**Problem Description:** The content covers TCP checksum issues.
When using Wireshark to capture packets, it was found that most of the packets coming from 10.81.2.92 were marked as abnormal packets (with IPv4 and TCP checksum enabled).
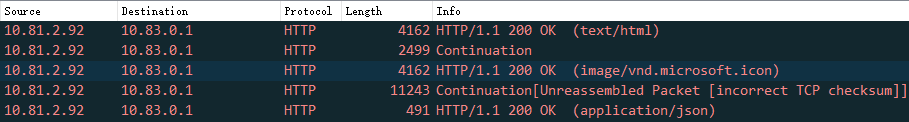
Upon analyzing the packets below, it was discovered that the length of the HTTP packet (i.e., TCP payload) was far larger than the actual MSS size, as shown in the below image, which is 4126.

Solution:
Problem Analysis:
Currently, many network cards support IP fragmentation and checksum computation for protocols like IP/TCP/UDP to reduce kernel-level processing (lowering CPU load). When the protocol layer detects that the network card supports these features, it delegates the processing to the network card. As mentioned above, checksums are normally handled by the corresponding protocol layer, but when enabled on the network card, they are deferred to the network card for processing, which then directly sends them after processing. This explains why the checksum of packets captured by Wireshark is marked as incorrect. Similarly, TCP selects packets not larger than the sliding window (which may exceed MSS) and assigns them to the network card for fragmentation processing. The command ethtool -k can be used to view the features supported by the network card.



