Cobalt Strike Feature Evasion and Traffic Obfuscation
Overview:
- Modify default ports
- Disable Ping on the server
- Modify Cobalt Strike’s default certificate
- Use CDN for concealment
- Obfuscate traffic using Malleable C2
Cobalt Strike Server Configuration
0x01. Required Setup
- A VPS
- Domain name
- CDN
- Cobalt Strike 4.0
0x02. Disabling Ping on the Server
Disabling ping on a server makes it appear non-existent in some cases, but tools like Nmap can still detect it.
To disable ping, use the following command:
vim /etc/sysctl.conf
Open the file, press i to enter edit mode, and add the following line anywhere:
net.ipv4.icmp_echo_ignore_all=1
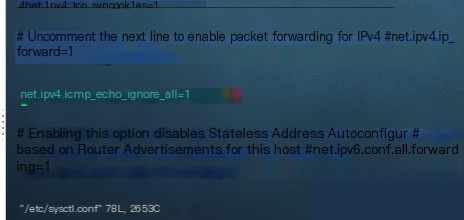
After adding the line, press ESC -> : -> wq (save and exit).
Then, apply the changes using:
sysctl -p
Now, the server will no longer respond to ping requests.

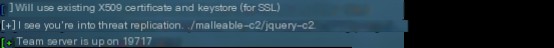
0x03. Changing Cobalt Strike’s Default Port
Modify the port at the end of the teamserver file.
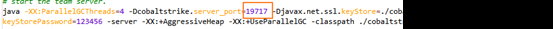
After making the change, restart the teamserver and verify that the port has been updated.
0x04. Modifying the Default Certificate
The default Cobalt Strike certificate contains identifiable characteristics, so it should be replaced with a custom certificate.
Prerequisite: Java must be installed on the server.
Use the keytool utility from JDK to generate a new certificate.
- Delete the existing Cobalt Strike certificate.
- Create a new certificate file and update the last line of the teamserver file to:
-Djavax.net.ssl.keyStore=./new.store - Generate a new certificate in the Cobalt Strike directory.
Run the following command:
keytool -keystore new.store -storepass bypass -keypass bypass -genkey -keyalg RSA -alias apex.tk -dname "CN=Microsoft Windows, OU=MOPR, O=Microsoft Corporation, L=Redmond, ST=Washington, C=US"

- Convert the certificate format and apply it:
keytool -importkeystore -srckeystore cobaltstrike.store -destkeystore cobaltstrike.store -deststoretype pkcs12
To verify the certificate, use:
keytool -list -v -keystore cobaltstrike.store
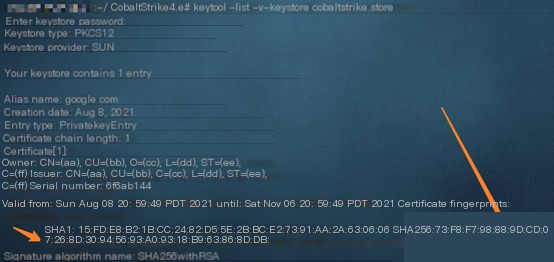
Check if the signature matches when starting the teamserver:
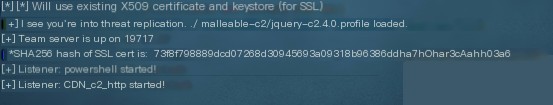
If the signature matches, the certificate modification was successful.
0x05. Traffic Obfuscation
Modify the communication patterns between Beacon and Cobalt Strike by creating a .profile file and adding the following configuration.
https-certificate {
set keystore "new.store";
set password "bypass";
}
http-get {
set uri "/image/";
client {
header "Accept" "text/html,application/xhtml+xml,application/xml;q=0.9,*/*l;q=0.8";
header "Referer" "http://www.google.com";
header "Host" "apex1.tk";
header "Pragma" "no-cache";
header "Cache-Control" "no-cache";
metadata {
netbios;
append ".jpg";
uri-append;
}
}
server {
header "Content-Type" "img/jpg";
header "Server" "Microsoft-IIS/6.0";
header "X-Powered-By" "ASP.NET";
output {
base64;
print;
}
}
}
Save the file and grant execution permissions to c2lint:
chmod 777 c2lint
Then, run:
./c2lint img.profile
If the output matches the following, the configuration is successful:

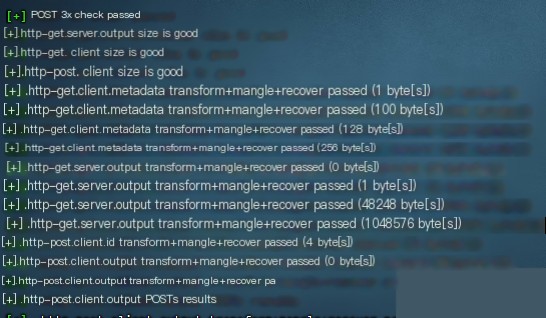
Using CDN for Concealment
0x01. Registering a Free Domain
You can get a free domain from:
www.freenom.com
These domains can be used for blogs or other purposes.
To register, log in with a Google account (use a VPN if necessary).
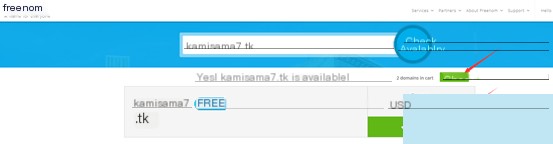
Choose a domain name, check availability, and proceed to checkout. Free registration is available for 1-12 months.
0x02. CDN Configuration (Free Options)
[Further details on CDN setup would go here.]


