What is Computer Intrusion Forensics
Computer forensics refers to the process of employing principles and methods in computer science and technology to obtain evidence related to computers to prove an objective fact. It involves the identification, collection, preservation, analysis, archiving, and presentation of computer evidence in court.
Bro Basic Introduction
Bro is a passive open-source traffic analyzer. It is mainly used for security monitoring of all suspicious behavior traffic on the link, providing a comprehensive platform for network traffic analysis, particularly focusing on semantic security monitoring. Although often compared to traditional intrusion detection/prevention systems, Bro adopts a completely different approach, offering users a flexible framework that helps to customize and perform deep monitoring far beyond the capabilities of traditional systems.
Bro aims to search for attack activities and provide background information and usage patterns. It can organize all devices in the network into visual graphs, delve into the network traffic, and inspect network data packets. It also offers a more general-purpose traffic analysis platform.
We study the technology of computer intrusion forensic analysis based on Bro through an experiment.
Experiment Objective
The practical example is pcap attack trace, where the IP of the attacking host is obtained by analyzing the extract file and log file within the traffic packets.
Experiment Process
Install Bro Tool
apt-get install bro bro-auxExperimental Environment
Configure Bro
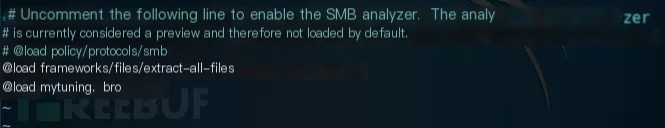
Edit /etc/bro/site/local.bro and append two new configuration lines at the end of the file
@load frameworks/files/extract-all-files # Extract all files@load mytuning.broCreate a new file mytuning.bro under the /etc/bro/site/ directory and add:
Reason: Generally, Bro’s event engine discards packets with invalid checksums. If you want to analyze locally generated/captured traffic on the system, all sent/captured packets will have bad checksums, as they have not been computed by the NIC; therefore, these packets will not be analyzed in Bro policy scripts, so it should be set to ignore checksum validation.
Download pcap Package (Experiment Objective)
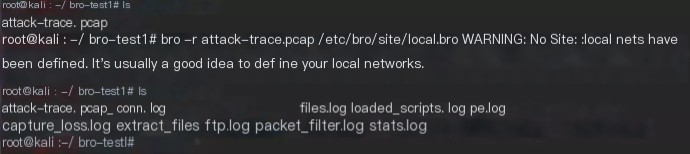
wget https://www.honeynet.org/files/attack-trace.pcap_.gzDecompress and Use Bro to Automatically Analyze the pcap Package
bro -r attack-trace.pcap_ /etc/bro/site/local.broA warning message appears: WARNING: No Site::local_nets have been defined. It’s usually a good idea to define your local networks. For this intrusion forensic experiment, it has no impact.
To resolve the above warning, edit mytuning.bro and add a line for variable definition:
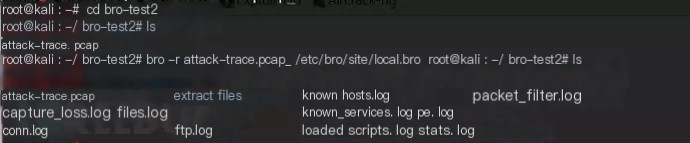
redef Site::local_nets = { 192.150.11.0/24 };Adding this line defining the local network IP address range will add two additional log files in this experiment, reporting that local network IPs and associated known service information were found in the current traffic (packet file).
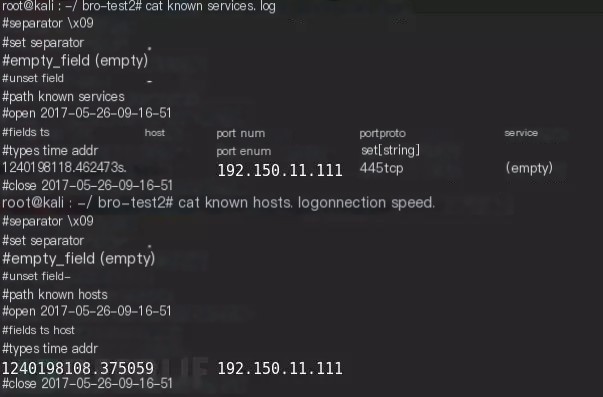
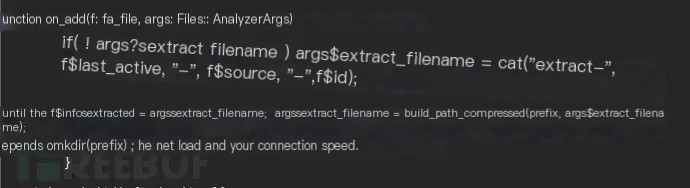
By reading the source code of /usr/share/bro/base/files/extract/main.bro, it can be understood that the string on the rightmost side of the filename FHUsSu3rWdP07eRE4l is the unique identifier in files.log.
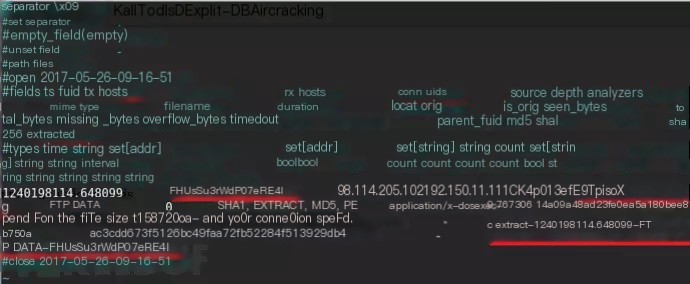
Upon checking files.log, it can be found that the file was extracted from an FTP session, and the traffic’s conn_uids is CK4p013efE9TpisoXg.
By viewing conn.log, locate the five-tuple information for the id CK4p013efE9TpisoXg, and determine that the PE file originated from a host at the IPv4 address 98.114.205.102.
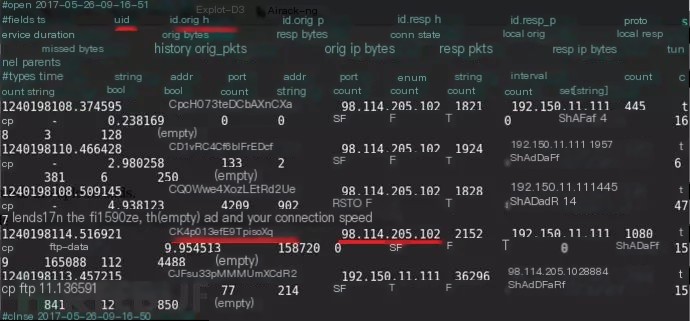
Tips for Displaying Log Files
bro-cut ts uid id.orig_h id.resp_h proto < conn.log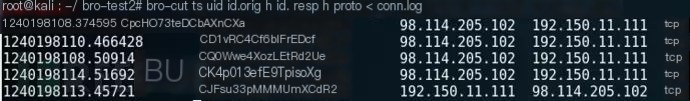
Conclusion
This experiment demonstrates that Bro is highly effective in computer forensics. It can capture the traces left by intruders through pcap packages.
However, it differs from ordinary network traffic analysis tools.
|
Bro |
Snort |
Wireshark & Tshark | |
|---|---|---|---|
|
Advantages |
Advanced Anomaly Detection |
Regular Expression, Signature |
Traffic Analysis |
|
Data Focus |
Connection Object, Events |
Packets, Data Streams |
Protocol Analysis |
|
Programmability |
Bro DSL |
No |
No |
|
Real-time or Replay |
Both |
Both |
Pcap Replay |
|
Application Layer |
Application Layer Automation, Dynamic Data Distribution |
Automation, OpenAppID |
Manual, Analyzer |
Besides the functions demonstrated in this experiment, Bro offers numerous critical advanced features, such as implementing application layer protocol functionality in the event generation engine. In computer forensic analysis, it can efficiently analyze network traffic to identify traces of intrusion, assisting managers in accountability and reducing losses.
Bro is a valuable tool for developers of network intrusion detection systems and a choice for users with certain network management experience to customize attack detection features.
References
https://www.sneakymonkey.net/2017/03/03/pcap-file-extraction
https://www.bro.org/sphinx/script-reference/proto-analyzers.html?highlight=arp#bro-connsize


