort-2.9.15.tar.gztar xvzf daq-2.0.6.tar.gzcd daq-2.0.6./configure && make && sudo make installcd ../wget http://luajit.org/download/LuaJIT-2.0.5.tar.gztar xvzf LuaJIT-2.0.5.tar.gzcd LuaJIT-2.0.5make installtar xvzf snort-2.9.15.tar.gzcd snort-2.9.15./configure --enable-sourcefire && make && sudo make installTest: snort, if no error occurs, the installation is successful.
Configuration
Before using snort, it needs to be configured according to the protected network environment and security policies, mainly including network variables, preprocessors, output plugins, and rule sets, located in the snort configuration file snort.conf in etc. You can open it with any text editor. Except for the internal network environment variable HOME_NET, in most cases, the default configuration of snort.conf can be used.
Since we do not want to run snort with root privileges, we need to create a relevant user. We also need to create working directories.
# Create the snort user and group:sudo groupadd snortsudo useradd snort -r -s /sbin/nologin -c SNORT_IDS -g snort# Create the Snort directories:sudo mkdir /etc/snortsudo mkdir /etc/snort/rulessudo mkdir /etc/snort/rules/iplistssudo mkdir /etc/snort/preproc_rulessudo mkdir /usr/local/lib/snort_dynamicrulessudo mkdir /etc/snort/so_rules# Create some files that store rules and IP listssudo touch /etc/snort/rules/iplists/black_list.rulessudo touch /etc/snort/rules/iplists/white_list.rulessudo touch /etc/snort/rules/local.rulessudo touch /etc/snort/sid-msg.map# Create our logging directories:sudo mkdir /var/log/snortsudo mkdir /var/log/snort/archived_logs# Adjust permissions:sudo chmod -R 5775 /etc/snortsudo chmod -R 5775 /var/log/snortsudo chmod -R 5775 /var/log/snort/archived_logssudo chmod -R 5775 /etc/snort/so_rulessudo chmod -R 5775 /usr/local/lib/snort_dynamicrules# Change Ownership on folders:sudo chown -R snort:snort /etc/snortsudo chown -R snort:snort /var/log/snortsudo chown -R snort:snort /usr/local/lib/snort_dynamicrulesMove configuration files
cd ~/snort_src/snort-2.9.16/etc/sudo cp *.conf* /etc/snortsudo cp *.map /etc/snortsudo cp *.dtd /etc/snortcd ~/snort_src/snort-2.9.16/src/dynamic-preprocessors/build/usr/local/lib/snort_dynamicpreprocessor/sudo cp * /usr/local/lib/snort_dynamicpreprocessor/sudo sed -i "s/include \$RULE\_PATH/#include \$RULE\_PATH/" /etc/snort/snort.confModify the configuration file, change HOME_NET to the CIDR address of your computer
sudo vim /etc/snort/snort.confipvar HOME_NET 10.0.0.0/24...104var RULE_PATH /etc/snort/rulesvar SO_RULE_PATH /etc/snort/so_rulesvar PREPROC_RULE_PATH /etc/snort/preproc_rulesvar WHITE_LIST_PATH /etc/snort/rules/iplistsvar BLACK_LIST_PATH /etc/snort/rules/iplists...564include $RULE_PATH/local.rules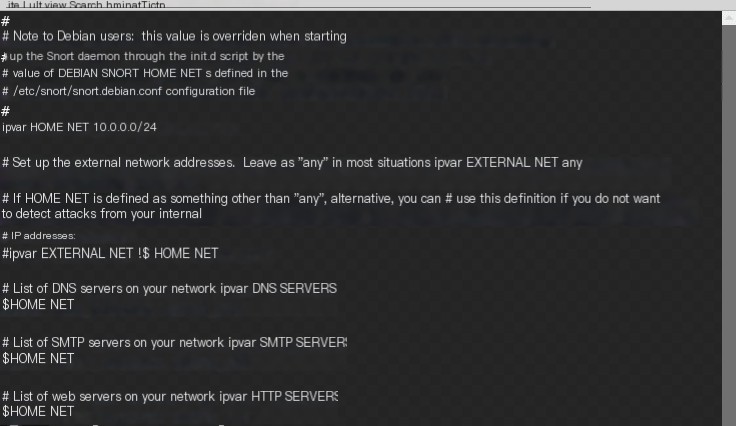
Test Usage
vim /etc/snort/rules/local.rulesalert icmp any any -> $HOME_NET any (msg:"ICMP test detected"; GID:1; sid:10000001; rev:001; classtype:icmp-event;)sudo /usr/local/bin/snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i eth0Run, at this time, when other machines Ping the Snort host, you can see log information
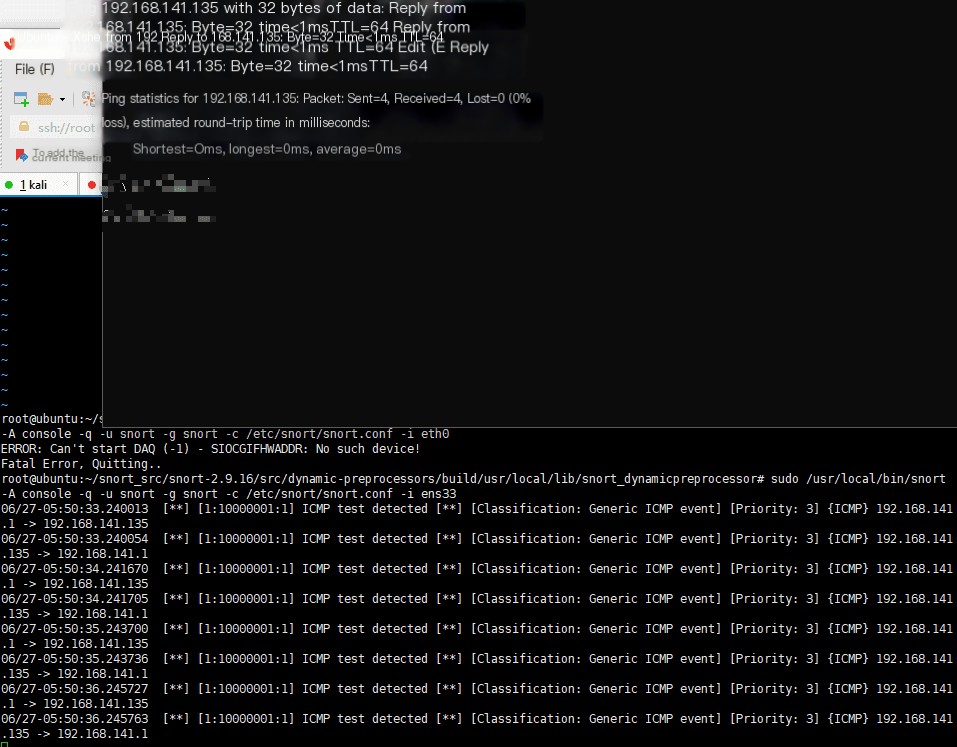
Of course, snort can also directly read pcap packages
sudo /usr/local/bin/snort -r foo.pcapalerts mechanism
When an intrusion is occurring or attempting to occur, the IDS system will issue an alert message to notify the system administrator. If the console is on the same machine as the IDS system, the alert message will display on the monitor and may be accompanied by a sound prompt. If it is a remote console, the alert will be transmitted to the administrator via built-in methods in the IDS system (usually encrypted), SNMP (Simple Network Management Protocol, usually unencrypted), email, SMS (Short Message Service), or a combination of these methods.
Snort uses rules to issue alert messages, and there are three types of rules provided by Snort’s official website
- Community rules: can be downloaded and used directly without registration or purchase
- Registered rules: require registration to download
- Subscriber rules: require registration and purchase
Visit the official website https://www.snort.org/ to download rules
After downloading, extract to the respective directory
cd /etc/snort/rules/wget https://www.snort.org/downloads/community/community-rules.tar.gz -O community-rules.tar.gztar -xvf community-rules.tar.gzmv /etc/snort/rules/community-rules/community.rules /etc/snort/rules/sudo vim /etc/snort/snort.confinclude $RULE_PATH/community.rulesWe can also customize rules, for instance, the following rule is used to detect PLC inject attacks
alert tcp any any -> $any 502 (msg:”plcinject”; content:”|d0 9d 00 00 00 06 01 03 00 80 00 01|”; sid:001111111; GID:001; priority:0;)Conclusion
This article introduces the installation and configuration of snort in a Linux environment, and also tests rule writing and loading. With the rise of IoT and smart home devices, the importance of IDS and IPS systems is self-evident. Open-source IDS systems are easy to install and use, making them very suitable for deployment in personal or small networks. In the next article, another open-source IDS product, Suricata, will be introduced.


