Intrusion Detection Systems can be categorized into two types: Network Intrusion Detection Systems (Network IDS, NIDS) and Host Intrusion Detection Systems (Host IDS, HIDS). NIDS monitors network traffic, while HIDS monitors system activities on a host. This article will share popular open-source Network IDS used in the open-source community and by major security companies. I have also used and studied tools such as Suricata, Snort, Zeek/Bro, OSSEC, and Security Onion in my work for security analysis and source code reading. In the next post, I will discuss open-source intrusion detection systems for hosts. The following sections will detail how to use these tools in real-world projects and understand their principles through source code analysis.
What is an Intrusion Detection System?
An Intrusion Detection System (IDS) is a security tool used to monitor abnormal activities and attacks in computer networks and systems. IDS can be divided into two types: Network Intrusion Detection Systems (Network IDS, NIDS) and Host Intrusion Detection Systems (HIDS). NIDS monitors network traffic, while HIDS monitors system activities on a host.
Purpose of Network IDS (Intrusion Detection Systems)
The purpose of an intrusion detection system is to help security teams detect and respond to security incidents in networks and systems promptly. This includes malware, intruder attacks, data breaches, etc. IDS can detect abnormal activities such as port scanning, malware propagation, brute force attacks, etc., to take timely measures to protect the organization’s security.
Principles of Intrusion Detection Systems
The principle of an intrusion detection system is to detect abnormal activities and attacks by monitoring network traffic or system activities on a host. IDS uses a series of rules and algorithms to analyze network traffic and system activities to detect and respond to security incidents promptly.
Below are useful open-source network intrusion detection systems:
1. Suricata

Suricata (NIDS) is an open-source, fast, highly stable, high-performance network intrusion detection system developed by the Open Information Security Foundation. The Suricata engine can be used to monitor network traffic, detect malicious activities, and provide real-time intrusion detection, inline intrusion prevention, and network security monitoring. Suricata consists of several modules such as capture, collection, decoding, detection, and output. It captures traffic in a flow before decoding, which is highly optimized. Unlike Snort, however, it configures separate processes after capturing and specifying how flows are separated among processors.
Suricata, based on rules and signatures, can detect various network attacks, including port scanning, vulnerability exploitation, malware propagation, etc. Suricata also supports custom rules and scripts to meet specific security needs.
Suricata supports IP blacklists and whitelists to filter out unnecessary traffic from being detected.
Suricata’s principle is to monitor network traffic and use rules and signatures to detect malicious activities. Suricata uses a multi-threaded and scalable architecture that can handle high-speed network traffic.
Advantages
Network traffic processing at OSI Model Layer 7 enhances the ability to detect malware activities.
Automatically detects and analyzes IP, TCP, UDP, ICMP, HTTP, TLS, FTP, SMB, and FTP protocols, applicable to all protocols.
High performance, advanced features include multi-threading, GPU acceleration, and scalable architecture.
Supports custom rules and scripts, high flexibility.
Supports IP blacklists and whitelists, filtering unnecessary traffic.
Disadvantages
Complex operation (configuration and use), requires more system resources to complete functions, and requires a certain level of technical expertise.
High CPU and memory resource consumption.

Official website: https://suricata.io/
GitHub address: https://github.com/OISF/suricata
2. Snort

Snort (NIDS) is a free and open-source network intrusion detection and prevention tool (firewall system). Created by Martin Roesch in 1998, Snort’s main advantage is its ability to perform real-time traffic analysis and packet logging on networks to monitor network traffic and detect malicious activities. With features like protocol analysis, content searching, and various preprocessors, Snort is widely accepted for detecting worms, attacks, stealth port scans, buffer overflows, CGI attacks, SMB probes, OS fingerprinting attempts, and other malicious threats. It is supported by many hardware platforms and operating systems, such as Linux, OpenBSD, FreeBSD, Solaris, HP-UX, macOS, Windows, etc.
Snort can be configured in three main modes – sniffer, packet logger, and network intrusion detection. In sniffer mode, it reads packets and displays information on the console. In packet logger mode, packets are logged to disk. In intrusion detection mode, it monitors real-time traffic and compares it against user-defined rules.
Snort, based on rules and signatures, can detect various network attacks, including port scanning, vulnerability exploitation, malware propagation, etc. Snort also supports custom rules and scripts to meet specific security needs.
Snort’s principle is to monitor network traffic and use rules and signatures to detect malicious activities. Snort uses a multi-threaded and scalable architecture that can handle high-speed network traffic. Snort also supports IP blacklists and whitelists to filter out unnecessary traffic.
Advantages
Highly flexible and dynamic in deployment.
Strong community support for problem-solving and rapid development.
Mature stability, widely used.
Supports custom rules and scripts, high flexibility, easy to write intrusion detection rules.
Supports IP blacklists and whitelists, filtering unnecessary traffic.
Disadvantages
Packet processing speed can be slow.
Cannot detect signatures segmented across multiple TCP packets, which happens when packets are configured in a serial mode.
High CPU and memory resource consumption.
Official website: www.snort.org
GitHub address: https://github.com/snort3/snort3
Snort 3 is the next generation of Snort IDS (Intrusion Prevention System)
3. Zeek/Bro

Zeek (formerly known as Bro) is a passive, open-source network traffic monitoring tool developed by Vern Paxson. It can monitor network traffic and generate detailed logs and reports. Zeek can analyze network traffic, detect malicious activities like network scanning and vulnerability exploitation. Zeek includes a set of log files for recording network activities, such as HTTP sessions, including URIs, key headers, MIME types, server responses, DNS requests, SSL certificates, SMTP sessions, etc. It also provides sophisticated functionality for analyzing and detecting threats, extracting files from HTTP sessions, complex malware detection, software vulnerabilities, SSH brute force attacks, and verifying SSL certificate chains. Zeek supports custom scripts to meet specific security needs.
Zeek’s principle is to monitor network traffic, analyze network activities, and detect malicious behavior. Zeek uses custom scripts and plugins to extend its functionality. Zeek can generate detailed logs and reports to help security teams detect and respond to security incidents promptly.
Zeek’s architecture is divided into two layers:
Bro Event Engine: It analyzes real-time or recorded network traffic packets using C++ and generates events when anomalies occur in the network.
Bro Policy Scripts: These scripts process events to create actionable policies, such as sending emails, issuing alerts, executing system commands, or even calling emergency numbers.
Differences between security tools Zeek and Bro:
Zeek (formerly known as Bro) and Bro are the same tool, renamed to Zeek in 2018. Zeek is a network security monitoring tool used to monitor network traffic and generate detailed logs and reports. Zeek can analyze network traffic, detect malicious activities like network scanning and vulnerability exploitation.
Bro is an open-source network security monitoring tool used to monitor network traffic, analyze network activities, and detect malicious behavior. Bro can generate detailed logs and reports to help security teams promptly detect and respond to security incidents.
Advantages
Supports custom scripts and plugins, high flexibility, using scripting language allows users to set monitoring rules for each protected object.
Efficient in high-traffic networks, handling large network projects.
Able to perform deep traffic analysis and support multiple protocol analyzers.
Can generate detailed logs and reports for security team analysis.
Low CPU and memory resource consumption.
Disadvantages
Weaker capability in handling high-speed network traffic.
Limited detection capability for some advanced attack behaviors.
Official website: www.zeek.org
GitHub address: https://github.com/zeek/zeek
4. Security Onion
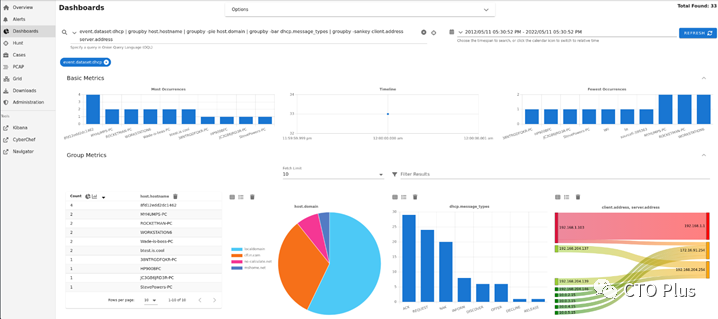
Security Onion can be used for monitoring network traffic, detecting malicious activity, and analyzing security incidents. Security Onion also supports real-time alerting and warning notifications to help security teams quickly identify and respond to security events.
The principle of Security Onion is to monitor network traffic and use multiple open-source security tools to detect malicious activity. Security Onion uses a client-server architecture, capable of monitoring multiple hosts, and sends alert information to a central server. It also supports custom rules and scripts to meet specific security needs.
**Core Features**
– Comprehensive packet capture.
– Network and host-based intrusion detection systems.
– Powerful analysis tools.
– Comprehensive packet capture: This is done using netsniff-ng, capturing all network traffic that Security Onion can see and storing it just like a storage solution. It acts like a network CCTV, providing all evidence of threats and malicious activities occurring on the network.
– Network and host-based IDS: Analyzes network or host systems and provides log and alert data for detected events and activities. Security Onion offers various IDS options like rule-driven IDS, analysis-driven IDS, HIDS, etc.
– Analysis tools: In addition to network data capture, Security Onion includes various tools such as Sguil, Squert, and ELSA to assist administrators in analysis.
**Advantages**
– Provides users with a highly flexible environment to adjust network security as needed.
– Integrates multiple open-source security tools, powerful functionality, and is composed of pre-installed sensor management tools, traffic analyzers, and packet sniffers, running without additional IDS/IPS software.
– Supports real-time alerting and warning notifications, promptly identifying and responding to security incidents.
– Supports custom rules and scripts, offering high flexibility.
**Disadvantages**
– Cannot be used as an IPS after installation and can only function as an IDS.
– Administrators need to learn various tools to use Security Onion effectively.
– Configuration files, apart from rules, cannot be backed up automatically.
– Configuration and use are quite complex, requiring a certain level of technical proficiency.
Official Website: https://securityonion.net/
GitHub Repository: https://github.com/Security-Onion-Solutions/securityonion
In summary, Suricata, Snort, and Zeek are all network security monitoring tools used to monitor network traffic and detect malicious activity. Their principle is to monitor network traffic and use rules and signatures to detect malicious activity. They all support custom rules and scripts to meet specific security needs. Their advantages and disadvantages vary, so the appropriate tool should be chosen based on the specific use case and requirements.


