Set up an environment that supports Bluetooth packet capture by ensuring you have the necessary hardware and software tools. Install a Bluetooth adapter compatible with your system and
Previously, we introduced data packets and protocol layers. Next, we will use Ubertooth One to capture Bluetooth packets during communication processes.

(1) Installing Libraries
Code language: JavaScriptCopy
apt-get install python-software-propertiesadd-apt-repository ppa:pysideapt-get updateapt-get install libnl-dev libusb-1.0-0-dev pyside-tools(2) Installing libbtbb
Code language: JavaScriptCopy
wget https://github.com/greatscottgadgets/libbtbb/archive/2015-09-R2.tar.gz -O libbtbb-2015-09-R2.tar.gztar xf libbtbb-2015-09-R2.tar.gzcd libbtbb-2015-09-R2mkdir buildcd buildcmake ..makesudo make install(3) Installing Ubertooth
Code language: JavaScriptCopy
wget https://github.com/greatscottgadgets/ubertooth/releases/download/2015-09-R2/ubertooth-2015-09-R2.tar.xz -O ubertooth-2015-09-R2.tar.xztar xf ubertooth-2015-09-R2.tar.xzcd ubertooth-2015-09-R2/hostmkdir buildcd buildcmake ..makesudo make installsudo ldconfig(4) Installing Wireshark
Code language: JavaScriptCopy
sudo apt-get install checkinstallwget https://www.wireshark.org/download/src/wireshark-2.0.3.tar.bz2tar -xvf wireshark-2.0.3.tar.bz2cd wireshark-2.0.3./configuremakemake install(5) Installing Kismet
Code language: JavaScriptCopy
wget https://kismetwireless.net/code/kismet-2013-03-R1b.tar.xztar xf kismet-2013-03-R1b.tar.xzcd kismet-2013-03-R1bln -s ../ubertooth-2015-09-R2/host/kismet/plugin-ubertooth ../configuremake && make pluginssudo make suidinstallsudo make plugins-install(6) Installing BLE Decryption Tool Crackle
Crackle (open-source project address)
Code language: JavaScriptCopy
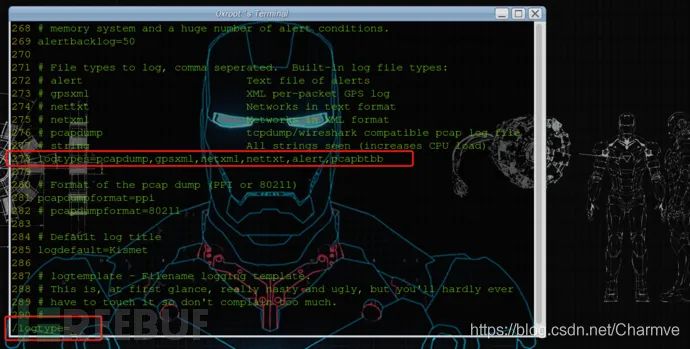
git clone https://github.com/mikeryan/crackle.gitcd cracklemakemake installFind Kismet’s configuration file kismet.conf and add “pcapbtbb” to the logtypes= section inside kismet.conf
Sniffing and Scanning
(1) Spectool
spectool_curses
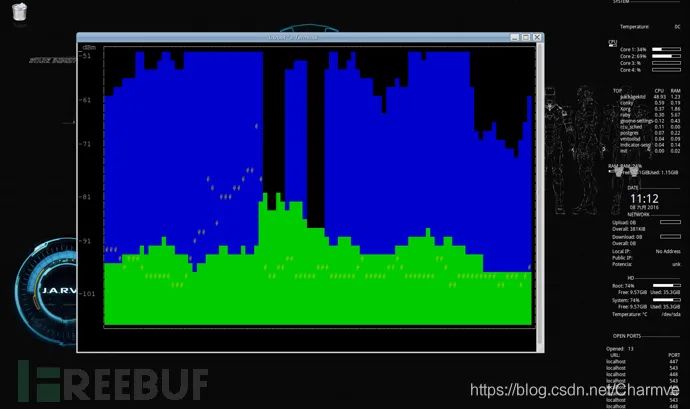
spectool_gtk scans nearby signals and displays them on the spectrum:
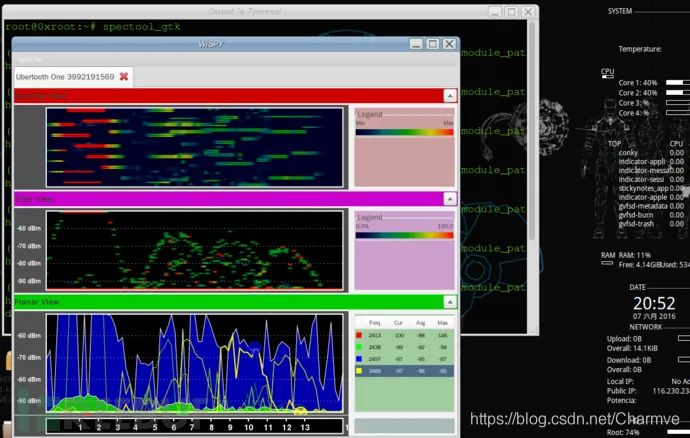
spectool_raw RAW is interpreted in Chinese as “raw materials” or “untreated things”. It presumably shows the raw signal data captured by the device:
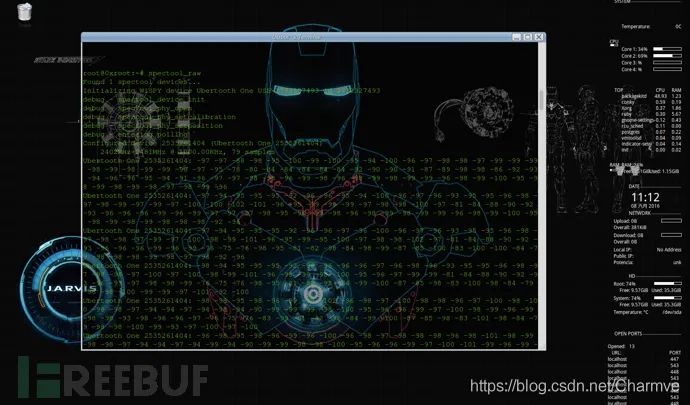
spectool_net makes Ubertooth One act as a “hardware server” and listen on TCP: port 30569, allowing any PC within the local network to communicate with the host to share devices via the Ubertooth host IP + 30569. Connection method: On another host terminal, execute: spectool_gtk
—> Select Open Network Device —> Enter IP, port.

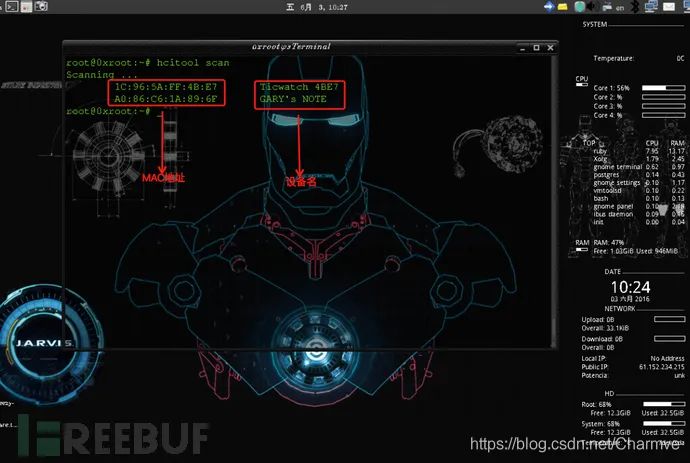
(2) hcitool
Code language: JavaScriptCopy
root@0xroot:~# hcitool --helphcitool - HCI Tool ver 4.99Usage: hcitool [options] hcitool scan: Scans for nearby Bluetooth devices
hcitool lescan: Scans for nearby low-energy Bluetooth devices
(3) gatttool
Code language: JavaScriptCopy
root@0xroot:~# gatttool -hUsage: gatttool [OPTION...]Help Options: -h, --help Show help options --help-all Show all help options --help-gatt Show all GATT commands --help-params Show all Primary Services/Characteristics arguments --help-char-read-write Show all Characteristics Value/Descriptor Read/Write argumentsApplication Options: -i, --adapter=hciX Specify local adapter interface -b, --device=MAC Specify remote Bluetooth address -m, --mtu=MTU Specify the MTU size -p, --psm=PSM Specify the PSM for GATT/ATT over BR/EDR -l, --sec-level=[low | medium | high] Set security level. Default: low -I, --interactive Use interactive modeCode language: JavaScriptCopy
gatttool -b 1C:96:5A:FF:4B:E7 -I[ ][1C:96:5A:FF:4B:E7][LE]> helphelp Show this helpexit Exit interactive modequit Exit interactive modeconnect [address] Connect to a remote devicedisconnect Disconnect from a remote deviceprimary [UUID] Primary Service Discoverycharacteristics [start hnd [end hnd [UUID]]] Characteristics Discoverychar-desc [start hnd] [end hnd] Characteristics Descriptor Discoverychar-read-hnd [offset] Characteristics Value/Descriptor Read by handlechar-read-uuid [start hnd] [end hnd] Characteristics Value/Descriptor Read by UUIDchar-write-req Characteristic Value Write (Write Request)char-write-cmd Characteristic Value Write (No response)sec-level [low | medium | high] Set security level. Default: lowmtu Exchange MTU for GATT/ATT[ ][1C:96:5A:FF:4B:E7][LE]>(4) ubertooth-scan
Code language: JavaScriptCopy
root@0xroot:~# ubertooth-scan --helpubertooth-scan: invalid option -- '-'ubertooth-scan - active(bluez) device scan and inquiry supported by UbertoothUsage: -h this Help -U<0-7> set ubertooth device to use -s hci Scan - perform HCI scan -t scan Time (seconds) - length of time to sniff packets. [Default: 20s] -x eXtended scan - retrieve additional information about target devices -b Bluetooth device (hci0)ubertooth-scan -s
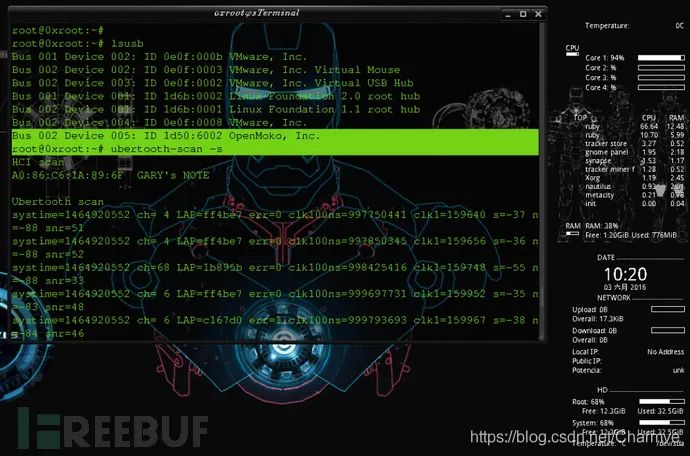
(5) ubertooth-btle
Code language: JavaScriptCopy
ubertooth-btle - passive Bluetooth Low Energy monitoringUsage: -h this help Major modes: -f follow connections -p promiscuous: sniff active connections -a[address] get/set access address (example: -a8e89bed6) -subertooth-btle -f -c test.pcap Capture & save to local
Using this command, we can save captured packets on the device locally. Once done, they can be imported into Wireshark for packet and protocol analysis.
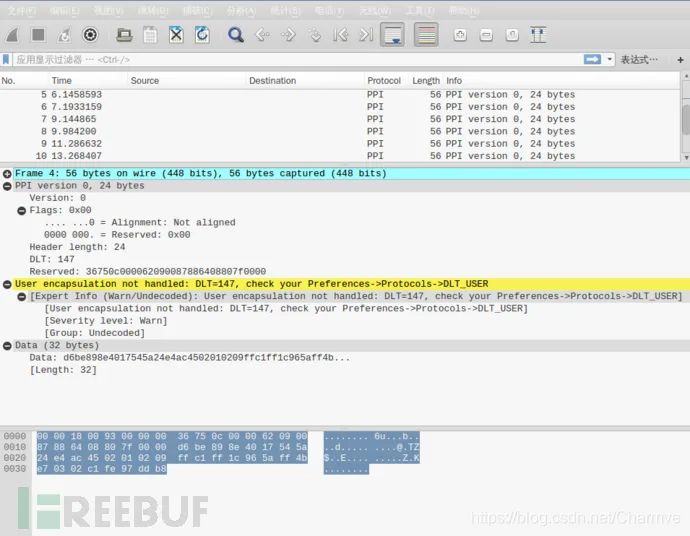
Importing Bluetooth packets sniffed by Wireshark needs to be processed for correct viewing, otherwise, analysis might not be possible:
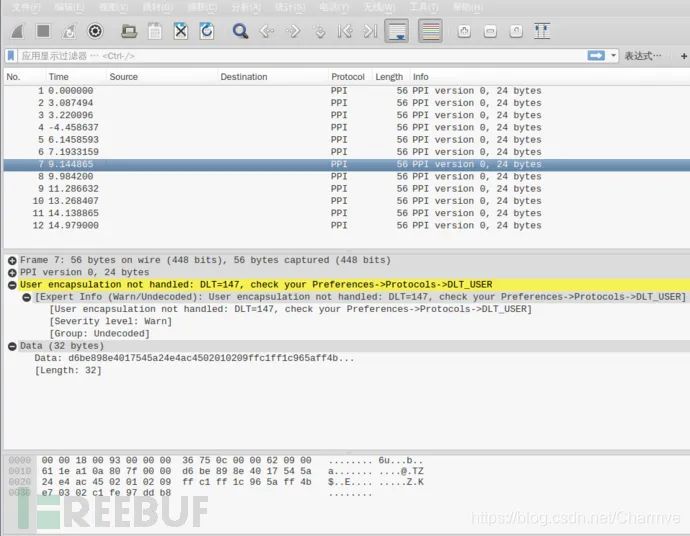
Edit → Preferences → Protocols → DLT_USER → Edit → New
Enter btle in the payload protocol
Use rules to filter packets: Refer to Capturing BLE in Wireshark
Code language: JavaScriptCopy
btle.data_header.length > 0 || btle.advertising_header.pdu_type == 0x05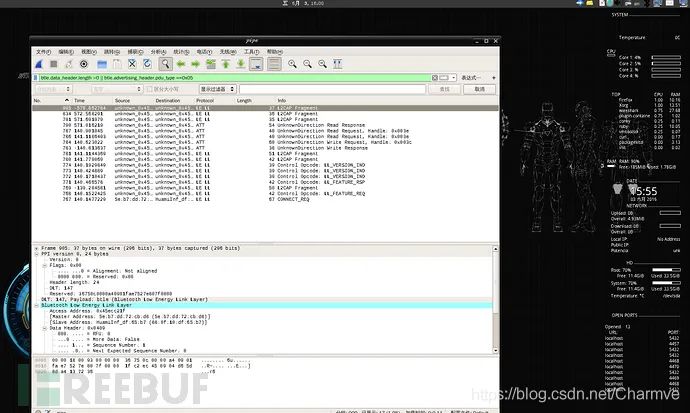
(6) Crackle
If you’ve captured enough packets, especially btsmp, you can proceed to use Crackle to crack tk and ltk:
Code language: JavaScriptCopy
crackle -i Decrypt packets and save the decrypted packets separately:
Code language: JavaScriptCopy
crackle -i -o crackle -i -o -l 


