Unlike viruses, Trojan horses usually do not infect documents. Instead, they are often used to gain backdoor access, steal passwords, and retrieve important files. Trojans can also be employed to track and monitor computer activity, control systems, view or edit information, and perform other operations. They are highly concealed, sudden, and offensive in nature. Due to their stealthy behavior, users often realize they have been infected only after noticing stolen passwords or missing confidential documents. Below is a guide on Trojan horse detection, including how to check if your machine is infected, as well as steps to remove and protect against Trojans.
1. Detects Trojan (BackDoor.Win32.Pigeon.gno)
The communication between client and server of Trojan is usually with TCP, UDP and ICMP protocol. Sax2 from Ax3soft is based on the analysis of protocol and can accurate tracking network connecting conversation and reorganize the TCP / IP data of the communication. When it detect that your network in the risk of Trojans, it will immediately suspended or interference with communications of Trojan to protect your network from attack. Why not have a try? Sax2 will immediately upgrade it’s Security Policy Knowledge Base after finished installation. Below will introduce how to use Sax2 to detect whether your system has infected of the Trojan – gray pigeons.
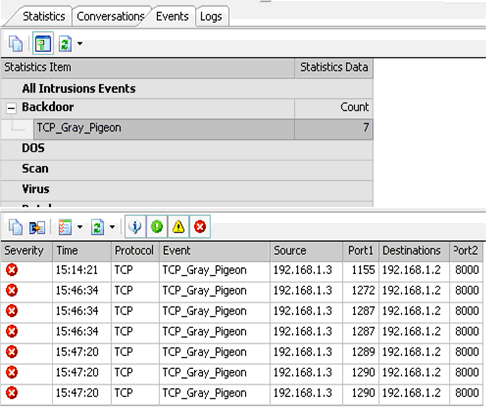
First of all, launch and run Sax2, switch to “EVENTS” pages. If there is gray pigeons communication in your network, Sax2 will immediately report and interrupt Trojan communications. See the picture:
2. Remove Trojan
According to the detected suspicion address listed the Event log you can find the computer virus gray pigeons. In the previous picture, the source address “192.168.1.3” is the Gray Pigeon in the Network Address.
http://www.366tian.net/soft/data/soft/875.html
3. How to prevent the gray pigeons Trojan infection
A. Never execute programs unless they are from a trusted source.
B. Never open e-mail attachments unless you know who they’re from, especially attachments with the extensions .exe, .ink and .vbs.
C. Update your antivirus and security software on a regular basis.
D. Install patches and security updates for your Operating System and application programs as they become available.
E. Beware of homemade CDs and floppy disks. If you plan to use these disks in your computer, scan them with your anti-virus software first.
F. Never accept programs transferred by instant messaging applications.