1. Introduction
In the previous article, we used Wireshark to troubleshoot and pinpoint TCP connection issues and retransmission problems, including the keyword duplicate ACKs.
TCP has another common issue — duplicate ACKs and fast retransmissions, and in this article, we’ll look at how to troubleshoot and identify this problem using Wireshark.
2. Fast Retransmission Mechanism
The timeout retransmission mechanism helps TCP avoid packet loss due to network anomalies, among other reasons. However, the timeout retransmission mechanism also comes with many problems, such as:
Thus, TCP gave rise to the fast retransmission mechanism.
As soon as the receiver receives a packet with a sequence number greater than the expected one, it indicates out-of-order packets. In this case, it is not necessary to wait for a timeout but instead immediately duplicates the ACK for the currently expected sequence number.
When the sender receives N duplicate ACKs, meaning that it receives an extra ACK for the same sequence number for the N+1th time, it considers the packet lost and immediately retransmits it.
Compared to the timeout retransmission mechanism, the fast retransmission mechanism changes the time-triggered mechanism to an event-triggered mechanism. The time taken for the receiver to receive three packets is typically much shorter than the retransmission timeout. Additionally, the already received subsequent packets are not cleared after a fast retransmission but will ACK the subsequent unreceived sequence numbers.
The diagram below shows this process:
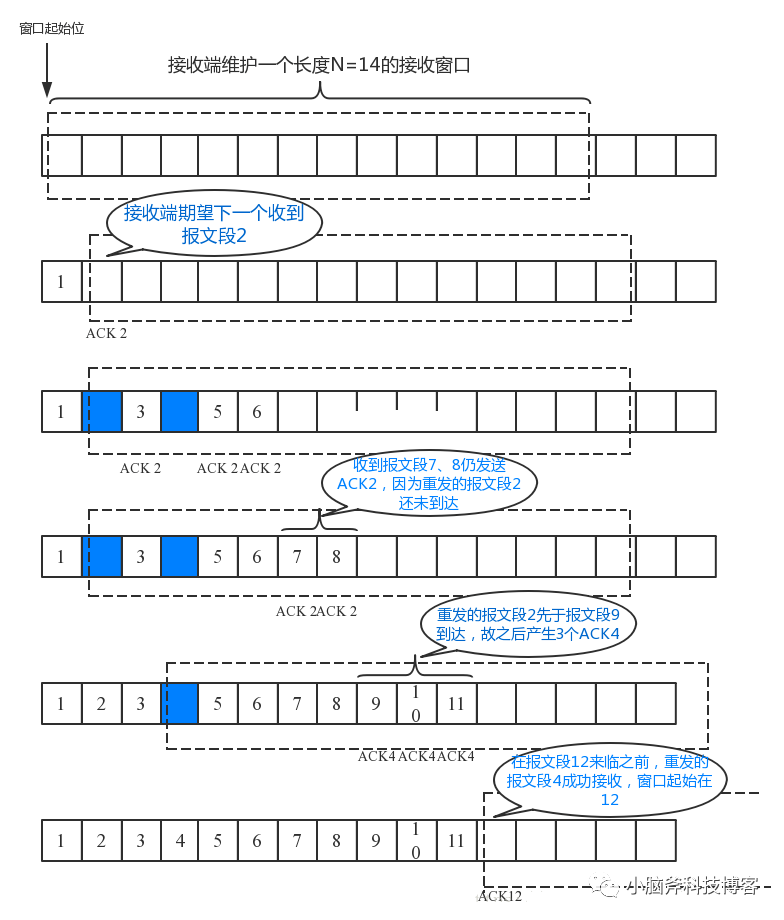
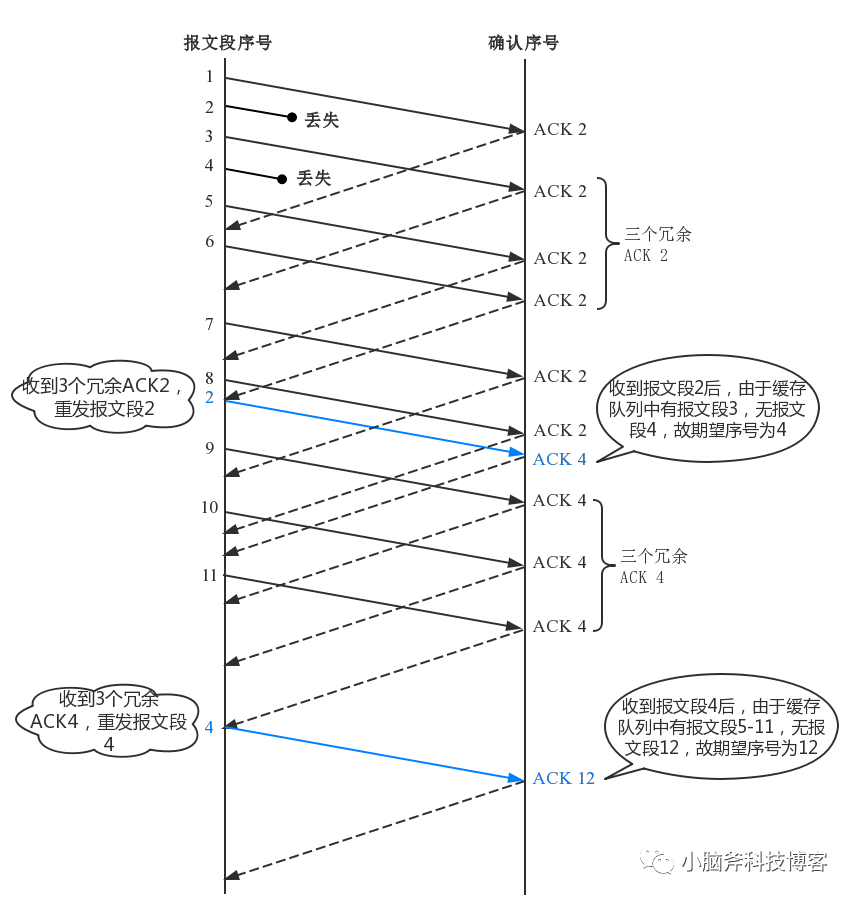
Accompanied by the fast recovery algorithm, after a fast retransmission occurs, the sender will immediately halve the sending rate or even reduce it to the minimum, significantly impacting communication efficiency.
However, occasional TCP fast retransmissions are acceptable due to the unordered nature of IP packets. If fast retransmissions exceed 1%, attention is needed.
3. Troubleshooting TCP Fast Retransmission with Wireshark
3.1 Fast Retransmission in Wireshark
In Wireshark, the keyword for duplicate ACKs is “TCP Dup ACK”, and for fast retransmission, it is “TCP Fast Retransmission”.
The following image shows an example of a fast retransmission occurring after 51 duplicate ACKs:
3.2 Problem Troubleshooting
Fast retransmissions are caused by out-of-order packets or packet loss, typically due to network latency or jitter.
It is advisable to check the buffer and CPU load status at each node in the server or network link or switch to a different network environment if possible.
4. Identifying Out-of-Order Packets with Wireshark
As mentioned earlier, multiple consecutive duplicate ACKs will trigger the TCP fast retransmission mechanism. However, even if the trigger count is not reached, duplicate ACKs might also indicate a network anomaly.
4.1 Phenomenon in Wireshark
There are three types of out-of-order packet phenomena in Wireshark:
As shown in the figure:
4.2 Problem Identification
If you notice this phenomenon while capturing packets with Wireshark, it may be due to Wireshark itself. If you only see out-of-order packets but no response to potentially lost or out-of-order packets, it actually might not be a problem.
4.2.1 Wireshark Capturing Issues
4.2.2 Network Latency
In TCP transmission, if the IP datagrams encapsulating TCP segments take different routing paths, out-of-order issues may occur. You can use the traceroute tool to check routing conditions and determine whether a particular routing link’s transmission efficiency is problematic.
For internal networks, you can configure SNMP traps on routers to enable network management software to automatically alert you.
References
https://datatracker.ietf.org/doc/html/rfc793
《Network Analysis Using Wireshark Cookbook》



