2024’s Top 25 Host Intrusion Detection Software Recommendations – Essential for Cybersecurity
Introduction to Host Intrusion Detection Software
In IT security, Host Intrusion Detection Software (HIDS) acts as a fortified firewall, complemented by inline Intrusion Prevention Systems, to protect IP addresses from cyber attacks and anomaly-based detection. These tools are ideal for various operating systems, capable of detecting malware and anomalies, fortifying the application layer, defending against DDoS attacks, and using packet sniffers to scrutinize networks […]
With the plethora of intrusion detection software available in the market, choosing the right solution can be challenging. This article not only lists the top 25 recommended intrusion detection software for 2024 but also delves into their performance in different network environments, their capability to help businesses meet security compliance requirements, and real user case studies. Through comparative analysis and additional recommendations, we aim to provide a comprehensive guide to help you choose the intrusion detection software that best suits your needs.
Top 10 Host Intrusion Detection Software Candidates
Here are the top 10 software I selected from the 25 tools reviewed:
1. SolarWinds Security Event Manager— Best for Centralized Event Management 2. Ossec— Best for Log Management and Analysis 3. Check Point IDS— Best for Multi-layer Security Strategy 4. RSA NetWitness— Best for Real-time Event Response 5. FireEye Network Security— Best for Advanced Threat Intelligence 6. Juniper IDP— Best for Threat Detection Versatility 7. Cisco IDS— Best for Large Enterprise Environments 8. Zeek— Best for Network Traffic Analysis 9. Trend Micro Deep Discovery— Best for Targeted Attack Identification 10. Tripwire— Best for System Integrity Monitoring
What is Intrusion Detection Software?
Intrusion detection software is a next-generation tool specifically designed to monitor networks and systems for malicious activities or policy violations. It acts as a digital sentinel, alerting system administrators and security professionals to any suspicious behavior. Organizations use this software to protect digital assets, ensuring data integrity, confidentiality, and availability.
Performance in Network Environments When selecting intrusion detection software, understanding its performance in different network environments is crucial. Networks of varying sizes and complexities have different requirements for resource usage, response speed, and false positive rates. For instance, in large enterprise networks, tools like Cisco IDS excel due to their ability to efficiently handle high traffic volumes; whereas OSSEC might be more suitable for small to medium-sized businesses, offering lightweight yet effective protection. Performance testing and evaluation at different network levels are essential to ensure the chosen tool can operate efficiently in real-world environments.
Security Compliance with Host Intrusion Detection Software
In the current regulatory environment, whether Host Intrusion Detection Software supports industry-specific security compliance requirements is a critical criterion for businesses. For example, the healthcare industry needs to comply with HIPAA, while the financial sector must adhere to PCI-DSS and SOX standards. Trend Micro Deep Discovery’s advanced threat
User Cases or Industry Application Scenarios
FireEye Network Security was adopted by a large financial institution to detect and respond to complex cyber attacks, effectively protecting customer data; while Zeek is widely used in the education sector, helping universities defend against increasingly sophisticated cyber threats through deep network traffic analysis.
Best Intrusion Detection Software Reviews
1. SolarWinds Security Event Manager – Best for Centralized Event Management
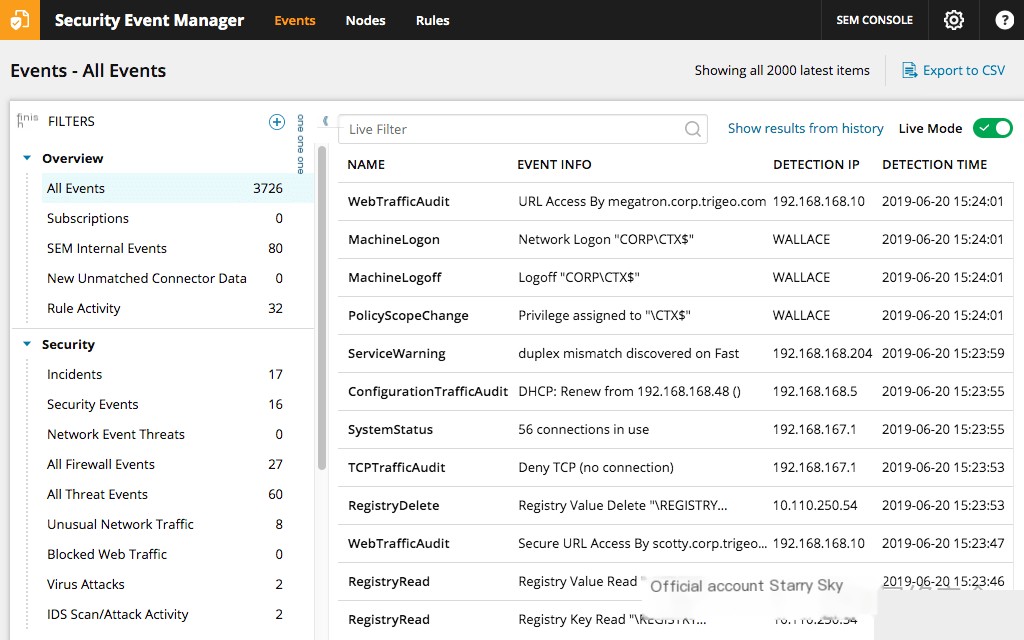
SolarWinds Security Event Manager (SEM) is designed to simplify the process of identifying and responding to security threats, audit failures, and operational issues. The tool stands out for its ability to centralize and interpret vast amounts of log data from multiple sources.
Why I chose SolarWinds Security Event Manager: During the evaluation process, SolarWinds SEM’s centralized event approach caught my attention. Based on my assessment, after comparing it with several other platforms, I determined that it offers a differentiated and efficient solution for organizations dealing with data sprawl. Its strong capabilities in centralized event management make it a valuable tool for many security professionals.
Key Features and Integration: SolarWinds SEM’s core strength lies in its log correlation technology, which quickly identifies potential issues by analyzing patterns. Additionally, its integration with other SolarWinds products provides organizations with a broader and more comprehensive view of their IT environment.
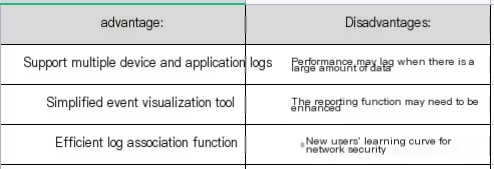
Pros and Cons:
2. OSSEC – Best for Log Management and Analysis
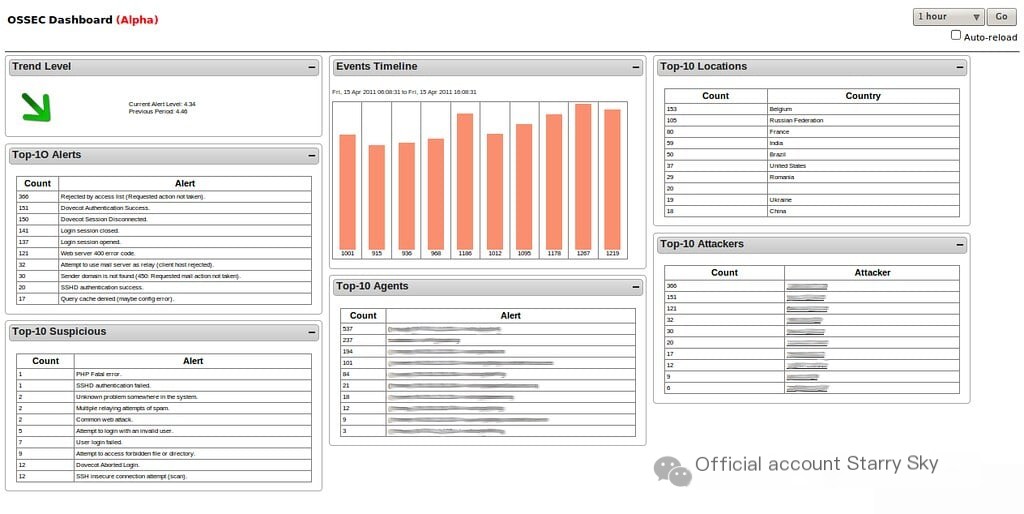
OSSEC is a powerful open-source host intrusion detection system that excels at parsing logs to uncover security events. It acts as a guardian of systems, providing precise log analysis, making it an indispensable tool for log management enthusiasts.
Why I chose OSSEC: When determining the best log analysis tool, OSSEC’s proficiency was evident. Its ability to correlate and analyze various log sources sets it apart. For those looking to delve deeply into log management and analysis, I believe OSSEC’s meticulous approach is superior.
Key Features and Integration: OSSEC offers detailed log analysis and alert mechanisms for potential security vulnerabilities. Its active response capabilities can automatically react to specific threats, streamlining security workflows. OSSEC’s integration with popular SIEM tools and visualization platforms ensures coherent data representation and actionable insights.
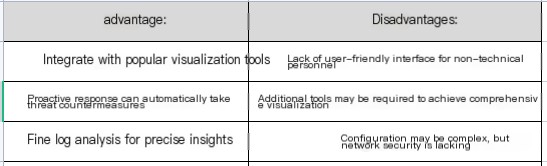
Pros and Cons:
3. Check Point IDS
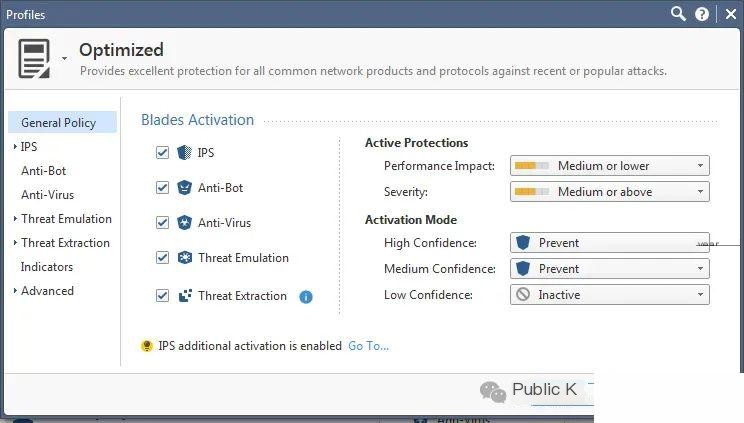
Check Point IDS is part of Check Point’s comprehensive security suite, emphasizing a multi-layered threat mitigation approach. This method ensures robust protection by addressing threats at various levels, regardless of their source or nature.
Why I chose Check Point IDS: After observing Check Point IDS’s holistic, multi-layer defense mechanism, I decided to choose it. Upon determining its performance and comparing it with other tools, I concluded that Check Point IDS is a commendable choice for organizations seeking a multi-layer security strategy.
Key Features and Integration: Check Point IDS’s threat defense technology is outstanding, including intrusion prevention, antivirus, and anti-bot modules. Additionally, its integration with Check Point security gateways extends the range of protection.
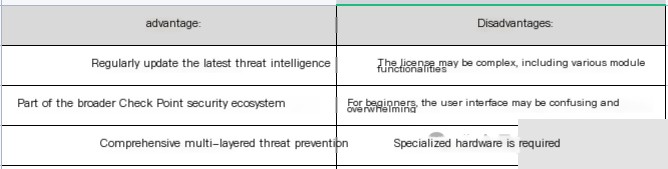
Pros and Cons:
4. RSA NetWitness – Best for Real-time Event Response
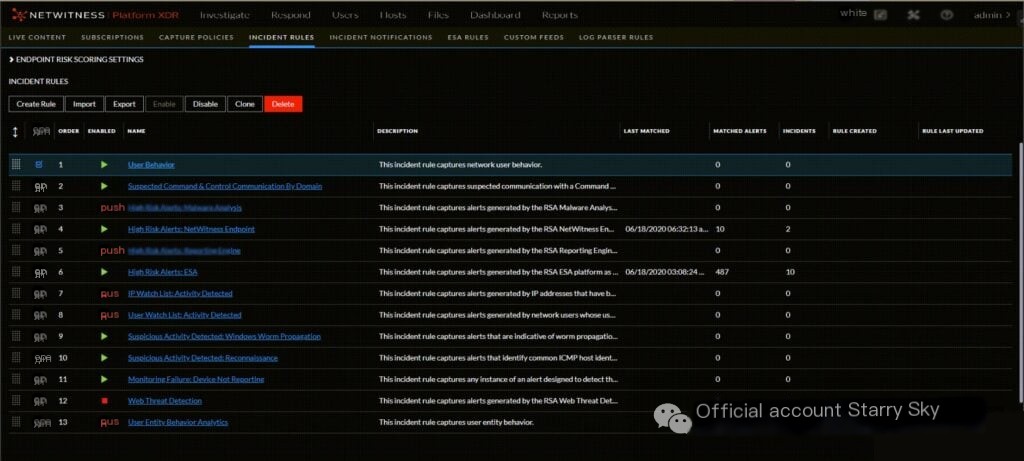
RSA NetWitness stands out for its exceptional ability to facilitate rapid responses to security breaches. Its design focuses on accelerating response times from the moment an incident is detected, making it perfectly suited for real-time event management needs.
Why I chose RSA NetWitness: The need for rapid incident response led me to evaluate several solutions, and RSA NetWitness excelled in this area. Its emphasis on real-time monitoring and swift response mechanisms was the decisive factor for my choice. For teams prioritizing immediate action upon breach detection, RSA NetWitness seems to be the top choice.
Key Features and Integration: At the core of RSA NetWitness is its real-time analytics engine, designed for instant event insights. Additionally, its integration capabilities cover a wide range of third-party tools, enhancing its situational awareness and response speed.
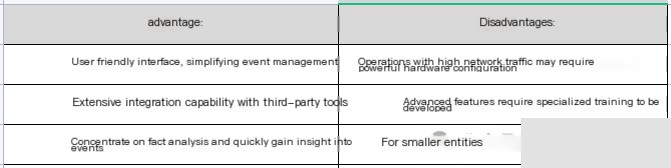
Pros and Cons:
5. FireEye Network Security – Best for Advanced Threat Intelligence
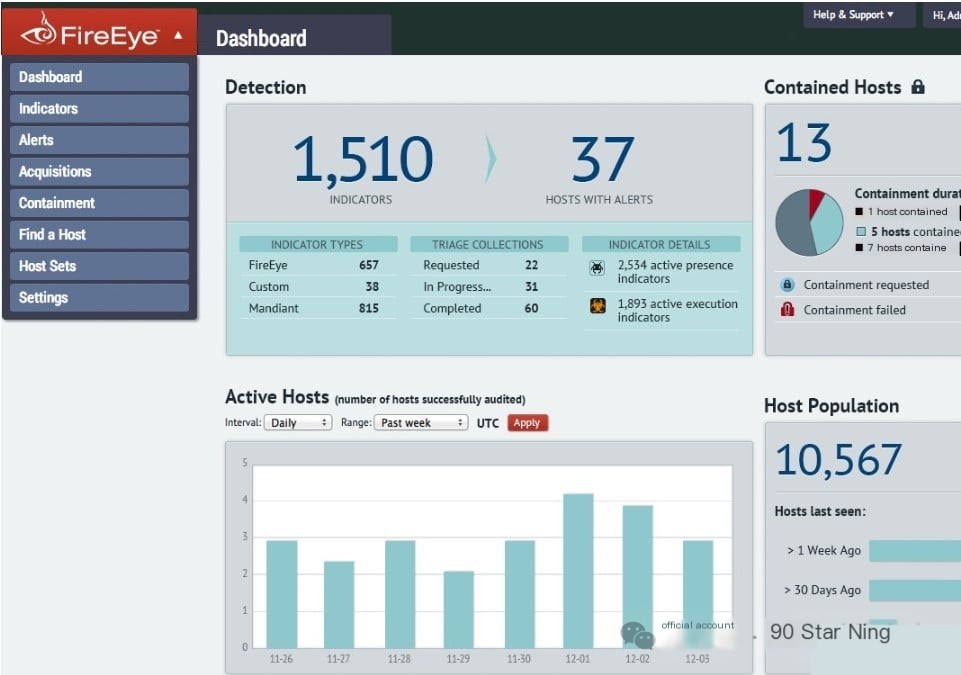
FireEye Network Security is a comprehensive platform focused on advanced threat detection, prevention, and investigation. The tool’s uniqueness lies in its rich threat intelligence, offering insights that many other platforms might miss.
Why I chose FireEye Network Security: After considering various security platforms and their offerings, I chose FireEye for its renowned advanced threat intelligence capabilities. I believe that in the ever-evolving threat landscape, FireEye’s approach to detecting and responding to complex threats sets it ahead of many competitors.
Key Features and Integration: FireEye’s strength lies in its MVX architecture, which identifies and blocks sophisticated threats in real-time. Additionally, its integration capabilities with third-party solutions allow it to adapt to various IT environments.
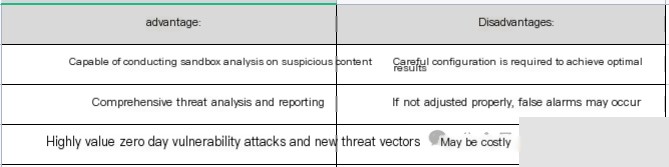
Pros and Cons:
6. Juniper IDP – Best for Threat Detection Versatility
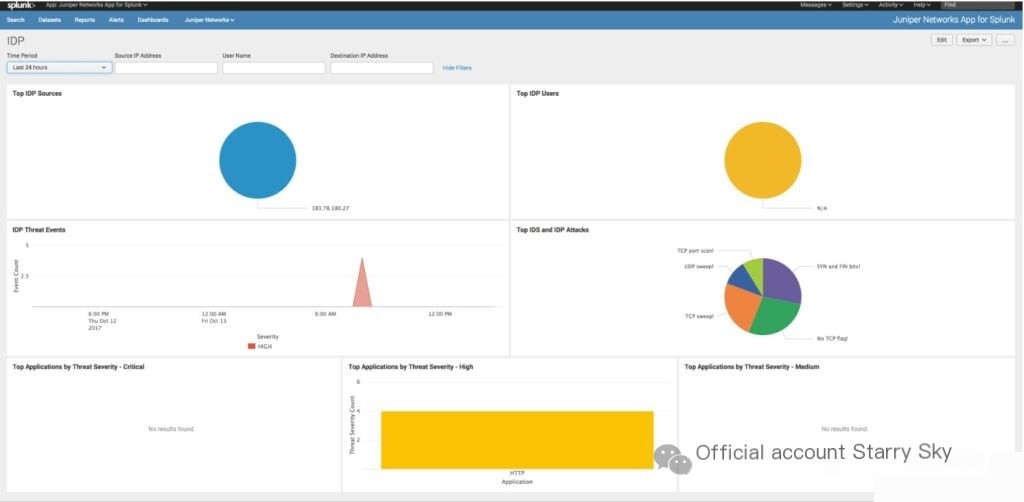
Juniper IDP is renowned for its extensive threat detection methods, making it a preferred choice for organizations that require multiple approaches to protect their digital infrastructure. Its ability to adapt to different threat environments proves that it is indeed built for versatile detection.
Kismet and Nagios Core are cost-effective choices in the intrusion detection field, particularly suitable for small and medium-sized enterprises.
3. Are there high-end, expensive software options?
Yes, tools like Darktrace and FireEye Network Security are at a higher level, primarily catering to the needs of large enterprises with complex requirements.
4. Are there free IDS software options?
Indeed, there are free options such as Kismet and Nagios Core. However, while these tools provide basic IDS functionality, they may lack some of the more advanced features found in paid versions.
Choosing the right Network Intrusion Detection System (NIDS) is crucial for organizations to effectively monitor and protect their network infrastructure. In this guide, we emphasize the importance of such tools, detailing their core functions, key features, availability, and different pricing models. As cyber threats continue to evolve, having a robust intrusion detection system has become an indispensable part of an organization’s defense strategy.
How to Learn Hacking & Cybersecurity
If you like my article today, I will share my private cybersecurity learning materials with you for free. Let’s see what’s included.
1. Learning Roadmap
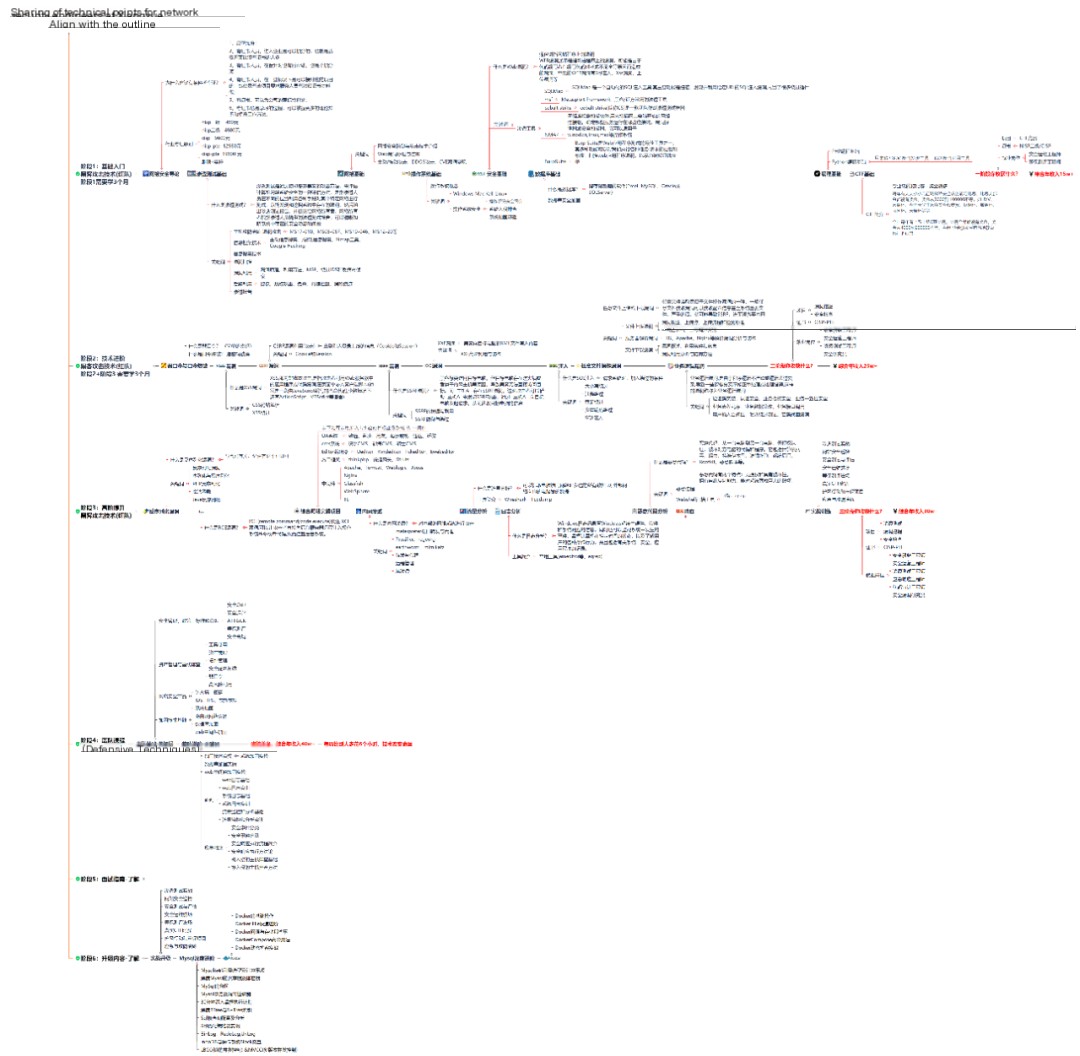
There is a lot to learn about both attack and defense. The specific content is written in the roadmap above. If you can complete it, you will have no problem finding a job or taking on freelance work.
2. Video Tutorials
Although there are many learning resources online, most of them are incomplete. These are my own recorded cybersecurity video tutorials, covering every knowledge point in the roadmap.
The content includes cybersecurity law studies, cybersecurity operations, compliance assessments, penetration testing basics, vulnerability details, and fundamental computer knowledge, all essential for beginners in cybersecurity.
(All packed together, can’t be displayed one by one, a total of over 300 episodes)
Due to space limitations, only a portion of the materials is shown. Click the link below to access the full content.
CSDN Gift Pack: “Hacker & Cybersecurity Beginner & Advanced Learning Resource Pack” Free Share
3. Technical Documents and E-books
The technical documents are also organized by me, including my experiences and technical points from participating in large-scale cybersecurity operations, CTFs, and SRC vulnerability hunting. There are also over 200 e-books. Due to the sensitivity of the content, I won’t display them one by one.

Due to space limitations, only a portion of the materials is shown. Click the link below to access the full content.
CSDN Gift Pack: “Hacker & Cybersecurity Beginner & Advanced Learning Resource Pack” Free Share
4. Toolkits, Interview Questions, and Source Code
“To do a good job, one must first sharpen their tools.” I have summarized the most popular hacker tools for everyone. The scope mainly focuses on information gathering, Android hacking tools, automation tools, phishing, etc. Interested students should not miss it.
There is also the source code of the cases I talked about in my videos and the corresponding toolkits, which you can take if needed.
Due to limited space, only part of the materials is displayed. Click the link below to get more.
CSDN Gift Pack: “Hacker & Network Security Beginner & Advanced Learning Resource Pack” Free Sharing
Finally, I have compiled network security interview questions over the years. If you are looking for a job in network security, they will definitely help you a lot.
These questions are often encountered during interviews with companies like Sangfor, Qi An Xin, Tencent, or other big companies. If you have good questions or insights, feel free to share them.
Reference Analysis: Sangfor official website, Qi An Xin official website, Freebuf, CSDN, etc.
Content Features: Clear and organized, with graphical representations for better understanding.
Content Summary: Includes internal network, operating system, protocols, penetration testing, security services, vulnerabilities, injection, XSS, CSRF, SSRF, file upload, file download, file inclusion, XXE, logical vulnerabilities, tools, SQLmap, NMAP, BP, MSF…
Due to limited space, only part of the materials is displayed. Click the link below to get more.
CSDN Gift Pack: “Hacker & Network Security Beginner & Advanced Learning Resource Pack” Free Sharing
It appears that the provided text contains only HTML tags and no actual content to translate. If you have any specific text content within a WordPress post that you need translated, please provide that text, and I will be happy to assist you.


